
Harnessing Machine Learning for Proactive Threat Detection in Cybersecurity
The ever-evolving threat landscape demands more than just traditional security measures. Enter AI-powered cybersecurity, an innovative approach leveraging machine learning (ML) for proactive threat detection.
Think of it as a vigilant sentinel constantly scanning the horizon, anticipating and neutralizing threats before they can wreak havoc.
i. Unlocking AI’s Power:

ML algorithms, trained on vast datasets of past attacks and anomalies, can identify subtle patterns that human analysts might miss. This enables:
o Real-time threat detection: Analyze network traffic, user behavior, and system logs in real-time, identifying suspicious activities as they occur.
o Predictive analysis: Anticipate potential attacks by learning from historical data and identifying emerging trends and vulnerabilities.
o Automated response: Trigger pre-defined actions to contain threats automatically, minimizing damage and response time.
ii. Benefits Abound:
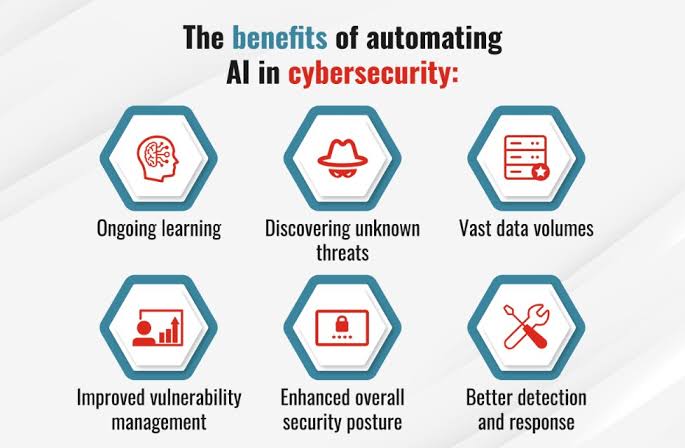
Implementing AI-powered cybersecurity offers several advantages:
o Enhanced efficiency: Free your security team from tedious tasks, allowing them to focus on strategic initiatives.
o Improved accuracy: Identify and respond to threats faster and more accurately, minimizing false positives.
o Scalability: Adapt to ever-growing data volumes and complex IT environments with ease.
o Proactive defense: Shift from reactive patching to proactive prevention, reducing the impact of successful attacks.
iii. Challenges to Consider:

While promising, AI-powered cybersecurity has its own set of challenges:
o Data quality and bias: The effectiveness of ML models depends on the quality and diversity of training data. Biases in the data can lead to biased models, perpetuating unfair outcomes.
o Explainability and transparency: Understanding how AI systems make decisions is crucial for building trust and ensuring fairness. Balancing explainability with model complexity is key.
o Security of the AI itself: AI systems themselves can be vulnerable to attacks, requiring robust security measures to protect them.
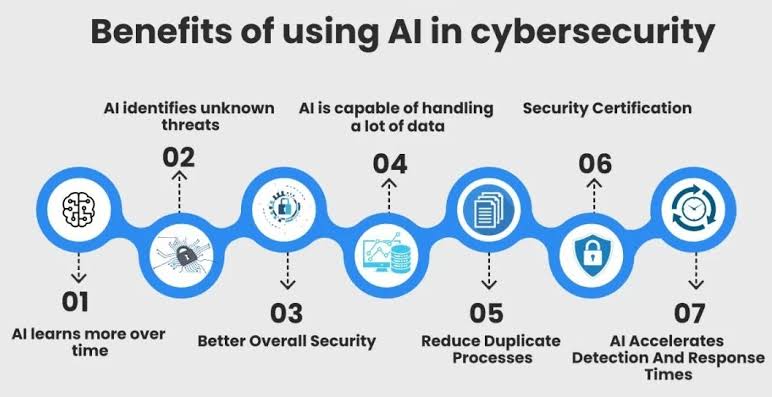
iv. Here’s an exploration of the key elements involved in leveraging machine learning for proactive threat detection in cybersecurity:
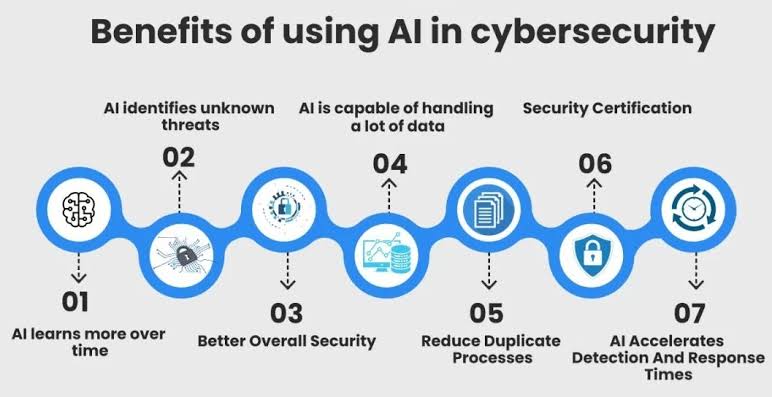
A. Anomaly Detection: Utilize machine learning algorithms to establish baselines for normal network behavior. Anomalies, deviations from these baselines, can signal potential threats. Continuous monitoring enables swift detection of unusual patterns indicative of cyber threats.
B. Behavioral Analysis: Implement behavioral analysis powered by machine learning to scrutinize user and system behavior. By understanding normal patterns, machine learning models can identify deviations that may signify unauthorized access or malicious activities.
C. Predictive Analysis: Employ machine learning for predictive analysis to forecast potential threats based on historical data and evolving attack trends. This forward-looking approach enables organizations to implement preemptive measures before threats materialize.
D. Advanced Threat Intelligence: Enhance threat intelligence by integrating machine learning algorithms that can sift through vast datasets to identify emerging threats. Machine learning aids in processing and analyzing threat data rapidly, improving the accuracy and timeliness of threat intelligence.

E. Phishing Detection: Machine learning models are capable of detecting phishing attempts by analyzing the content and metadata of emails to identify malicious intent.
F. Malware and Ransomware Detection: AI-powered systems can recognize the signatures of known malware, and more importantly, use behavior-based analysis to detect new and evolving forms of malware and ransomware.
G. Dynamic Risk Scoring: Implement dynamic risk scoring models that leverage machine learning to assess the severity of detected anomalies. This facilitates prioritized responses, focusing resources on addressing the most critical threats first.
H. User and Entity Behavior Analytics (UEBA): Leverage UEBA solutions driven by machine learning to scrutinize the behavior of users and entities within the network. Detecting deviations from normal behavior can unveil insider threats or compromised accounts.

I. Automated Incident Response: Integrate machine learning into incident response mechanisms to automate the identification and containment of threats. This accelerates response times, reducing the potential impact of cyber incidents.
J. Adaptive Security Architectures: Develop adaptive security architectures that evolve in response to emerging threats. Machine learning enables systems to learn from past incidents and adapt defenses to thwart similar future attacks.
K. Zero-Day Threat Detection: Enhance the ability to detect zero-day threats by leveraging machine learning algorithms that identify patterns and anomalies indicative of previously unseen attacks. This proactive approach is crucial for safeguarding against emerging threats.
L. Continuous Learning Models: Implement continuous learning models that evolve and improve over time. Regular updates based on new threat intelligence and evolving attack techniques ensure the effectiveness of machine learning models in detecting the latest cyber threats.

M. Explainability and Transparency: Prioritize machine learning models with explainability features to enhance transparency. Understanding how models arrive at conclusions is crucial for cybersecurity professionals in validating and trusting automated threat detection systems.
N. Collaborative Threat Detection: Foster collaborative threat detection by enabling machine learning models to share insights across interconnected systems. This collective intelligence strengthens the overall cybersecurity posture.
O. Data Quality and Diversity: Ensure high-quality and diverse datasets for training machine learning models. Representative data enhances the accuracy and reliability of threat detection algorithms across various scenarios.
P. Secure Authentication: AI enhances authentication by integrating biometric data, behavioral characteristics, and device usage patterns into the authentication process.
Q. Network Security Policy Management: AI systems can assist in the creation and enforcement of network security policies by analyzing network configurations and recommending optimizations.
R. Vulnerability Management: AI can monitor and analyze systems continuously for vulnerabilities, sometimes predicting which vulnerabilities are likely to be exploited before they cause an issue.
S. Security Orchestration, Automation, and Response (SOAR): Integrating AI into SOAR platforms can help coordinate, execute, and automate complex workflows across various security tools without human intervention.
T. Deep Learning: Using deep learning, a subset of ML, AI can identify patterns hidden deep within data that would evade traditional cybersecurity measures.

U. Human-Machine Collaboration: Facilitate collaboration between cybersecurity professionals and machine learning systems. While automation is powerful, human expertise is essential for contextual understanding and decision-making in complex threat scenarios.
V. Compliance and Ethics: Uphold ethical considerations and comply with relevant regulations when implementing AI-powered cybersecurity measures. Transparency, fairness, and accountability are vital aspects of deploying machine learning in a responsible manner.
v. The Road Ahead:

Despite the challenges, AI-powered cybersecurity is rapidly evolving, holding immense potential for a more secure future. By fostering responsible development, addressing ethical concerns, and continuously improving algorithms, we can make this technology a powerful tool in the fight against cyber threats.
Remember: AI is not a silver bullet, but a valuable addition to your security arsenal. By combining it with traditional security measures and skilled personnel, you can create a comprehensive and proactive defense against the ever-changing threat landscape.
By incorporating AI and machine learning into cybersecurity strategies, organizations can shift from reactive security postures to proactive ones.
However, it’s crucial to recognize that machine learning models require continuous training and fine-tuning to adapt to the evolving threat landscape.
Additionally, there needs to be a balanced approach that includes human oversight to interpret and respond to the nuances that AI might miss.
vi. Further references
freeCodeCamphttps://www.freecodecamp.org › newsHow Security Analysts Can Use AI in Cybersecurity
TechMagichttps://www.techmagic.co › blogAI in Cybersecurity: Exploring the Top 6 Use Cases
LinkedInhttps://www.linkedin.com › pulseLeveraging the Power of Artificial Intelligence in …
