
The CyBOK (Cyber Security Body of Knowledge) Forensics Knowledge Area is focused on the field of digital forensics, which involves the identification, preservation, analysis, and presentation of digital evidence for legal investigations or incident response.
i. What is it?
The CyBOK Forensics Knowledge Area (FA) is part of the Cybersecurity Body of Knowledge (CyBOK) framework, which outlines the core knowledge and skills required for cybersecurity professionals. The FA specifically focuses on the technical aspects of digital forensics, which is the application of scientific methods to collect, preserve, and analyze digital evidence in support of legal proceedings or investigations.
ii. What does it cover?
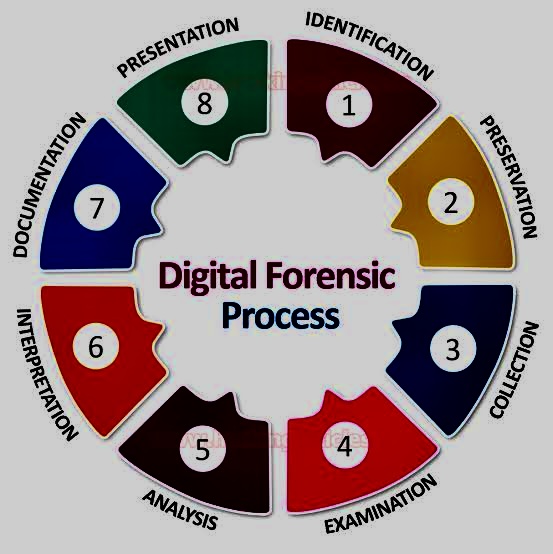
The FA covers a wide range of topics related to digital forensics, including:
o Definitions and conceptual models: This section provides an overview of key terms and concepts in digital forensics, such as evidence, chain of custody, and admissibility.
o Acquisition and preservation: This section discusses the different methods for acquiring and preserving digital evidence, such as imaging, hashing, and journaling.
o Analysis and examination: This section covers the various techniques used to analyze digital evidence, such as file system forensics, memory forensics, and network forensics.
o Reporting and presentation: This section provides guidance on how to document and present digital evidence in a clear and concise manner.
o Legal and regulatory considerations: This section discusses the legal and regulatory aspects of digital forensics, such as search and seizure warrants, chain of custody requirements, and e-discovery.
iii. The CyBOK (Cyber Security Body of Knowledge) Forensics Knowledge Area Sub-topics
A. Digital Crime: Understanding different types of digital crimes and their impact on digital forensics investigations.
B. Digital Evidence: Learning about the types of digital evidence, its collection, preservation, and analysis methods.
C. Investigation Methods: Understanding various investigation techniques and methodologies used in digital forensics.
D. Forensic Tools: Familiarizing yourself with the different software, hardware, and open-source tools used in digital forensics investigations.
E. Data Recovery: Learning about techniques and methods for data recovery from different digital devices.
F. Network Forensics: Understanding the methods and tools used to analyze network traffic and identify potential security breaches or attacks.
G. Mobile Device Forensics: Exploring the unique challenges and techniques involved in extracting and analyzing evidence from mobile devices.
H. Malware Analysis: Understanding how to analyze and reverse-engineer malicious software to identify its functionality and origin.
I. Incident Response: Developing the skills necessary to respond effectively to cybersecurity incidents, including evidence collection and preservation.
J. Legal and Ethical Considerations: Understanding legal and ethical issues related to digital forensics, including privacy, jurisdiction, and chain of custody.
iv. Why is it important?
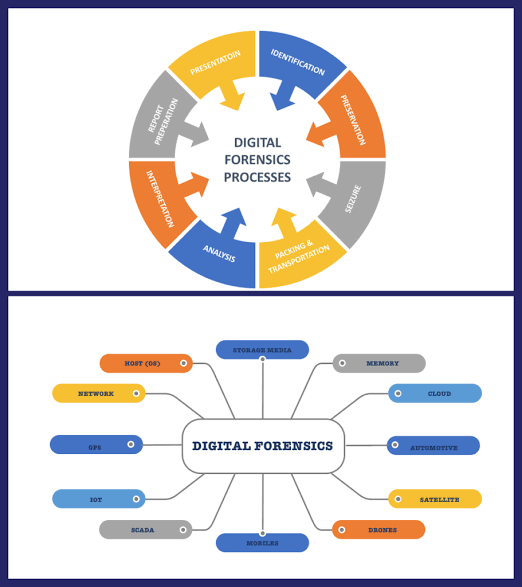
Digital forensics is an increasingly important field in cybersecurity, as cybercriminals are increasingly using digital evidence to cover their tracks. A strong understanding of the FA can help cybersecurity professionals:
o Investigate cyberattacks: By understanding how to collect, preserve, and analyze digital evidence, cybersecurity professionals can help to identify the attackers and their methods.
o Respond to incidents: The FA can help cybersecurity professionals to quickly and effectively respond to cyberattacks by identifying the affected systems and data.
o Prevent future attacks: By understanding the techniques used by cybercriminals, cybersecurity professionals can help to develop better defenses against future attacks.
v. Who should learn it?
The FA is a valuable resource for any cybersecurity professional who may be involved in digital forensics, such as:
o Incident responders: The FA can help incident responders to collect and analyze evidence from cyberattacks.
o Security analysts: Security analysts can use the FA to investigate suspicious activity and identify potential threats.
o Penetration testers: Penetration testers can use the FA to learn about the techniques used by cybercriminals and develop more effective penetration tests.
vi. Key aspects covered in the Forensics Knowledge Area
A. Evidence Collection and Preservation:
o Aspect: Techniques for properly collecting and preserving digital evidence.
o Objective: Ensures the integrity and admissibility of evidence in legal proceedings.
B. Incident Response Forensics:
o Aspect: Integrating digital forensics into incident response activities.
o Objective: Helps in identifying and mitigating the impact of cybersecurity incidents.
C. Forensic Imaging:
o Aspect: Creating forensic images of digital devices for analysis.
o Objective: Preserves the original state of digital evidence without altering the source.
D. File System Forensics:
o Aspect: Analyzing file systems to extract relevant information for investigations.
o Objective: Unearths valuable insights about user activities and system interactions.
E. Memory Forensics:
o Aspect: Analyzing volatile memory to identify active processes and uncover artifacts.
o Objective: Provides a snapshot of system activity during a specific time period.
F. Network Forensics:
o Aspect: Investigating network traffic and logs to trace and analyze cyber incidents.
o Objective: Reveals patterns of communication and potential malicious activities.
G. Mobile Device Forensics:
o Aspect: Extracting and analyzing digital evidence from mobile devices.
o Objective: Addresses the increasing use of mobile devices in cyber incidents.
H. Database Forensics:
o Aspect: Examining databases for evidence of unauthorized access or data manipulation.
o Objective: Unravels unauthorized activities within databases.
I. Anti-Forensics Techniques:
o Aspect: Understanding methods used to evade or obstruct forensic investigations.
o Objective: Helps forensic analysts anticipate and counteract attempts to hide evidence.
J. Legal and Ethical Considerations:
o Aspect: Addressing legal and ethical issues in digital forensics.
o Objective: Ensures investigations adhere to legal standards and ethical principles.
K. Forensic Tools and Technologies:
o Aspect: Familiarity with tools and technologies used in digital forensics.
o Objective: Enables effective analysis and interpretation of digital evidence.
L. Report Writing and Documentation:
o Aspect: Communicating findings through clear and comprehensive reports.
o Objective: Ensures that investigative results are conveyed accurately for legal and organizational purposes.
vii. Resources
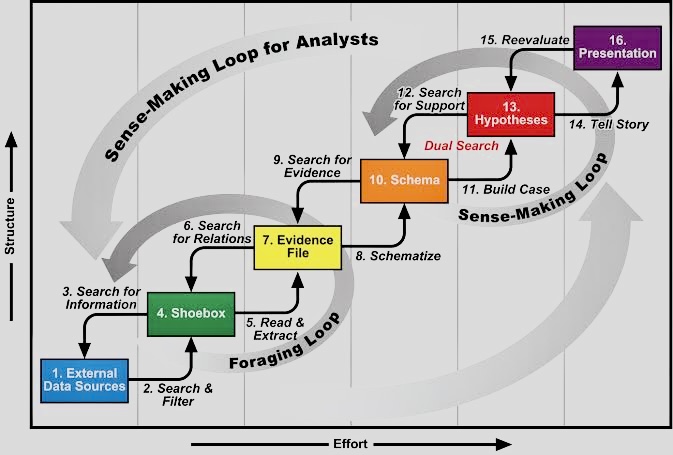
The CyBOK website provides a wealth of resources for learning more about the FA, including:
o The FA Knowledge Product: This document provides a comprehensive overview of the FA content.
o The CyBOK Glossary: This glossary defines key terms used in the FA.
o The CyBOK Training Catalog: This catalog lists training courses that cover the FA content.
The CyBOK Forensics Knowledge Area provides a comprehensive framework for individuals seeking to develop expertise in digital forensics. It covers a wide range of topics and skills needed in this field.
Digital forensics is a critical component of cybersecurity, providing the means to investigate and respond to cyber incidents, support legal proceedings, and enhance overall cybersecurity resilience.
The Forensics Knowledge Area in CyBOK guides professionals in acquiring the skills and knowledge needed to perform effective digital forensic investigations.
https://www.academia.edu/40172072/CyBOK_Cyber_Security_Body_Of_Knowledge
https://www.tripwire.com/state-of-security/icybok-introduction-cybersecurity-body-knowledge-project
https://www.bcs.org/articles-opinion-and-research/cybok-the-new-go-to-cyber-security-resource/
