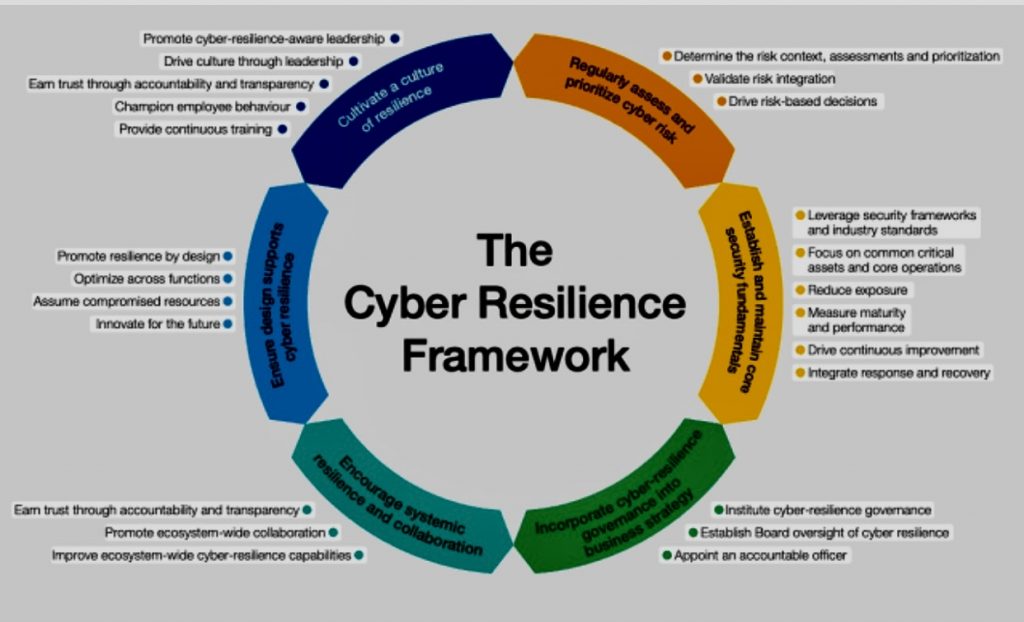
Building fraud resilience in the digital era requires organizations to adopt a comprehensive approach that encompasses prevention, detection, and response.
This involves implementing robust security measures, fostering a culture of fraud awareness, and leveraging technology to proactively identify and mitigate fraud risks.
Here are key strategies to enhance fraud resilience:
A. Risk Assessment and Understanding:
– Conduct a comprehensive risk assessment to identify potential fraud risks specific to your organization. Understand the nature of digital fraud threats, including phishing, account takeovers, and social engineering.
B. Establish a Fraud Risk Management Program: Develop a centralized fraud risk management program that outlines the organization’s approach to identifying, assessing, and managing fraud risks. This program should include clear roles and responsibilities, risk assessment methodologies, and incident response procedures.
C. Identify and Assess Fraud Risks: Regularly conduct fraud risk assessments to identify and prioritize potential fraud threats. This involves analyzing historical data, industry trends, and emerging fraud tactics to understand the organization’s vulnerability to various fraud schemes.
D. Implement Robust Security Controls: Implement a layered security architecture that encompasses physical, network, and application security controls to protect sensitive data and prevent unauthorized access. This includes firewalls, intrusion detection systems, data encryption, and access controls.
E. Foster a Culture of Fraud Awareness: Raise awareness among employees about fraud risks and common fraud schemes. Provide training and education to help employees recognize and report suspicious activity, reducing the risk of insider fraud.
F. Establish a Collaborative Fraud Response Process: Develop a clear and well-defined incident response plan to effectively handle fraud incidents. This plan should include communication protocols, escalation procedures, and law enforcement coordination.
G. Stay Informed About Fraud Regulations: Keep abreast of emerging fraud regulations and industry standards to ensure compliance and implement appropriate measures to address evolving regulatory requirements.
H. Behavioral Biometrics: Explore the use of behavioral biometrics to authenticate users based on their unique patterns of behavior. This can include keystroke dynamics, mouse movements, and other behavioral markers, adding an extra layer of security.
I. Multi-Factor Authentication (MFA): Enforce multi-factor authentication to enhance user verification. Require users to provide multiple forms of identification, such as passwords, biometrics, or one-time passcodes, to access sensitive information or conduct transactions.
J. Utilize Fraud Detection Technologies: Leverage fraud detection technologies, such as machine learning and artificial intelligence, to analyze transaction data and identify anomalous patterns that may indicate fraudulent activity. These technologies can provide real-time insights and enable proactive fraud prevention.
K. Implement strong access controls: Precise control over who has access to certain data can play a crucial role in preventing fraudulent activities. The principle of least privilege (PoLP) should be applied, where users are given the minimum levels of access necessary to complete their tasks.
L. Real-Time Transaction Monitoring: Implement real-time monitoring of transactions to quickly detect and respond to potentially fraudulent activities. Automated systems can analyze transaction patterns and flag suspicious behavior for further investigation.
M. Collaboration and Information Sharing: Collaborate with industry peers, law enforcement agencies, and cybersecurity organizations to share information about emerging fraud trends and tactics. Collective intelligence enhances your ability to stay ahead of evolving threats.

N. Secure Development Practices: Integrate secure development practices into software and application development processes. This includes regular security assessments, code reviews, and adherence to best practices for mitigating vulnerabilities.
O. Identity Verification Solutions: Utilize robust identity verification solutions to ensure that individuals accessing your systems or services are who they claim to be. This can involve document verification, biometric authentication, or knowledge-based authentication.
P. Customer Authentication Controls: Provide customers with controls to manage and customize their authentication settings. This empowers users to set preferences for security features and receive alerts for suspicious activities.
Q. Customer Education and Awareness: Educate customers about common fraud tactics and best practices for protecting their accounts. Promote awareness of phishing emails, social engineering attempts, and the importance of secure password practices.
R. Create a culture of accountability and transparency: Foster a positive workplace culture where ethical behavior is valued and rewarded. Make it easy and safe for employees to report suspicious behavior.
S. Incident Response Plan: Have a robust incident response plan in place. In the event of fraud, the organization should be prepared to respond swiftly to minimize damage, gather evidence, and take necessary legal steps.
T. Customer Support and Communication: Maintain effective customer support channels to address inquiries and reports of potential fraud. Clear communication with customers during incidents helps build trust and confidence in your organization’s commitment to security.
U. Continuous Monitoring and Adaptation: Implement continuous monitoring of your fraud prevention measures. Regularly reassess and adapt strategies based on the evolving threat landscape and changes in the digital environment.
Building fraud resilience in the digital era is an ongoing process that requires a combination of technological measures, user education, and strategic planning. By adopting a proactive and adaptive approach, organizations can strengthen their defenses against digital fraud and protect both their assets and the trust of their customers.
https://m.grazitti.com/blog/building-cyber-resilience-in-the-age-of-digital-transformation/
https://www.pasai.org/blog/2020/5/29/cybersecurity-building-digital-resilience-in-a-virtual-world
https://www.ey.com/en_ao/how-digital-transformation-increases-consumer-and-retail-fraud-risks
