
The Cyber Security Body Of Knowledge, or CyBOK, is a scholarly initiative aimed at codifying the foundational and generally recognized knowledge on cybersecurity.
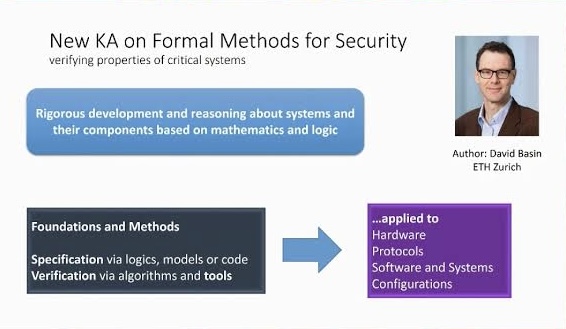
The “Formal Methods for Security Knowledge Area” is one of the areas covered in the CyBOK. Formal Methods are mathematical approaches used for the specification, development, and verification of software and hardware systems.
In the context of security, formal methods can play a significant role in ensuring that systems are secure by design.
The application of formal methods in security can greatly reduce the risk of design flaws, which can be exploited as security vulnerabilities. However, it’s important to note that formal methods also come with challenges such as scalability and complexity, and they often require significant expertise to apply effectively.
i. Key aspects of the Formal Methods for Security Knowledge Area (KA)
A. Foundations of formal methods: Explores the theoretical underpinnings of formal methods, including logic systems, formal languages, and verification techniques.
B. Modeling and abstraction: Discusses how to create accurate and concise formal models of systems, focusing on security-relevant aspects.
C. Verification and analysis: Covers various techniques for verifying and analyzing security properties of systems, such as model checking, theorem proving, and symbolic execution.
D. Applications in security: Examines the practical application of formal methods in different security domains, including access control, information flow, cryptography, and network security.
E. Challenges and limitations: Addresses the challenges and limitations of using formal methods in security, such as scalability, complexity, and tool support.
ii. Key concepts covered in the Formal Methods for Security Knowledge Area (KA)
A. Formal languages: Languages like temporal logic, modal logic, and process calculi that represent system behavior and security properties.
B. Models and abstractions: Abstractions like finite-state machines, Petri nets, and process algebra models that capture key aspects of systems for analysis.
C. Verification techniques: Techniques like model checking, theorem proving, and symbolic execution that prove or disprove the presence of desired security properties in models.
D. Security properties: Properties like confidentiality, integrity, availability, non-repudiation, and accountability that formal methods can be used to verify.
E. Formal tools and languages: Tools like theorem provers, model checkers, and specification languages that support the application of formal methods in security.
iii. Benefits of understanding Formal Methods for Security

A. Enhanced system security: Formal methods can help develop more secure systems by rigorously verifying and eliminating vulnerabilities before deployment.
B. Improved design and development: Formal models can guide the design and development process, ensuring adherence to security principles.
C. Increased confidence in systems: Rigorous verification using formal methods can build confidence in the security of developed systems.
D. Automated analysis and verification: Formal tools can perform automated analysis and verification, saving time and resources compared to manual testing.
E. Reduced risk of vulnerabilities: Early identification and elimination of vulnerabilities through formal methods lead to reduced risk of exploits and breaches.
iv. How formal methods can contribute to cybersecurity
A. Specification: Formal methods allow for the precise and unambiguous specification of system and security requirements. By using formal languages to express these specifications, it is possible to eliminate the ambiguities that are often present in natural language descriptions.
B. Modeling: Formal modeling gives a clear framework for understanding the security properties of a system before it is built. This can include creating abstract models of the system and potential threat models that can highlight security weaknesses.
C. Verification: Formal methods can be used to prove that a system’s security properties hold true under certain assumptions. This can involve proving the correctness of protocols or algorithms, thereby ensuring that they are free from security flaws.
D. Analysis: Using formal methods can help in analyzing the system for vulnerabilities. Through tools like model checking, it is possible to explore all possible states of a system to check for security violations.
E. Design: Formal methods can guide the design of security mechanisms by providing a clear framework within which these mechanisms can be developed and verified.
v. Aspects of Formal Methods in Cybersecurity
A. Formal Methods Overview:
o Aspect: Applying mathematical and formal techniques for specifying, designing, and verifying security properties in systems.
o Objective: Provides a rigorous and structured approach to ensuring security correctness.
B. Mathematical Modeling for Security:
o Aspect: Using mathematical models to represent security policies, protocols, and system behaviors.
o Objective: Enables precise analysis and verification of security properties.
C Theorem Proving and Formal Verification:
o Aspect: Applying formal methods like theorem proving to verify the correctness of security protocols or system components.
o Objective: Rigorously proves the absence of certain vulnerabilities or security flaws.
D. Model Checking:
o Aspect: Systematically checking finite state models of a system to verify security properties.
o Objective: Helps in identifying and eliminating potential security vulnerabilities.
E. Specification Languages:
o Aspect: Using formal specification languages to describe security requirements and properties.
o Objective: Provides a clear and unambiguous representation of security expectations.
F. Security Protocol Analysis:
o Aspect: Applying formal methods to analyze and verify the correctness of security protocols.
o Objective: Ensures that cryptographic protocols function securely and resist various attacks.
G. Automated Reasoning:
o Aspect: Employing automated reasoning tools to analyze security properties.
o Objective: Enhances the efficiency of security analysis, especially in complex systems.
H. Formal Methods in Software Development:
o Aspect: Integrating formal methods into the software development lifecycle for security assurance.
o Objective: Helps in building secure systems from the ground up.
I. Concurrency and Parallelism in Security Models:
o Aspect: Addressing security challenges related to concurrent and parallel execution in distributed systems.
o Objective: Ensures that security properties hold even in concurrent or parallel processing scenarios.
J. Application to Hardware Security:
o Aspect: Extending formal methods to verify security properties in hardware design.
o Objective: Ensures the security of hardware components in computing systems.
K. Combining Formal Methods with Other Approaches:
o Aspect: Integrating formal methods with other cybersecurity approaches for comprehensive security assurance.
o Objective: Takes advantage of the strengths of formal methods in conjunction with other security practices.
vi. Resources for further exploration
A. CyBOK: Formal Methods for Security Knowledge Area – [https://www.cybok.org/media/downloads/Formal_Methods_for_Security_v1.0.0.pdf](https://www.cybok.org/media/downloads/Formal_Methods_for_Security_v1.0.0.pdf)
B. National Institute of Standards and Technology (NIST) Special Publication 800-188: Software Security Engineering – [https://www.nist.gov/privacy-framework/nist-sp-800-188](https://www.nist.gov/privacy-framework/nist-sp-800-188)
C. International Symposium on Formal Methods (FM) – [https://fmi.or.id/downloads/](https://fmi.or.id/downloads/)
CyBOK’s handling of formal methods includes guidance on their scope and limitations, methodology, and practical applications within cybersecurity, with real-world examples and case studies to illustrate their use in industry and government settings. It is part of a broader effort to provide a reliable reference for academic programs, professionals, and practitioners in the field of cybersecurity.
By understanding and leveraging the knowledge and techniques offered by the Formal Methods for Security KA, organizations can significantly improve the security posture of their systems and software, contributing to a more secure and trustworthy digital environment.
https://dl.acm.org/doi/10.1145/3522582
https://link.springer.com/article/10.1007/s10639-022-11261-8#change-history
