Navigating the Evolving Landscape: Latest Insights on IoT Security
The Internet of Things (IoT) continues its relentless expansion, with billions of connected devices woven into the fabric of our lives. While this interconnectedness offers undeniable convenience and innovation, it also presents a growing security challenge. However, as IoT adoption continues to surge, so do the security challenges associated with it. With billions of connected devices worldwide, securing the IoT ecosystem has become a critical priority for businesses, governments, and consumers alike.
i. The Growing IoT Landscape

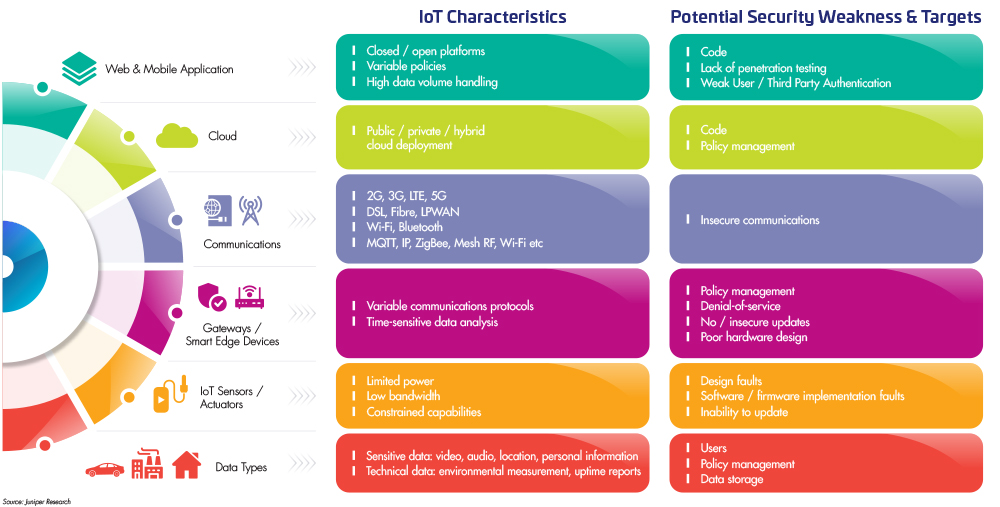
The IoT landscape is expanding rapidly, with applications spanning across various industries including healthcare, manufacturing, transportation, smart homes, and more. According to industry reports, the number of IoT devices is expected to reach 30.9 billion by 2025. This proliferation of connected devices brings numerous benefits, such as improved operational efficiency, enhanced data collection, and innovative services. However, it also introduces significant security risks.
ii. The Evolving Threat Landscape
- Mass and Fragility: The sheer number of connected devices, often with limited security features, creates a vast attack surface for malicious actors.
- Emerging Attack Vectors: Hackers are constantly developing new ways to exploit vulnerabilities in IoT devices, from botnet attacks to firmware manipulation.
- Supply Chain Risks: The complex global supply chains for IoT devices introduce potential vulnerabilities that attackers can exploit.
iii. The Rise of Proactive Defense

- Security by Design: Manufacturers are increasingly prioritizing security throughout the design and development lifecycle of IoT devices.
- Standardization and Certification: Industry standards and certifications are emerging to ensure a minimum level of security in IoT devices.
- Software Updates and Patch Management: Regular software updates and vulnerability patching are crucial to maintain robust security.
iv. Securing the Future of IoT

- Focus on Secure Onboarding: Streamlining the onboarding process for new IoT devices is essential, but it should prioritize security measures like secure authentication and authorization protocols.
- Leveraging PKI (Public Key Infrastructure): Digital certificates issued by trusted authorities can enhance secure communication and identity management for IoT devices.
- Micro-segmentation and Access Control: Granular access controls and segmentation of IoT networks can limit the potential damage caused by a security breach.
v. Emerging IoT Security Threats

- Device Vulnerabilities: Many IoT devices are designed with minimal security features, making them easy targets for cyberattacks. Common vulnerabilities include weak or hardcoded passwords, lack of encryption, and outdated firmware. Attackers can exploit these weaknesses to gain unauthorized access to devices and networks.
- Botnets and DDoS Attacks: Botnets, which are networks of compromised devices controlled by attackers, pose a major threat to IoT security. IoT devices can be hijacked to form botnets and used to launch Distributed Denial of Service (DDoS) attacks, overwhelming networks and causing widespread disruption. Notable examples include the Mirai botnet attack that took down major internet services in 2016.
- Data Privacy Issues: IoT devices collect vast amounts of data, often including sensitive personal information. Without proper security measures, this data can be intercepted, stolen, or misused by malicious actors. Data breaches can lead to identity theft, financial loss, and erosion of user trust.
- Network Attacks: IoT devices are typically interconnected through networks, creating multiple entry points for attackers. Compromising a single device can provide access to the entire network, allowing attackers to move laterally and escalate privileges.
- Physical Security Risks: Many IoT devices are deployed in unsecured or remote locations, making them susceptible to physical tampering. Attackers can manipulate devices, extract sensitive information, or even replace them with malicious counterparts.
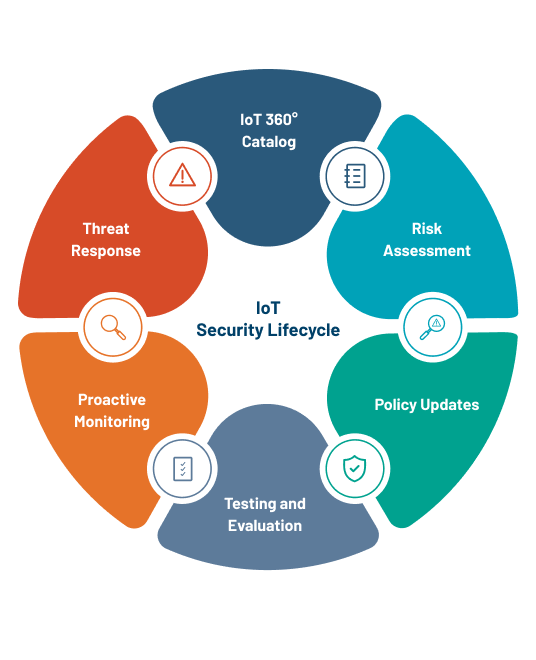
vi. Best Practices for Enhancing IoT Security

- Device Hardening
- Securing IoT devices starts with hardening them against attacks. This includes:
- Changing Default Passwords: Replace default passwords with strong, unique passwords.
- Firmware Updates: Regularly update device firmware to patch known vulnerabilities.
- Disabling Unused Features: Turn off unnecessary features and services to reduce attack surfaces.
- Encryption: Implement end-to-end encryption to protect data in transit and at rest.
- Securing IoT devices starts with hardening them against attacks. This includes:
- Network Segmentation
- Segmenting IoT devices into separate network zones can limit the impact of a security breach. By isolating IoT devices from critical systems and data, organizations can contain potential threats and prevent attackers from moving laterally.
- Implementing Strong Authentication
- Use multi-factor authentication (MFA) to enhance security. MFA requires users to provide two or more verification factors, making it more difficult for attackers to gain unauthorized access.
- Regular Security Audits
- Conduct regular security audits and vulnerability assessments to identify and address potential weaknesses in IoT systems. Penetration testing can also help uncover hidden vulnerabilities before attackers exploit them.
- Data Privacy Measures
- Protect user data by implementing robust data privacy measures. This includes:
- Data Minimization: Collect only the data that is necessary for the intended purpose.
- Anonymization: Anonymize data to prevent the identification of individuals.
- Access Controls: Restrict access to sensitive data based on user roles and responsibilities.
- Protect user data by implementing robust data privacy measures. This includes:
- Monitoring and Incident Response
- Establish continuous monitoring and incident response capabilities to detect and respond to security incidents promptly. Use security information and event management (SIEM) systems to collect and analyze security data in real-time.
- Supply Chain Security
- Ensure that all components and software used in IoT devices are sourced from trusted suppliers. Verify the integrity of hardware and software to prevent supply chain attacks.
vii. Industry Standards and Regulations
- Stricter Compliance Requirements: Regulatory bodies are imposing more stringent requirements on IoT device manufacturers to ensure security. Standards like the European Union’s General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) influence global security practices by demanding robust data protection measures.
- Industry Collaboration: There is a growing emphasis on collaboration among industry stakeholders to develop and implement unified security standards. Alliances such as the Internet of Things Security Foundation (IoTSF) promote best practices and provide guidelines to enhance security across IoT ecosystems.
viii. Future Trends in IoT Security

- AI and Machine Learning: Artificial intelligence (AI) and machine learning (ML) are being increasingly integrated into IoT security solutions. These technologies can analyze vast amounts of data to detect anomalies, predict potential threats, and automate responses, enhancing the overall security posture.
- Edge Computing: Edge computing involves processing data closer to where it is generated, reducing latency and bandwidth usage. By implementing security measures at the edge, organizations can protect data locally and reduce the risk of exposure during transmission.
- Blockchain Technology: Blockchain offers a decentralized and tamper-proof ledger that can enhance IoT security. It can be used to secure data transactions, manage identities, and ensure the integrity of IoT devices and networks.
- Zero Trust Security Model: The Zero Trust security model operates on the principle of “never trust, always verify.” It requires strict verification of all devices and users, regardless of their location, to prevent unauthorized access. Implementing Zero Trust can significantly strengthen IoT security.
- Regulatory Compliance: Governments and regulatory bodies are increasingly introducing regulations to enhance IoT security. Organizations must stay informed about these regulations and ensure compliance to avoid legal and financial repercussions.
ix. Beyond the Technical: Building a Culture of Security

- User Education and Awareness: Empowering users to identify suspicious activity and practice safe use of IoT devices is vital.
- Shared Responsibility: A collaborative approach is necessary. Manufacturers, device owners, and service providers all have a role to play in ensuring IoT security.
- Regulatory Landscape: Governments are increasingly enacting regulations to hold manufacturers and service providers accountable for IoT security.
x. Conclusion

As the IoT landscape continues to expand, so do the security challenges associated with it. Organizations must adopt a proactive and comprehensive approach to IoT security to protect their assets, data, and users. By implementing best practices, leveraging emerging technologies, and staying informed about future trends, businesses can enhance their IoT security posture and navigate the complexities of the digital age with confidence. Investing in robust IoT security measures is not just a technical necessity but a strategic imperative for sustained success.
xi. Further references
Download Report | It security | Embrace DevOps’ best practicesredhat.comhttps://www.redhat.com
IoT Tech News | Latest IoT News & Insights | Internet of Things …IoT Tech Newshttps://www.iottechnews.com
Best IoT Security Reviews 2024Gartnerhttps://www.gartner.com › reviews › market › iot-security
IoT Security Challenges and ProblemsBalbixhttps://www.balbix.com › insights › addressing-iot-securi…
IoT Security Market Analysis and Updates for 2023-2030LinkedIn · Trend Insights Hub4 months ago
