
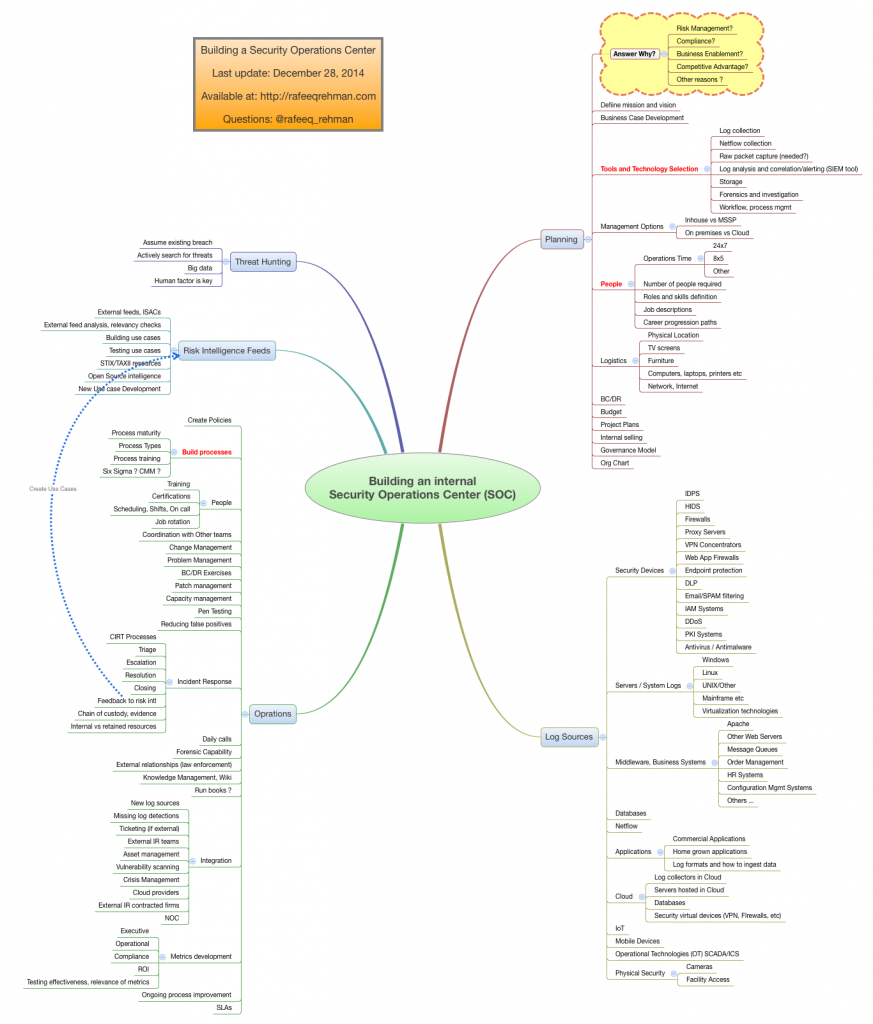
Securing Your Castle: Building a Budget-Friendly Security Operations Center (SOC)
In today’s digital age, cybersecurity threats are increasingly sophisticated and prevalent, making it essential for organizations of all sizes to have robust security measures in place. A Security Operations Center (SOC) plays a crucial role in defending against these threats by providing continuous monitoring, detection, and response to security incidents. However, setting up a SOC can be expensive, particularly for small to medium-sized businesses. This article outlines practical steps to build an effective SOC on a budget without compromising on security.
i. Understanding the SOC

A Security Operations Center (SOC) is a centralized unit that deals with security issues at both technical and organizational levels. It involves people, processes, and technology to monitor and improve an organization’s security posture while preventing, detecting, analyzing, and responding to cybersecurity incidents.
ii. A Roadmap to Build a Budget-Friendly SOC

Assess Your Needs and Define Objectives
- Assess Your Needs and Define Objectives
- Why It Matters:
- Understanding your organization’s specific security needs and defining clear objectives will help in designing a cost-effective SOC.
- Steps:
- Risk Assessment: Conduct a thorough risk assessment to identify critical assets, potential threats, and vulnerabilities.
- Objectives: Define clear objectives for your SOC, such as improving threat detection, reducing response times, and enhancing incident management.
- Define Scope: Clearly define the scope of your SOC, including the types of threats you’ll monitor and the key performance indicators (KPIs) you’ll use to measure success.
- Budget Planning: Establish a realistic budget based on your organization’s financial constraints and the essential elements required for your SOC.
- Why It Matters:
- Prioritize and Consolidate
- Why It Matters:
- Understanding your organization’s business objectives and priorities will help in designing a cost-effective SOC.
- Steps:
- Identify Your Critical Assets: Start by pinpointing your most valuable assets – data, systems, and applications.Focus your initial SOC efforts on protecting these critical elements.
- Consolidate Existing Tools: Audit your current security tools. Look for opportunities to consolidate redundant functionalities and leverage free or open-source alternatives where possible.
- Why It Matters:
Establish Clear Policies and Procedures
- Establish Clear Policies and Procedures
- Why It Matters:
- Standardized policies and procedures are critical for the effective operation of a SOC and can be developed without significant costs.
- Steps:
- Incident Response Plan: Develop a comprehensive incident response plan that outlines the steps to be taken during a security incident.
- Standard Operating Procedures (SOPs): Create SOPs for common SOC activities such as threat detection, logging, and alert management.
- Documentation and Reporting: Implement thorough documentation practices to ensure all activities are recorded and can be reviewed for continuous improvement.
- Why It Matters:
Leverage Existing Resources

- Leverage Existing Resources
- Why It Matters:
- Maximizing the use of existing resources can significantly reduce costs.
- Steps:
- Current Infrastructure: Assess your current IT infrastructure and determine which components can be integrated into the SOC.
- Staff Utilization: Identify internal staff with relevant skills who can take on additional security responsibilities.
- Why It Matters:
Adopt a Phased Approach

- Adopt a Phased Approach
- Why It Matters:
- Implementing the SOC in phases allows you to spread out costs and make adjustments as needed.
- Steps:
- Phase 1 – Initial Setup: Start with essential components such as a Security Information and Event Management (SIEM) system and basic monitoring capabilities.
- Phase 2 – Expansion: Gradually add advanced features like threat intelligence integration, automated response capabilities, and forensic tools.
- Phase 3 – Optimization: Continuously optimize and expand your SOC as your budget allows and your needs evolve.
- Why It Matters:
Utilize Open Source Tools

- Utilize Open Source Tools
- Why It Matters:
- Open source security tools offer robust functionality at a fraction of the cost of commercial solutions.
- Steps:
- Security Information and Event Management (SIEM): Utilize open-source SIEM solutions like ELK Stack (Elasticsearch, Logstash, and Kibana) for centralized log management and event correlation.
- Vulnerability Scanners: OpenVAS or Nessus offer robust vulnerability scanning capabilities to identify weaknesses in your systems.
- Intrusion Detection/Prevention Systems (IDS/IPS): Snort is a popular open-source IDS that monitors network traffic for suspicious activity.
- Network Monitoring: Implement tools like Snort or Suricata for network intrusion detection.
- Endpoint Security: Deploy open source endpoint detection and response (EDR) solutions like OSSEC.
- Why It Matters:
Outsource Where Possible

- Outsource Where Possible
- Why It Matters:
- Outsourcing certain SOC functions can provide expertise and technology at a lower cost than building in-house capabilities.
- Steps:
- Managed Security Service Providers (MSSPs): Partner with MSSPs for 24/7 monitoring, threat detection, and incident response services.
- Consultants: Use cybersecurity consultants for specific tasks like risk assessments, compliance audits, and SOC design.
- Co-Managed SOCs: Partnerships where certain responsibilities are outsourced, while your team handles the rest, can balance cost and control.
- Why It Matters:
Implement Automation

- Implement Automation
- Why It Matters:
- Automation reduces the workload on your team and improves efficiency, allowing you to do more with less.
- Steps:
- Automated Incident Response: Implement automation tools to handle routine tasks such as log analysis, alert triage, and basic incident response.
- Orchestration: Use Security Orchestration, Automation, and Response (SOAR) platforms to integrate and automate workflows across different security tools.
- Security Automation Tools: Explore open-source security automation tools like Security Onion or Wazuh to automate routine tasks, freeing up your team to focus on high-level threat analysis.
- Streamline Workflows: Develop standardized procedures and incident response plans to streamline your team’s workflow and improve efficiency.
- Why It Matters:
Leverage Cloud-Based Security Solutions
- Leverage Cloud-Based Security Solutions:
- Why It Matters:
- Cloud-based SIEM and Security Analytics
- Cost Efficiency
- Reduced Capital Expenditure: Cloud-based SIEM solutions eliminate the need for substantial upfront investments in hardware and software, leading to lower capital expenditure.
- Predictable Costs: Subscription-based pricing models make it easier to predict and manage security expenditures.
- Scalability
- Flexible Scaling: Cloud-based solutions can easily scale up or down based on the organization’s needs, allowing for flexibility as the business grows or changes.
- Resource Optimization: Organizations can allocate resources dynamically, optimizing performance and cost efficiency.
- Rapid Deployment
- Quick Implementation: Cloud-based SIEM solutions can be deployed more quickly compared to on-premise systems, reducing the time to operationalize security measures.
- Less Complexity: The reduced need for complex hardware and software installations streamlines the deployment process.
- Access to Advanced Features
- Cutting-Edge Technology: Cloud providers often incorporate the latest security features and updates, ensuring organizations have access to advanced capabilities such as AI-driven analytics, real-time threat detection, and comprehensive log management.
- Continuous Improvement: Cloud-based solutions benefit from continuous updates and improvements without the need for manual intervention.
- Reduced Maintenance
- Managed Infrastructure: The cloud provider handles the maintenance, updates, and management of the infrastructure, reducing the burden on internal IT staff.
- Focus on Core Activities: IT teams can focus on core business activities and strategic initiatives rather than managing SIEM infrastructure.
- Cost Efficiency
- Cloud-based SIEM and Security Analytics
- Why It Matters:
- Security as a Service (SaaS) through Managed Security Service Providers (MSSPs)
- 1. Comprehensive Security Coverage
- Broad Range of Services: MSSPs offer a wide array of security services, including threat detection, incident response, vulnerability management, and compliance monitoring.
- Expertise and Specialization: Access to specialized security expertise and resources that might not be available in-house.
- 2. Cost-Effective Solution
- Lower Upfront Costs: MSSPs typically operate on a subscription basis, reducing the need for large upfront investments in security infrastructure and personnel.
- Operational Expense: Shifts security spending from capital expenditure to operational expenditure, making it easier to budget and manage costs.
- 3. 24/7 Monitoring and Support
- Round-the-Clock Security: MSSPs provide continuous monitoring and support, ensuring that security threats are detected and addressed promptly, regardless of time.
- Rapid Response: MSSPs can offer rapid incident response and mitigation, reducing the potential impact of security breaches.
- 4. Access to Advanced Technologies
- Latest Tools and Techniques: MSSPs leverage state-of-the-art technologies and methodologies to protect their clients, often incorporating the latest advancements in cybersecurity.
- Regular Updates: Clients benefit from regular updates and improvements to security tools without additional effort or cost.
- 5. Scalability and Flexibility
- Adaptable Services: Security services can be scaled according to the organization’s needs, providing flexibility to adapt to changing business requirements.
- Customized Solutions: MSSPs can offer tailored security solutions that meet the specific needs and regulatory requirements of different industries.
- 6. Risk Reduction
- Proactive Threat Management: MSSPs proactively manage and mitigate risks, reducing the likelihood and impact of security incidents.
- Compliance Assistance: MSSPs often help organizations comply with regulatory requirements, reducing the risk of non-compliance penalties.
- 1. Comprehensive Security Coverage
- Steps:
- Cloud-based SIEM and Security Analytics: Cloud-based SIEM solutions can offer cost-effective alternatives to on-premise solutions, with features like log management and threat intelligence. Tools like Microsoft Azure Sentinel provide scalable security analytics at a fraction of the cost of traditional SIEM solutions.
- Security as a Service (SaaS): Consider managed security services (MSSPs) that offer a range of security functions on a subscription basis, reducing upfront costs and ongoing maintenance.
- Log Management: Services like AWS CloudWatch or Google Cloud Logging enable robust log collection, monitoring, and analysis.
Leverage Talent Creatively

- Leverage Talent Creatively:
- Why It Matters:
- Cross-train Existing Staff
- Cost Efficiency
- Reduced Hiring Costs: Cross-training existing IT personnel eliminates the need for hiring additional dedicated SOC staff, thereby saving on recruitment and onboarding expenses.
- Utilization of Current Resources: Leveraging existing employees maximizes the use of current resources and reduces overhead costs associated with expanding the workforce.
- Faster Implementation
- Immediate Availability: Existing staff are already familiar with the organization’s systems, processes, and culture, allowing for quicker integration into security roles.
- Quick Adaptation: Employees can begin contributing to SOC functions more rapidly compared to hiring and training new staff from scratch.
- Enhanced Skill Set
- Broadened Expertise: Cross-training broadens the skill sets of IT personnel, making them more versatile and valuable to the organization.
- Improved Problem Solving: Employees with both IT and security knowledge are better equipped to understand and address complex security issues.
- Increased Employee Engagement
- Career Development: Offering cross-training opportunities can enhance employee satisfaction and loyalty by providing avenues for professional growth and development.
- Empowerment: Employees feel more empowered and motivated when they are given the chance to expand their skill sets and take on new challenges.
- Cost Efficiency
- Partner with Cybersecurity Students
- Access to Emerging Talent
- Fresh Perspectives: Cybersecurity students bring new ideas and fresh perspectives that can invigorate your SOC with innovative approaches to security challenges.
- Up-to-Date Knowledge: Students are often well-versed in the latest cybersecurity trends, technologies, and best practices, thanks to their recent education and training.
- Cost-Effective Workforce
- Affordable Labor: Internships and student partnerships can provide access to skilled labor at a lower cost compared to hiring full-time employees.
- Trial Period: Internships serve as a trial period to evaluate potential future employees without the long-term commitment, allowing for better hiring decisions.
- Strengthened Community Relations
- University Partnerships: Collaborating with local universities and colleges helps build strong relationships with educational institutions, which can be beneficial for future recruitment and joint projects.
- Corporate Social Responsibility: Offering internship opportunities supports educational initiatives and contributes to the development of the next generation of cybersecurity professionals.
- Scalability and Flexibility
- Flexible Workforce: Interns can be brought in on a seasonal or project basis, providing scalability and flexibility in managing workforce needs according to project demands.
- Talent Pipeline: Developing a talent pipeline through internships ensures a steady flow of potential full-time hires who are already familiar with your organization’s environment and expectations.
- Access to Emerging Talent
- Cross-train Existing Staff
- Steps:
- Cross-train Existing Staff: Instead of hiring a dedicated SOC team initially, consider cross-training existing IT personnel on core security concepts and open-source tools.
- Partner with Cybersecurity Students: Collaborate with universities or colleges with cybersecurity programs.Offer internship opportunities to gain valuable talent and fresh perspectives.
- Why It Matters:
Focus on Training and Awareness

- Focus on Training and Awareness
- Why It Matters:
- Well-trained staff are critical to the success of your SOC, and continuous training can be more cost-effective than hiring new personnel.
- Steps:
- Internal Training: Provide ongoing training for existing staff on the latest cybersecurity trends, tools, and techniques.
- Certifications: Encourage and support staff in obtaining relevant cybersecurity certifications such as CISSP, CISM, or CEH.
- Invest in Employee Training: Regular security awareness training for employees is crucial. Educate them on phishing attacks, social engineering tactics, and best practices for password hygiene.
- Encourage Reporting: Create a culture where employees feel comfortable reporting suspicious activity without fear of reprisal.
- Budget-Friendly Tip: Encourage self-paced online training through platforms like Coursera, Udemy, and LinkedIn Learning, which often provide affordable courses on cybersecurity fundamentals and advanced topics.
- Why It Matters:
Monitor and Improve Continuously

- Monitor and Improve Continuously
- Why It Matters:
- Continuous improvement ensures your SOC remains effective and efficient as new threats and technologies emerge.
- Steps:
- Metrics and KPIs: Establish and track key performance indicators (KPIs) to measure the effectiveness of your SOC.
- Regular Audits: Conduct regular audits and assessments to identify gaps in your SOC’s capabilities.
- Feedback Loop: Create a feedback loop to incorporate lessons learned from incidents and audits into SOC operations.
- Performance Review: Periodically review and adjust your SOC’s performance metrics and objectives.
- Adopt New Technologies: Stay informed about new, cost-effective technologies that could enhance your SOC’s effectiveness.
- Why It Matters:
iii. Building a Secure Future

Remember, a budget-friendly SOC is not about compromising security. It’s about utilizing available resources creatively.By prioritizing critical assets, leveraging open-source tools, and fostering a culture of security awareness, you can establish a functional SOC that safeguards your organization within your budgetary constraints. As your security posture strengthens and resources permit, you can gradually invest in more sophisticated tools and expand your SOC capabilities.
iv. Conclusion

Building a Security Operations Center on a budget is achievable with careful planning, resourcefulness, and a focus on maximizing the value of existing assets and open source tools. By adopting a phased approach, leveraging automation, and investing in training, organizations can develop a robust SOC that enhances their security posture without breaking the bank. Continuous improvement and strategic outsourcing can further optimize SOC operations, ensuring that your organization remains resilient against evolving cyber threats.
The key takeaway? Your organization’s security doesn’t have to break the bank. With a strategic approach and a commitment to continuous improvement, you can build a robust SOC that protects your critical assets and keeps your organization safe.
v. Further references
How to Build a SOC on a BudgetIEEE Xplorehttps://ieeexplore.ieee.org › iel7
KIT | Cybersecurity Management ToolKitsenhasegurahttps://lp.senhasegura.co › cybersecurity
