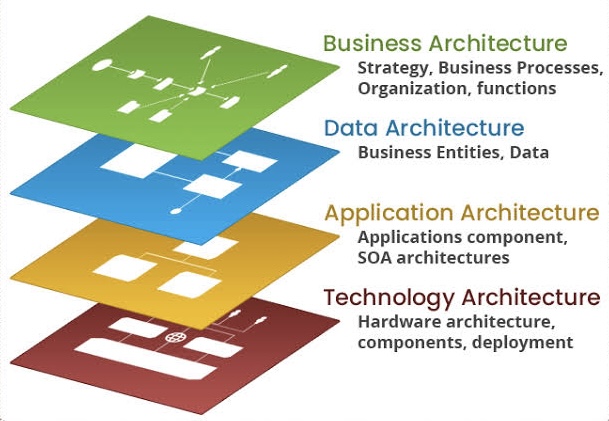
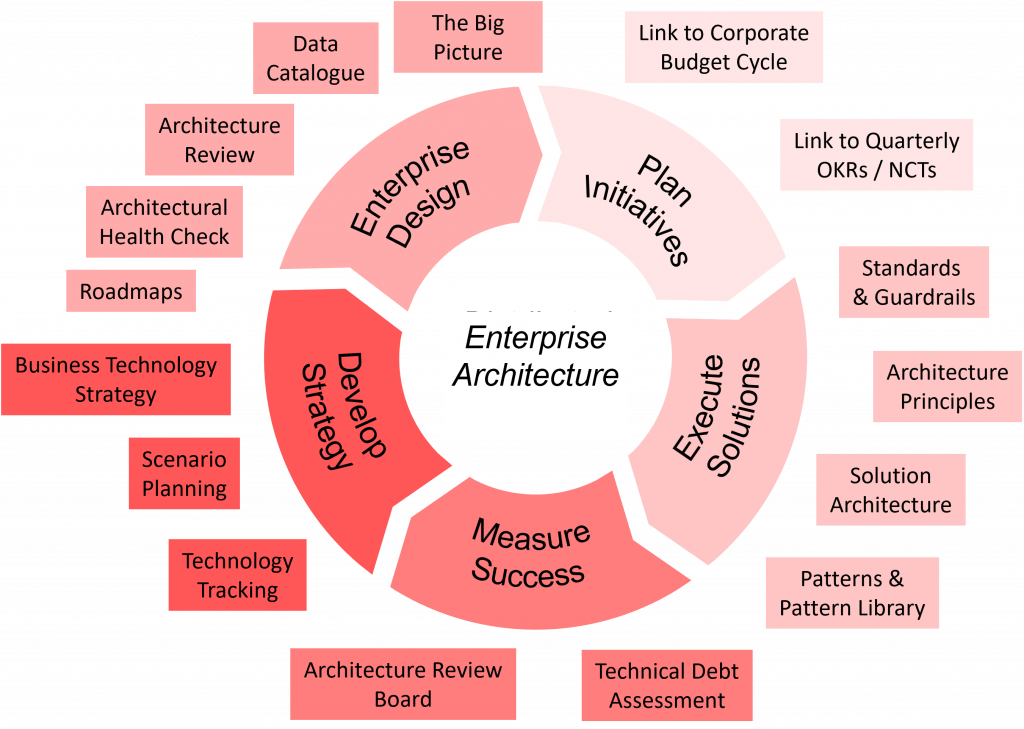
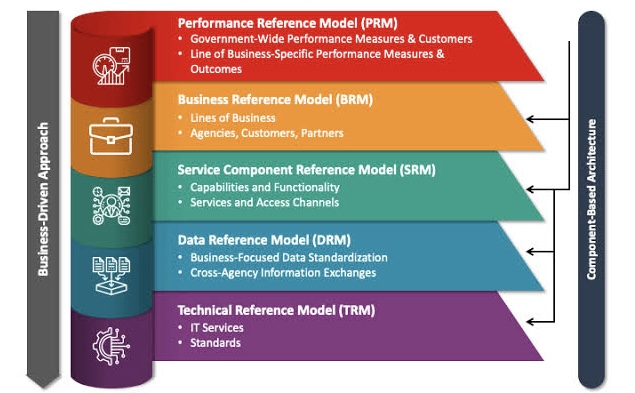
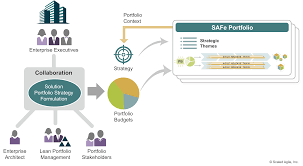
Exploring Edge Al: The Future of On-Device Intelligence
In the rapidly evolving world of technology, staying updated with the latest and most efficient devices is not just a luxury, but a necessity for those looking to leverage cutting-edge features.
One of the most significant advancements in recent times has been the integration of Artificial Intelligence (AI) directly into personal gadgets and devices.
As we venture deeper into the AI frontier, understanding the impacts and advantages of on-device AI becomes essential when considering a device refresh.
i. The Rise of On-Device AI
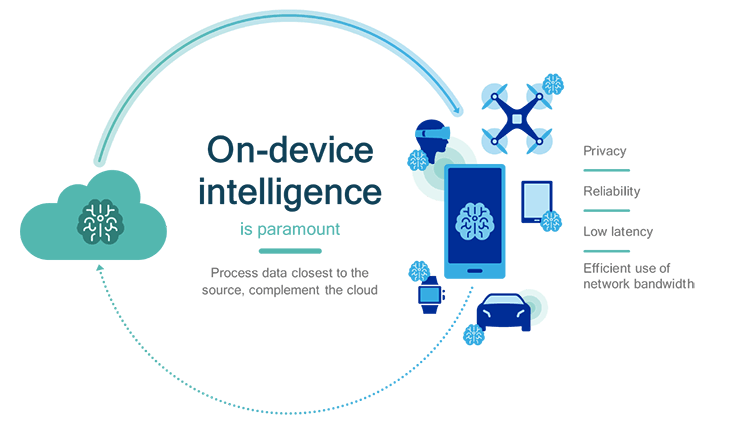
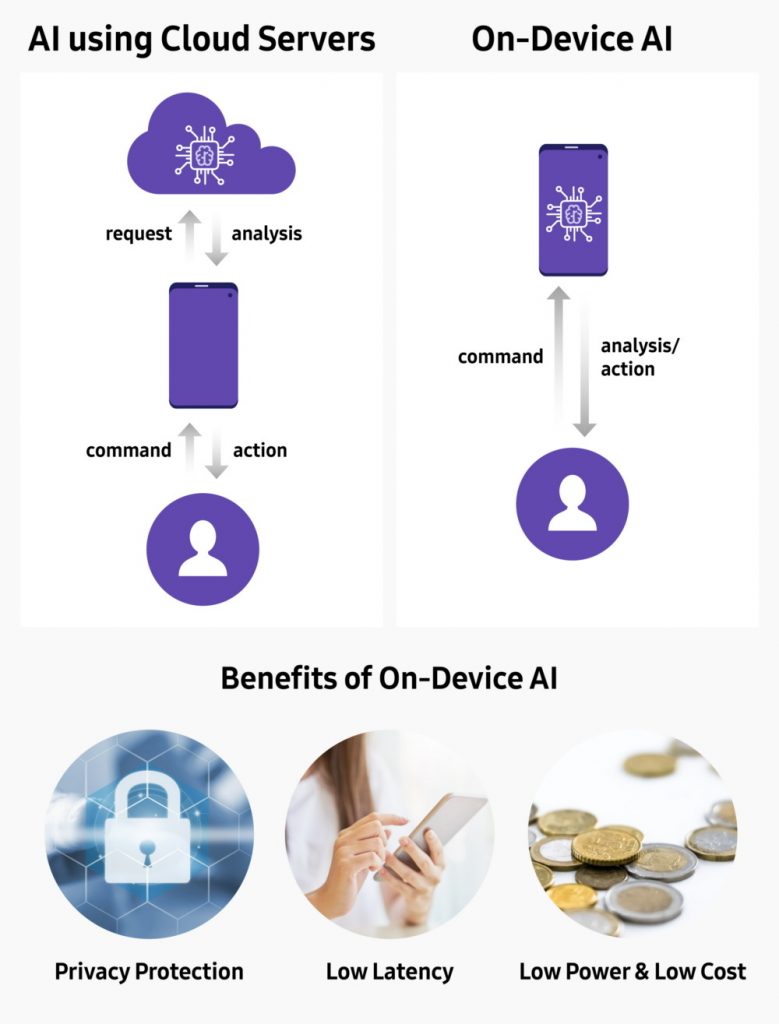
Traditionally, AI processes have been reliant on cloud computing, where data is sent to remote servers for analysis. While effective, this approach has limitations such as latency, privacy concerns, and dependency on internet connectivity. On-device AI, on the other hand, brings AI capabilities directly to your device, enabling faster processing and greater privacy.
ii. What is On-Device AI?
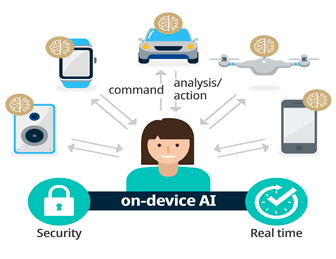
On-device AI refers to the capability of a device to process and execute AI algorithms locally, without needing to connect to the cloud or external servers. This method of processing is made possible by embedding AI processing capabilities directly into the device’s hardware. Key examples of on-device AI include smartphones that use AI for enhancing photos, voice assistants that process requests directly on the device, and wearables that provide real-time health monitoring and advice.
iii. Why On-Device AI Matters

On-device AI offers several advantages:
o Faster Performance: Processing data locally reduces reliance on cloud servers, leading to faster response times.
o Improved Privacy: Sensitive data stays on the device, potentially enhancing user privacy.
o Offline Functionality: On-device AI enables certain AI features to function even without an internet connection.
o Energy Efficiency: Local processing consumes less power compared to constantly transmitting data to remote servers, leading to improved battery life.
iv. Benefits of On-Device AI
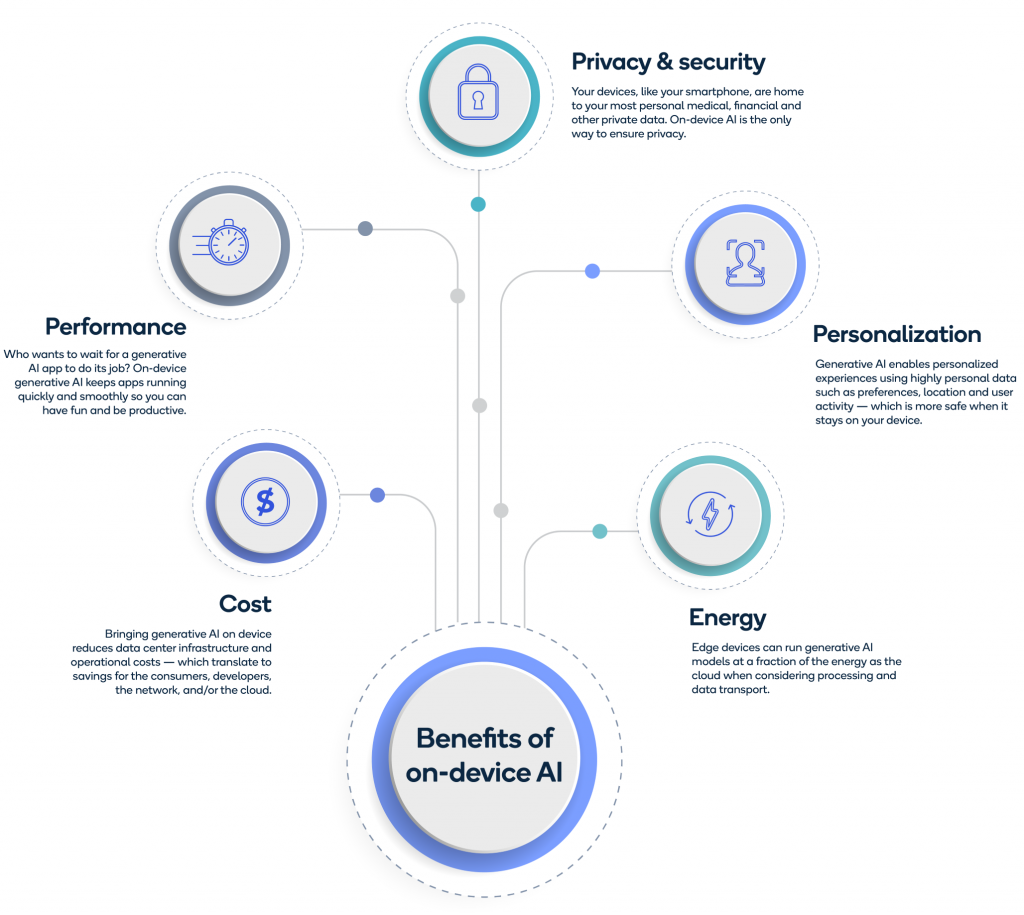
The introduction of AI capabilities directly on devices has several compelling advantages:
A. Privacy and Security: By processing data locally, devices can significantly reduce the amount of personal data that must be sent to the cloud, minimizing privacy risks.
B. Speed and Reliability: On-device processing eliminates the dependency on internet connectivity and server response times, offering faster and more reliable performance.
C. Efficiency: Local data processing reduces the energy required to transmit data to and from the cloud, which can extend battery life and reduce bandwidth usage.
v. The Impact on Device Refresh

With on-device AI becoming increasingly important, here’s how it can influence your decision to upgrade a device:
o Evaluating Your Needs: Consider how you’ll leverage AI features. If on-device AI is crucial for your tasks, a newer device with a powerful processor and dedicated AI hardware (like an NPU) might be necessary.
o Future-Proofing: Newer devices are better equipped to handle the evolving demands of on-device AI applications. Upgrading now ensures you have the processing power for future advancements.
o Balancing Needs and Budget: If basic AI functionality suffices, you might not need the latest device. However, for power users who rely heavily on AI features, a refresh might be prudent.
vi. Applications of On-Device AI
A. Voice Assistants: On-device AI powers voice assistants like Siri, Google Assistant, and Alexa, allowing them to understand and respond to commands without relying solely on cloud processing.
B. Image Recognition: On-device AI enables smartphones to recognize objects, faces, and scenes directly from the camera app, without requiring an internet connection.
C. Health Monitoring: Wearable devices equipped with on-device AI can track health metrics such as heart rate, sleep patterns, and physical activity in real-time, providing valuable insights to users.
D. Autonomous Vehicles: On-device AI plays a crucial role in autonomous vehicles, enabling them to make split-second decisions based on sensor data without relying on cloud connectivity.
vii. Considerations for Device Refresh

When deciding whether it’s time for a device update focused on enhanced AI capabilities, here are several key considerations:
A. Current Device Limitations: Analyze whether your current device supports the AI-driven tasks that are most relevant to your needs. Does your smartphone struggle with voice recognition, or does your smartwatch lag when processing health data?
B. AI-Enhancement Features: Investigate what AI features the new device offers. For instance, newer smartphones might offer advanced photography enhancements like better night mode or refined AI-based image stabilization.
C. Cost vs. Benefit: Evaluate the cost of the new device against the benefits of the AI features. High-end devices often come at a premium, so consider whether the AI enhancements provide sufficient value for you.
D. Ecosystem Compatibility: Ensure that the new device is compatible with other devices and systems you use. Seamless integration can enhance the overall experience and utility of on-device AI.
E. Privacy Policies: Review the device manufacturer’s privacy policies to understand how your data is handled and whether on-device AI processes sensitive information locally without transmitting it to external servers.
F. Performance: Evaluate the performance of on-device AI features on the device you’re considering. User reviews and benchmark tests can provide valuable insights into real-world performance.
G. Future-Proofing: With the rapid development of AI technology, consider choosing a device that is likely to receive updates and support over an extended period.
viii. When to Consider an Upgrade

Upgrading to a device with robust on-device AI capabilities might be ideal if:
o You experience lag or sluggishness in AI-powered apps.
o You value privacy and want more control over your data.
o Your work demands offline access to AI features.
ix. The Future of On-Device AI

The trajectory for on-device AI is set towards more personalized and intuitive interactions between humans and devices. Future devices are likely to offer even more sophisticated AI operations that can learn and adapt to individual user needs without compromising privacy or efficiency.
x. Conclusion

A device refresh driven by the desire to harness the power of on-device AI can significantly enhance both personal and professional productivity.
However, it requires a thoughtful analysis of what specific AI capabilities will meaningfully impact your daily device interactions.
Understanding these aspects will ensure that your investment into a new device with powerful AI features is both strategic and beneficial.
Whether for enhanced photography, smarter health monitoring, or seamless voice interactions, the latest in on-device AI is set to redefine our technological experiences.
xi. Further references
Canalyswww.canalys.comCanalys Insights – On-device AI and Samsung’s role in the future smart …
PCMaghttps://www.pcmag.com › … › AIMediaTek’s On-Device Generative AI Is the Fastest I’ve Seen
MIT Technology Reviewhttps://www.technologyreview.com › …On-Device AI – MIT Technology Review
The Vergewww.theverge.comI went to paradise to see the future of AI, and I’m more confused than ever