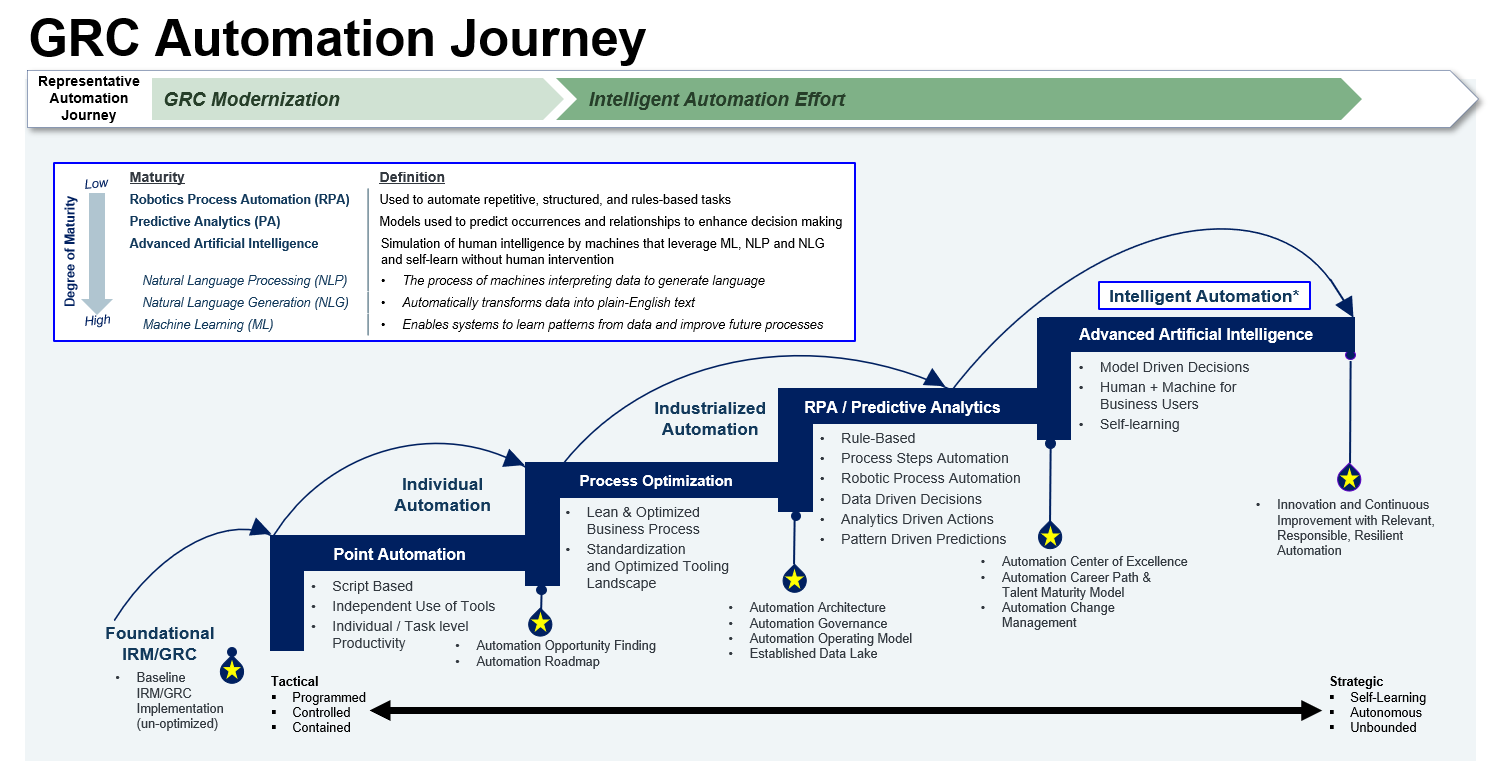
Automating Internal Controls: A GRC Management Boost
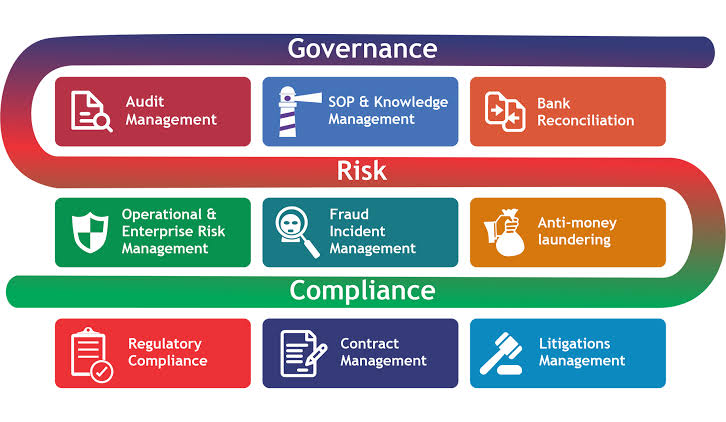
Effective governance, risk management, and compliance (GRC) hinge on well-defined, documented, and monitored internal controls. But managing these controls manually can be cumbersome and error-prone.
This is where automated solutions step in, offering a powerful boost to GRC management.
Automated solutions streamline the process of defining internal controls by providing templates and libraries of best practices. They can also automate the documentation process, ensuring controls are clearly defined and readily accessible.
Additionally, automation can continuously monitor the effectiveness of controls, identifying any gaps or weaknesses.
This allows organizations to proactively address risks and ensure compliance.
i. How automated solutions enhance GRC management
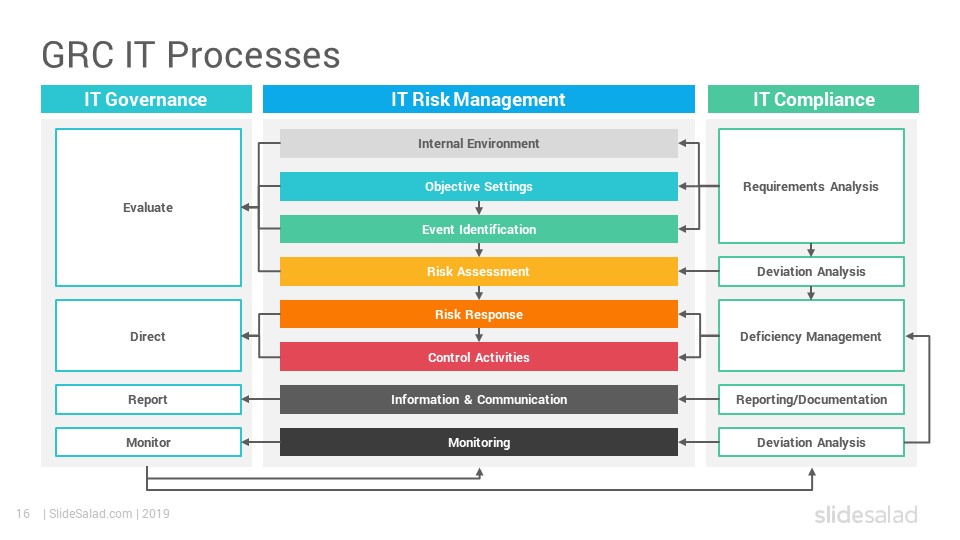
o Streamlined Definition: Automated solutions offer pre-built control libraries and templates, accelerating the process of defining internal controls. These tools can also guide users through the process, ensuring all essential elements of a control are captured.
o Enhanced Documentation: Manual documentation is time-consuming and error-prone. Automation eliminates these issues by generating control descriptions, narratives, and flowcharts automatically. This ensures consistency and accuracy in control documentation.
o Continuous Monitoring: Automated solutions can continuously monitor the functioning of internal controls. This includes tasks like tracking control activities, identifying exceptions, and generating reports. Real-time monitoring allows for prompt identification and rectification of control weaknesses.
o Cost Reduction: By streamlining GRC processes, organizations can reduce the costs associated with manual compliance management and mitigate the financial risks of non-compliance.
o Regulatory Agility: Automated solutions can quickly adapt to changes in regulatory requirements, ensuring that organizations remain compliant with the latest standards.
ii. Defining Internal Controls
A. Standardization and Consistency
Automated solutions bring a level of standardization and consistency to the process of defining internal controls. By utilizing a centralized platform, organizations can create and disseminate a standardized set of control definitions across various departments. This ensures that everyone adheres to the same guidelines and minimizes the discrepancies that often arise with manual processes.
B. Access to Best Practices
Modern GRC software often comes with built-in libraries of industry best practices and regulatory requirements. These resources help organizations define controls that are not only compliant with current regulations but also aligned with industry standards. This access to up-to-date information allows businesses to stay ahead of regulatory changes and adopt best practices swiftly.
C. Efficient Risk Assessment
Automated tools can integrate with other business systems to assess risks more efficiently. By leveraging data analytics and machine learning, these tools can identify potential risks and suggest appropriate controls. This proactive approach enables organizations to define controls that mitigate identified risks effectively.
iii. Documenting Internal Controls
A. Centralized Documentation
Automated GRC solutions provide a centralized repository for all documentation related to internal controls. This centralization simplifies the process of accessing, updating, and managing control documentation. It also ensures that all relevant stakeholders have access to the most current information, reducing the likelihood of miscommunication and outdated practices.
B. Version Control and Audit Trails
One of the significant advantages of automated solutions is the ability to maintain version control and audit trails. Every change to control documentation is recorded, providing a clear history of modifications. This feature is invaluable during audits, as it demonstrates the organization’s commitment to maintaining accurate and compliant documentation.
C. Collaboration and Workflow Automation
Automated GRC tools facilitate collaboration among various stakeholders by providing workflow automation features. These tools streamline the process of creating, reviewing, and approving control documentation, ensuring that tasks are completed efficiently and deadlines are met. Workflow automation not only saves time but also enhances the accuracy and thoroughness of the documentation process.
iv. Monitoring Internal Controls
A. Continuous Monitoring
Automated solutions enable continuous monitoring of internal controls, allowing organizations to detect and address issues in real-time. This ongoing oversight reduces the risk of control failures and ensures that any deviations are promptly identified and corrected. Continuous monitoring also provides organizations with up-to-date insights into their compliance status, enabling proactive risk management.
B. Dashboards and Reporting
Modern GRC systems offer advanced dashboards and reporting capabilities that provide a comprehensive overview of control performance. These dashboards present key metrics and indicators, allowing stakeholders to monitor the effectiveness of controls at a glance. Customizable reports can be generated to meet specific regulatory requirements or to provide detailed insights for internal reviews.
C. Automated Testing and Alerts
Automated GRC solutions can conduct regular testing of internal controls to ensure they are functioning as intended. These tests can be scheduled at predetermined intervals, freeing up valuable resources and ensuring ongoing compliance. Additionally, automated alerts can notify relevant personnel of any issues or anomalies, enabling swift corrective actions.
v. Conclusion
In an era where regulatory environments are continually evolving and becoming more complex, automated solutions provide a significant advantage in GRC management.
By defining, documenting, and monitoring internal controls more efficiently and effectively, these solutions help organizations maintain compliance, mitigate risks, and enhance overall operational integrity.
The integration of automation in GRC processes is no longer optional but a necessity for organizations aiming to achieve robust governance and sustained compliance.
As technology continues to advance, the capabilities of automated GRC solutions will only expand, further solidifying their role as indispensable tools in the modern business landscape.
vi. Further references
Swiss GRChttps://swissgrc.com › internal-con…Solution for Internal Control System (ICS)
6clickshttps://www.6clicks.com › blogWhat is Governance, Risk, and Compliance (GRC) software?
Metricstreamhttps://www.metricstream.com › G…Governance, Risk, and Compliance (GRC) framework
ResearchGatehttps://www.researchgate.net › 2211…(PDF) Governance, Risk & Compliance (GRC …
OCEGhttps://www.oceg.org › internal-co…Internal Control Management Technology Illustrated
Centraleyeshttps://www.centraleyes.com › best…The 11 Best GRC Tools for 2024
LinkedIn · iRM10+ reactions · 1 year agoWhat is GRC Automation? Governance, Risk, and Compliance …
Compact Magazine | KPMGhttps://www.compact.nl › articles › i…Implementing a new GRC solution
PwC Australiahttps://www.pwc.com.au › …PDFWhite Paper – Governance, Risk Management and Compliance