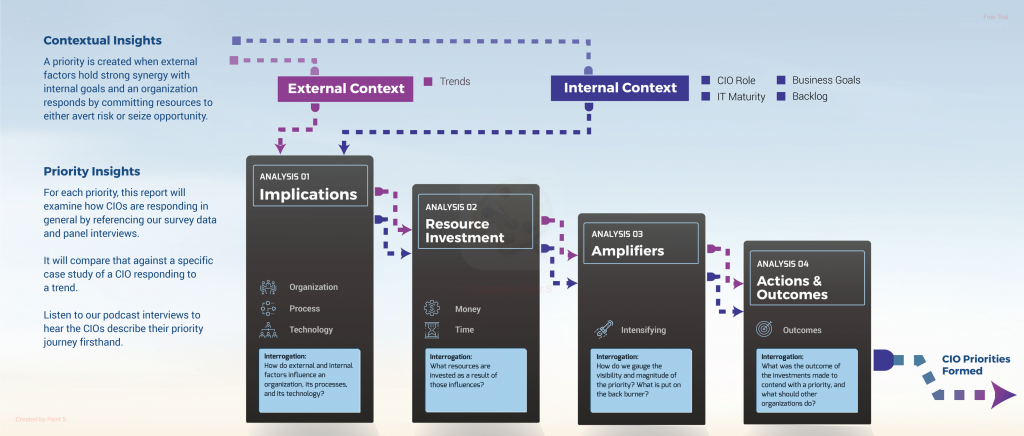
The Definitive Guide to Achieving CIO Success
In the rapidly evolving landscape of technology and business, the role of the Chief Information Officer (CIO) has never been more critical. The CIO is not just a technology leader but a strategic partner driving digital transformation, innovation, and business value. To navigate this complex environment and achieve success, CIOs need a comprehensive roadmap.
Here’s the ultimate guide to ensuring your success as a CIO.
A. Understand the Business Landscape
Align IT with Business Goals
The first step towards CIO success is understanding the business’s strategic goals and objectives. Align IT initiatives with these goals to ensure technology supports and drives business outcomes.
Develop Industry Knowledge
Stay updated with industry trends, challenges, and opportunities. This knowledge will enable you to anticipate changes and position your organization to leverage new technologies effectively.
B. Build a Strong IT Strategy
Create a Clear Vision
Develop a clear and compelling IT vision that aligns with the overall business strategy. Communicate this vision effectively to all stakeholders to ensure everyone is on the same page.
Implement a Robust IT Governance Framework
Establish governance structures to oversee IT investments, manage risks, and ensure compliance with regulations. This framework should facilitate decision-making and accountability.
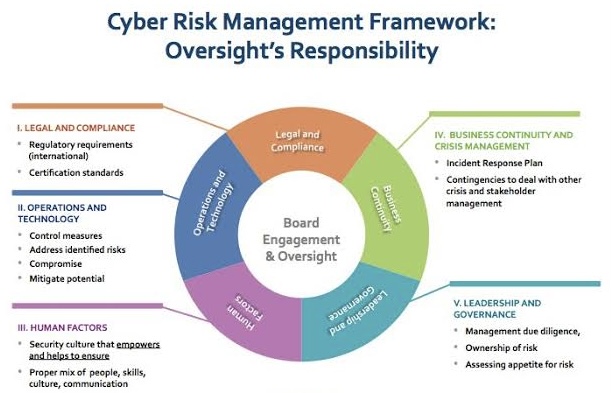
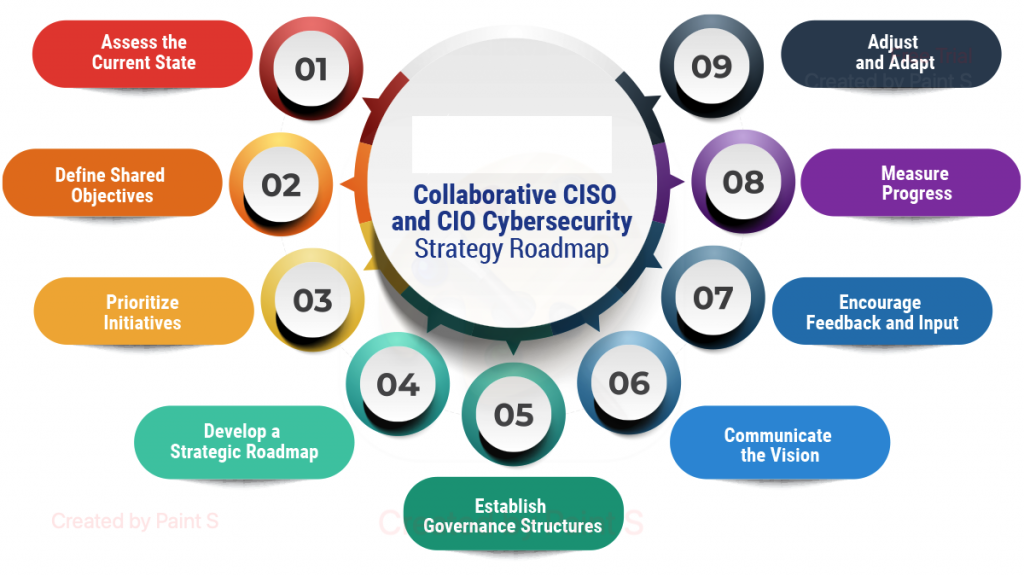
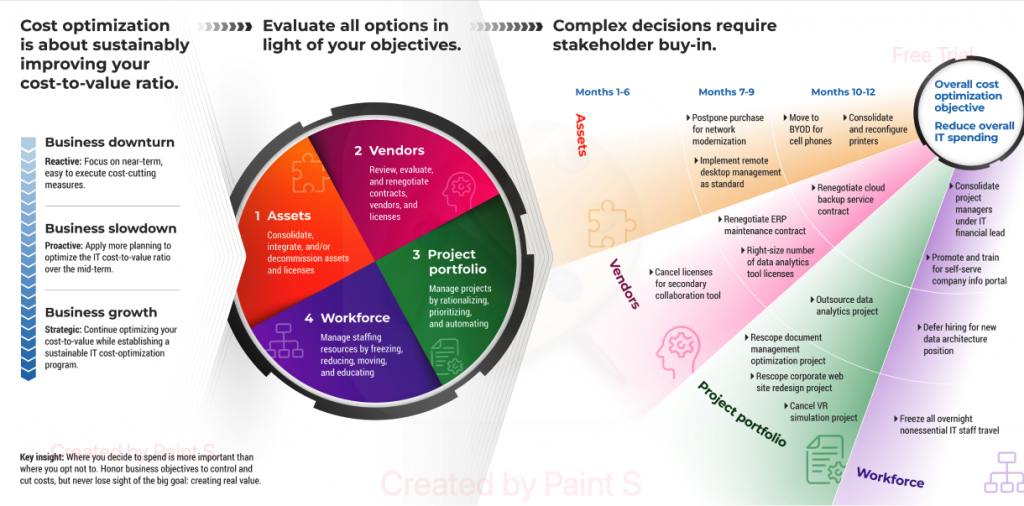
C. Focus on Cybersecurity
Prioritize Cybersecurity Measures
With increasing cyber threats, cybersecurity should be at the top of your agenda. Implement robust security measures, conduct regular audits, and stay ahead of emerging threats.
Foster a Security-Aware Culture
Educate employees about cybersecurity best practices and ensure they understand their role in protecting the organization’s digital assets. A security-aware culture can significantly reduce the risk of cyber incidents.
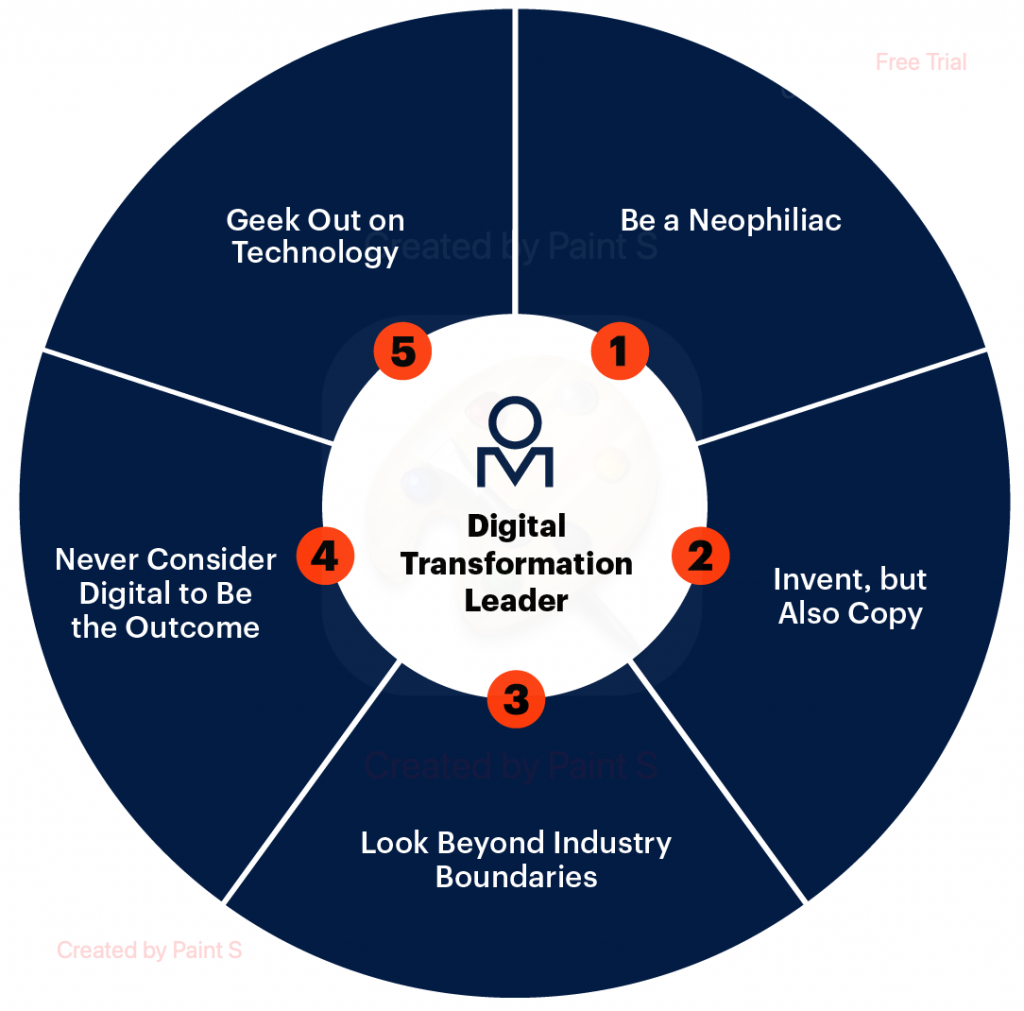
D. Embrace Digital Transformation
Drive Innovation
Encourage a culture of innovation within your IT team. Explore emerging technologies such as artificial intelligence, machine learning, blockchain, and the Internet of Things (IoT) to drive business innovation.
Streamline Processes
Leverage digital technologies to streamline business processes, enhance efficiency, and improve customer experiences. Focus on automation and process optimization to deliver value quickly.
E. Develop a Skilled IT Workforce
Invest in Talent Development
Ensure your team has the necessary skills and knowledge to handle the latest technologies. Invest in continuous learning and development programs to keep your workforce updated.
Foster Collaboration
Promote collaboration within the IT team and across other departments. A collaborative environment encourages the sharing of ideas and enhances problem-solving capabilities.
F. Leverage Data Analytics
Implement Data-Driven Decision Making
Utilize data analytics to gain insights into business performance, customer behavior, and market trends. Data-driven decision-making can significantly enhance business outcomes.
Ensure Data Quality and Integrity
Implement data governance practices to ensure data quality, integrity, and security. Reliable data is crucial for accurate analysis and informed decision-making.
G. Enhance Customer Experience

Focus on User-Centric IT Solutions
Develop IT solutions that enhance the customer experience. Understand customer needs and pain points to design solutions that provide real value.
Implement Omni-channel Strategies
Ensure seamless integration across various customer touch-points. An omni-channel approach provides a consistent and personalized customer experience.
H. Manage Change Effectively
Develop Change Management Capabilities
Change is constant in the IT world. Develop robust change management capabilities to handle transitions smoothly. Communicate changes effectively and provide the necessary support to those affected.
Monitor and Measure Impact
Regularly monitor the impact of IT initiatives and changes. Use metrics and KPIs to measure success and identify areas for improvement.
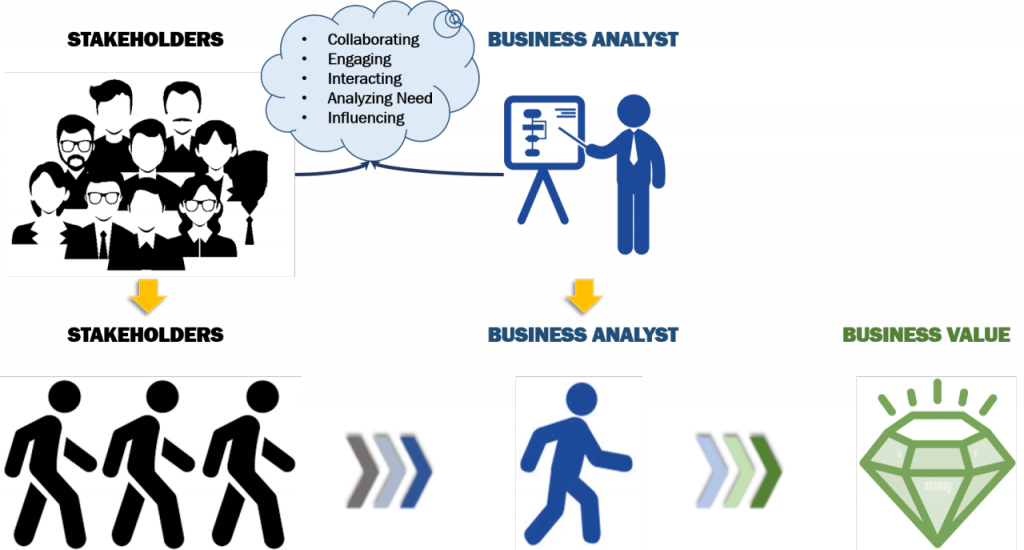
I. Cultivate Strong Relationships with Stakeholders
Communicate Effectively
Maintain open and transparent communication with all stakeholders. Regular updates and clear communication help build trust and ensure alignment with business objectives.
Demonstrate IT Value
Showcase the value IT brings to the organization. Use success stories, case studies, and metrics to demonstrate how IT initiatives contribute to business success.
J. Stay Agile and Adaptive
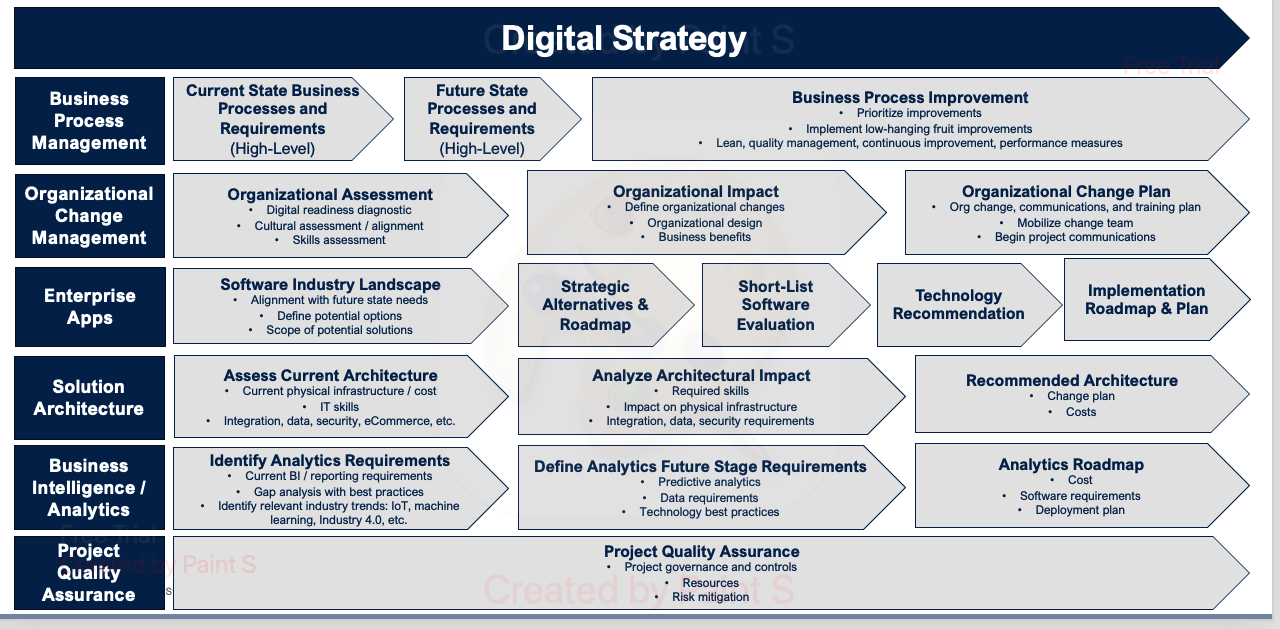
Adopt Agile Practices
Implement agile methodologies to enhance flexibility and responsiveness. Agile practices enable IT teams to deliver value quickly and adapt to changing business needs.
Encourage Continuous Improvement
Foster a culture of continuous improvement. Regularly review processes, solicit feedback, and make necessary adjustments to enhance performance.
Conclusion

Success as a CIO requires a strategic approach, a focus on innovation, and a commitment to driving business value through technology. By following this ultimate roadmap, CIOs can navigate the complexities of the modern business environment, foster a culture of continuous improvement, and lead their organizations towards sustained success. Embrace these strategies, and you’ll be well on your way to achieving CIO excellence.
Further References
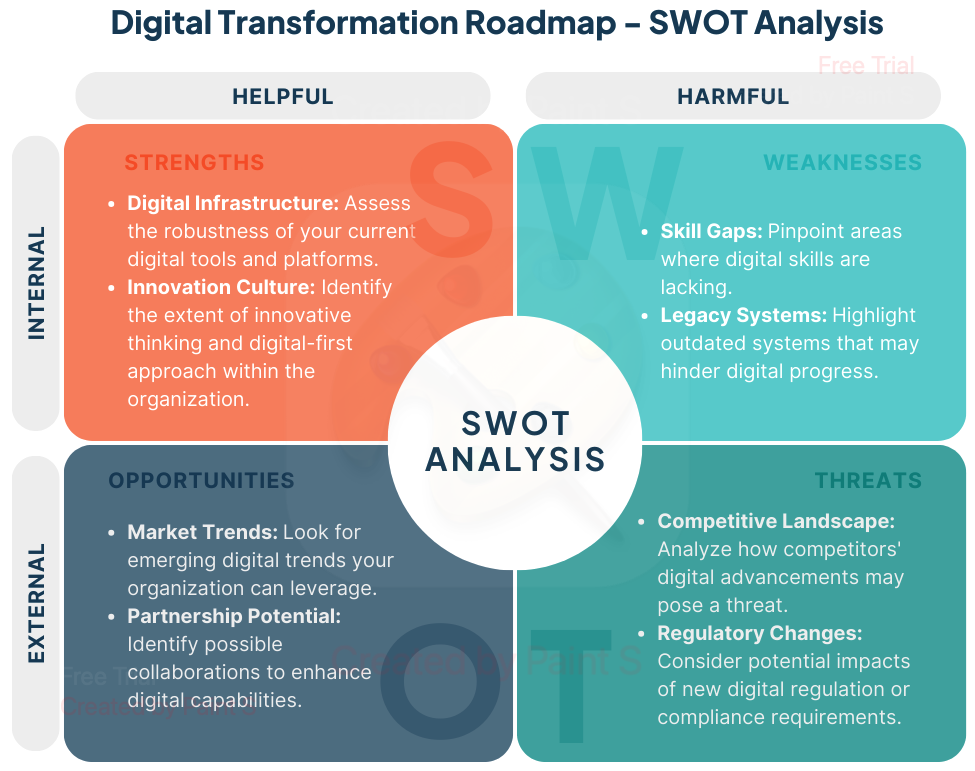
A Digital Transformation Roadmap for Every CIO
Transitioning to the CIO roleDeloittehttps://www2.deloitte.com › focus › cio-role-transition
The CIO’s Playbook for Operational Excellence in 2024 | enreapenreap.comhttps://www.enreap.com