The Time is Now: Managing Risks of New Technologies in the Financial Industry
The financial services sector stands on the cusp of a technological revolution.
As they rapidly adopt emerging technologies like artificial intelligence (AI), blockchain, and cloud computing to stay competitive, they must also confront a growing threat: cyberattacks.
The financial services industry is a prime target for cybercriminals due to the vast amount of sensitive data it holds.
A successful attack can have devastating consequences, causing financial losses, reputational damage, and even disruptions to critical infrastructure.
i. Understanding the Pace of Change
In recent years, financial services have seen rapid technological evolution. AI is refining predictive models and customizing financial advice.
Blockchain is rethinking how transactions are recorded and validated, aiming for greater transparency and security. Meanwhile, IoT devices are personalizing the insurance industry, adapting premiums and policies based on data collected from connected devices.
However, this fast pace of digital transformation brings about significant cybersecurity challenges. These challenges must be managed not only to protect the financial health of institutions but also to safeguard the trust and personal data of millions of customers.
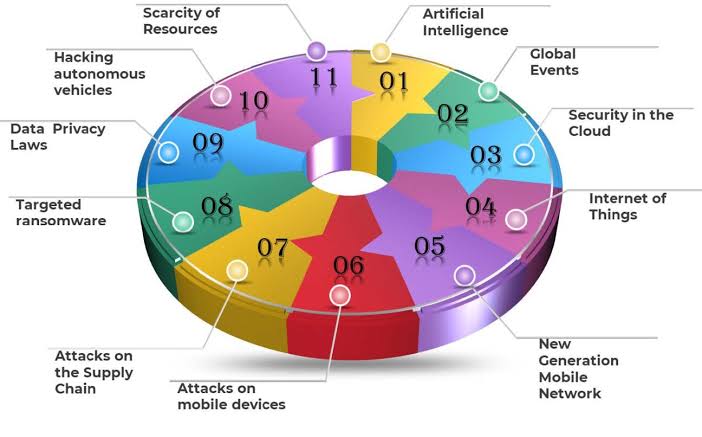
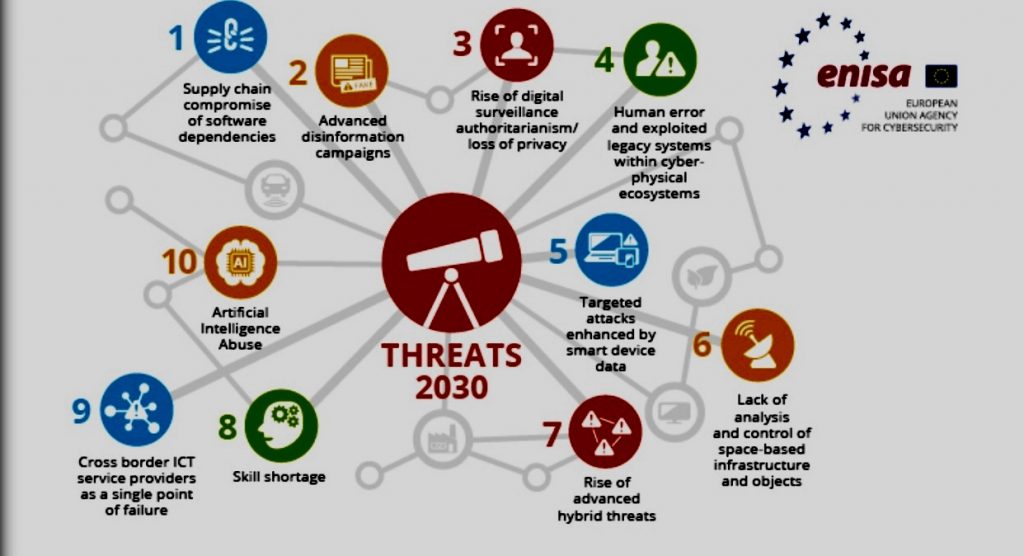
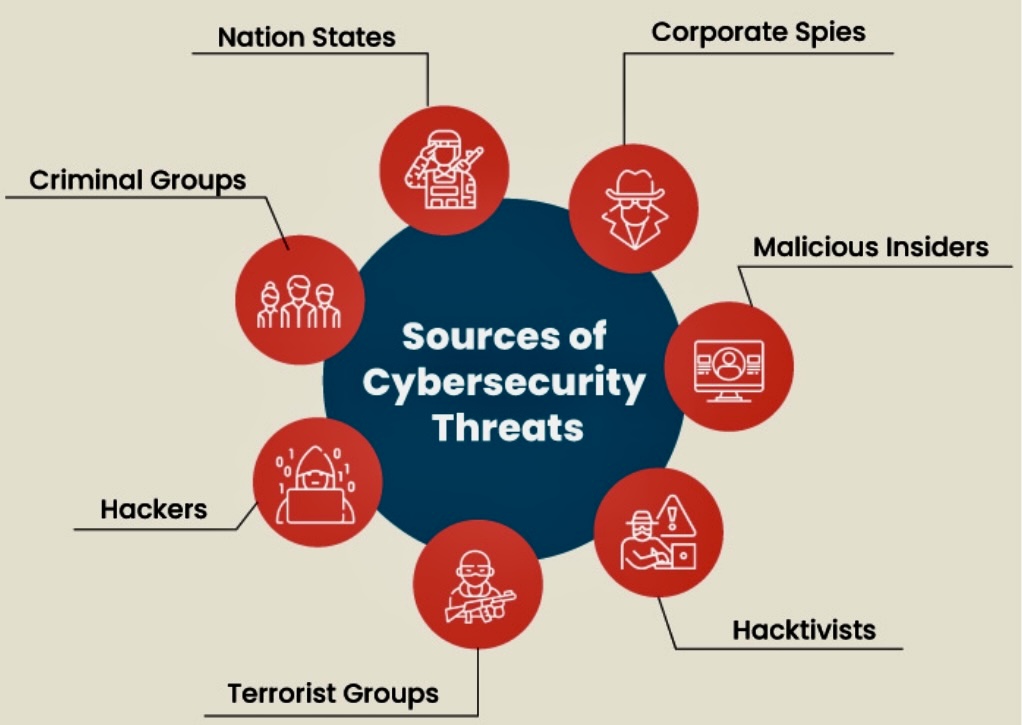
ii. The Evolving Threat Landscape

Cyberattacks are becoming more sophisticated and targeted. Here’s a glimpse into the evolving threat landscape:
o Exploiting New Technologies: Cybercriminals are quick to identify vulnerabilities in emerging technologies like AI and cloud platforms.
o Supply Chain Attacks: Targeting third-party vendors with weaker cybersecurity measures can give attackers a backdoor into a financial institution’s network.
o Ransomware on the Rise: Ransomware attacks, where attackers encrypt data and demand a ransom for its release,pose a significant threat to financial institutions.
iii. The Intersection of Innovation and Vulnerability
Emerging technologies promise to revolutionize the financial sector by increasing efficiency, accessibility, and profitability.
However, they also introduce complex risk factors that need immediate and thorough addressing:
A. Data Breaches and Privacy Concerns
Emerging technologies rely heavily on data, making financial institutions treasure troves of personal information, ripe for cyber attacks. AI and IoT amplify these concerns, with large datasets and connected devices providing multiple entry points for unauthorized access.
B. Compliance and Regulatory Challenges
Financial institutions are among the most heavily regulated sectors. Adapting to new technologies while maintaining compliance with all applicable laws—such as GDPR, CCPA, or the evolving landscape of fintech regulations—requires a delicate balance and foresight in implementation strategies.
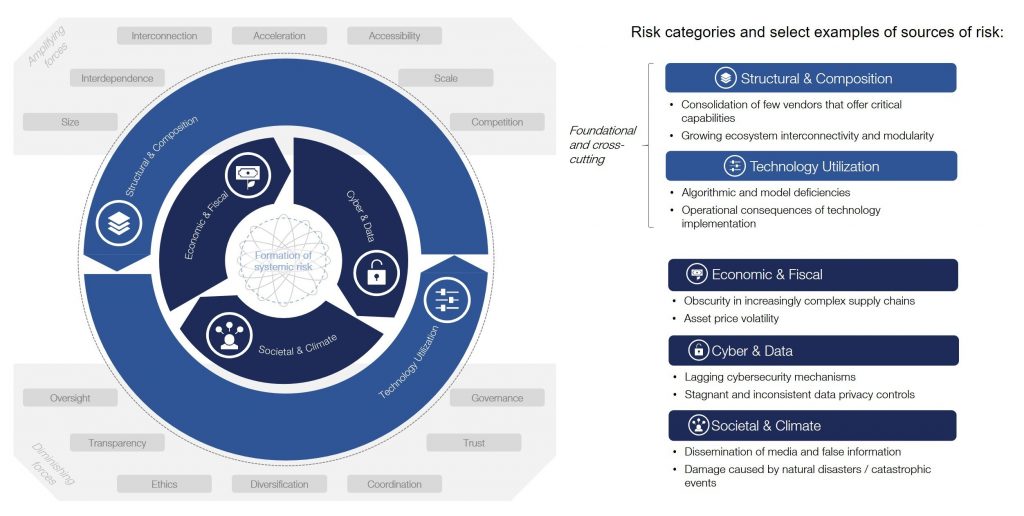
C. Dependency and System Complexities
New technologies often integrate with or replace existing systems, creating complex dependencies. Any failure, whether due to technical malfunctions or cyber attacks, can lead to severe operational disruptions and financial losses.
D. Emerging Threat Vectors
Cybercriminals are simultaneously evolving, leveraging AI and other technologies to create more sophisticated attack methods. Phishing attacks have become more targeted, ransomware more damaging, and the strategies more deceptive than ever before.
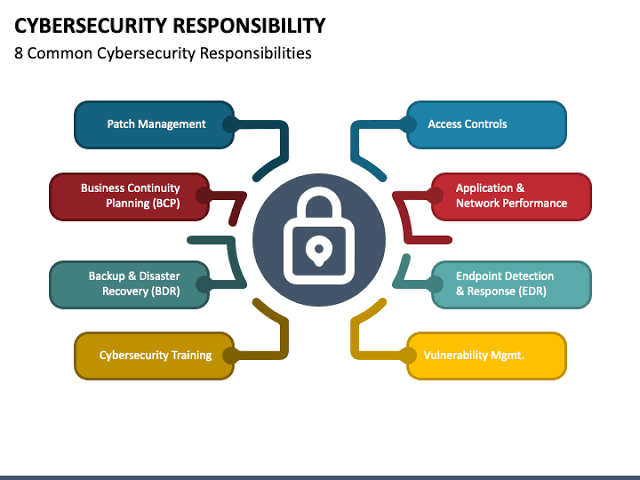
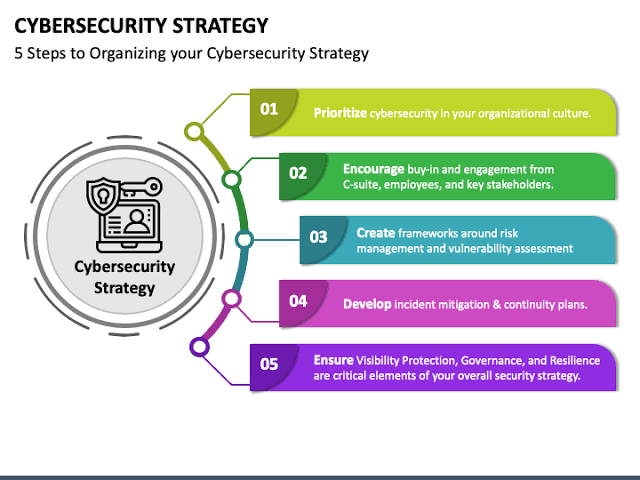
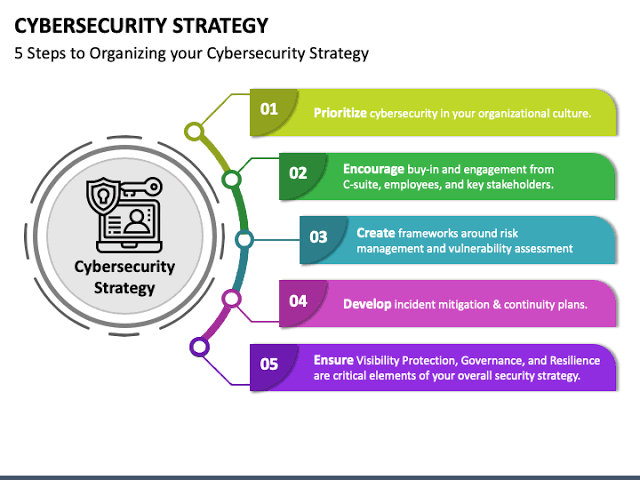
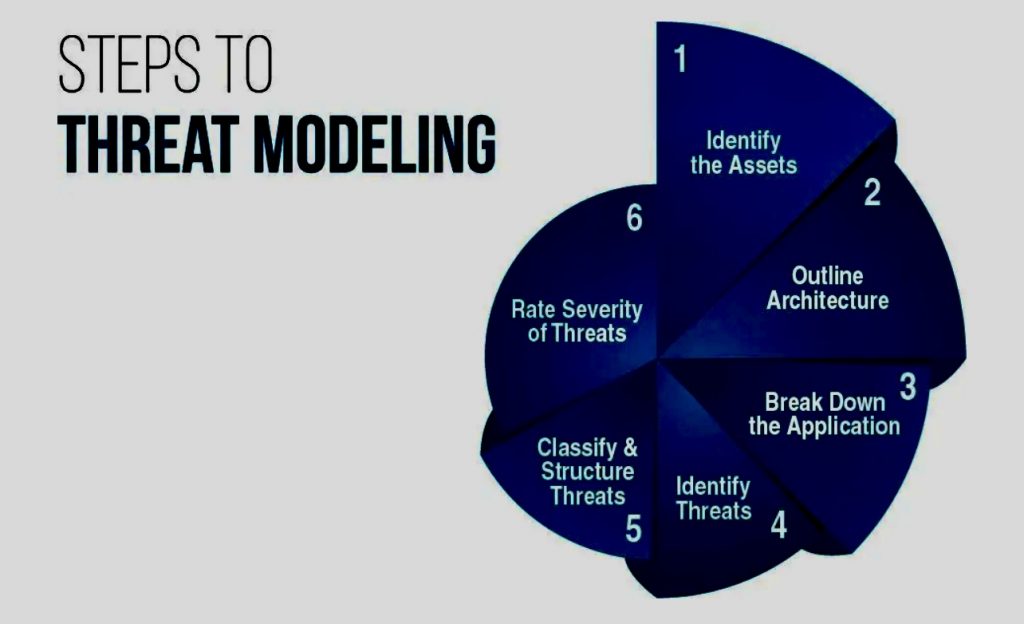
iv. Strategies for Derisking
To manage these risks while harnessing the benefits of emerging technologies, financial institutions must adopt a multi-faceted approach to cybersecurity:
A. Proactive Threat Intelligence
Institutions should invest in real-time threat intelligence solutions that provide early warnings about new types of attacks and potential vulnerabilities.
B. Robust Regulatory Compliance
Technology implementation must go hand-in-hand with compliance strategies designed to meet all current and anticipated regulations.
C. System Redundancies and Recovery Plans
Building resilient systems that can withstand attacks and quickly recover from them is critical. This involves not only technical redundancies but also clear, efficient crisis management protocols.
D. Regular Audits and Updates
Continuous testing and updates to security systems ensure defenses keep pace with changing attack vectors. Regular audits help identify and mitigate potential vulnerabilities before they can be exploited.

E. Human Factor Training
Employees should receive regular training on the latest cybersecurity practices and threats. Human error often remains one of the weakest links in security chains.
v. Derisking the Future: Building a Secure Foundation

Financial institutions can’t afford to be complacent. Proactive measures are essential to derisking emerging technologies:
o Security by Design: Integrate security considerations from the very beginning when implementing new technologies.
o Comprehensive Risk Assessments: Conduct thorough risk assessments to identify and prioritize vulnerabilities in emerging technologies.
o Employee Training and Awareness: Regularly train employees on cybersecurity best practices and how to identify phishing attempts or social engineering tactics.
o Zero-Trust Architecture: Implement a zero-trust security model that verifies every user and device before granting access to sensitive data or systems.
o Collaboration is Key: Cybersecurity is not just an IT issue but a strategic business imperative. As such, there should be continuous collaboration between IT, business leadership, and external cybersecurity vendors and consultants to close any gaps in understanding and implementation.
vi. The Role of Artificial Intelligence

While artificial intelligence presents its own set of cybersecurity challenges, it also offers solutions for derisking emerging technologies. AI-powered cybersecurity systems can analyze vast amounts of data in real-time, identify patterns indicative of cyber threats, and autonomously respond to mitigate risks.
vii. Blockchain for Security
Blockchain technology, often associated with cryptocurrencies, holds promise for enhancing cybersecurity in financial services. Its decentralized and immutable nature makes it inherently resistant to tampering and fraud. Implementing blockchain-based solutions for identity management, secure transactions, and data integrity can bolster cybersecurity in the financial sector.
viii. The Time to Act is Now
The cyber clock is ticking. Financial institutions that prioritize cybersecurity and proactively derisk emerging technologies will be better positioned to thrive in the digital age. By building a robust security posture, they can protect their customers’ data, maintain trust, and ensure the future of financial services is secure and innovative.
ix. The Road Ahead
The journey towards a secure future for financial services is ongoing. Continuous vigilance, embracing new security solutions, and fostering a culture of cybersecurity awareness will be essential for financial institutions to navigate the ever-evolving cyber threat landscape. By prioritizing cybersecurity today, they can pave the way for a more resilient and trustworthy financial ecosystem tomorrow.
x. Conclusion

As financial institutions embrace emerging technologies to drive innovation and competitive advantage, the need to derisk these technologies becomes increasingly urgent.
By prioritizing cybersecurity, conducting thorough risk assessments, and leveraging technologies like artificial intelligence and blockchain, financial services can navigate the evolving threat landscape and build a more resilient infrastructure for the future.
Failure to do so not only jeopardizes the security and trust of customers but also exposes institutions to regulatory scrutiny and financial losses.
Through diligent planning, comprehensive risk management frameworks, and a culture that prioritizes cybersecurity as a cornerstone of technological adoption, financial institutions can secure their operations and their customers’ trust in this digital age.
xi. Further references
The cyber clock is ticking: Derisking emerging technologies in financial services
LinkedIn · Menda Sims10+ reactions · 1 month agoMenda Sims – The cyber clock is ticking
LinkedIn · Josh Welle1 month agoJosh Welle – The cyber clock is ticking
McKinsey & Companyhttps://www.mckinsey.com › a-byt…A byte out of crime
SponsoredLogRhythmhttps://www.logrhythm.com › guides › security-firstGuide to Reduce Cyber Risk
pat.edu.euhttps://pat.edu.eu › 2024/03PDFPAT FINTECH WEEKLY ZEITGEIST
Hong Kong Digital Currency Academyhttps://www.hkdca.com › other-res…other research report list page
PwChttps://www.pwc.com › library › n…Net zero and insurance underwriting: The clock is ticking