Building Strategic Cybersecurity Capabilities: A Foundation for Resilient Organizations
In an era dominated by digital connectivity, the importance of robust cybersecurity capabilities cannot be overstated.
As cyber threats continue to evolve in sophistication and frequency, organizations must go beyond mere defense and actively cultivate strategic cybersecurity capabilities.
A. Understanding the Cybersecurity Landscape
The first step in building strategic cybersecurity capabilities involves gaining a deep understanding of the current cybersecurity landscape. This includes being aware of the types of threats that exist, from malware and phishing to more advanced persistent threats (APTs) and ransomware attacks, as well as understanding the potential vulnerabilities within your own organization. Keeping abreast of the latest developments in cybersecurity technology and threat intelligence is crucial.
B. Risk Assessment and Management
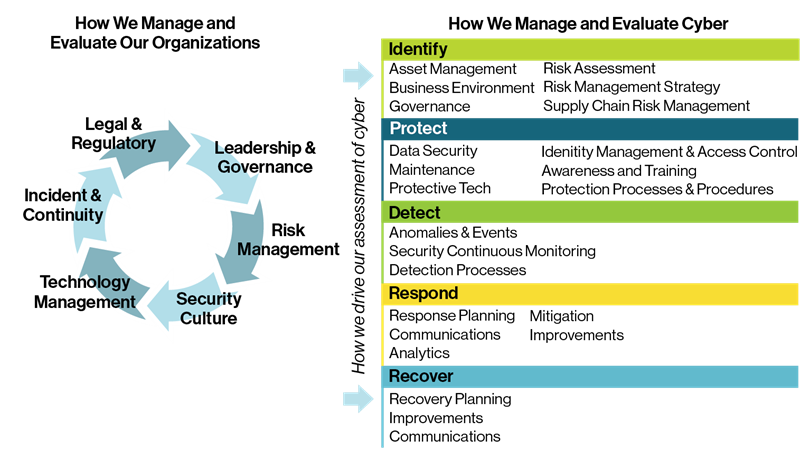
Organizations must identify and prioritize potential threats, vulnerabilities, and the potential impact of a security breach. By understanding their risk landscape, businesses can tailor their cybersecurity strategies to focus on the most critical areas, ensuring resource allocation aligns with the level of risk.
C. Developing a Cybersecurity Framework
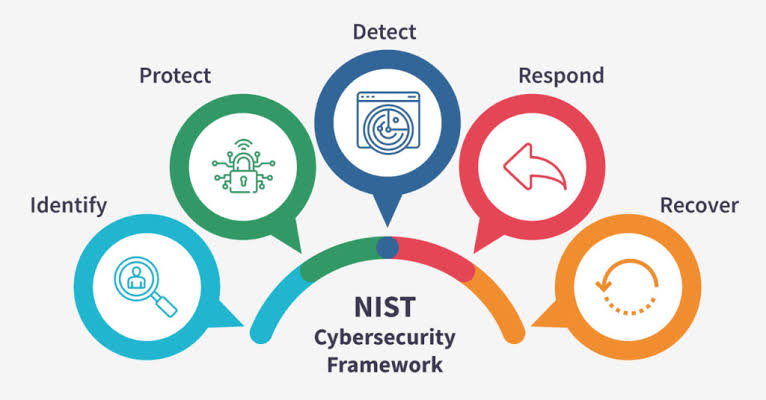
A well-structured cybersecurity framework is essential for orchestrating the various components of cybersecurity strategy. Frameworks such as NIST (National Institute of Standards and Technology) provide guidelines for managing and reducing cybersecurity risks. Tailoring these frameworks to fit the specific needs and nuances of your organization is vital. It involves setting up the right balance between preventive, detective, and responsive measures.
D. Continuous Monitoring and Threat Intelligence
A strategic cybersecurity stance necessitates continuous monitoring of networks, systems, and data. Implementing real-time threat intelligence allows organizations to stay ahead of emerging threats. By actively collecting and analyzing data on potential risks, cybersecurity teams can adapt their defense mechanisms, fortifying their capabilities against new and evolving cyber threats.
E. Investing in Technology and Talent
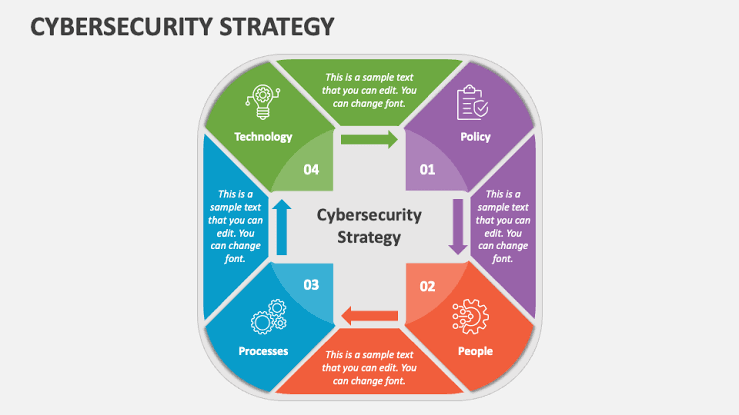
Strategic cybersecurity cannot be achieved without the right mix of technology and talent. Investing in advanced cybersecurity technologies—such as AI and machine learning for threat detection, blockchain for secure transactions, and zero-trust architectures—is key to enhancing your security posture. Equally important is investing in skilled cybersecurity professionals who can effectively manage and navigate the cybersecurity landscape. Continuous training and education are vital to keep up with the rapid pace of change in cyber threats and defenses.
F. Establishing a Culture of Cybersecurity Awareness
Building cybersecurity capabilities goes beyond technology and processes; it requires a cultural shift towards cybersecurity awareness at all levels of the organization. Regular training sessions, simulations, and awareness campaigns can help cultivate a culture where every employee understands their role in maintaining cybersecurity and is equipped to recognize and respond to threats.
G. Collaborating and Sharing Intelligence
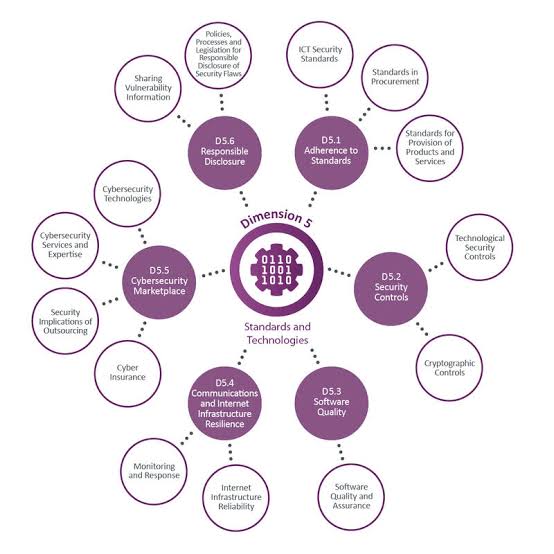
Cyber threats are constantly evolving, and so are the strategies to combat them. Collaboration among businesses, governments, and cybersecurity agencies can foster a more resilient cybersecurity ecosystem. Sharing threat intelligence and best practices can help organizations stay ahead of adversaries and better prepare for emerging threats.
H. Regularly Reviewing and Updating Cybersecurity Practices
Regular audits and reviews of cybersecurity practices allow organizations to adapt to new threats and technological advancements. This includes revisiting risk assessments, updating policies, and continuously improving incident response strategies.
I. Incident Response Planning
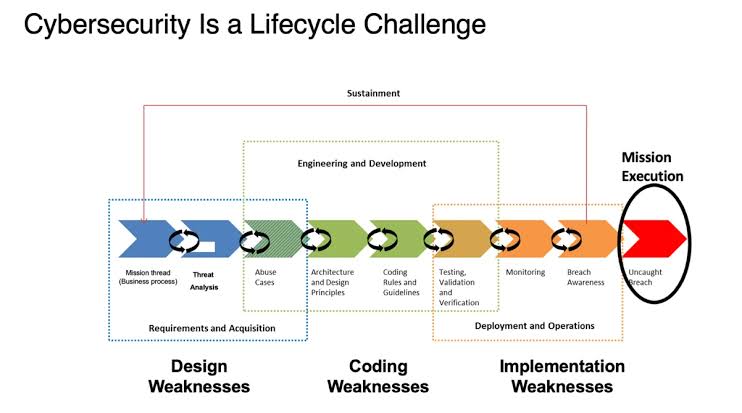
No organization is immune to cyber incidents. Developing a robust incident response plan is crucial for minimizing the impact of a security breach. This plan should outline clear procedures, roles, and responsibilities to ensure a swift and coordinated response. Regularly testing and updating the incident response plan ensures its effectiveness in the face of ever-changing cyber threats.
J. Cybersecurity Training and Awareness
Human error remains a significant contributor to cybersecurity incidents. Building strategic cybersecurity capabilities involves investing in ongoing training programs to educate employees about security best practices. A workforce that is well-informed and vigilant serves as a valuable line of defense against phishing, social engineering, and other human-centric cyber threats.
K. Technology Integration and Innovation
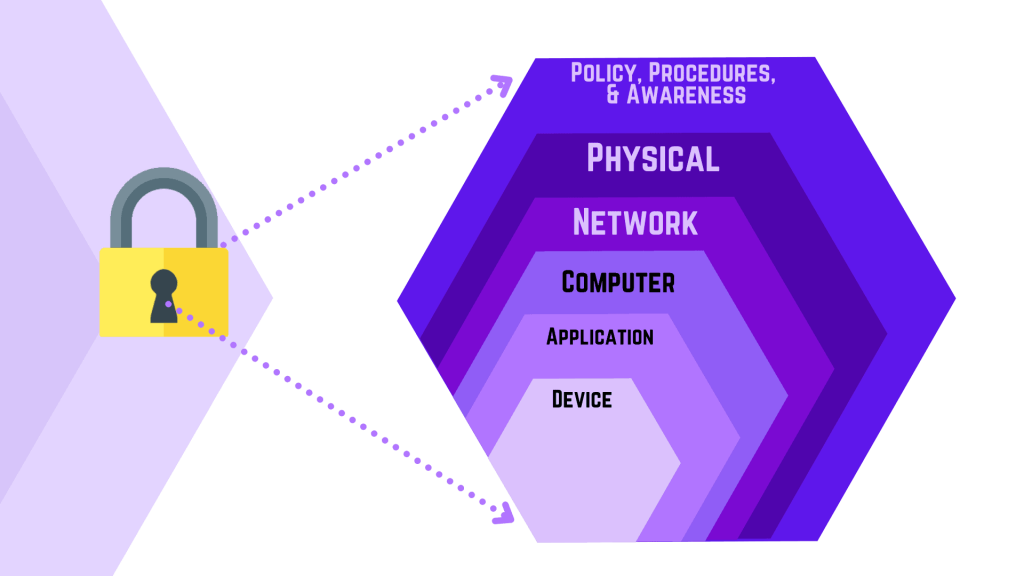
Embracing cutting-edge technologies is integral to strategic cybersecurity capabilities. Advanced tools powered by artificial intelligence, machine learning, and automation can enhance threat detection, response times, and overall resilience. Regularly evaluating and integrating innovative technologies ensures that cybersecurity capabilities stay ahead of evolving cyber threats.
L. Regulatory Compliance
Adhering to regulatory requirements is not just a legal obligation but a crucial component of strategic cybersecurity. Compliance frameworks provide guidelines for securing sensitive data and ensuring the privacy of individuals. Aligning cybersecurity strategies with applicable regulations helps organizations build a resilient security infrastructure while avoiding legal and reputational risks.
M. Continuous Education
Providing ongoing education on the latest cyber threats and safe practices empowers employees to contribute effectively to the organization’s cybersecurity.
N. Simulated Cyberattack Exercises
Conducting mock cyberattack drills can test the organization’s readiness and improve response times to actual cybersecurity incidents.
Conclusion
Building strategic cybersecurity capabilities is an ongoing process that requires a proactive and multifaceted approach. By integrating risk management, holistic frameworks, continuous monitoring, incident response planning, employee training, collaboration, technology innovation, and regulatory compliance, organizations can establish a robust cybersecurity posture.
In an ever-changing digital landscape, strategic cybersecurity capabilities are not just a necessity; they are a competitive advantage that safeguards the integrity, confidentiality, and availability of critical assets.
Further references
Cybersecurity Strategy – Seven Steps to Develop a Strong Plan – Sprintzeal.com
Spiceworkshttps://www.spiceworks.com › ampA Practical Guide to 8 Core Cybersecurity Capabilities
ENISAhttps://www.enisa.europa.eu › …PDFCyber SeCurity Strategy – ENISA
McKinsey & Companyhttps://www.mckinsey.com › cybers…Cybersecurity
