
Beyond Compliance: Building Resilience in the EU Cybersecurity Landscape post-NIS 2.0
Strengthening cybersecurity in the European Union (EU) is crucial given the increasing number of cyber attacks affecting businesses and critical infrastructure. Legislative measures such as the NIS (Network and Information Systems) Directive, which is the EU’s first piece of cybersecurity legislation, and its updates, are fundamental to this effort.
i. Evolution of NIS Directive:

The initial NIS Directive, established in 2016, sought to enhance the overall resilience of critical infrastructure and essential services against cyber threats. With the threat landscape continually evolving, the need for an updated directive became evident. NIS Directive 2.0 is expected to provide a comprehensive framework that addresses emerging challenges, including sophisticated cyber-attacks and rapidly advancing technologies.
ii. Key Components of NIS Directive 2.0:

a. Extended Scope:
NIS Directive 2.0 is likely to broaden its scope to cover a wider range of sectors, including digital services, cloud computing, and emerging technologies. By doing so, it aims to encompass a more extensive array of potential targets for cyber threats, ensuring a more holistic approach to cybersecurity.
b. Enhanced Cooperation:
Collaboration among EU member states is crucial for effective cybersecurity. NIS Directive 2.0 is expected to emphasize increased cooperation, encouraging the sharing of threat intelligence, best practices, and incident response strategies. This collective approach aims to strengthen the EU’s overall cybersecurity posture.
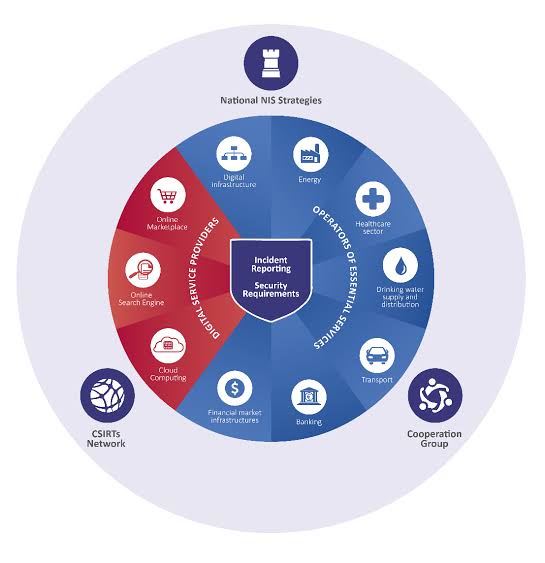
c. Incident Reporting and Response:
Improving incident reporting mechanisms is a focal point of NIS Directive 2.0. Establishing clear guidelines for reporting cybersecurity incidents promptly and effectively will facilitate a quicker response and mitigation of potential damages. This proactive approach is integral to minimizing the impact of cyber-attacks.
iii. Implementation Challenges:
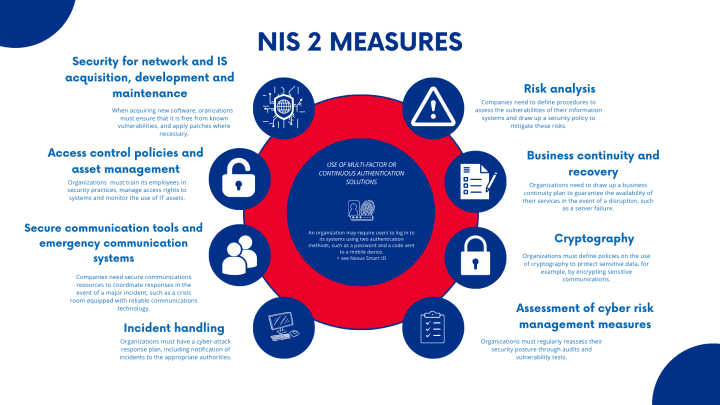
While NIS Directive 2.0 holds promise, its successful implementation faces various challenges. These include ensuring uniform adoption across member states, addressing the diverse cybersecurity maturity levels, and staying ahead of rapidly evolving cyber threats. Harmonizing regulations and fostering a culture of cybersecurity will be vital for overcoming these challenges.
iv. Benefits of NIS Directive 2.0:
A. Improved cybersecurity posture: Increased focus on risk management and incident reporting will lead to a more resilient and responsive EU cybersecurity landscape.
B. Enhanced protection for critical infrastructure: Expanding the scope protects essential services from cyberattacks.
C. Harmonized approach: Creates a level playing field for businesses across the EU.
D. Greater consumer trust: Increased transparency and accountability build trust in digital services.
Here’s an overview of how the EU is aiming to strengthen cybersecurity with the NIS 2.0 Directive and what may lie beyond.
v. NIS Directive 2.0 Key Points:
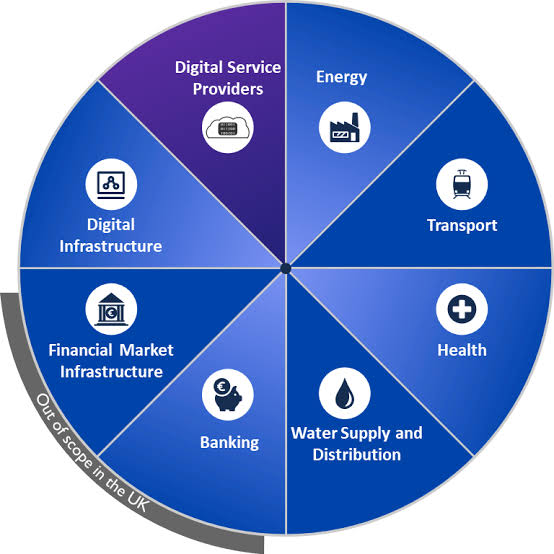
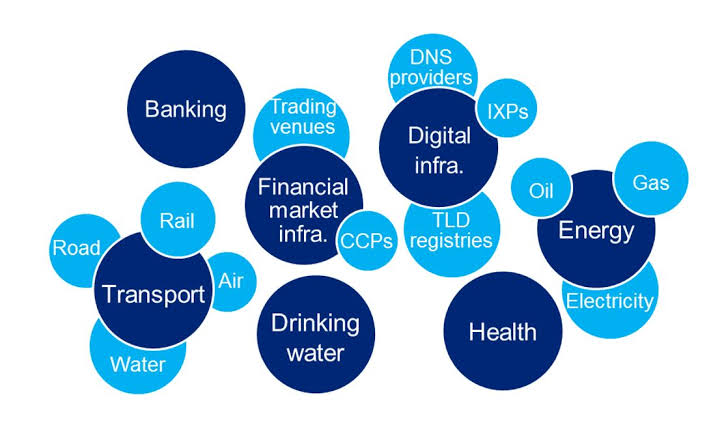
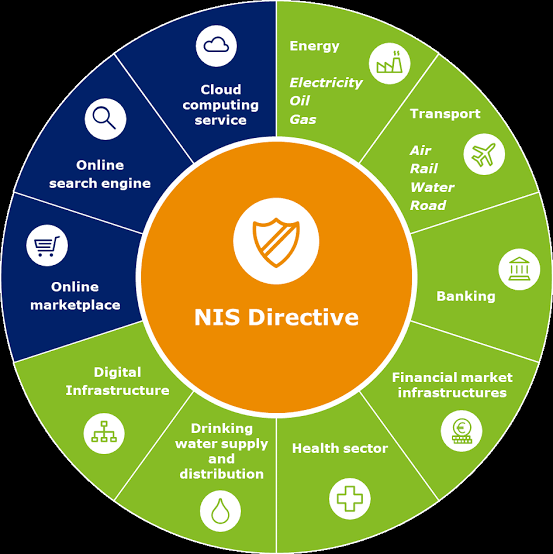
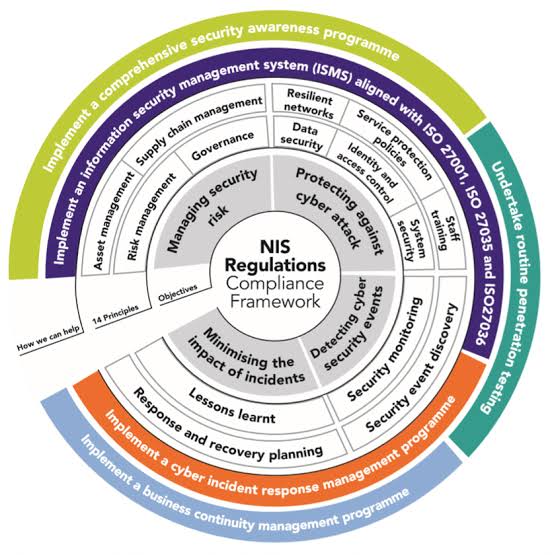
A. Broader Scope: The updated directive expands on the sectors and types of entities that will be considered essential and therefore subject to stricter security requirements. This includes essential entities like energy, transport, banking, health, as well as important entities such as digital providers, public administration, and space.
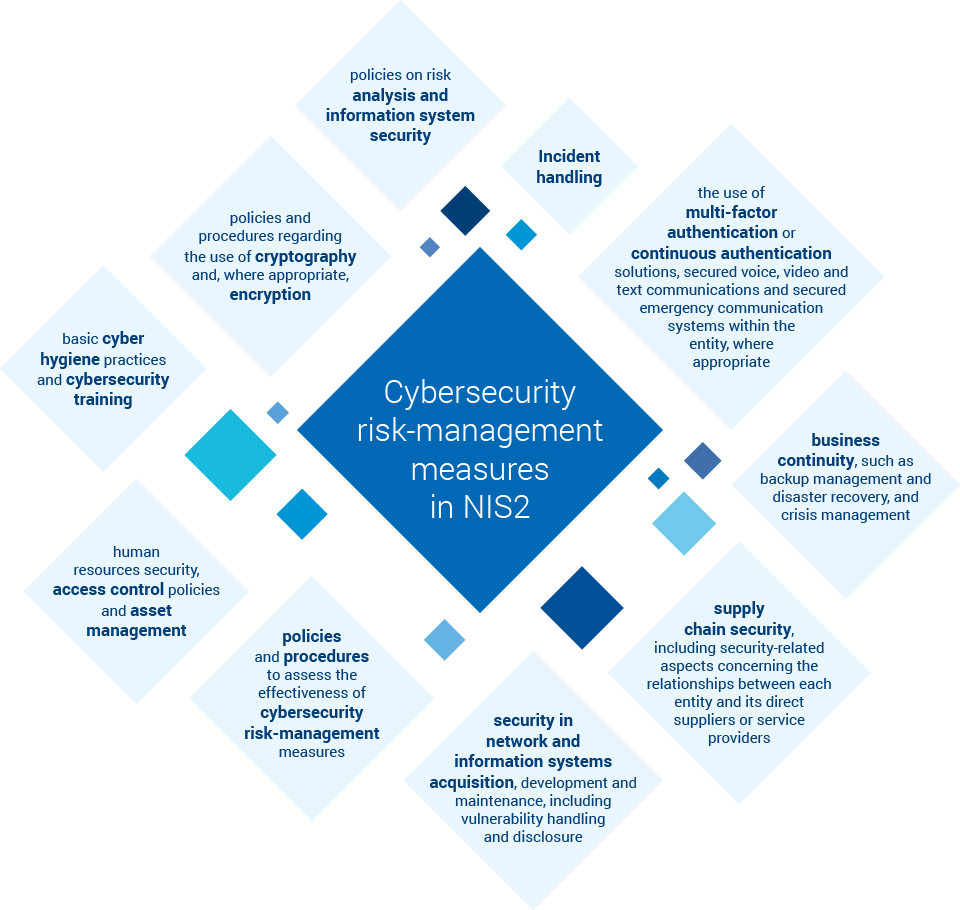
B. Stricter Security Requirements: There will be a focus on enhancing the security requirements from a technical and organizational perspective, incorporating risk management measures, and ensuring secure network and information system configurations.
C. Increased Reporting Obligations: Entities will have to report significant cyber incidents to relevant national authorities within a shorter time frame to ensure quick response and recovery, and to facilitate a coordinated EU-wide approach.
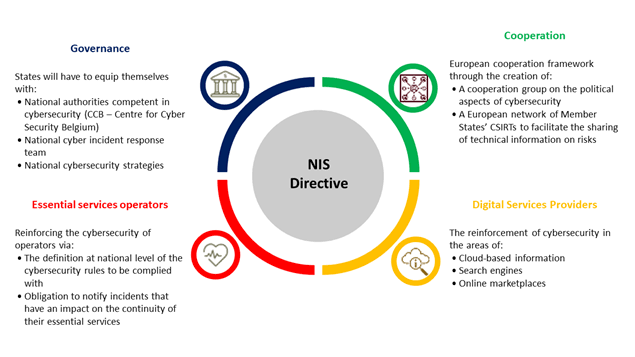
D. NIS Cooperation Group Enhancements: The role of the NIS Cooperation Group will be strengthened to support strategic cooperation and information exchange among EU Member States.
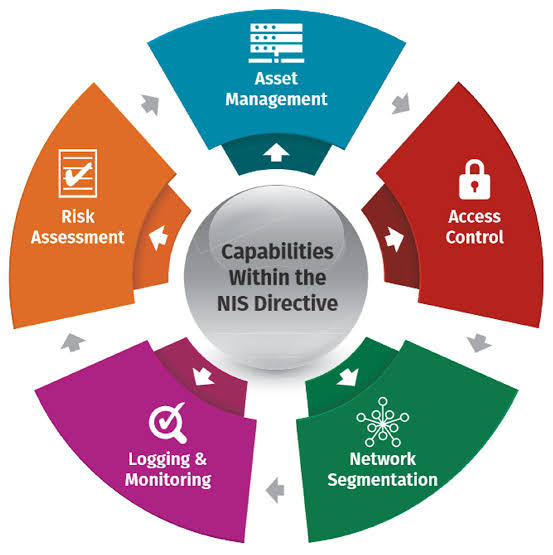
E. International Cooperation:
a. Harmonization: Promote international cooperation and alignment on cybersecurity standards, regulations, and incident response frameworks with global partners.
b. Information Sharing: Strengthen cooperation mechanisms with international organizations, such as the United Nations, NATO, and Interpol, to facilitate the exchange of information, expertise, and best practices.
c. Capacity Building: Support capacity-building initiatives in developing countries to help enhance their cybersecurity capabilities, thereby fostering global cybersecurity resilience.
F. Size-agnostic Approach: Unlike the initial directive, the updated one takes a size-agnostic approach to security, meaning it takes into account not just the size of an entity but the significance of potential service disruptions they might cause.
G. Provisions for SMEs: While the directive imposes stringent requirements on larger entities, it also includes provisions to avoid overburdening small and medium enterprises (SMEs) with disproportionate compliance costs.
H. Continuous Monitoring and Evaluation:
a. Regulatory Review: Conduct periodic reviews of the NIS Directive and its amendments to ensure their effectiveness, relevance, and adaptability to emerging cyber threats.
b. Performance Indicators: Develop performance indicators and metrics to assess the effectiveness of cybersecurity measures, incident response capabilities, and the overall resilience of the EU’s cybersecurity landscape.
c. Lessons Learned: Regularly evaluate and incorporate lessons learned from cyber incidents, exercises, and audits into policy development, capacity building, and future cybersecurity initiatives.
vi. Beyond NIS Directive 2.0:
Looking beyond the NIS 2.0, we can anticipate the European Union’s cybersecurity strategy to evolve in the following ways:
A. Adaptive Legislation: Continual updates to legislation to keep pace with the rapidly evolving cyber threat landscape and technological advancements.
B. Enhanced Cooperation: A stronger emphasis on cross-border cooperation, including information sharing and joint response to large-scale cyber incidents.
C. AI and Automation: Further integration of AI and automation tools in cybersecurity to provide proactive defense measures and to handle the sheer volume and sophistication of threats.
D. Cybersecurity Culture: Efforts to promote a cybersecurity culture among citizens and businesses, emphasizing the importance of cybersecurity hygiene and awareness.
E. Certification Frameworks: Development of EU-wide cybersecurity certification frameworks ensuring that products, processes, and services are secure by design.
F. International Partnerships: Strengthening international partnerships outside the EU to address global cybersecurity challenges comprehensively.
G. Investment in Cybersecurity: Increased funding for cybersecurity research, development, and innovation to build a resilient cyber ecosystem.
H. Focus on Cyber Resilience: Shifting focus from just prevention to resilience, ensuring that systems and organizations can recover swiftly from cyber attacks.
I. Training and Education: Expanding training and education programs to address the shortage of cybersecurity professionals.
J. Public-Private Collaboration: Enhancing collaboration between the public and private sectors to share best practices and resources.
The EU remains committed to strengthening its cybersecurity posture. Ongoing initiatives like the Cybersecurity Act and the European Cybersecurity Competence Centre demonstrate this commitment. By effectively implementing NIS2 and continuing to invest in research, collaboration, and education, the EU can build a more secure and resilient digital future.
vii. Conclusion:

As the EU advances toward NIS Directive 2.0, it marks a significant commitment to fortify its cybersecurity defenses. This directive, coupled with ongoing efforts and future strategies, lays the groundwork for a resilient and adaptive cybersecurity framework. The journey to strengthen cybersecurity in the EU is not just a directive; it is a continuous evolution to safeguard against the dynamic and persistent cyber threats of the digital age.
These efforts, combined with a vigilant stance on cybersecurity, aim to build a robust and resilient digital infrastructure in the EU that can withstand and adapt to the cyber threats of today and the future. The continuous evolution of these policies demonstrates the EU’s commitment to maintaining a secure digital space for its citizens and businesses.
viii. Additional Resources:
NIS2 Directive: [https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX:32022L0284](https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX:32022L0284)
European Commission Cybersecurity Portal: [https://digital-strategy.ec.europa.eu/en/policies/cybersecurity-policies](https://digital-strategy.ec.europa.eu/en/policies/cybersecurity-policies)
Council of the European Union – Strengthening EU-wide cybersecurity and resilience: [https://www.consilium.europa.eu/en/press/press-releases/2023/11/30/cyber-resilience-act-council-and-parliament-strike-a-deal-on-security-requirements-for-digital-products/](https://www.consilium.europa.eu/en/press/press-releases/2023/11/30/cyber-resilience-act-council-and-parliament-strike-a-deal-on-security-requirements-for-digital-products/)
Strengthening Cybersecurity in the EU with NIS Directive 2.0 and Beyond
EYhttps://www.ey.com › cybersecurityHow to prepare for the NIS2 Directive?
KPMGhttps://assets.kpmg.com › pdfPDFNetwork & Information Security Directive (NIS2)
PECBhttps://pecb.com › article › a-compr…A Comprehensive Guide: Understanding the NIS 2 Directive
DNVhttps://www.dnv.com › cyber-insightsNIS2: From risk to opportunity – DNV
KPMGhttps://assets.kpmg.com › pdfPDFComplying with the European NIS Directive
BeyondTrusthttps://www.beyondtrust.com › entryPreparing for NIS2: Answers to the Most Frequently…
