Boards of Directors: The Ultimate Safeguard in Cybersecurity for Industrial Firms
In an increasingly digitalized world, the threat landscape for industrial companies has evolved dramatically.
With the proliferation of interconnected devices and the rise of sophisticated cybercriminals, safeguarding critical infrastructure has become paramount.
Amidst this landscape, the role of boards of directors in ensuring robust cybersecurity measures has emerged as a crucial line of defense.
Boards of directors, traditionally tasked with strategic oversight and governance, are now being called upon to actively engage in cybersecurity governance.
As custodians of shareholder value and stewards of corporate reputation, boards play a pivotal role in setting the tone at the top and driving a culture of cybersecurity awareness throughout the organization.
The board of directors, in this setting, emerges as the critical line of defense, functioning at the strategic apex to safeguard enterprises against cyber threats.
i. Why Industrial Sectors are Unique

The industrial sector includes businesses like manufacturing, energy, oil and gas, and utilities, which are heavily reliant on Operational Technology (OT) systems in addition to IT systems. This integration exposes them to unique vulnerabilities, where a cyberattack could result in not just data theft, but potentially catastrophic physical consequences—if systems controlling physical machinery are compromised, the results can be destructive and even life-threatening.
ii. Why Boards Matter
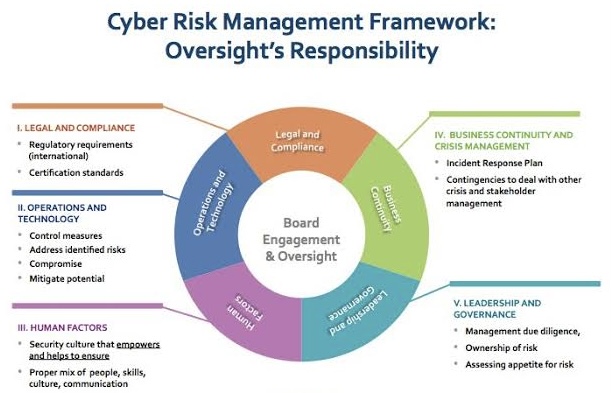
Here’s why boards hold a critical position in industrial cybersecurity:
o Strategic Oversight: Boards provide strategic direction and ensure the company prioritizes cybersecurity at the highest level.
o Resource Allocation: They allocate sufficient resources to build and maintain a strong cybersecurity posture.
o Risk Management: Boards oversee risk management strategies, ensuring cybersecurity risks are adequately identified, mitigated, and communicated.
iii. Beyond Basic Awareness

While board members don’t necessarily need to be cybersecurity experts, a basic understanding of the evolving threat landscape is essential. They should be able to ask critical questions and hold management accountable for cybersecurity preparedness.
iii. The Role of the Board in Cybersecurity
A. Strategic Oversight and Governance
The board of directors plays a quintessential role in defining the strategic direction for a company’s cybersecurity initiatives. Unlike operational teams, who are tasked with the implementation of cybersecurity measures, the board ensures that these measures are aligned with overall business objectives and risk management frameworks. This alignment is vital because a misalignment can either expose the organization to cyber risks or misdirect resources away from critical threats.
B. Resource Allocation
Cybersecurity requires significant investment in technologies, personnel, and training. Directors on the board have the authority to influence and approve these investments, ensuring that adequate resources are allocated to safeguard against and respond to cyber incidents. They must balance expenditures on cybersecurity with other financial considerations, maintaining sustainability and growth.
C. Risk Management and Cyber Resilience
Industrial firms operate in sectors where the impact of a cyber-attack can transcend conventional financial losses, potentially leading to severe physical and environmental consequences. Therefore, boards are uniquely positioned to influence how risk is comprehended and managed. By adopting a macro-level view of cyber risks as part of the organization’s overall risk portfolio, directors can push for resilience strategies that not only protect information assets but also physical operations and personnel.
D. Expertise and Experience
To fully understand and oversee cybersecurity strategies, boards themselves must evolve. This evolution includes incorporating directors who possess deep expertise in technology and cybersecurity. Their knowledge is crucial, as it enables the entire board to make informed decisions about risk management, cybersecurity investments, and incident response strategies.
E. Legal and Regulatory Compliance
With increasing scrutiny from regulators on how data and systems are protected, boards must also ensure that their respective companies comply with a myriad of cybersecurity regulations and laws. Non-compliance can result in substantial penalties, loss of customer trust, and a damaged reputation. Board members should, therefore, prioritize regulatory compliance as an integral aspect of the cybersecurity strategy.
F. Crisis Management and Recovery
In the wake of a security breach, the board’s involvement in crisis management and recovery is paramount. Their leadership can determine the speed and effectiveness of the response, impacting how quickly the company can return to normal operations and how the incident is communicated to stakeholders, including investors, regulators, and customers.
G. Education and Culture
Boards must also champion a culture of cybersecurity. This begins with their own education – board members must be informed about the latest cyber threats and risk management trends to make knowledgeable decisions. Equally, they should promote cybersecurity awareness and practices across all levels of the organization.
iv. Key Questions for Boards
Here are some key questions boards should ask regarding cybersecurity:
o Does the company have a comprehensive cybersecurity strategy aligned with business objectives?
o Are there clear roles and responsibilities for cybersecurity within the organization?
o How are we investing in cybersecurity training for employees at all levels?
o How regularly are our cybersecurity defenses tested and evaluated?
o Do we have a clear incident response plan in case of a cyberattack?
v. Challenges Boards Face in Cybersecurity Oversight

The primary challenge is the rapid technological change and increasingly sophisticated threat landscape. Moreover, board members often come from diverse backgrounds, and not all may have familiarity with the specific technical challenges associated with cybersecurity in industrial settings.
To overcome these challenges, continuous education is vital. Boards might consider regular briefing sessions with cybersecurity experts and investing in their members’ understanding of IT and OT systems.
Additionally, boards can establish a dedicated cybersecurity committee or seek regular insights from external cyber security consultants to stay abreast of best practices and the latest threats.
vi. Collaboration is Key

Effective cybersecurity requires collaboration between boards, management, and the cybersecurity team. Open communication and a culture of security awareness are essential for a robust defense.
vii. The Final Line of Defense

While firewalls and advanced security software are vital, a well-informed and engaged board of directors serves as the ultimate line of defense for industrial companies facing the ever-present threat of cyberattacks. By actively overseeing cybersecurity strategy, resource allocation, and risk management, boards can empower their companies to operate securely and navigate the digital age with confidence.
viii. The Future of Industrial Cybersecurity

As cyber threats continue to evolve, boards must remain vigilant and adapt their oversight practices. Continuous learning,embracing new technologies, and fostering a culture of security awareness will be crucial for boards to ensure the long-term cybersecurity resilience of their industrial companies.
ix. Conclusion

As cyber threats continue to target industrial sectors with increasing complexity and potential for severe implications, the role of the board in cybersecurity oversight becomes more critical than ever.
It is not merely about compliance or risk management but about strategic foresight—anticipating threats, investing in robust defense mechanisms, and leading the charge in governance that treats cybersecurity as a top-tier strategic concern.
Boards in industrial organizations must go beyond traditional governance roles and actively engage in, and understand, the nuances of cybersecurity management.
By embracing their role as the ultimate safeguard against cyber threats, boards can enhance their company’s resilience and secure their operational future.
For industrial companies, where stakes include the safety of people and environments, robust leadership from the board, acting with informed, proactive cyber risk strategies, can indeed be the final line of defense in an increasingly perilous digital world.
x. Further references
X · jdiazandreu5 likes · 1 month agoJuan Diaz-Andreu
X · kannagoldsun1 month agoBoards of directors: The final cybersecurity defense for industrials
McKinsey & Companyhttps://www.mckinsey.com › cybe…Cybersecurity | Digital
KPMGhttps://kpmg.com › articles › sec-fi…SEC’s final cybersecurity rules: A board lens