Safeguarding the organization’s data from external and internal threats is crucial for protecting sensitive information, maintaining business continuity, and upholding the organization’s reputation.
The following steps outline important procedures to minimize risk and safeguard one’s important information:
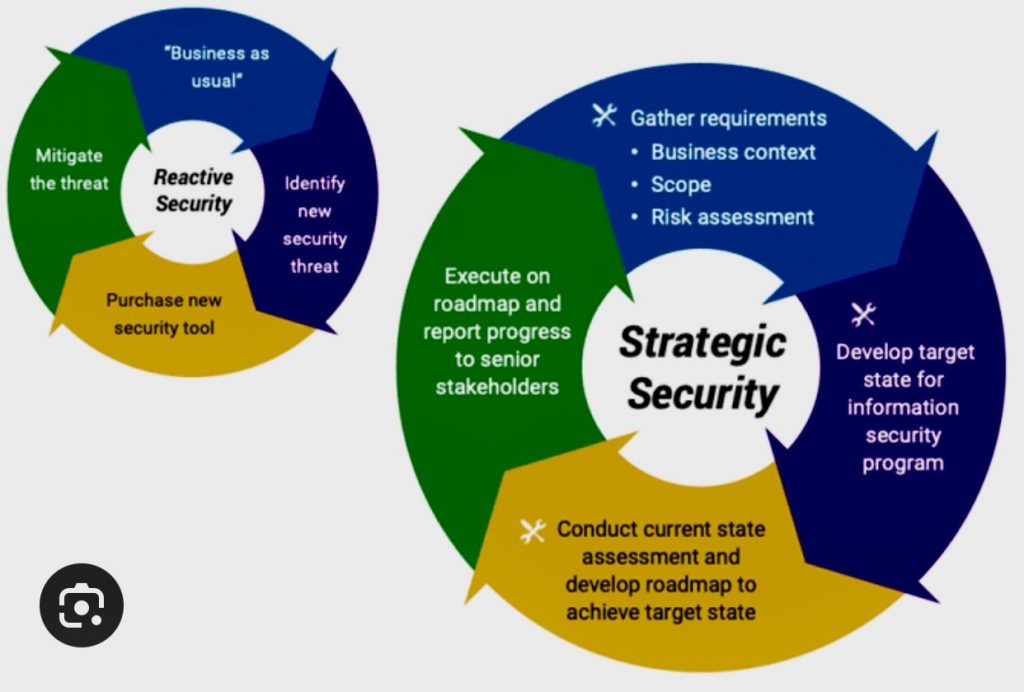
A. Implement a Strong Security Policy: It’s not just about the tools you have but also about the practices you support. A comprehensive, organization-wide security policy is crucial for understanding and mitigating risks.
B. Risk Assessment: Understand the risks associated with the data you hold. High-risk data may require additional security measures.
C. Regular Security Audits: Regular audits can identify potential weaknesses in the organization’s system. By proactively addressing these weaknesses, you can prevent potential breaches.
D. Assign a Data Protection Officer: Larger companies might find it beneficial to assign a dedicated Data Protection Officer. Their job would be to advise on compliance with relevant data protection laws and monitor the organization’s adherence to them.
E. Strict Vendor Controls: Vendors often have access to the organization’s systems and data. Make sure you have clear security expectations in the organization’s vendor contracts.
F. Third-Party Risk Management: Assess and manage risks associated with third-party vendors and service providers. Ensure they have adequate data security practices in place.
G. Establish Strong Access Controls: Use complex passwords and consider two-factor authentication to provide an extra layer of security. Regularly update the organization’s passwords and ensure each password is unique to each platform.
H. Keep Software and Systems Updated: Regular updates keep systems guarded against known vulnerabilities that attackers could exploit. Ensure automatic updates are enabled for the organization’s operating system and apps, where possible.
I. Secure the organization’s Network: Use a firewall to secure the organization’s internet connection. If possible, use a virtual private network (VPN) when accessing information remotely to encrypt the organization’s connection.
J. Back up Data: Regularly back up the organization’s data and ensure these backups themselves are secure. This adds to a robust data recovery plan in case of an accidental loss or a ransomware attack.
K. Vulnerability Management: Regularly scan systems and applications for vulnerabilities and apply security patches promptly. Prioritize patching critical vulnerabilities that pose the highest risk.
L. Incident Response Plan: Develop and maintain an incident response plan to effectively handle data breaches or security incidents. The plan should outline roles, responsibilities, and communication protocols.
M. Cybersecurity Awareness Training: Educate employees about cybersecurity threats and best practices. Train them to recognize phishing attempts, social engineering attacks, and other common threats.
N. Implement Access Controls: Implement role-based access controls to limit the access to sensitive data within the organization. Not everyone in the organization needs to access all data.
O. Regularly Dispose of Unwanted Data: Unnecessary storage of data can enhance vulnerability. Safely dispose of data you don’t need.
P. Data Usage Control: Limit the usage of sensitive data. Only those who need access for effective functioning of their roles should have access to it.
Q. Use Antivirus Software: Use any reputable antivirus software to safeguard the organization’s systems from malware attacks and regularly update it.
R. Data Anonymization: In cases where certain sensitive data needs to be used for development or testing purposes, this data can be anonymized or pseudonymized. This method protects the real identities and any potentially sensitive connections to the data.
S. Encrypt Sensitive Data: This ensures that even if the data is accessed or stolen, it can’t be read without the decryption key.
T. Monitor and Audit: Regularly monitor and audit the organization’s network and data access logs. Any suspicious activity can be promptly detected and addressed.
U. Employ Data Leak Prevention Tools: Encrypt emails, secure important data, and use security measures to prevent unauthorized data transfers.
V. Continuous Monitoring and Auditing: Regularly monitor and audit data security controls to identify and address potential weaknesses. Conduct penetration testing to assess system vulnerabilities.
By taking steps to secure the organization’s data and staying vigilant about potential threats, you can significantly mitigate the risk of loss and theft.
It is crucial to understand that no single solution provides full security and hence a layered security approach combining multiple methods is usually the best strategy.
https://www.integrate.io/blog/data-security-threat-best-practices/
