Understanding BYOD Risks: How Technology Threat Avoidance Theory (TTAT) Can Help
In the evolving landscape of business technology management, the proliferation of personal mobile devices in the workplace has led to the BYOD trend, enabling employees to use their smartphones, tablets, and laptops for work purposes.
While BYOD offers increased flexibility and productivity, it also presents significant security challenges.
The Technology Threat Avoidance Theory (TTAT) focuses on how individuals perceive threats related to technology and how they adopt strategies to mitigate these risks.
In the context of BYOD, understanding users’ risk perceptions and behaviors is crucial in safeguarding sensitive corporate data.
i. TTAT Framework

The Technology Threat Avoidance Theory (TTAT) posits that individuals’ reactions to technology-related risks are influenced by their perception of the threat, vulnerability, and the effectiveness of available coping mechanisms. In the context of BYOD, employees’ attitudes toward security threats, their awareness of vulnerabilities, and their belief in the efficacy of security measures play a key role in shaping their behaviors and decision-making.
ii. TTAT: A Framework for Understanding User Behavior

TTAT sheds light on how individuals perceive and respond to technology threats. Here’s how it applies to BYOD:
o Perceived Susceptibility: Do employees believe their personal devices are vulnerable to cyberattacks?
o Perceived Severity: How serious do employees perceive the consequences of a data breach or malware infection to be (for themselves and the company)?
o Safeguarding Measures: Are employees aware of the security measures needed to protect their devices and company data (e.g., strong passwords, encryption)?
o Safeguarding Cost: Do employees find security measures (like installing security software) inconvenient or time-consuming?
o Self-Efficacy: Do employees feel confident in their ability to use their devices securely?
iii. The Rise of BYOD and its Advantages

BYOD allows employees to use their smartphones, laptops, and tablets for work activities, leading to several benefits:
o Increased Productivity and Flexibility: Employees can access work data and applications anytime, anywhere,potentially boosting productivity.
o Reduced Costs: Companies can save on hardware purchases by allowing employees to use their own devices.
o Improved Employee Satisfaction: BYOD empowers employees and fosters a sense of trust and autonomy.
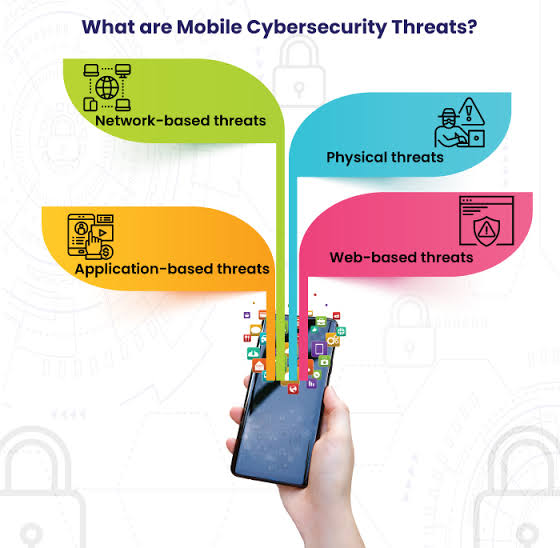
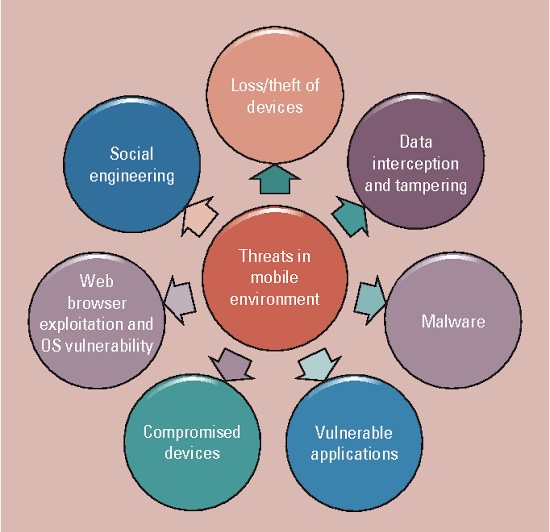
iv. The Flip Side: Security Concerns with BYOD
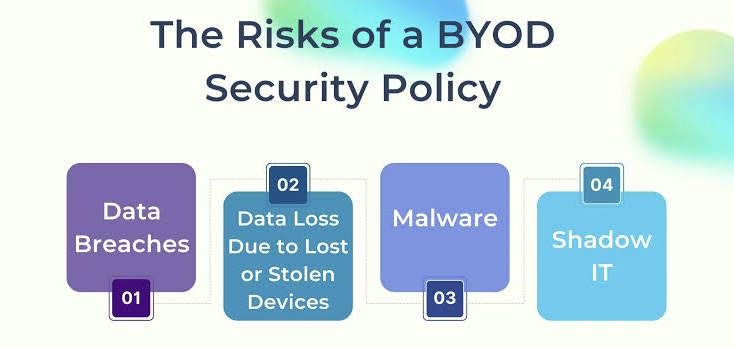
However, BYOD also presents security challenges:
o Data Breaches: Lost or stolen devices can expose sensitive company data if not properly secured.
o Malware and Phishing Attacks: Personal devices might be more vulnerable to malware or phishing scams,potentially compromising company systems.
o Device Loss or Theft: Personal devices are more susceptible to loss or theft, potentially resulting in unauthorized access to corporate data.
o Unauthorized Access: Weak authentication mechanisms or shared device usage may result in unauthorized individuals gaining access to sensitive information.
o Lack of Control: Companies have less control over security measures on personal devices compared to company-issued equipment.
v. Understanding TTAT in the Context of BYOD
The Technology Threat Avoidance Theory, developed within the field of information systems, suggests that users’ willingness to adopt technology-driven processes or comply with security measures depend on their perception of the threats associated with the technology. TTAT proposes that the perception of threat motivates the user to engage in behaviors that avoid the potential risks. In the context of BYOD, TTAT can be employed to predict and enhance users’ compliance with secure usage policies.
vi. Key Components of TTAT in BYOD
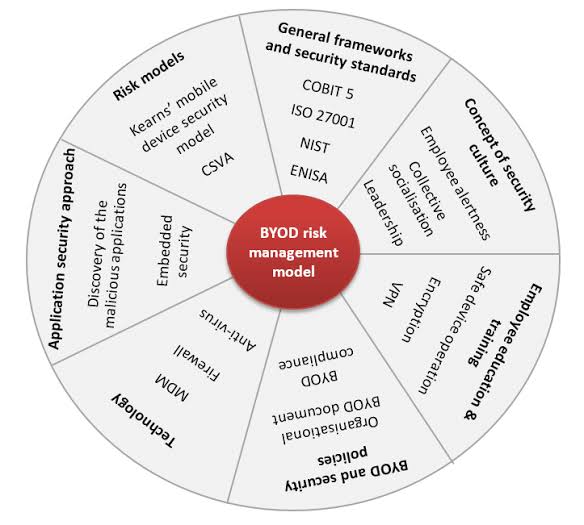
A. Threat Appraisal: This involves users assessing the potential harm that could result from cyber threats when using their personal devices for work purposes. When users perceive high levels of risk (e.g., data theft or device malware), it can catalyze a stronger intention to comply with security protocols.
B. Coping Appraisal: This determines the user’s belief in the efficacy of the security measures provided by the organization to mitigate those identified threats. If the users feel that following certain security measures will significantly lower the risks, they are more likely to adopt those measures.
C. Behavioral Intention: The perceived severity and susceptibility to threats, combined with the confidence in coping mechanisms, lead to a behavioral intention. In BYOD, this could translate into compliance with secure access measures, regular updates, and adherence to company policies on data usage and device access.
vii. Adoption and Enhance Compliance with TTAT

Organizations can leverage TTAT by implementing targeted security awareness training that specifically addresses both the personal and professional repercussions of security breaches in a BYOD environment. This training should not only focus on the types and severity of potential threats but also thoroughly educate employees on how adherence to security policies helps mitigate these risks effectively.
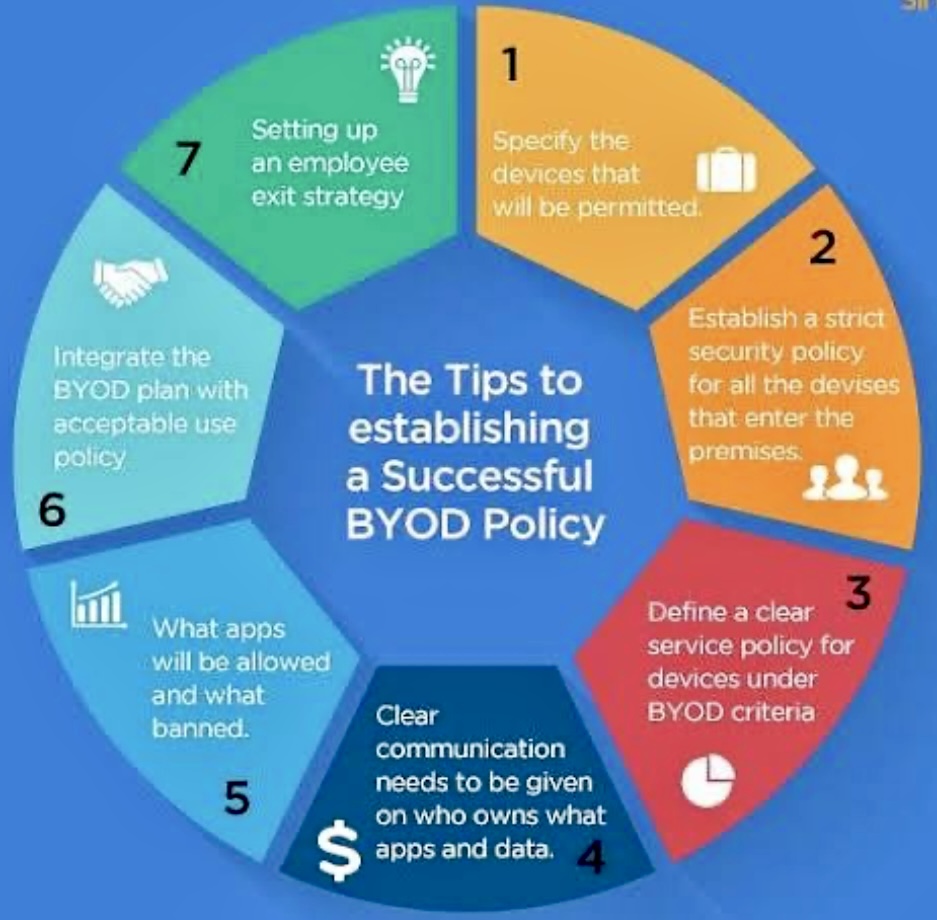
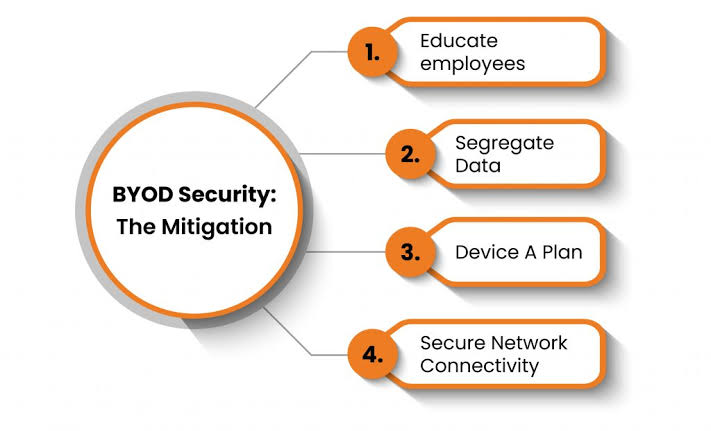
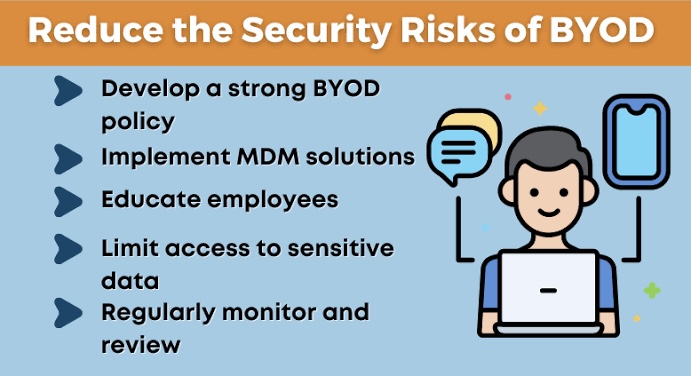
viii. Managing User Risk in BYOD

A. Regular audits and updates: Keeping software up to date and routinely checking for vulnerabilities can help mitigate the risks associated with outdated technologies.
B. Strategic policy enforcement: Policies should be enforced that limit types of allowable devices and regulate their security configurations. For example, requiring that all devices have updated antivirus software and are configured to comply with privacy standards.
C. User authentication and secure access: Employ strategies such as multi-factor authentication and encrypted connections to secure access to corporate data, thus reducing the chances of unauthorized access.
D. Technical Safeguards: Implement encryption, remote wipe capabilities, and mobile device management (MDM) solutions to protect corporate data on personal devices.
E. User Training and Awareness: Provide regular training sessions and awareness programs to educate users about BYOD risks and best practices for safe usage.
F. BYOD Agreements: Require users to sign BYOD agreements acknowledging their responsibilities regarding data security and compliance with organizational policies.
G. Data-centric security measures: Focus on protecting the data itself, regardless of the device that accesses it, through technologies such as mobile application management (MAM) and mobile content management (MCM).
ix. TTAT: A Stepping Stone to a Secure BYOD Environment
TTAT doesn’t offer a one-size-fits-all solution, but it provides a valuable framework for understanding user behavior and crafting effective BYOD security strategies. By addressing employee perceptions, concerns, and capabilities,organizations can encourage secure BYOD practices, fostering a productive and secure work environment.
x. The Road Ahead: A Collaborative Approach

A successful BYOD program requires collaboration between IT departments, security teams, and employees. By fostering open communication, raising awareness, and implementing effective security measures, organizations can reap the benefits of BYOD while minimizing associated risks. TTAT, by providing insights into user behavior, can serve as a valuable tool on this journey.
xi. Conclusion

In conclusion, the Technology Threat Avoidance Theory (TTAT) provides a valuable framework for understanding how individuals perceive and respond to technology-related threats, particularly in the context of BYOD adoption.
By applying TTAT principles to BYOD security, organizations can better assess user risk perceptions, strengthen security practices, and effectively mitigate the security risks associated with personal device use in the workplace.
Prioritizing security awareness, adopting robust security measures, and implementing proactive security strategies are essential for safeguarding corporate data in the era of BYOD.
In summary, the Technology Threat Avoidance Theory offers a systematic approach to analyzing and addressing the security risks associated with BYOD adoption.
Organizations that proactively apply TTAT principles can enhance their security posture, protect sensitive data, and promote a secure BYOD environment for employees.
xii. Further references
COREhttps://core.ac.uk › pdfPDFTECHNOLOGY THREAT AVOIDANCE FACTORS AS PREDICTORS OF RISKY …
NSUWorkshttps://nsuworks.nova.edu › …PDFA Technology Threat Avoidance Approach – NSUWorks
Studypoolhttps://www.studypool.com › tech…SOLUTION: Technology threat avoidance theory ttat
ResearchGatehttps://www.researchgate.net › 3278…(PDF) Bring your own device: A survey of threats …
IS Theoryhttps://is.theorizeit.org › wiki › Tec…Technology Threat Avoidance Theory (TTAT)
SponsoredVeriatohttps://www.veriato.comAI-Powered Behavior Analytics | Insider Risk Management (IRM)