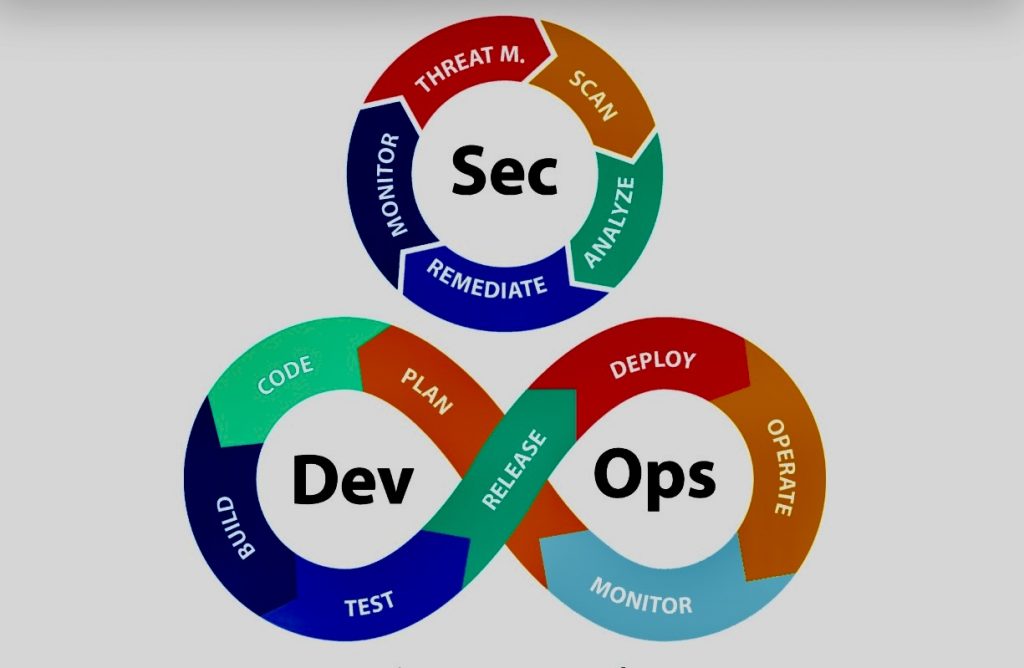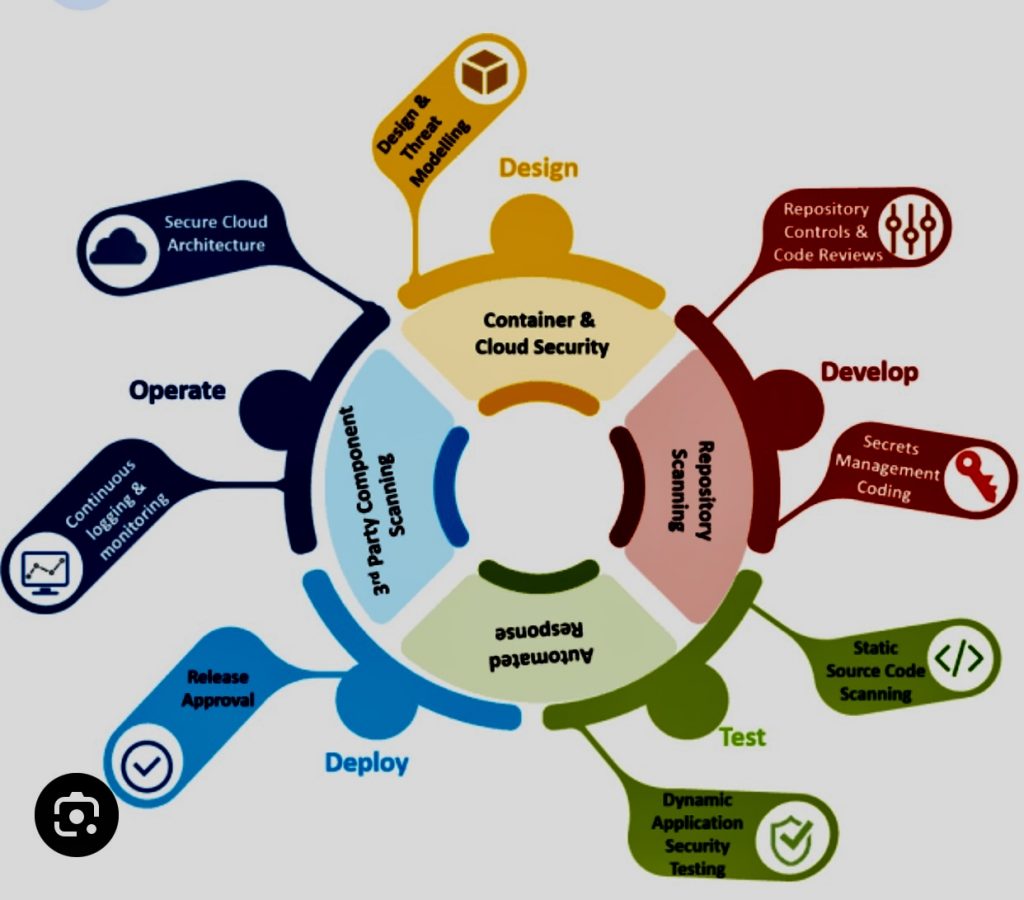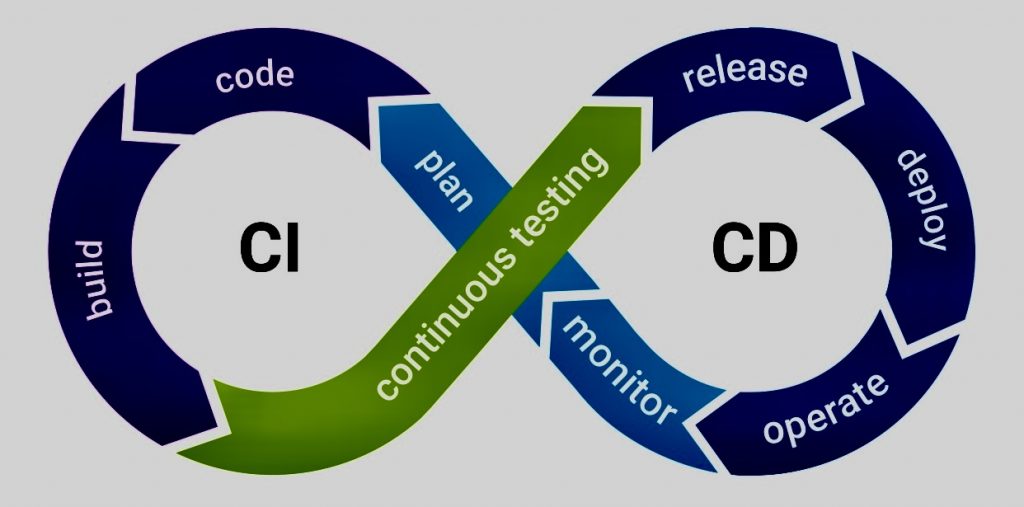
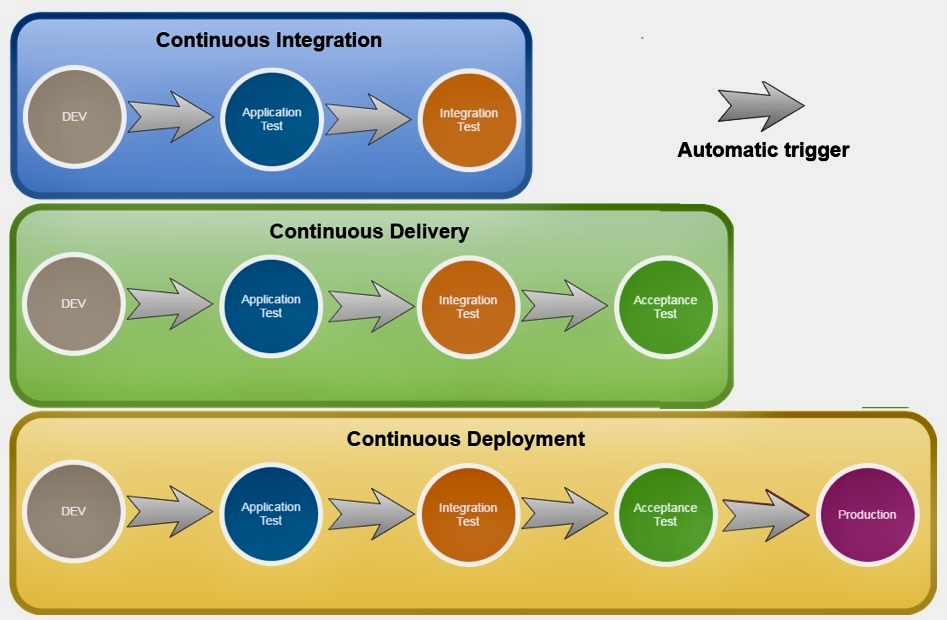
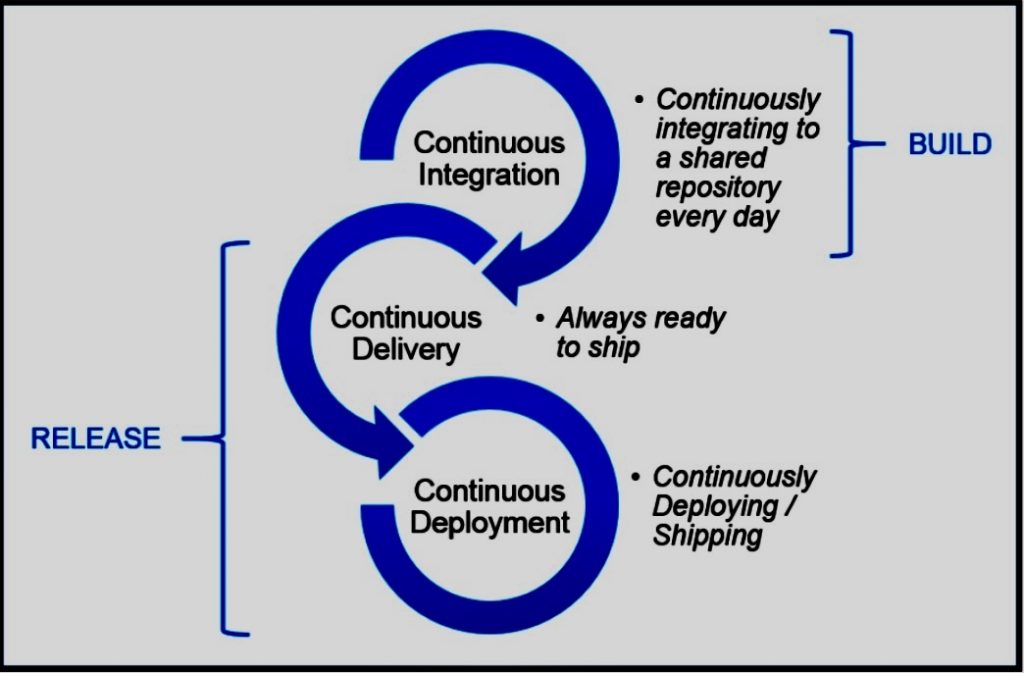
Continuous Integration/Continuous Deployment (CI/CD) is a methodology used in modern software development to deliver code changes more frequently and reliably. The approach fosters a culture of regular, automated code deployments.
Continuous Integration (CI) is a coding perspective where developers merge their changes back to the main branch as often as possible, ideally multiple times a day. This usually involves an automated process for building and testing the software, ensuring that changes made by developers don’t break the product or introduce errors.
Continuous Deployment (CD), on the other hand, involves taking the validated changes from CI and automatically deploying them into production environments. This approach ensures users benefit from new updates quickly and minimizes the delay between software development and its use.
i. Key Components of CI/CD
A. Continuous Integration (CI):
o Concept: Integrating code changes from multiple contributors into a shared repository frequently.
o Goal: Detecting and addressing integration issues early in the development cycle.
B. Continuous Deployment (CD):
o Concept: Automating the process of deploying code changes to production after successful CI.
o Goal: Ensuring a rapid and reliable delivery pipeline from development to production.
C. CI/CD Pipeline:
o Concept: An automated sequence of steps that include building, testing, and deploying code changes.
o Goal: Streamlining the software delivery process, reducing manual interventions, and increasing efficiency.
D. Automated Testing:
o Concept: Running automated tests during the CI/CD pipeline to validate code changes.
o Goal: Ensuring code quality and identifying issues early in the development cycle.
E. Version Control:
o Concept: Managing and tracking changes to source code using version control systems (e.g., Git).
o Goal: Providing a collaborative and organized environment for developers to work on code.
F. Containerization (e.g., Docker):
o Concept: Packaging applications and their dependencies into containers for consistency across different environments.
o Goal: Ensuring that applications run consistently in various environments, from development to production.
G. Orchestration (e.g., Kubernetes):
o Concept: Managing and automating the deployment, scaling, and operation of containerized applications.
o Goal: Ensuring efficient and reliable containerized application management.
ii. General stages in a CI/CD pipeline
A. Source: The developer pushes the code to a version control system (like Git), which triggers the pipeline.
B. Build: This stage involves compiling source code into executable code. The steps might vary depending on the type of project.
C. Test: Automated tests are run to ensure the introduction of new code does not introduce any defects or bugs. This can include unit tests, integration tests, and more.
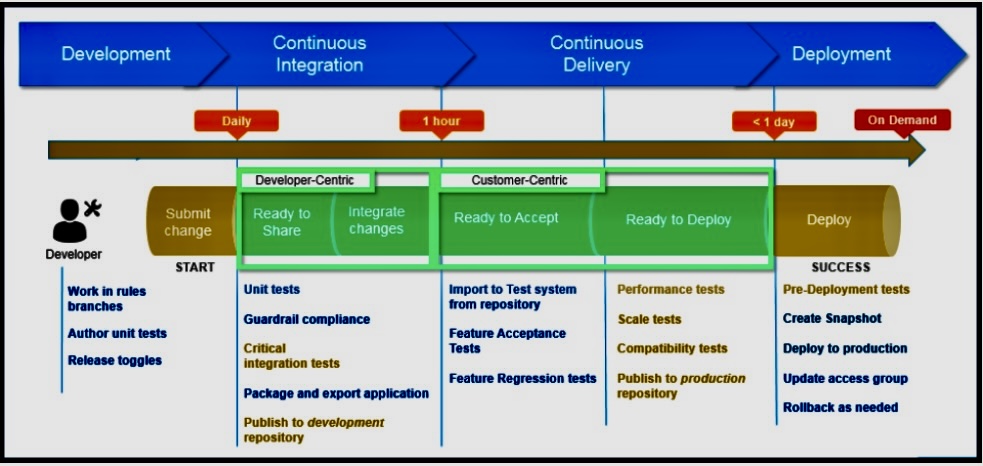
D. Deployment: The validated code is then automatically deployed to a production environment in CD.
E. Monitor & Validate: After deployment, the application’s performance is monitored to quickly identify and address any issues that may arise due to the new changes.
iii. Implementing CI/CD
A. Choose a CI/CD Toolset: There are many CI/CD tools available, so it is important to choose one that fits the organization’s needs and budget.
B. Define the Pipeline: The CI/CD pipeline is the set of steps that are automated to build, test, and deploy code changes.
C. Automate the Pipeline: Use CI/CD tools to automate the pipeline, including building, testing, and deploying code changes.
D. Continuously Monitor: Monitor the CI/CD pipeline to ensure that it is running smoothly and that all tests are passing.
iv. Benefits of CI/CD
A. Increased Software Quality: CI/CD helps to improve software quality by catching bugs early in the development process and automating the testing process.
B. Reduced Delivery Time: CI/CD enables developers to deliver software more frequently and reliably, which can lead to increased customer satisfaction.
C. Improved Collaboration: CI/CD provides a platform for developers to collaborate more effectively and share code changes more easily.
D. Reduced Costs: CI/CD can reduce the cost of software development by automating tasks and eliminating manual errors.
Implementing a CI/CD pipeline can help reduce errors in code, lower the cost of development, and speed up the overall development process.
It requires a culture of continuous improvement and an investment in test automation and build automation tools but provides significant benefits in application quality and developer productivity.
By implementing CI/CD, development teams can accelerate the release cycle, reduce manual errors, and enhance the overall quality and reliability of software products.
https://www.browserstack.com/guide/difference-between-continuous-integration-and-continuous-delivery
https://media.defense.gov/2023/Jun/28/2003249466/-1/-1/0/CSI_DEFENDING_CI_CD_ENVIRONMENTS.PDF