Maximizing Talent ROI: Key Strategies and Metrics for Success
In today’s competitive talent landscape, employees are no longer just a cost; they’re a strategic investment. Organizations that prioritize their workforce and maximize its potential see a significant return on talent (ROT). This translates to higher productivity, innovation, and ultimately, a stronger bottom line. Here’s how to cultivate a high-performing workforce and measure the impact of your talent management efforts:
i. Understanding Return on Talent (ROT)

Return on Talent (ROT) measures the value that employees bring to an organization relative to the investment made in their recruitment, development, and retention. A high ROT indicates that an organization effectively leverages its human capital to achieve strategic goals, while a low ROT suggests potential inefficiencies in talent management processes.
ii. Key Moves to Increase Return on Talent
Build a Skills-Based Workforce Strategy

- Build a Skills-Based Workforce Strategy
- Why It Matters:
- Identify the critical skills and competencies your organization needs to thrive in the current market. This forms the foundation for talent acquisition, development, and deployment.
- Strategies:
- Conduct a Strategic Analysis: A strategic analysis helps align your talent needs with your organization’s goals and market demands.
- Engage with Stakeholders: Engaging with key stakeholders ensures that you capture diverse perspectives and identify the most relevant skills and competencies.
- Analyze Current Workforce Capabilities: Understanding the existing skills and competencies within your organization helps identify gaps and areas for improvement.
- Identify Skill Gaps: Identifying skill gaps allows you to focus your talent acquisition and development efforts on the areas with the greatest need.
- Define Critical Skills and Competencies: Clearly defining the critical skills and competencies provides a foundation for all talent management activities.
- Integrate Findings into Talent Management Processes: Integrating the identified skills and competencies into your talent management processes ensures they are consistently applied and reinforced.
- Regularly Review and Update: The skills and competencies required for success can change over time, so it is important to keep your analysis up to date.
- Why It Matters:
Hire the Right Talent

- Hire the Right People
- Why It Matters:
- Go beyond resumes. Implement rigorous skill-based assessments during the interview process to ensure you’re hiring individuals who can make a real contribution.
- Strategies:
- Define Job Requirements and Skills: Clearly defining the skills and competencies required for each role ensures that you know exactly what to look for in candidates.
- Develop Skill-Based Assessments: Skill-based assessments provide objective measures of a candidate’s abilities, reducing reliance on resumes which may not fully capture a candidate’s potential.
- Integrate Assessments into the Hiring Process: Integrating assessments into the hiring process ensures that all candidates are evaluated consistently and objectively.
- Train Hiring Managers and Interviewers: Training hiring managers and interviewers on how to effectively use skill-based assessments ensures consistency and fairness in the evaluation process.
- Evaluate Candidates Based on Assessments: Evaluating candidates based on skill-based assessments ensures that hiring decisions are grounded in objective data rather than subjective impressions.
- Provide Feedback to Candidates: Providing feedback to candidates, both successful and unsuccessful, enhances their experience and helps build a positive employer brand.
- Monitor and Refine the Process: Continuous monitoring and refinement of the assessment process ensure its effectiveness and fairness over time.
- Why It Matters:
Invest in Learning and Development (L&D)

- Invest in Employee Development
- Why It Matters:
- Continuous learning and development ensure that employees remain competent and capable of contributing to organizational goals. Investing in employee development boosts engagement, job satisfaction, and retention.
- Strategies:
- Training Programs: Implement comprehensive training programs tailored to the specific needs of employees and the organization.
- Mentorship and Coaching: Establish mentorship and coaching initiatives to provide employees with guidance and support.
- Career Pathing: Develop clear career paths and opportunities for advancement to motivate employees and align their goals with organizational objectives.
- Why It Matters:
Foster a Positive Work Environment

- Foster a Positive Work Environment
- Why It Matters:
- A positive work environment enhances employee satisfaction and productivity. Happy employees are more likely to stay with the company, reducing turnover and the associated costs of recruiting and training new hires.
- Strategies:
- Employee Well-being: Promote work-life balance, provide wellness programs, and create a supportive workplace culture.
- Recognition and Rewards: Implement recognition programs to celebrate employee achievements and contributions.
- Open Communication: Foster open communication channels to ensure employees feel heard and valued.
- Why It Matters:
Leverage Data and Analytics

- Leverage Data and Analytics
- Why It Matters:
- Data-driven decision-making helps identify areas for improvement and optimize talent management strategies. Analytics can provide insights into employee performance, engagement, and development needs.
- Strategies:
- Performance Metrics: Use performance metrics to evaluate individual and team contributions.
- Engagement Surveys: Conduct regular employee engagement surveys to gauge satisfaction and identify areas for improvement.
- Talent Analytics: Leverage talent analytics to predict turnover, identify high-potential employees, and tailor development programs.
- Why It Matters:
Enhance Recruitment and Onboarding Processes

- Enhance Recruitment and Onboarding Processes
- Why It Matters:
- Effective recruitment and onboarding processes ensure that the right talent is brought into the organization and integrated smoothly. This reduces time-to-productivity and increases retention.
- Strategies:
- Employer Branding: Develop a strong employer brand to attract top talent.
- Efficient Recruitment: Streamline recruitment processes to reduce time-to-hire and improve candidate experiences.
- Comprehensive Onboarding: Implement structured onboarding programs to acclimate new hires and provide them with the tools and knowledge they need to succeed.
- Why It Matters:
Implement Performance Management Systems

- Implement Performance Management Systems
- Why It Matters:
- Robust performance management systems align employee objectives with organizational goals and provide ongoing feedback for improvement. This drives accountability and performance.
- Strategies:
- Regular Reviews: Conduct regular performance reviews to provide constructive feedback and set goals.
- 360-Degree Feedback: Use 360-degree feedback to gain a holistic view of employee performance.
- Individual Development Plans: Create individual development plans (IDPs) that outline specific goals, skills development, and career aspirations.
- Why It Matters:
iii. Essential Metrics to Track
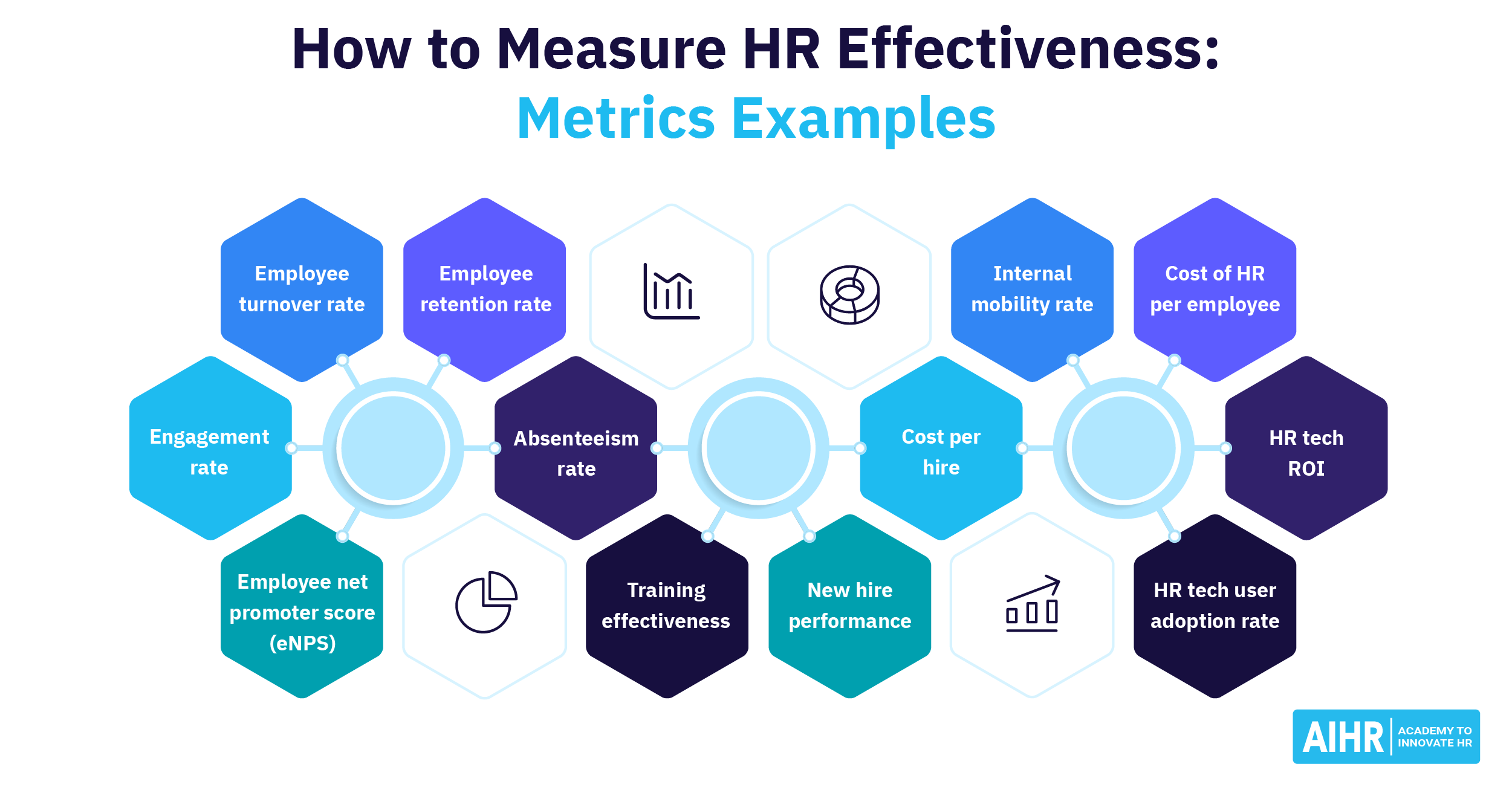
Employee Engagement
- Employee Engagement
- What It Measures:
- Employee engagement measures the emotional commitment employees have to their organization and its goals. High engagement levels indicate motivated and dedicated employees.
- How to Measure:
- Engagement Surveys: Conduct regular engagement surveys and analyze the results to identify trends and areas for improvement.
- Employee Net Promoter Score (eNPS): Measure employees’ likelihood to recommend the organization as a great place to work.
- What It Measures:
Turnover Rate
- Turnover Rate
- What It Measures:
- The turnover rate indicates the percentage of employees who leave the organization within a specific period. High turnover can be costly and disruptive.
- How to Measure:
- Voluntary Turnover Rate: Calculate the percentage of employees who leave voluntarily.
- Involuntary Turnover Rate: Calculate the percentage of employees who are terminated or laid off.
- What It Measures:
Time to Fill

- Time to Fill
- What It Measures:
- Time to fill measures the average number of days it takes to fill an open position. Longer times can indicate inefficiencies in the recruitment process.
- How to Measure:
- Average Time to Fill: Track the time from when a job opening is posted to when an offer is accepted.
- What It Measures:
Training ROI
- Training ROI
- What It Measures:
- Training ROI evaluates the return on investment for employee development programs. It helps determine the effectiveness of training initiatives.
- How to Measure:
- Pre- and Post-Training Assessments: Compare employee performance and productivity before and after training.
- Cost-Benefit Analysis: Calculate the costs of training programs and the benefits gained in terms of improved performance and reduced turnover.
- What It Measures:
Employee Productivity

- Employee Productivity
- What It Measures:
- Employee productivity measures the output of employees relative to their input. High productivity indicates efficient and effective performance.
- How to Measure:
- Performance Metrics: Use performance metrics such as sales figures, project completion rates, and customer satisfaction scores.
- Revenue per Employee: Calculate the total revenue generated divided by the number of employees.
- What It Measures:
Additional Metrics

- Other Metrics
- Employee Engagement Scores: Regularly measure employee engagement through surveys or pulse checks. High engagement scores indicate employees are satisfied, motivated, and invested in the organization’s success.
- Time-to-Productivity: Track the time it takes for new hires to become fully productive. This metric can be improved by streamlining onboarding processes and providing effective training.
- Customer Satisfaction: Highly skilled and engaged employees are more likely to deliver exceptional customer service. Track customer satisfaction metrics to understand the impact of talent management on customer experience.
- Innovation Rate: Innovation thrives in a culture of empowerment and learning. Track the number of new ideas, inventions, or successful process improvements to gauge the impact of your talent management efforts on innovation.
iv. The Future of ROT
As the world of work continues to evolve with technological advancements and shifting work dynamics, the importance of optimizing ROT will only increase. Organizations must remain agile and proactive in attracting, developing, and retaining talent. By strategically implementing effective talent management practices and diligently measuring their impact, companies can significantly enhance their overall performance and sustain a competitive advantage.
v. Conclusion
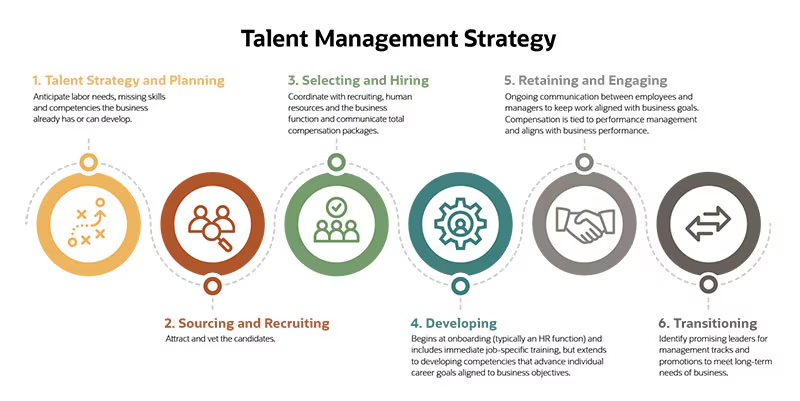
Increasing your return on talent involves strategic investments in employee development, fostering a positive work environment, leveraging data and analytics, enhancing recruitment and onboarding processes, and implementing robust performance management systems. By tracking essential metrics such as employee engagement, turnover rate, time to fill, training ROI, and employee productivity, organizations can gain valuable insights into their talent management strategies and make data-driven decisions to optimize their workforce. Ultimately, a focus on maximizing return on talent leads to a more motivated, productive, and loyal workforce, driving long-term organizational success.
vi. Further references
Manage Your Talent Pipeline – Manage Your Recruiting Easilybreezy.hrhttps://www.breezy.hr
Business Explained – 14 Productivity Strategies PDFbusiness-explained.comhttps://www.business-explained.com
Increasing your return on talent: The moves and metrics …SoundCloud · McKinsey & Company2 months ago
Metrics Archives – BrianHeger.comBRIAN HEGERhttps://www.brianheger.com › tag › metrics