The Intriguing Life of a Technology Audit Expert
In the tapestry of modern corporate structures, technology audit experts stand out as vital guardians of digital integrity and operational efficiency.
These specialized auditors play a crucial role in evaluating the effectiveness of an organization’s technology systems, ensuring that they are secure, reliable, and in alignment with business objectives.
The lifestyle of a technology audit expert is a blend of rigorous analysis, continuous learning, and navigating the challenges of evolving tech landscapes. This article provides a glimpse into the daily life, work environment, challenges, and personal growth avenues for individuals in this dynamic field.
i. Demystifying the Role

Technology audit experts, also known as IT auditors, are responsible for assessing an organization’s IT infrastructure and practices. They ensure these align with regulations, best practices, and internal controls to safeguard data and systems.
ii. Daily Responsibilities

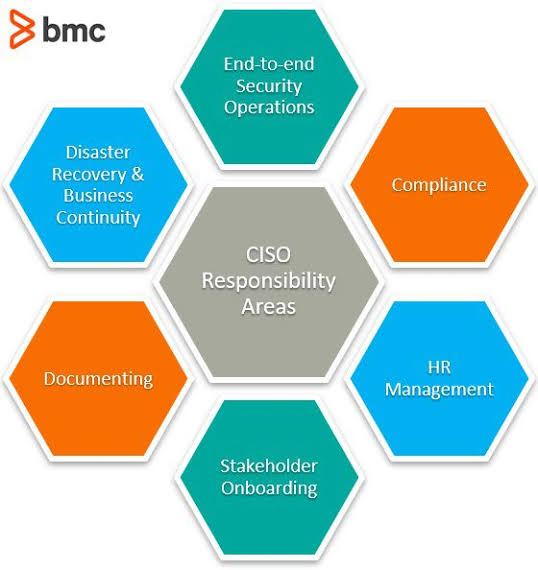
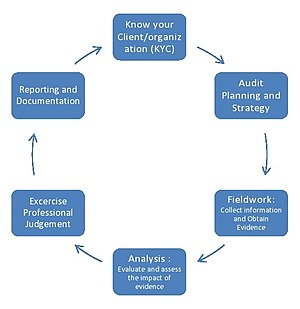
o Audit Planning and Execution: Designing and executing audit plans that scrutinize an organization’s IT systems, policies, and operations. This involves a mix of on-site visits, remote audits, and in-depth discussions with IT personnel.
o They work closely with stakeholders to understand the organization’s technology landscape, identify potential risks, and establish audit objectives and criteria.
o During the audit process, Technology Audit Experts utilize various tools and techniques to assess the effectiveness of IT controls, identify vulnerabilities, and evaluate compliance with relevant regulations and standards.
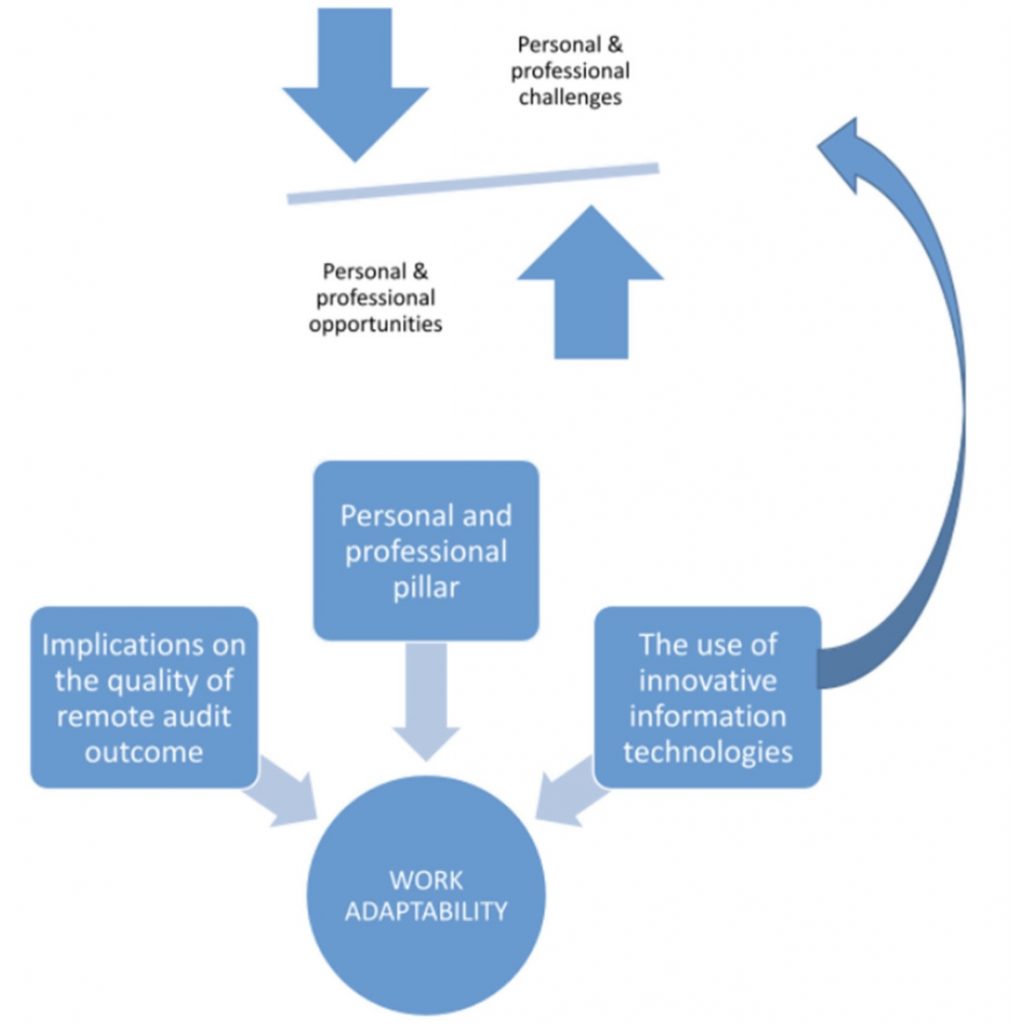
o Analysis and Reporting: Collecting and analyzing data to assess risks, effectiveness, and compliance with standards. Technology audit experts then compile their findings into reports that highlight issues, provide benchmarks against best practices, and recommend improvements.
o Stakeholder Engagement: Communicating with stakeholders across various departments to ensure the alignment of technology systems with business goals and compliance requirements. This often includes presenting findings to senior management and working collaboratively to implement recommendations.
o Continuous Education: Keeping abreast of the latest in technology trends, audit methodologies, and regulatory changes. This could involve attending workshops, webinars, or pursuing additional certifications.
iii. Continuous Learning and Skill Enhancement

Technology Audit is a rapidly evolving field, with new technologies, threats, and regulatory requirements emerging constantly. As a result, Technology Audit Experts are committed to continuous learning and skill enhancement. They stay up-to-date with the latest industry trends, attend training sessions and certifications, and participate in professional development activities to sharpen their skills and expertise.
iv. Attention to Detail and Analytical Thinking
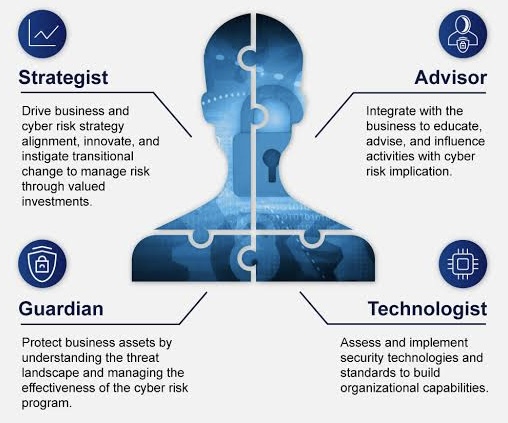
One of the defining characteristics of a Technology Audit Expert is their keen attention to detail and strong analytical thinking skills. They meticulously examine IT systems, processes, and controls, identifying weaknesses, gaps, and areas for improvement. By carefully analyzing data and information, they can provide valuable insights and recommendations to enhance the organization’s IT governance and risk management practices.
v. Communication and Collaboration

Effective communication and collaboration are essential aspects of a Technology Audit Expert’s lifestyle. They interact with a wide range of stakeholders, including IT teams, business leaders, external auditors, and regulatory authorities. Clear and concise communication is crucial for conveying audit findings, explaining complex technical concepts to non-technical audiences, and building strong relationships with key stakeholders.
vi. Compliance and Risk Management
Technology Audit Experts play a vital role in helping organizations achieve compliance with industry regulations, standards, and internal policies. By assessing IT controls and practices, they can identify areas of non-compliance and potential risks, enabling the organization to address issues proactively and mitigate future threats.
vii. Career Growth and Development
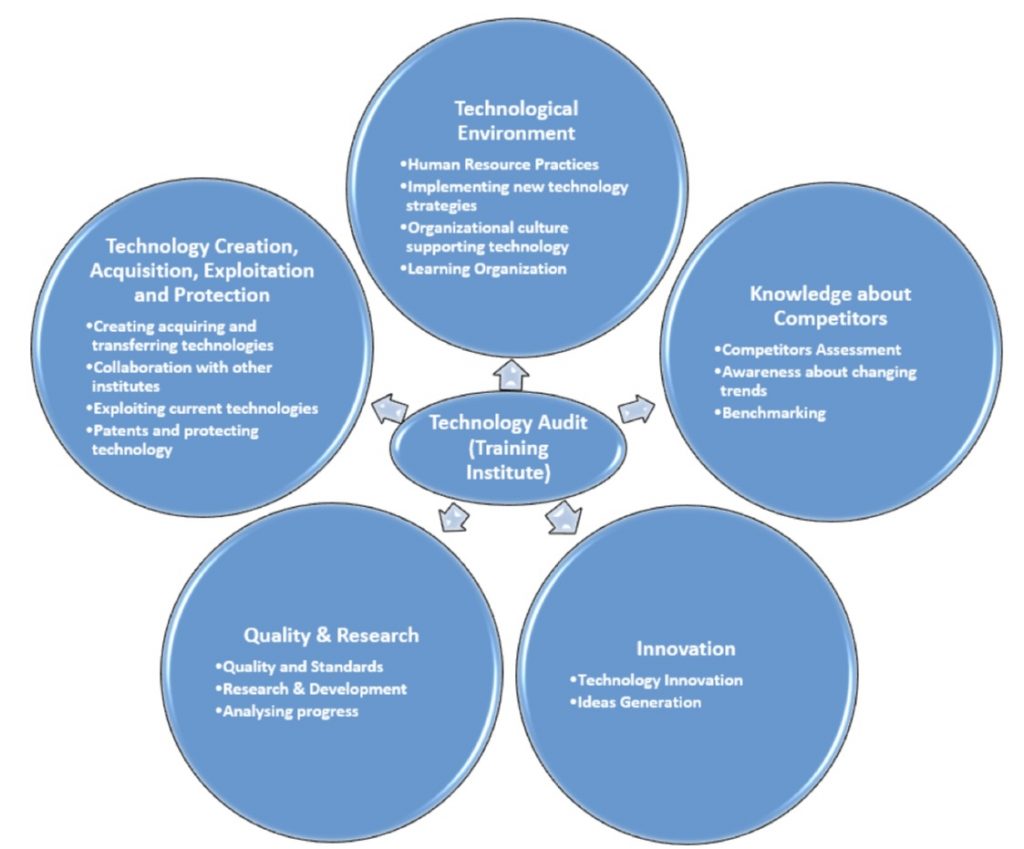
As Technology Audit Experts gain experience and expertise in the field, they have opportunities for career growth and advancement. They may take on leadership roles, specialize in specific areas of technology audit (such as cybersecurity or cloud computing), or transition into broader IT governance or risk management positions.
Professional certifications, such as CISA (Certified Information Systems Auditor) or CISSP (Certified Information Systems Security Professional), can further enhance their credentials and career prospects.
Moreover, the diversity of industries and projects they work on fosters a broad skill set and deep industry knowledge, paving the way for advancements into senior management roles, consulting, or specialist cybersecurity positions.
viii. Flexibility and Agility
The technology landscape is subject to rapid changes, and Technology Audit Experts must be adaptable and agile in response. Flexibility in audit methodologies and the ability to pivot quickly to address emerging issues is essential. This adaptability ensures that audits remain relevant and effective in the face of evolving technological challenges.
ix. Required Skills
To excel in this role, individuals need a blend of technical expertise and soft skills:
o Technical knowledge: Understanding of IT systems, networks, and security controls
o Analytical skills: Ability to analyze complex data and identify potential risks
o Communication skills: Effectively communicate findings and recommendations to technical and non-technical audiences
o Problem-solving skills: Ability to identify and resolve IT control deficiencies
x. The Work Environment
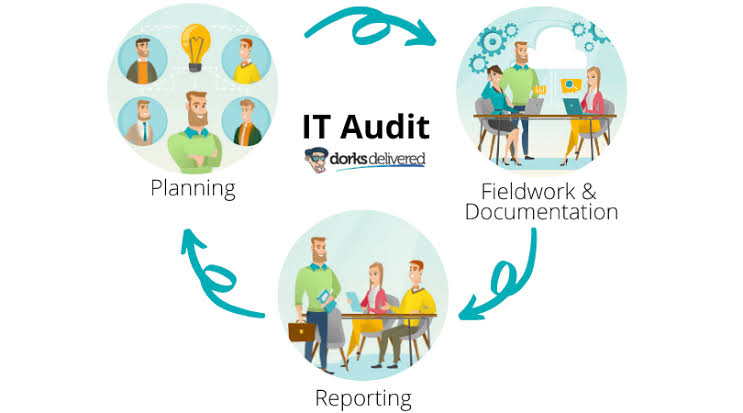
Technology audit experts often work within the internal audit department of larger organizations or as part of specialized consulting firms.
Their work can take them across various sectors, offering a broad exposure to different types of IT environments—from financial systems and e-commerce platforms to healthcare records and manufacturing automation systems.
With technology now integral to almost every aspect of business operations, the demand for skilled technology auditors has led to opportunities for both in-office and remote work arrangements, allowing for flexibility in work-life balance.
xi. Challenges and Rewards

The role of a technology audit expert comes with its unique set of challenges. The rapid pace of technological advancement means that new risks and vulnerabilities are always on the horizon, requiring constant vigilance and adaptability.
The complexity of modern IT systems and the intricacies of regulatory compliance further complicate their task.
However, the career is also deeply rewarding. Technology audit experts are at the forefront of safeguarding organizations’ digital assets and ensuring the integrity of data and systems.
Their work not only protects the organization from financial loss and reputational damage but also contributes to the strategic development of more efficient, secure, and compliant technology practices.
xii. Life Outside Work

Maintaining a healthy work-life balance is essential for technology audit experts, given the potentially high-stress nature of their work. Many professionals in the field prioritize hobbies and interests that provide a counterbalance to their work—be it through physical activities, tech tinkering for personal projects, or simply enjoying quality time with family and friends.
xiii. Conclusion

The lifestyle of a Technology Audit Expert is characterized by a continual pursuit of knowledge, a meticulous attention to detail, and a commitment to excellence in assessing and improving IT systems and controls.
These professionals play a critical role in helping organizations navigate the complex and ever-changing technology landscape, ensuring that they operate efficiently, securely, and in compliance with regulatory requirements.
By embracing a lifestyle of continuous learning, analytical thinking, effective communication, and risk management, Technology Audit Experts contribute significantly to the success and resilience of modern organizations in an increasingly digital world.
xiv. Further references
Indeedhttps://uk.indeed.com › finding-a-jobWhy choose a career in internal auditing? (Plus skills)
BDO UKhttps://careers.bdo.co.uk › audit-mo…More about Audit
ISACAhttps://www.isaca.org › industry-newsWhat the Post-Pandemic Future Holds for IT Auditors
ResearchGatehttps://www.researchgate.net › 3278…(PDF) The Role of IT Audit in the Era of Digital …
Innowisehttps://innowise.com › it-consulting…IT Consulting Services
Accountancy SAhttps://www.accountancysa.org.za › …Feature: The internal audit function of the future