IT Governance: A Roadmap with COBIT
In the modern digital landscape, effective governance of information technology (IT) has emerged as a critical component for businesses striving to achieve strategic objectives, maintain compliance, and harness technology as a driver of value creation. COBIT (Control Objectives for Information and Related Technologies) stands at the forefront of IT governance frameworks by providing extensive guidelines and tools aimed at optimizing the delivery of enterprise IT.
i. The Significance of EGIT
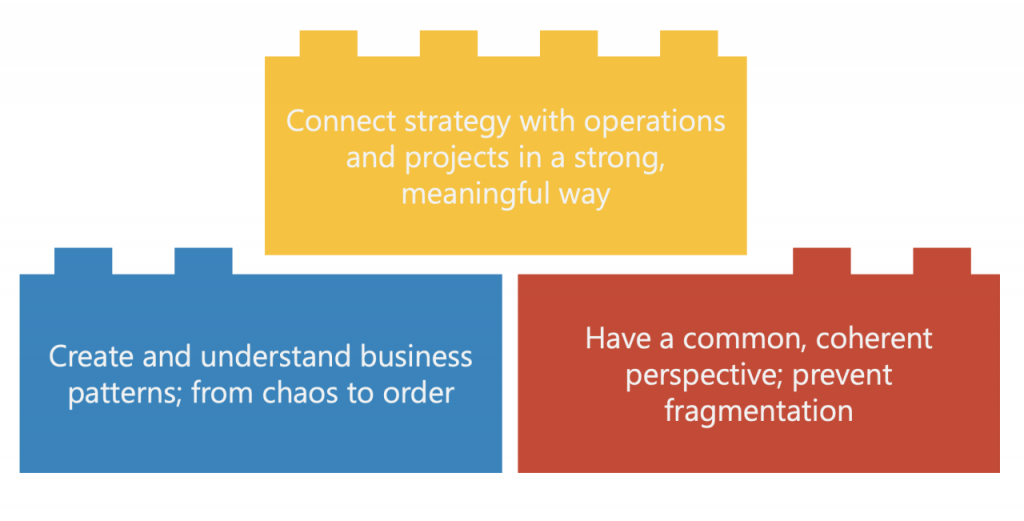
Enterprise Governance of IT encompasses the frameworks and processes by which the use of Information and Technology is directed and controlled in an organization. It aligns IT with strategic business goals, ensuring that organizations achieve their objectives through effective decision-making and resource optimization. EGIT bridges the gap between business and IT, focusing on risk management, performance measurement, and value delivery from IT investments.
ii. Introduction to COBIT
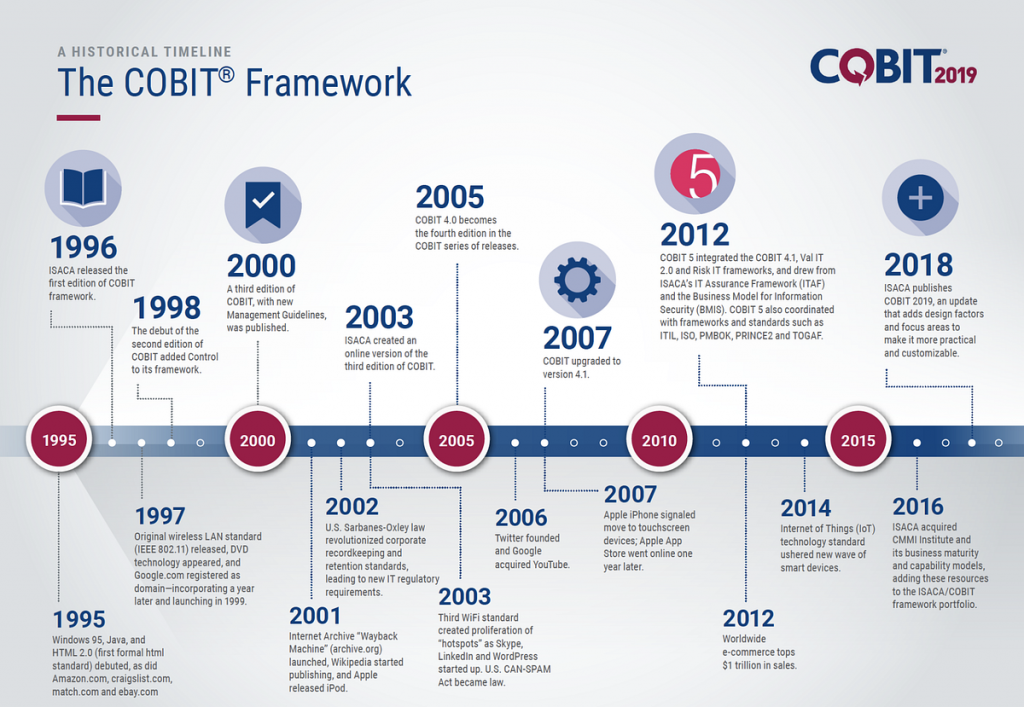
COBIT, developed by ISACA (Information Systems Audit and Control Association), is a comprehensive framework that aids organizations in achieving their IT governance goals. The latest version, COBIT 2019, builds upon its predecessors by integrating governance principles, processes, and objectives that align IT operations with business strategy. COBIT facilitates a holistic approach to IT management, ensuring that IT serves enterprise needs effectively and efficiently.
COBIT, developed by ISACA, Key components of COBIT include:
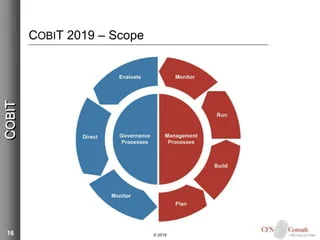
A. Framework: The COBIT framework offers a comprehensive structure for IT governance and management, encompassing all aspects of IT from planning and organization to implementation and monitoring.
B. Processes: COBIT outlines a set of processes and practices that organizations should follow to ensure effective IT governance. These processes cover areas such as risk management, resource management, and performance measurement.
C. Controls: Specific control objectives are provided for each IT process to guide the development of robust IT controls that mitigate risks and ensure compliance.
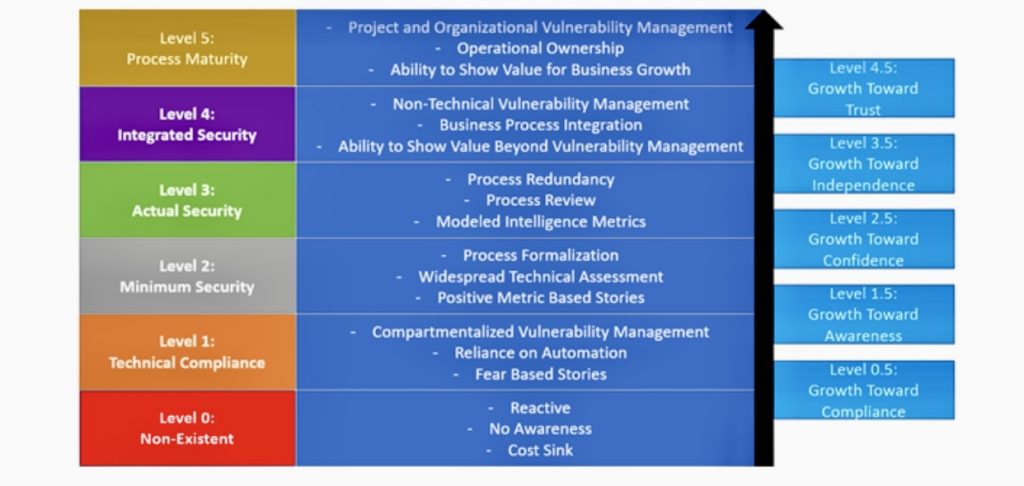
D. Maturity Models: COBIT includes maturity models to help organizations assess their current IT governance capabilities and identify areas for improvement.
E. Metrics: Performance metrics are used to measure the effectiveness of IT governance practices and ensure continuous improvement.
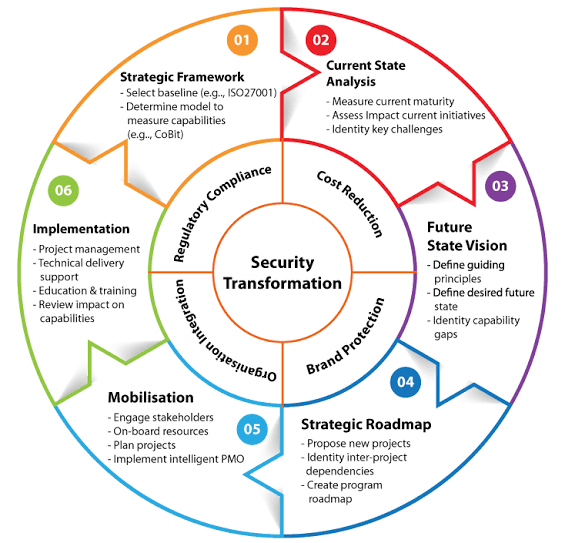
iii. COBIT: A Framework for IT Governance
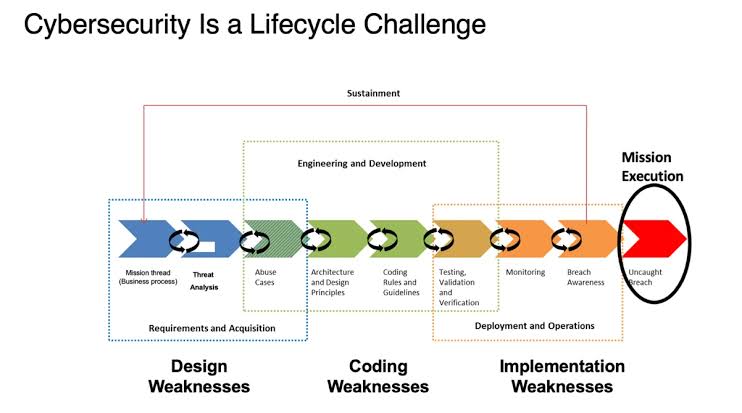
COBIT is a good practice framework developed by ISACA (Information Systems Audit and Control Association) that provides a comprehensive set of guidelines for IT governance. It offers a structured approach to aligning IT with business strategy, managing IT resources effectively, and ensuring compliance with regulations. COBIT is divided into five high-level processes:
- Plan and Organize: Defines the strategic direction for IT and ensures it aligns with business goals.
- Acquire and Implement: Focuses on the acquisition, development, and implementation of IT solutions.
- Deliver, Service and Support: Ensures the efficient and effective delivery of IT services to support business processes.
- Monitor and Evaluate: Provides a framework for monitoring IT performance and evaluating its effectiveness against business goals.
- Assess and Optimize: Focuses on continuous improvement by identifying opportunities to optimize IT processes and controls.
iv. Building Blocks of COBIT
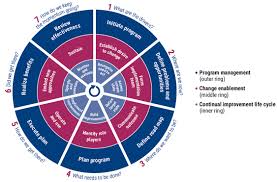
COBIT is structured around several key principles and enablers that form the building blocks of effective IT governance:
A. Meeting Stakeholder Needs: COBIT ensures that IT governance aligns with the needs and expectations of all stakeholders, including customers, employees, and shareholders.
B. End-to-End Governance: The framework covers all aspects of IT governance, from strategic planning to operational management, ensuring a holistic approach.
C. Applying a Single Integrated Framework: COBIT integrates with other standards and frameworks, such as ITIL and ISO/IEC 27001, providing a unified approach to IT governance.
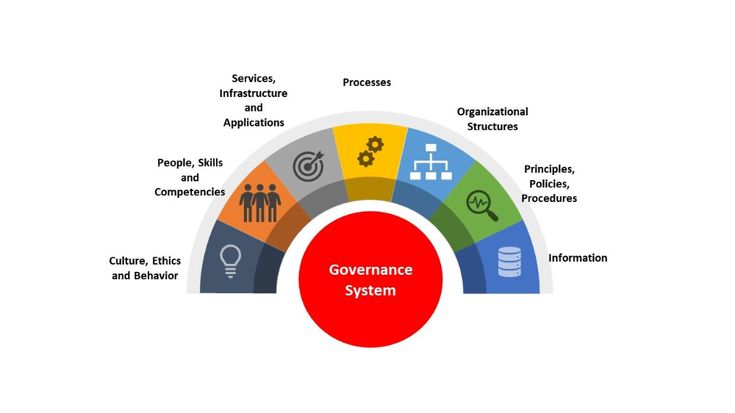
D. Enabling a Holistic Approach: The framework emphasizes the importance of considering all enablers of IT governance, including organizational structures, processes, culture, and information.
E. Separating Governance from Management: COBIT clearly distinguishes between governance and management, ensuring that strategic direction and oversight are separated from operational execution.
COBIT’s structure is composed of several essential building blocks:
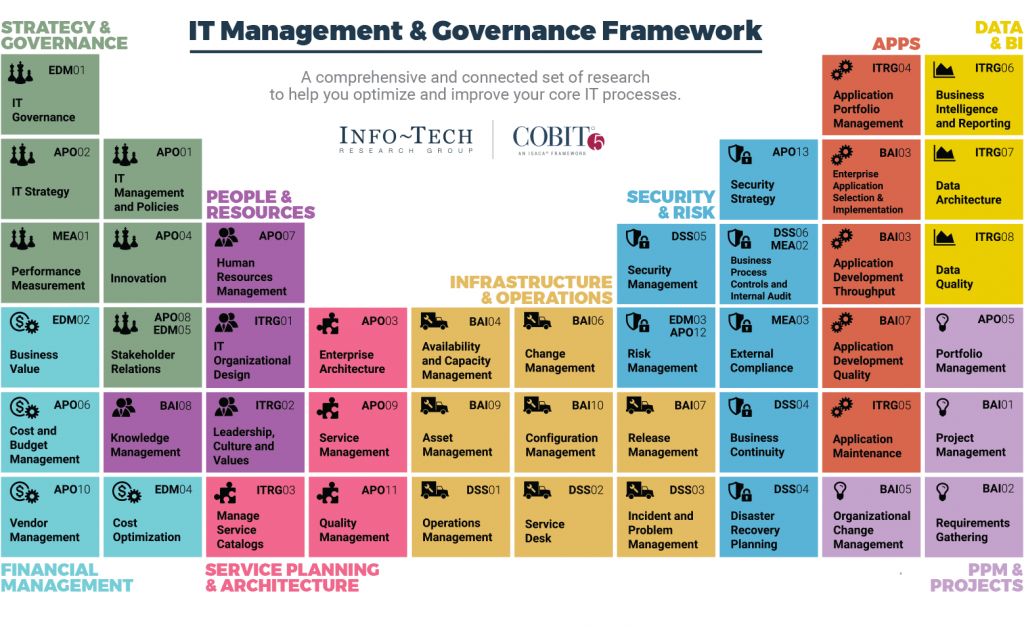
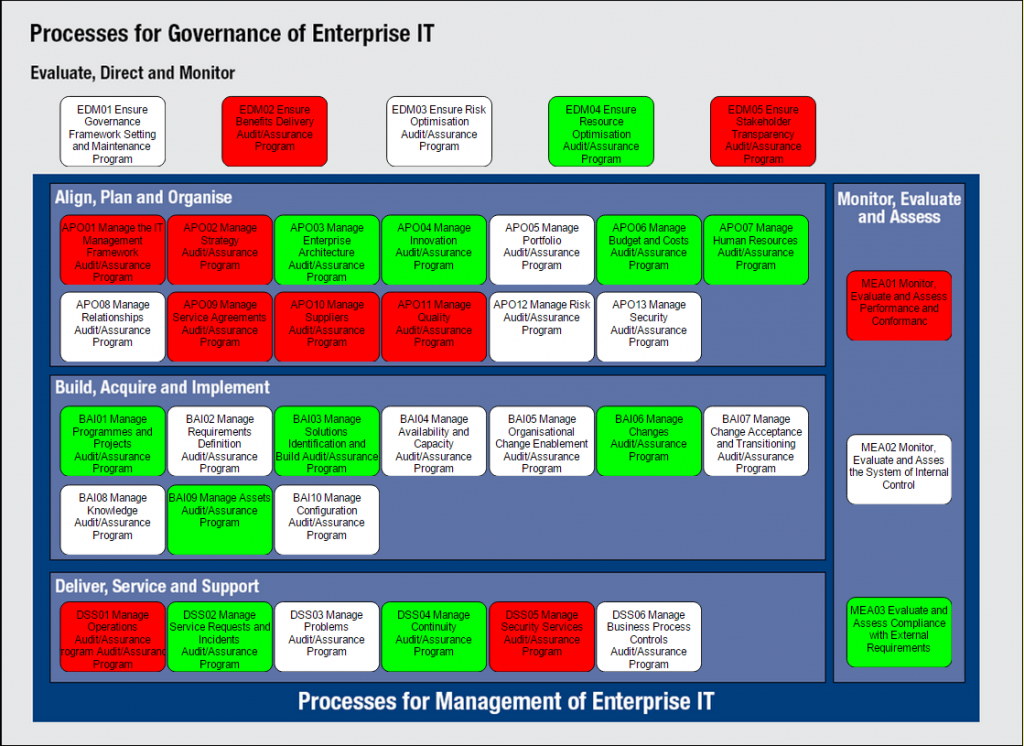
A. Governance and Management Objectives: COBIT delineates 40 governance and management objectives that span across five domains:
o Evaluate, Direct, and Monitor (EDM): Focuses on aligning IT strategy with business objectives.
o Align, Plan, and Organize (APO): Encompasses strategic planning and project management.
o Build, Acquire, and Implement (BAI): Deals with the development and implementation of IT solutions.
o Deliver, Service, and Support (DSS): Concerns day-to-day IT operations and service delivery.
o Monitor, Evaluate, and Assess (MEA): Involves performance measurement and compliance monitoring.
B. Design Factors: These influence the tailoring of COBIT to specific organizational contexts and include factors such as enterprise strategy, organizational environment, risk profile, and compliance requirements.
C. Governance and Management Framework: This comprises a set of practices, principles, and mechanisms that guide and support the governance of enterprise IT (GEIT). It integrates components like policies, procedures, structures, and culture.
D. Performance Management: COBIT incorporates a performance management framework which utilizes a balanced set of metrics and maturity models to gauge the effectiveness and efficiency of IT governance practices.
v. The Role of COBIT in Enterprise Governance
COBIT facilitates the harmonization of IT goals with enterprise objectives, ensuring that IT investments generate value and support business innovation. Key roles of COBIT in enterprise governance include:
o Strategic Alignment: Ensuring that IT strategies and initiatives are in congruence with business strategies and objectives.
o Risk Management: Identifying, assessing, and managing IT-related risks to an acceptable level.
o Resource Optimization: Efficient and effective use of IT resources, including people, processes, infrastructure, and information.
o Value Delivery: Ensuring that IT initiatives deliver benefits in alignment with business priorities.
o Performance Measurement: Establishing metrics and management systems to measure, monitor, and improve IT performance and contributions to enterprise goals.
vi. COBIT as a Building Block for Research
COBIT’s well-defined structure, comprehensive coverage of IT governance topics, and global recognition make it a valuable foundation for research in enterprise governance of IT. Here are some potential research opportunities based on COBIT:
o Impact of COBIT on Business Performance: Investigate the correlation between implementing COBIT and improved business performance metrics such as revenue, efficiency, and customer satisfaction.
o COBIT Adoption in Different Industries: Analyze how COBIT is adopted and adapted in different industries with varying IT needs and regulatory environments.
o Integrating COBIT with Other Frameworks: Explore how COBIT can be integrated with other relevant frameworks, such as ITIL (IT Infrastructure Library) or Project Management Institute (PMI) methodologies, for a more holistic approach to IT governance.
o COBIT and Emerging Technologies: Examine how COBIT can be adapted to address the challenges and opportunities presented by emerging technologies like cloud computing, artificial intelligence, and the Internet of Things (IoT).
o The Future of COBIT: Research how COBIT can evolve to remain relevant in the face of continuous changes in technology and business practices.
vii. Research Opportunities in COBIT and IT Governance

Despite the comprehensive nature of COBIT, the dynamic and ever-evolving IT landscape opens a plethora of research opportunities:
A. Integration with Emerging Technologies: Investigating how COBIT can be adapted to govern new technological paradigms such as Artificial Intelligence (AI), Internet of Things (IoT), and blockchain.
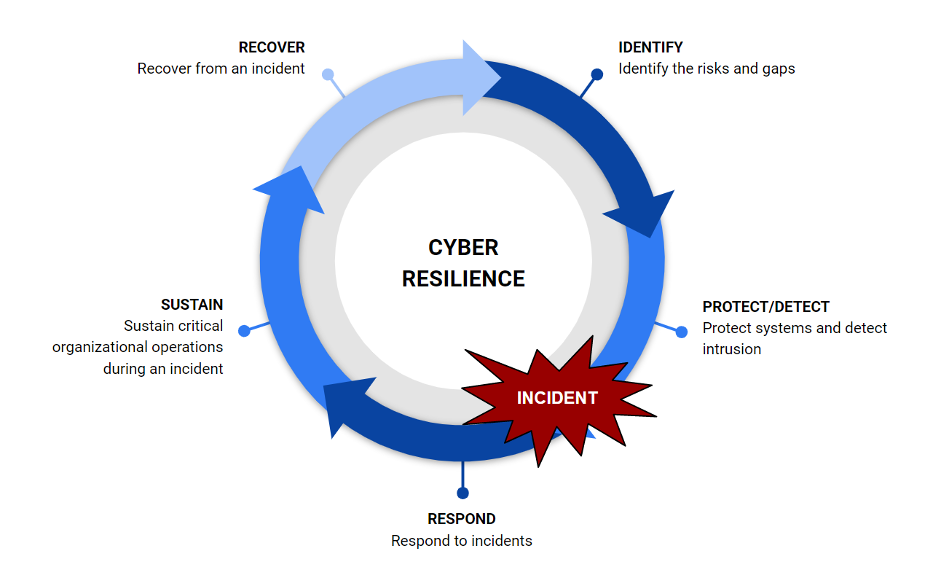
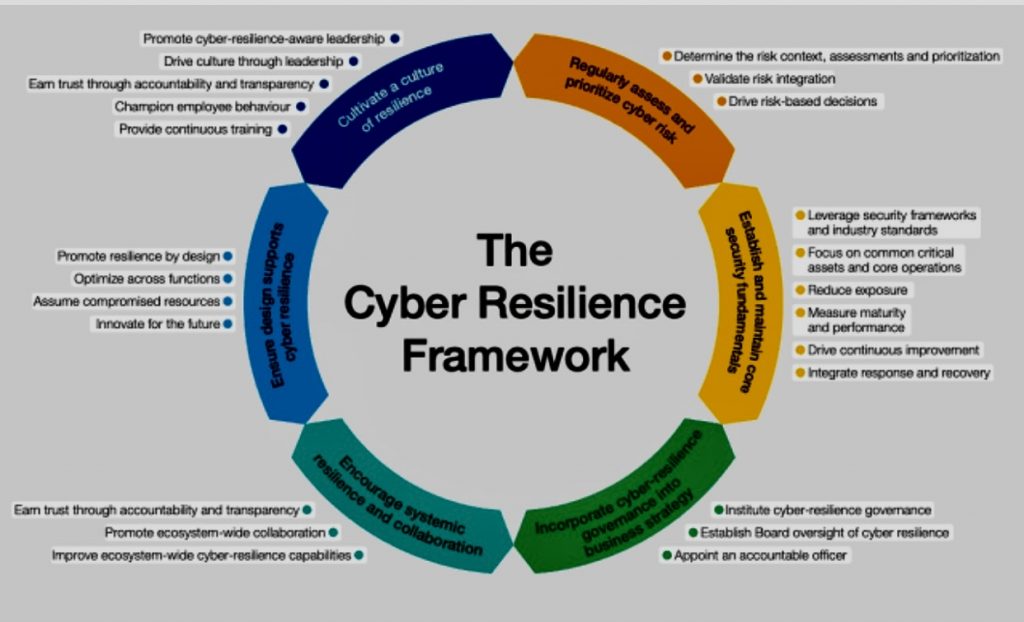
B. Cybersecurity and COBIT: Developing frameworks and methodologies for incorporating advanced cybersecurity measures within the context of COBIT’s governance structures.
C. SME Adaptation: Exploring how COBIT can be scaled and tailored for small and medium enterprises (SMEs) with limited resources and personnel.
D. Global Compliance and Regulation: Examining the role of COBIT in helping organizations navigate complex regulatory environments across different jurisdictions.
E. Agile and DevOps Integration: Assessing how COBIT can be aligned with agile methodologies and DevOps practices to maintain governance without stifling innovation and speed.
F. Cultural and Behavioral Aspects of IT Governance: Understanding the cultural and behavioral factors that influence the success of IT governance initiatives is crucial. Research can delve into how organizational culture, leadership styles, and employee attitudes impact the effectiveness of COBIT implementation.
G. Comparative Studies with Other Frameworks: Comparing COBIT with other IT governance frameworks, such as ITIL, TOGAF, and ISO/IEC 38500, can highlight their relative strengths and weaknesses. Such studies can provide guidance on selecting and integrating frameworks based on organizational needs.
H. Longitudinal Studies on COBIT Implementation: Long-term studies on organizations that have implemented COBIT can offer insights into the framework’s evolution and its long-term benefits and challenges. These studies can help refine COBIT and guide future updates.
I. Performance Measurement Advancements: Advancing the metrics and performance management aspects of COBIT to better reflect business outcomes and real-time analytics.
viii. Beyond the Framework: Limitations and Considerations
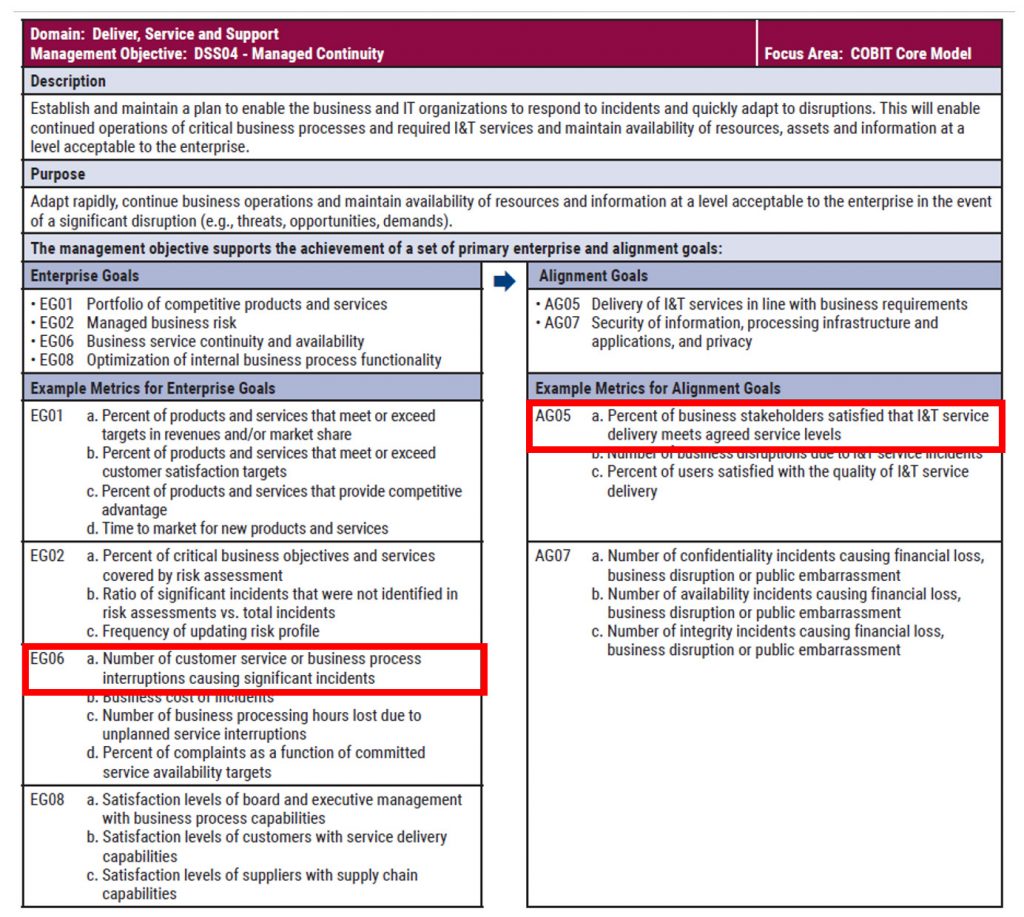
While COBIT offers a valuable framework, it’s important to acknowledge its limitations. Here are some additional considerations for researchers:
o One-size-fits-all approach: COBIT provides a generic framework, and organizations may need to adapt it to their specific needs and context.
o Focus on controls: COBIT emphasizes control objectives, but it’s vital to balance control with innovation and agility.
o Limited guidance on implementation: COBIT provides high-level guidance, and researchers can investigate best practices for implementation and customization.
ix. Conclusion

COBIT plays a pivotal role in the Enterprise Governance of Information Technology, offering a structured framework that helps bridge the gap between business priorities and IT efficiency. The ever-evolving nature of IT presents numerous research opportunities within this domain. By exploring these opportunities, academics and practitioners can contribute to the enhancement of EGIT practices, leading to more resilient, efficient, and aligned organizations in the digital age.
Additionally, considering the limitations of COBIT can guide further research into tailoring the framework for specific contexts and fostering innovation alongside control objectives.
The building blocks of COBIT provide a solid foundation for governing IT, yet there remains substantial scope for further exploration and innovation. By delving into emerging research opportunities, scholars and practitioners can contribute to the evolving landscape of IT governance, ensuring that businesses can navigate the complexities of the digital era with confidence and agility.
As businesses continue to rely heavily on IT for their operations and strategy execution, the importance of such research cannot be overstated, promising substantial benefits for organizations worldwide.
x. Further references
A bibliometric analysisJournal of Information Technology Managementhttps://jitm.ut.ac.ir › …
Cobit Formal Assessment – COBIT managementAdvantiohttps://www.advantio.com
Top 6 Ways IT Governance Can Help Your BusinessEZO.iohttps://ezo.io › Assetsonar › AssetSonar Blog
A Comprehensive Framework for AI Development …LinkedIn · Mandar Kulkarni110+ reactions
Business-IT Alignment | PPTSlideSharehttps://www.slideshare.net › Business
25 Cybersecurity Frameworks: A Guide to Choosing the …LinkedIn · Lahiru Livera8 reactions