Why Modern Enterprise Architecture is Key to Agile Scaling
In today’s fast-paced digital landscape, agility and scalability have become fundamental for businesses striving for competitive advantage and innovation. Agile methodologies, once the province of software development teams, are now being scaled across entire organizations to enhance flexibility, responsiveness, and customer satisfaction.
However, scaling agile practices is not merely a matter of expanding principles from a single team to many. It necessitates a foundational shift in how a company’s infrastructure – its enterprise architecture (EA) – is designed and implemented. A modern enterprise architecture is pivotal in ensuring that the scaling of agile methodologies is successful, sustainable, and aligned with business objectives.
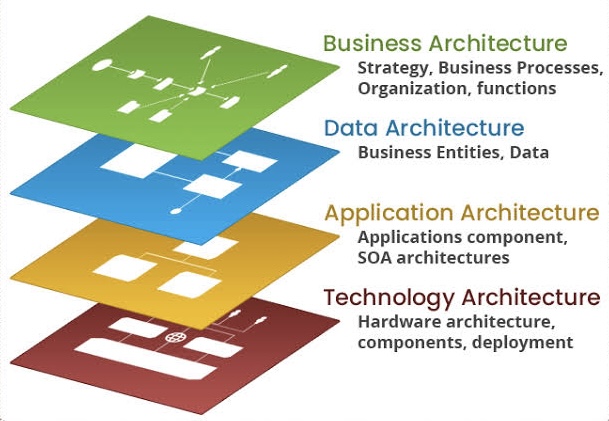
i. What is Modern Enterprise Architecture?
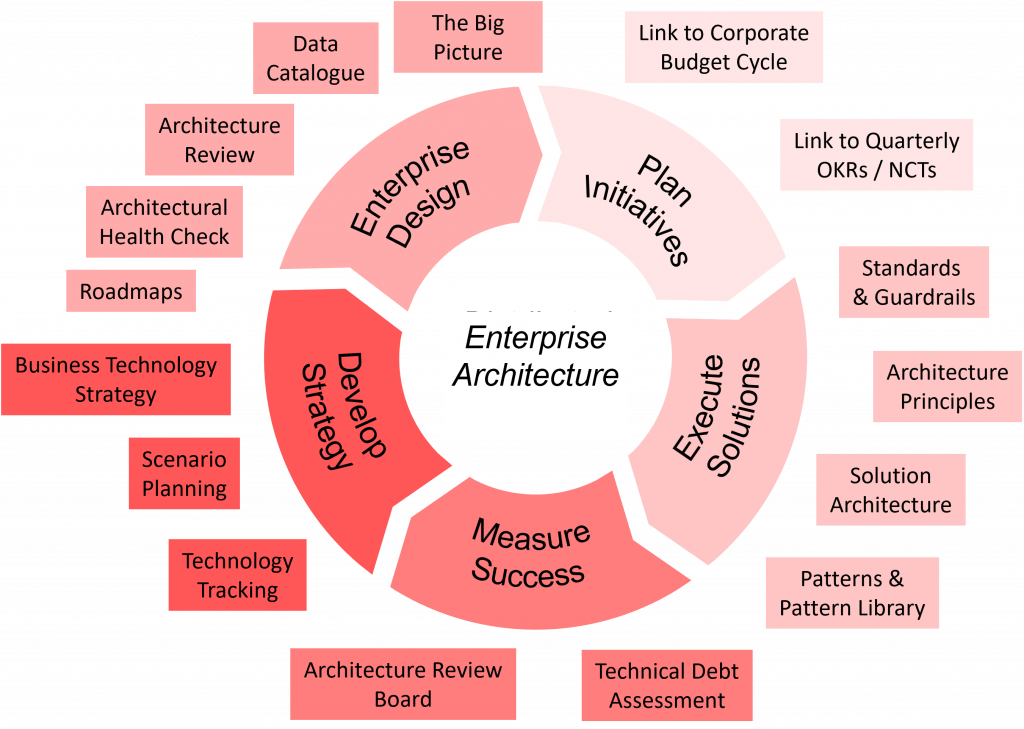
Modern enterprise architecture (EA) is a strategic approach to designing and aligning an organization’s technology landscape with its business goals. It provides a blueprint for how applications, data, and infrastructure should be structured to support agility, scalability, and innovation.
ii. How Modern EA Supports Agile Scaling
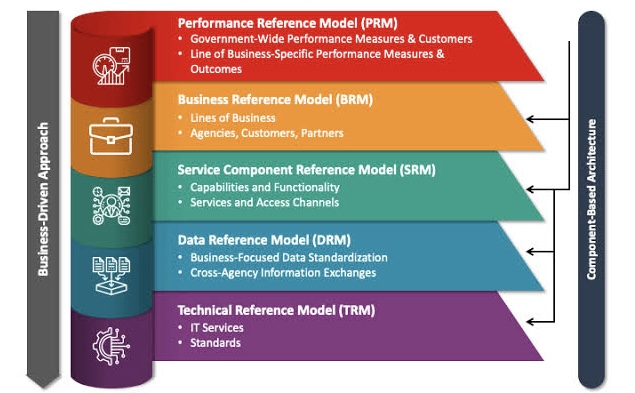
o Alignment: Modern EA ensures that agile development teams are working towards a common goal by providing a shared vision of the target architecture.
o Modularity and Flexibility: A well-designed architecture breaks down complex systems into smaller, independent components that can be easily integrated and modified. This enables agile teams to deliver features faster and respond to changing requirements.
o Center of Excellence: Modern EA fosters a collaborative environment where architects act as advisors and coaches, supporting agile teams throughout the development lifecycle.
iii. Agile at Scale: The Need for a Modern Enterprise Architecture

While Agile methodologies have proven effective at the team level, scaling Agile across large organizations presents unique challenges. Traditional monolithic architectures, with their rigid structures and siloed systems, are ill-suited for the rapid pace and collaborative nature of Agile development. As teams grow in size and complexity, coordination, communication, and alignment become increasingly challenging. Without a modern enterprise architecture that can support Agile principles and practices, organizations risk inefficiency, duplication of efforts, and disjointed customer experiences.
iv. The Symbiosis of Agile and Modern Enterprise Architecture

A. Flexibility and Responsiveness: A modern enterprise architecture is inherently designed to support flexibility and rapid change. It adopts modular, service-oriented designs that allow for parts of the IT system to be changed or upgraded without disrupting the whole. This modular approach is harmonious with agile’s iterative development and continuous delivery models, allowing businesses to respond swiftly to market changes or new customer demands.
B. Enhanced Collaboration and Visibility: Agile methodologies thrive on collaboration and cross-functional team dynamics. Modern EA frameworks facilitate this by promoting transparency and interconnectedness among systems, data, and processes. By fostering an environment where information flows freely and systems are integrated, organizations can break down silos and encourage more cohesive and cooperative work practices, which are essential for scaling agile.

C. Strategic Alignment: Scaling agile requires more than the adoption of flexible working practices; it demands alignment between IT initiatives and business objectives. Modern enterprise architectures support this by providing a roadmap that guides not only IT strategy but also how it aligns with broader business goals. This ensures that agile scaling efforts are driving value and are in sync with the company’s strategic vision.
D. Integrated Systems and Data: Siloed systems and segregated data repositories create barriers to Agile scaling, leading to inefficiencies and inconsistencies. A modern EA emphasizes integration and interoperability, ensuring that systems and data are seamlessly connected and accessible, thereby enhancing collaboration and decision-making speed.
E. Sustainability and Scalability: A common challenge in scaling agile is maintaining the momentum and practices as more teams and complexities are added. Modern EA helps address this by building scalability into the system’s core, ensuring that the infrastructure can handle growth without performance degradation. This includes considerations for cloud computing, data management, and application scalability, ensuring that the enterprise can grow without compromising agility.
F. Innovation Support: Finally, by providing a flexible, aligned, and scalable foundation, a modern enterprise architecture fosters an environment conducive to innovation. Agile teams can experiment, iterate, and deploy new solutions with confidence, knowing the underlying architecture supports rapid development cycles and the continuous evolution of products and services.
v. Implementing Modern Enterprise Architecture for Agile Scaling
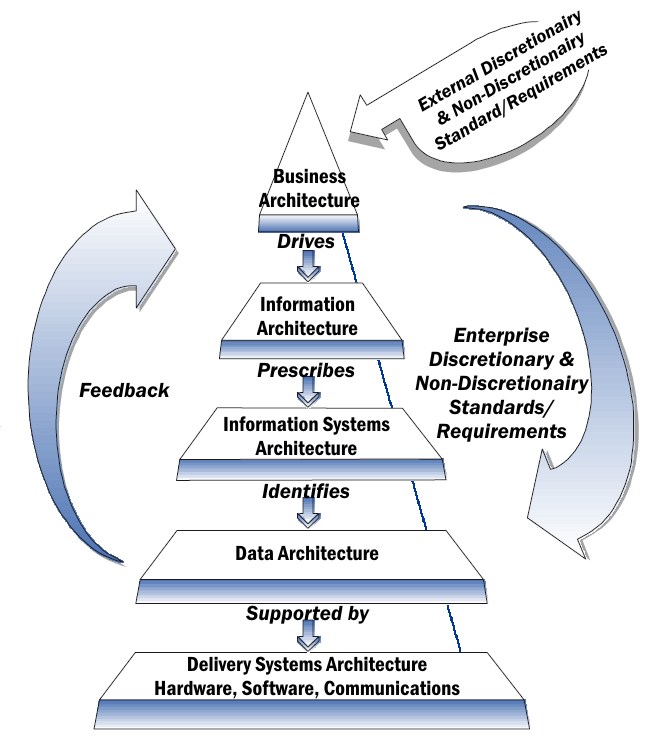
Implementing a modern EA to support agile scaling is not without its challenges. It requires a deep understanding of both the current state of the organization’s architecture and its future needs.
Key steps include:
o Assessment and Planning: Evaluating the existing architecture, identifying gaps, and planning for a transition to a more modular, flexible, and scalable architecture.
o Technology Standardization: Rationalizing technology stacks and investing in tools and platforms that support agile practices and integration needs.
o Cultural Shift: Beyond technology, fostering a culture that embraces change, learning, and collaboration across all levels of the organization.
o Governance and Compliance: Establishing governance models that support agility while ensuring compliance and security are not compromised.
vi. Key Elements of a Modern Enterprise Architecture
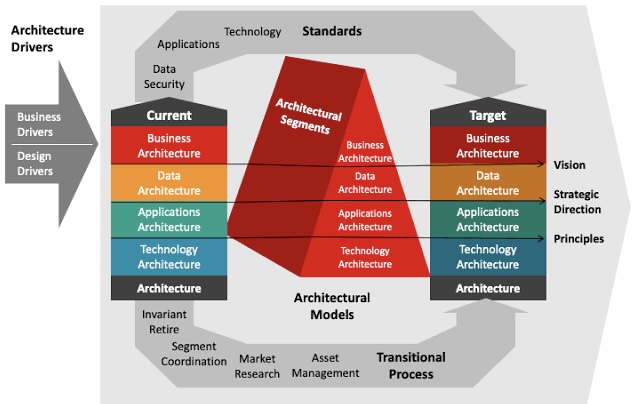
A modern enterprise architecture is designed to facilitate agility, collaboration, and innovation at scale. It provides the foundation for seamless integration, continuous delivery, and cross-functional collaboration, enabling organizations to adapt quickly to changing business needs and market demands. Several key elements are essential for building a modern enterprise architecture that supports scaled Agile:
A. Microservices Architecture: Breaking down large, monolithic systems into smaller, independently deployable services allows for greater flexibility, scalability, and agility. Microservices enable teams to work autonomously, iterate quickly, and release software updates independently, without disrupting other parts of the system.
B. Cloud Computing: Leveraging cloud infrastructure provides the scalability, elasticity, and reliability needed to support Agile development practices. Cloud platforms offer on-demand access to computing resources, enabling teams to scale their infrastructure dynamically to meet changing demands and optimize costs.
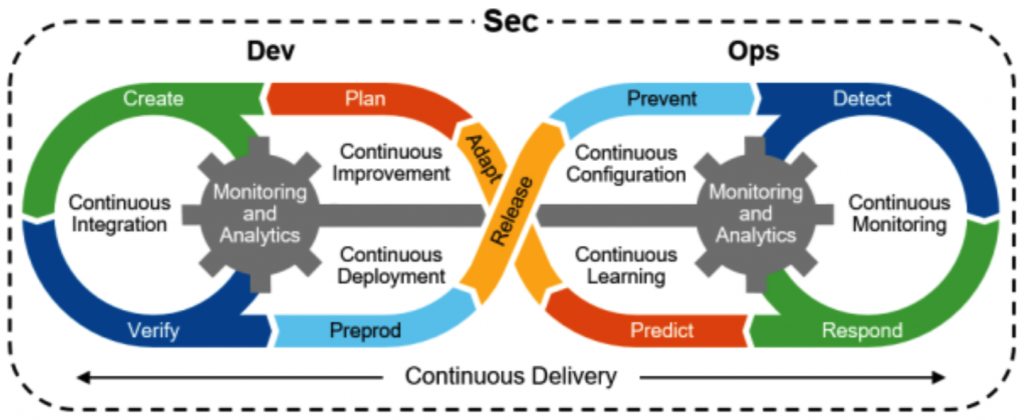
C. DevOps Practices: Embracing DevOps principles and practices streamlines the software delivery pipeline, from development to deployment and beyond. Automation, continuous integration, and continuous delivery (CI/CD) enable organizations to release software more frequently, reliably, and with reduced lead times, fostering a culture of collaboration and innovation.
D. API-First Approach: Adopting an API-first approach to software development promotes modularity, interoperability, and reusability. APIs serve as the building blocks of digital ecosystems, enabling seamless integration and interoperability between disparate systems and applications, both internally and externally.

E. Event-Driven Architecture: Embracing event-driven architecture facilitates real-time data processing, event-driven workflows, and asynchronous communication between services. Events serve as triggers for business processes, enabling organizations to respond quickly to changing conditions and deliver timely, personalized experiences to customers.
vii. Benefits of a Modern Enterprise Architecture for Scaling Agile

A modern enterprise architecture offers numerous benefits for organizations seeking to scale Agile practices effectively:
o Enhanced Flexibility: Modular, loosely coupled systems enable teams to respond quickly to changing requirements and market conditions, fostering adaptability and innovation.
o Improved Collaboration: Seamless integration, automated workflows, and cross-functional collaboration promote alignment, transparency, and knowledge sharing across the organization.
o Faster Time-to-Market: Streamlined development and delivery pipelines, coupled with scalable infrastructure, enable organizations to release software updates more frequently and reliably, accelerating time-to-market and reducing time-to-value.
o Better Customer Experiences: Agile development practices, combined with real-time data processing and event-driven workflows, enable organizations to deliver personalized, responsive experiences to customers, driving satisfaction and loyalty.
viii. Conclusion

The symbiosis between a modern enterprise architecture and Agile practices is a critical enabler for organizations aiming to scale agility and thrive in a digital-first world.
A modern EA provides the structure, visibility, and alignment necessary to scale Agile effectively, turning it from a team-based methodology into a comprehensive enterprise-wide strategy.
As companies increasingly recognize the value of both Agile and a modern EA, the fusion of these approaches will continue to be a hallmark of successful digital transformation initiatives.
By investing in the development and continual evolution of a modern EA, organizations can ensure the scalability, flexibility, and responsiveness required to excel in today’s dynamic business environment.
ix. Further references
SponsoredLeanIXhttps://www.leanix.netDownload free White Paper – Enterprise Architecture
A Modern Enterprise Architecture Is Essential for Scaling Agile
LeanIXhttps://www.leanix.net › blog › su…Using Enterprise Architecture To Support Scaled Agile
Scaled Agile Frameworkhttps://scaledagileframework.com › …Enterprise Architect
SponsoredLeanIXhttps://www.leanix.netEnterprise Architecture – Frameworks and Methodologies
agiledata.orghttps://agiledata.org › essays › enter…Agile Enterprise Architecture: Collaborative …
LinkedIn · Bizcon7 reactionsThe Role of Enterprise Architecture in Business Agility and Resilience
Medium · Aman Luthra10+ likesRoles and Responsibilities: Enterprise Architect | by Aman Luthra
Conexiamhttps://conexiam.com › agile-devel…Understanding Enterprise Architecture and Agile
Capsterahttps://www.capstera.com › enterpri…The Ultimate Guide to Enterprise Architecture Management