
Navigating the Nuances: Zero Trust, SDP, and VPN
In the evolving landscape of cybersecurity and network architecture, concepts such as Zero Trust, Software Defined Perimeter (SDP), and Virtual Private Networks (VPN) represent pivotal strategies for protecting digital assets. While they share common goals of securing network access and data, their approaches, implementations, and use cases exhibit distinct differences.
i. Zero Trust: A Philosophy of Inherent Distrust
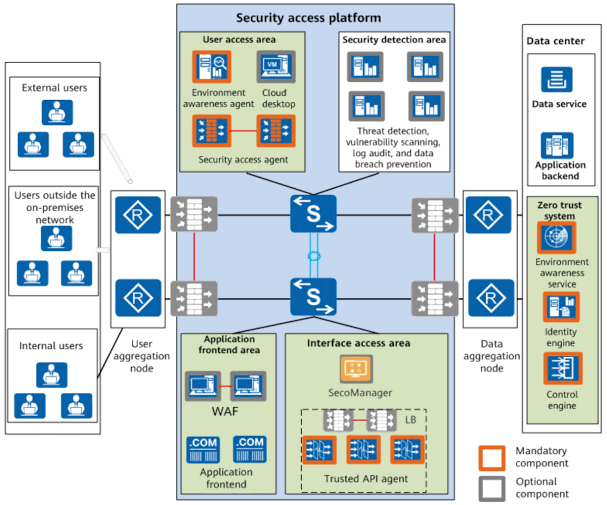
A. Zero Trust: A Security Philosophy
Zero trust is a security framework, not a specific technology. It enforces the principle of “never trust, always verify,” continuously authenticating users and devices before granting access to resources. This granular approach minimizes the attack surface and potential damage from breaches.
Unlike traditional security models that enforce stringent defenses at the perimeter but assume trust once inside, Zero Trust treats all users and devices, both inside and outside the network, as potential threats. Access to resources is granted based on strict verification, necessitating continuous authentication and authorization regardless of the user’s location or network segment.
B. Key Characteristics:
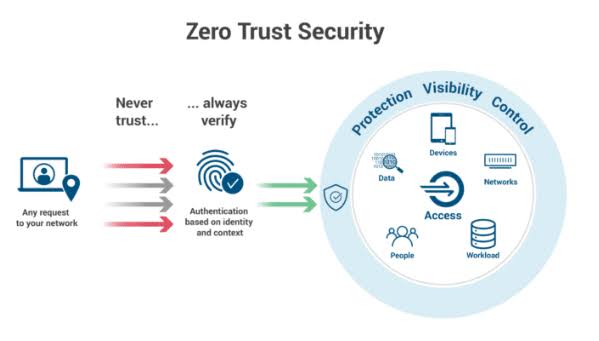
o Identity-Centric: Focuses on who is trying to access what, instead of where the access request comes from.
o Microsegmentation: Divides the network into small, controlled segments to limit lateral movement during a breach.
o Least Privilege Access: Users and devices are granted the minimum level of access required to perform their functions, reducing the attack surface.
ii. Software Defined Perimeter (SDP): The Invisible Shield
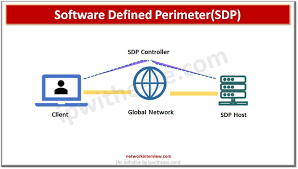
A. SDP: Carving a Secure Path
SDP creates a secure software-defined perimeter around specific applications. Unlike VPNs that grant broad network access, SDPs restrict access to authorized users and devices for designated applications. This reduces the risk of unauthorized lateral movement within the network.
SDP, often seen as an instantiation of the Zero Trust model, creates a dynamic, context-aware, virtual boundary around network resources. It makes resources effectively “invisible” and inaccessible to unauthorized users. Access to network services is not granted based on one’s physical network connection but through a secure and authenticated gateway that verifies the identity and context of the access request before allowing entry.
B. Key Characteristics:
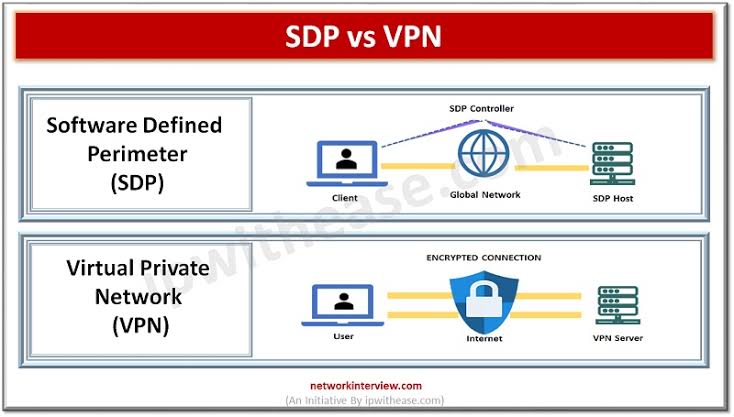
o Dynamic Access Control: Provides access based on real-time assessment of trust and context, adapting as these factors change.
o Application-Level Segmentation: Focuses on securing access to applications rather than network segments.
o Stealth Mode: Resources are not discoverable by unauthorized entities, reducing the likelihood of being targeted.
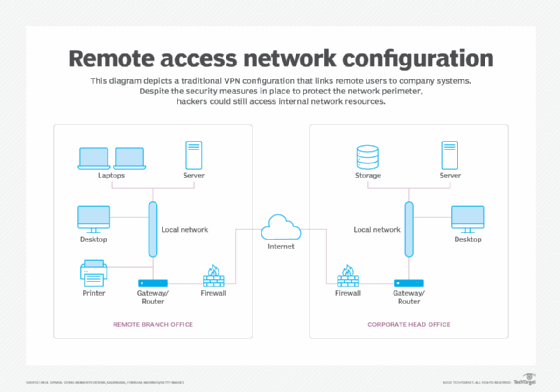
iii. Virtual Private Network (VPN): The Encrypted Tunnel
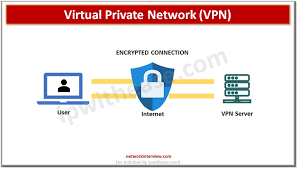
A. VPN: The Legacy Gateway
VPNs establish encrypted tunnels between user devices and the corporate network. While effective for remote access, VPNs can be cumbersome to manage and provide full network access, potentially exposing internal resources if compromised.
By creating a “tunnel,” VPNs encapsulate and encrypt data packets, ensuring that data transmitted between the user and the network remains private and secure from eavesdropping.
B. Key Characteristics:
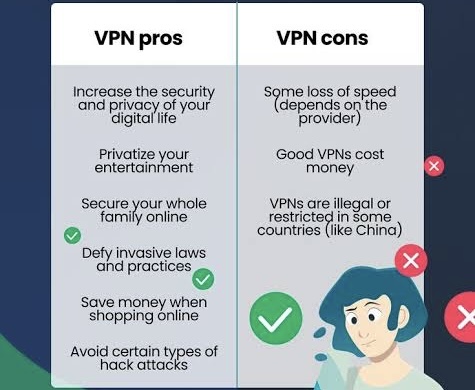
o Encrypted Communication: Ensures data privacy and integrity by encrypting the data in transit.
o Remote Access: Facilitates secure access to enterprise resources for remote and mobile workers.
o Network-Level Connectivity: Provides users with access to a network, exposing them to internal resources as if they were directly connected to the private network.
iv. Comparison and Use Cases
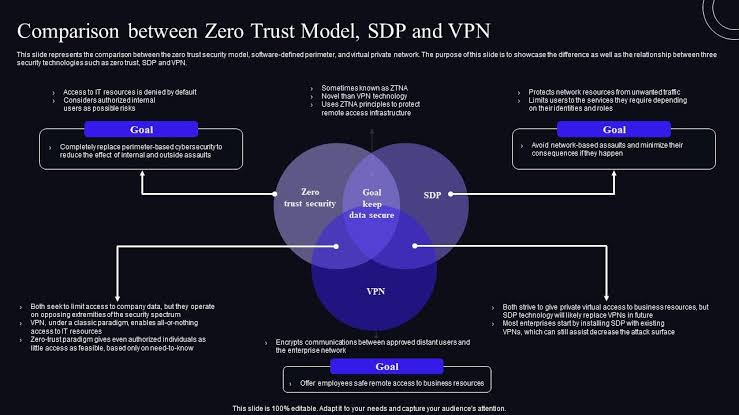
o Trust and Access Control: Zero Trust and SDP emphasize continuous verification and granular control over access, making them suitable for environments where security needs to dynamically adapt to changing contexts. VPN, while secure, operates under a different trust model, assuming that users within the VPN are authorized to access network resources.
o Visibility and Segmentation: Both Zero Trust and SDP offer superior visibility into user activity and allow for more nuanced segmentation compared to traditional VPN solutions. This segmentation is crucial for minimizing the impact of breaches.
o Ease of Deployment and Compatibility: VPNs have been around longer and are widely supported across various devices and operating systems, making them easier to deploy in some scenarios. However, the increasing adoption of cloud services and the need for more flexible security models are driving the adoption of Zero Trust and SDP frameworks.
v. Differences

o Scope of Protection: Zero Trust and SDP focus on securing individual access to specific resources, prioritizing identity and context-based access controls. VPNs, on the other hand, secure broader network connections, providing access to entire network infrastructures.
o Access Control Mechanisms: Zero Trust and SDP employ granular access controls based on user identity, device trust, and contextual factors. VPNs typically provide access based on network credentials, offering less granularity in access control.
o Visibility and Segmentation: SDP and Zero Trust emphasize segmentation and limit visibility to resources, reducing the attack surface. VPNs, while encrypting data, provide broader visibility into the network, potentially exposing more resources to attackers.
vi. Choosing the Right Security Solution
The ideal solution depends on your specific needs. Zero trust provides a robust security foundation, while SDPs offer a secure and manageable approach for application access. VPNs remain suitable for remote access scenarios but may require stricter access controls.
vii. Conclusion

Choosing between Zero Trust, SDP, and VPN depends on an organization’s specific security requirements, existing network infrastructure, and overarching digital transformation goals.
As cyber threats evolve, adopting a strategy that not only addresses current needs but is also scalable and flexible for future challenges becomes paramount.
While VPNs continue to offer a reliable solution for secure remote access, the principles of Zero Trust and the methodologies embodied in SDP represent the next step in the journey towards more adaptive, resilient, and effective cybersecurity architectures.
A blended approach, leveraging the strengths of each according to the organization’s unique context, often yields the best results in fortifying cybersecurity defenses.
viii. Further references
VPN vs. zero trust vs. SDP: What’s the difference? – TechTarget
Zscalerhttps://www.zscaler.com › zpediaWhat’s the Difference Between SDP and VPN? | Zpedia
InstaSafehttps://instasafe.com › blog › zero-…Zero Trust vs VPN vs SDP: Understanding the Difference
Cyolohttps://cyolo.io › blog › zero-trust-v…Zero Trust vs. VPN vs. SDP: Which One Should You Choose?
ResearchGatehttps://www.researchgate.net › …PDFSDP vs. VPN vs. Zero-Trust Networks (ZTN)
LinkedIn · Meriem SMACHE10+ reactions · 1 year agoMeriem SMACHE – VPN vs. zero trust vs. SDP
IPknowledge.nethttps://www.ipknowledge.net › wh…The Difference Between SDP users and VPN users
