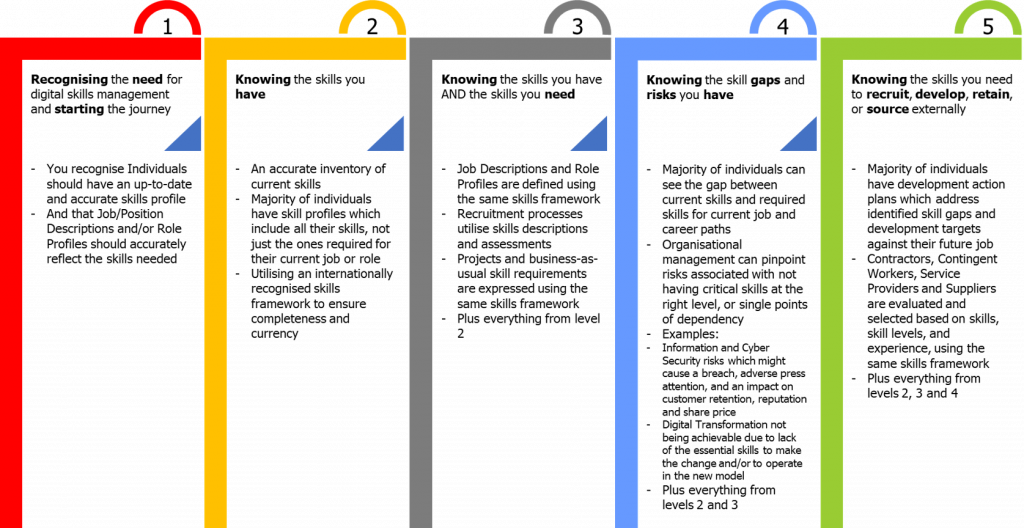Escape the Training Labyrinth: How SFIA Can Sharpen Your Workforce (and Save Money)
In the rapidly evolving world of technology, businesses aims to ensure their workforce possesses the right skills is critical for maintaining a competitive edge.
Yet, many organizations find themselves trapped in what can be described as “training purgatory.”
This state is characterized by endless cycles of training programs that yield minimal results, high costs, and growing frustration.
While continuous learning is essential, the challenge lies in ensuring that training is both relevant and cost-effective.
Enter the Skills Framework for the Information Age (SFIA).
This internationally-recognized framework offers a strategic way to manage skills and competencies that can ultimately liberate your organization from the constraints of inefficient training practices.
i. Understanding the Training Purgatory

Training Purgatory is a term that describes a state where organizations invest heavily in training without seeing significant returns.
This limbo is characterized by:
o Unstructured Learning Paths: Employees attend numerous courses that don’t align with their roles or the organization’s goals.
o Repetitive Training Cycles: Employees attend multiple training sessions without achieving mastery or practical application of the skills learned.
o Lack of clear direction: a lack of clear direction and effectiveness in training programs.
o High Costs with Low ROI: Substantial amounts of money are spent on training programs without clear improvement in performance or productivity.
o Skill Gaps and Mismatches: Despite various trainings, employees still face skill gaps that affect their efficiency and job satisfaction.
o Misalignment of Skills and Needs: Training programs often do not align with the actual skills required for specific roles, leading to irrelevant or redundant training.
o Employee Frustration: Employees become disengaged when they feel their training is ineffective or not relevant to their career goals.
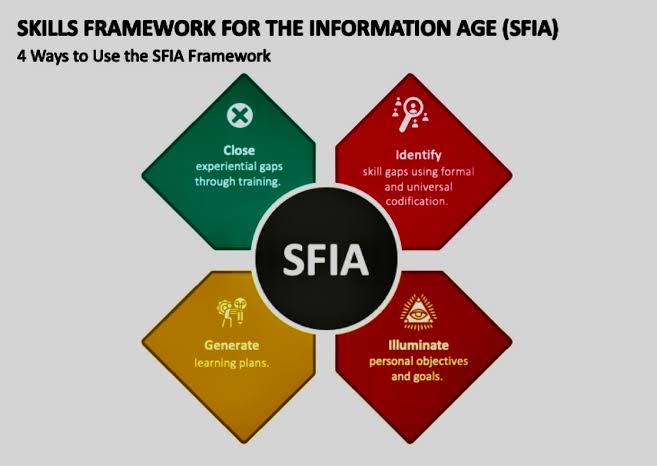
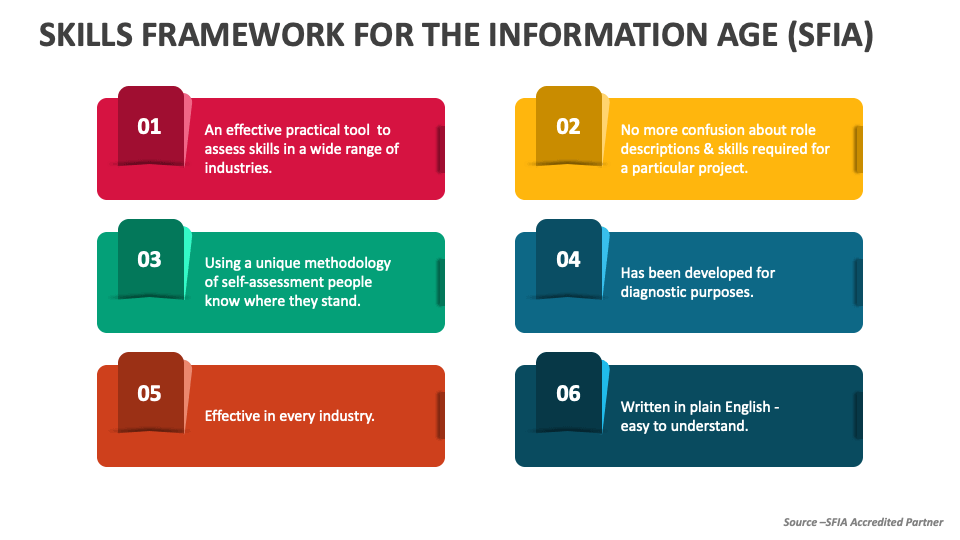
ii. What is SFIA?
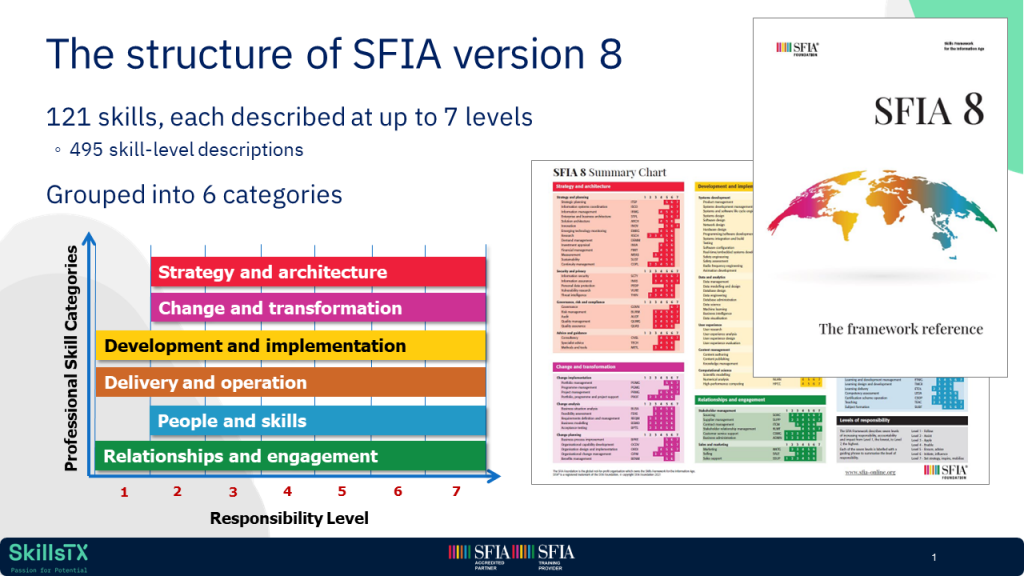
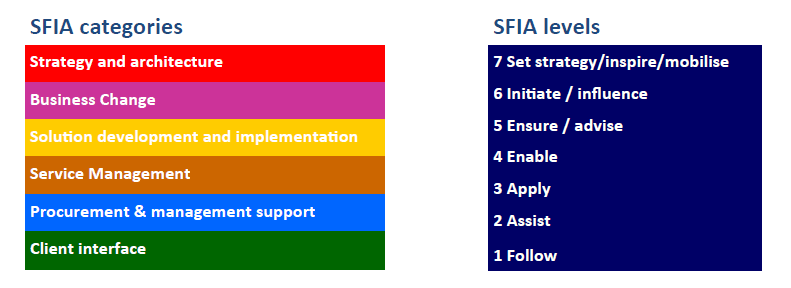
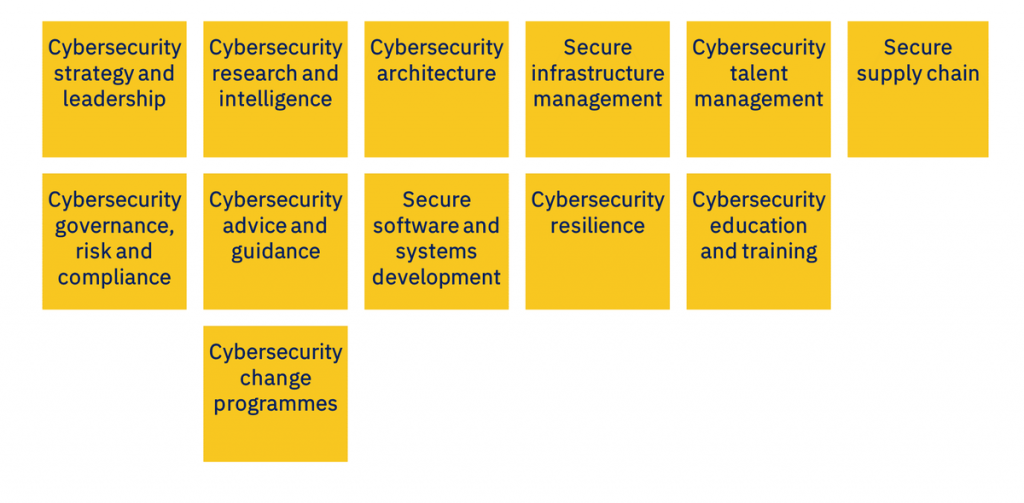
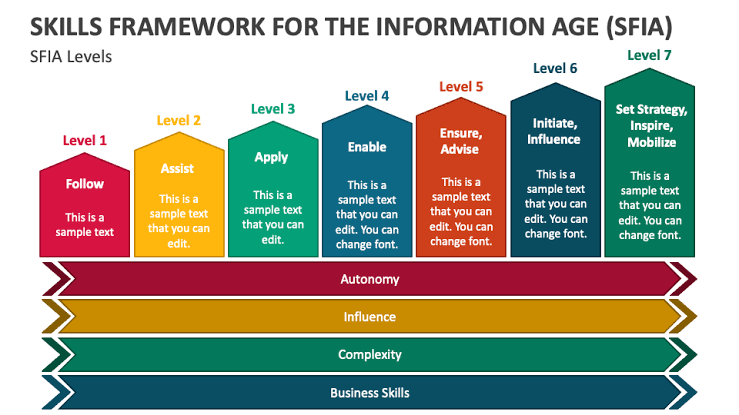
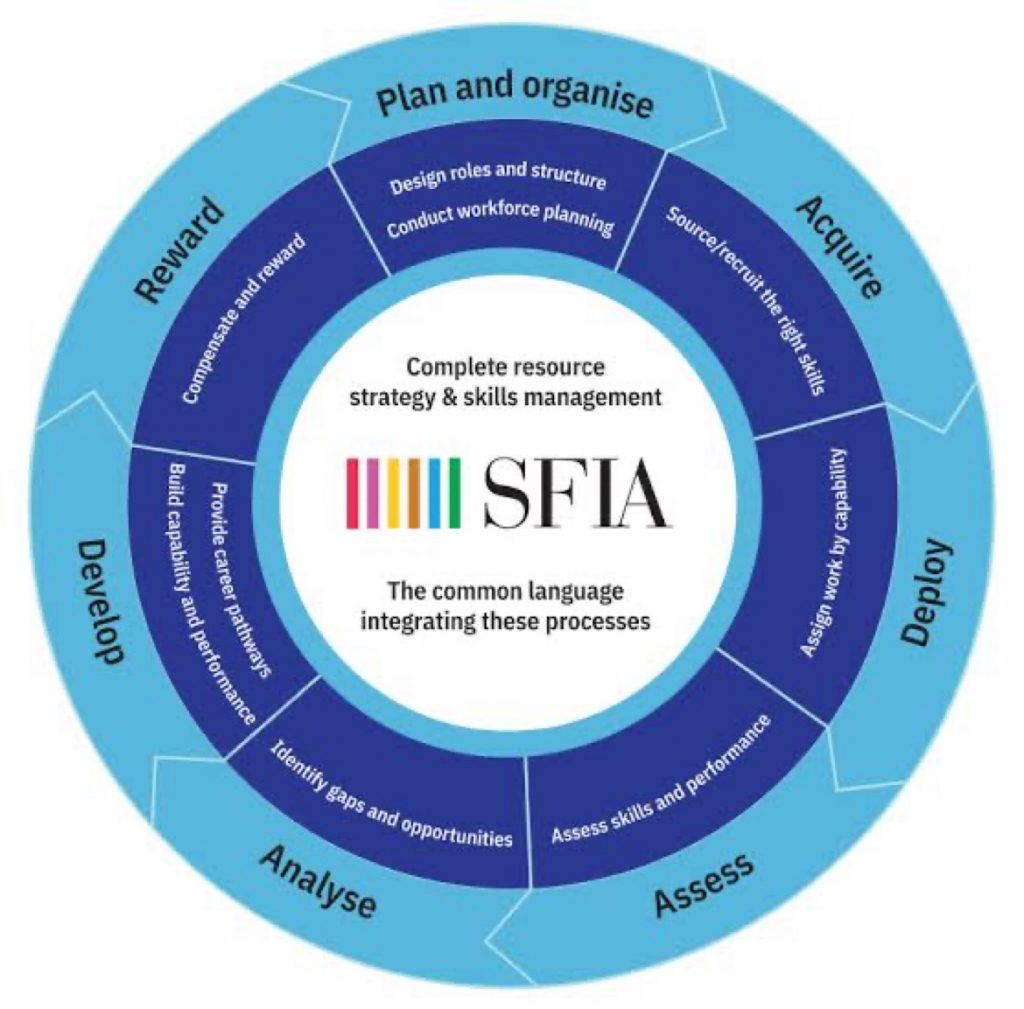
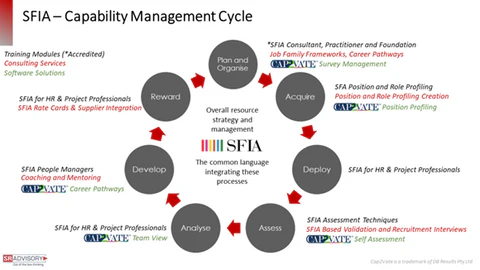
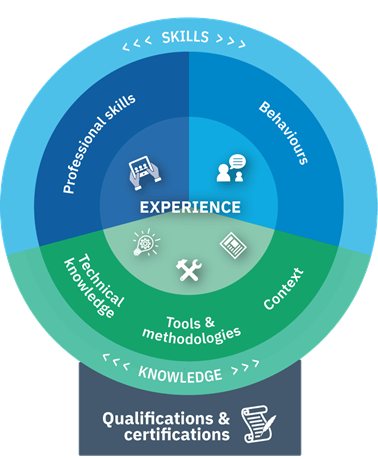
The Skills Framework for the Information Age (SFIA) provides a common language to describe skills and competencies required by professionals in the digital world. SFIA categorizes and standardizes skills across seven levels of responsibility, from entry-level positions to senior leadership roles. Its structured approach ensures that training programs are directly aligned with the needs of the business and the professional development of the employees.
iii. How SFIA Can Liberate Your Training Strategy

A. Aligning Skills with Business Needs: SFIA helps organizations identify the specific skills required for various roles. By aligning training programs with these skills, businesses can ensure that employees are learning what’s necessary to meet organizational objectives. This alignment minimizes wasted resources on irrelevant training courses.
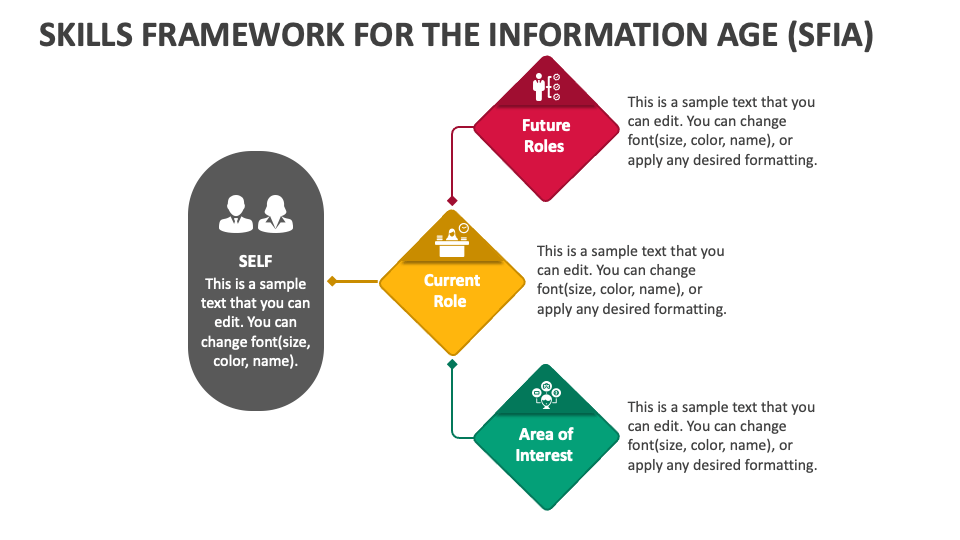
B. Creating Clear Career Pathways: With SFIA, career progression becomes structured and transparent. Employees can see a clear pathway for advancement, which includes the skills and competencies needed at each level. This clarity motivates employees to engage in targeted training that directly supports their career goals.
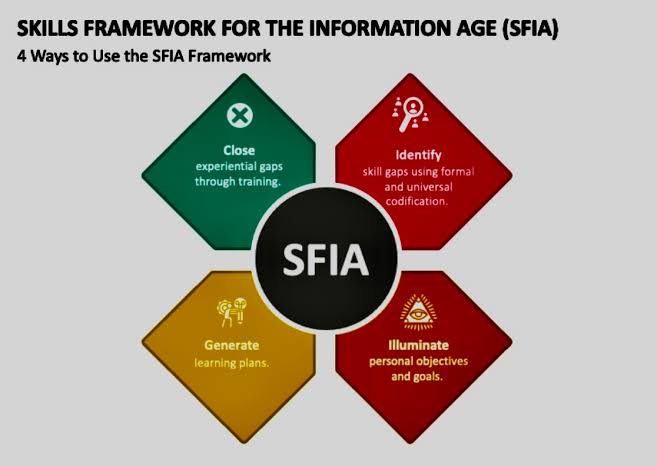
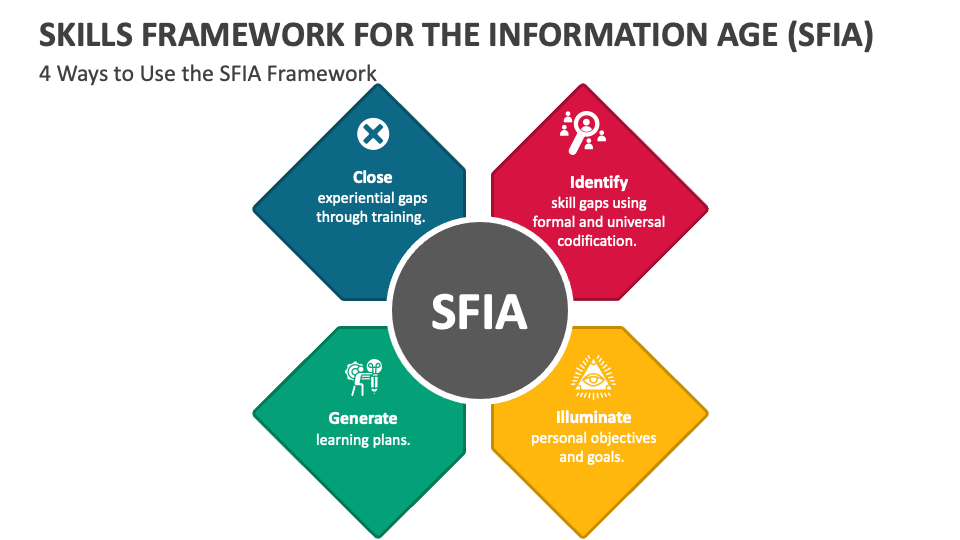
C. Optimizing Training Investments: SFIA allows organizations to perform a skills gap analysis. By understanding where gaps exist, companies can invest in precise training initiatives rather than blanket programs. This targeted approach maximizes the return on investment and ensures that training budgets are spent wisely.

D. Targeted Training: By pinpointing specific skill gaps using SFIA, companies can tailor their training programs to address the exact needs of their team. This eliminates wasted resources spent on generic training that may not be relevant to their daily tasks.
E. Enhancing Talent Management: A coherent skills framework like SFIA aids in more effective talent management. Organizations can better assess current competencies, identify areas for development, and plan for future workforce needs. This strategic management of talent leads to higher performance and job satisfaction among employees.
F. Future-Proof the Workforce: The IT industry is constantly evolving. SFIA helps organizations stay ahead of the curve by identifying the skills their teams will need to succeed in the future.

G. Standardized Language: SFIA provides a common language for discussing skills across the organization. This improves communication and collaboration between departments, ensuring everyone is on the same page.
H. Facilitating Continuous Professional Development: SFIA supports the continuous professional development of employees by ensuring they are aware of the skills they need to develop. Continuous learning, structured by SFIA, is more purposeful and engaging, moving away from the monotonous cycles of unrelated training activities.
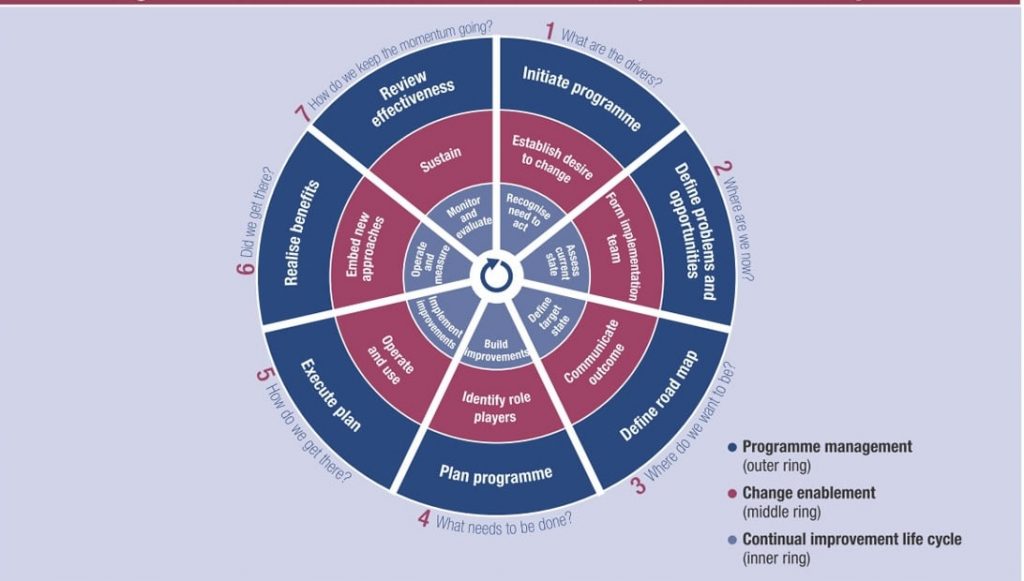
iv. Implementing SFIA: Steps for Success
o Assessment and Benchmarking: Begin by assessing the current skills within your organization and benchmarking them against SFIA’s standards. This process helps in identifying existing strengths and areas for development.
o Strategic Planning: Develop a strategic training and development plan based on the SFIA framework. This plan should align with the organization’s goals and address the identified skills gaps.
o Define Role Requirements: Clearly define the skills and competencies required for each role within your organization. SFIA provides a detailed model that can be tailored to fit your specific needs.

o Identify Skill Gaps: Perform a gap analysis to determine where the discrepancies lie between current skills and required skills. This analysis will guide your training strategy.
o Develop Targeted Training Programs: Design and implement training programs that address the identified skill gaps. Ensure these programs are aligned with your organizational goals and the specific needs of your employees.
o Engagement and Communication: Communicate the importance and benefits of SFIA to your employees. Engage them in the process to ensure their buy-in and commitment to targeted learning.
o Ongoing Monitoring and Evaluation: Continuously monitor the effectiveness of your training programs and measure their impact on performance and productivity. Use this data to refine and improve your training strategy over time.
v. Implementation Considerations

Adopting SFIA requires thoughtful planning and engagement from various stakeholders within the organization. Key steps include:
o Strategic Audit: Assess the current skills landscape and how it aligns with organizational goals.
o Framework Customization: Tailor the SFIA framework to reflect the specific context and needs of your organization.
o Stakeholder Engagement: Ensure buy-in from leadership, HR, IT, and employees through clear communication and demonstration of benefits.
o Ongoing Monitoring: Regularly review skill levels, training effectiveness, and alignment with strategic objectives, adjusting as necessary.
vi. Conclusion

Training purgatory can be a significant drain on resources and morale, but it doesn’t have to be a permanent state. By leveraging the SFIA framework, organizations can develop a strategic approach to skills development that is both cost-effective and impactful. This structured method not only sets training programs free from inefficiency but also empowers the workforce with the skills they need to drive success.
By adopting SFIA, organizations can move away from generic, one-size-fits-all training and create a more strategic and targeted approach to workforce development.
This will not only empower teams with the skills they need to succeed but also save organizations valuable time and money in the long run.