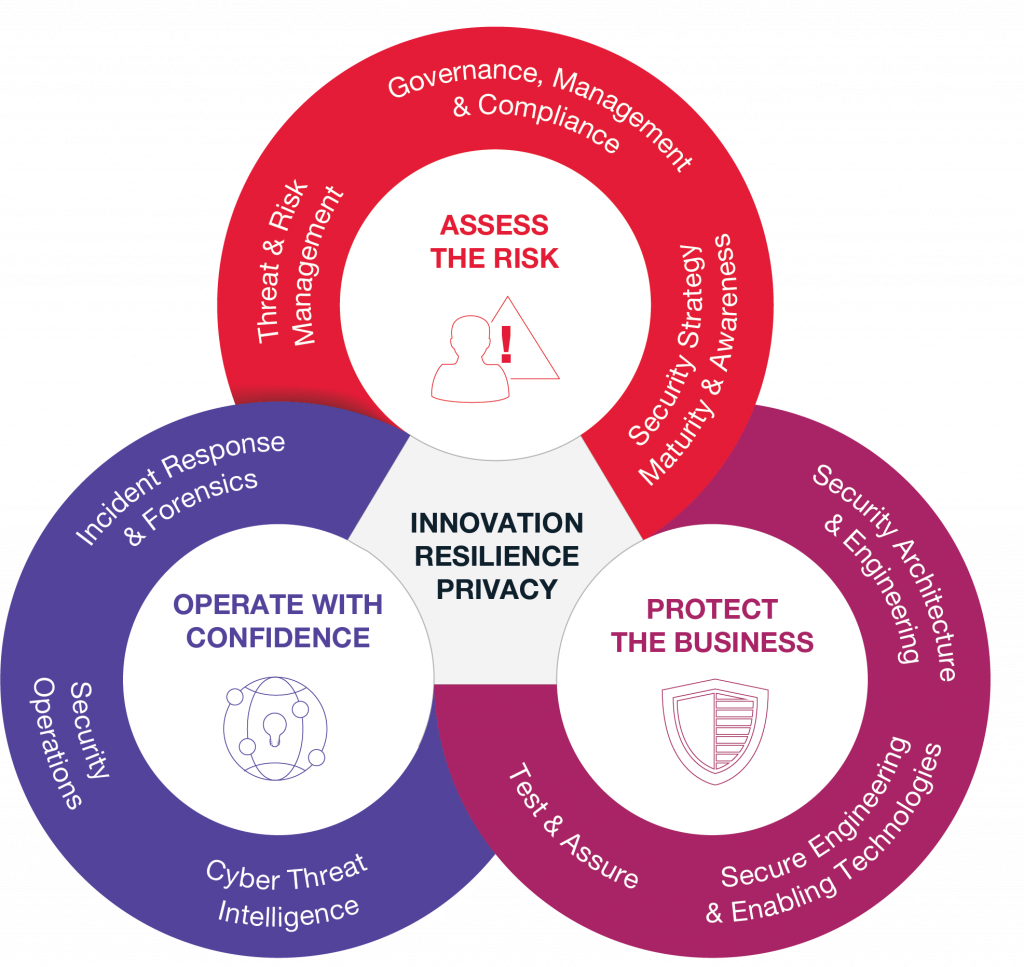
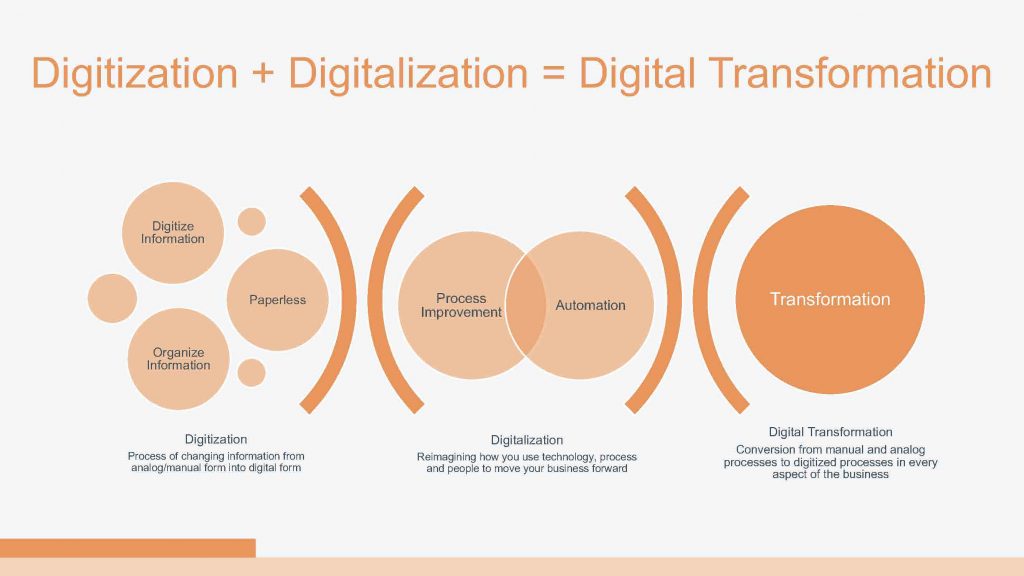
Digitizing the Risk Function for the Modern Era: Embracing Technology to Thrive
The modern business landscape is a whirlwind of interconnected systems, evolving threats, and ever-changing regulations. In this dynamic environment, traditional risk management approaches, traditionally seen as a gatekeeper of security and compliance, are struggling to keep pace. Embracing digital technologies can help organizations not only manage risks more effectively but also uncover new opportunities for growth and innovation.
i. The Imperative for Digital Transformation in Risk Management

Risk management has typically been a reactive domain, relying on established frameworks and historical data to mitigate potential threats. However, the rapid pace of technological advancement, coupled with the increasing sophistication of cyber threats, requires a more proactive and dynamic approach. Digitizing the risk function addresses several critical needs in the modern era:
A. Enhanced Data Analysis: With the proliferation of big data, risk managers can leverage advanced analytics and artificial intelligence (AI) to predict and identify potential risks with greater accuracy. Machine learning algorithms can process vast amounts of data to detect patterns and anomalies that might indicate emerging threats.
B. Real-Time Monitoring: Digital tools enable continuous monitoring of risk factors in real-time. Automated systems can alert risk managers to deviations from the norm, allowing for swift action to mitigate potential issues before they escalate.
C. Improved Collaboration: Digital platforms facilitate better communication and collaboration across departments and geographic locations. By integrating risk management into the overall business strategy, organizations can foster a culture of risk awareness and collective responsibility.
D. Regulatory Compliance: Keeping up with ever-changing regulations can be daunting. Digital solutions can streamline compliance processes, ensuring that organizations adhere to relevant laws and standards without compromising efficiency.
ii. The New Risk Landscape
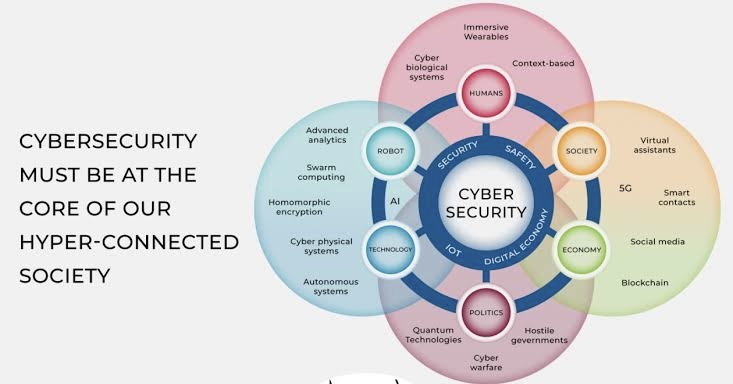
Today’s risk landscape is vastly different from what it was a decade ago. Cybersecurity threats have become a daily concern, regulatory pressures are mounting, and global supply chains are more interconnected — and vulnerable — than ever. Market volatility and geopolitical uncertainties add further complexity. This dynamic environment necessitates a robust, agile, and highly responsive risk management approach, underpinning the need for a digitized risk function.
iii. The Challenges of Traditional Risk Management
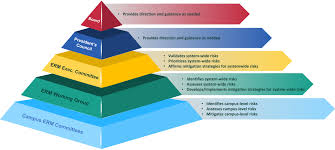
o Silos and Fragmentation: Risk data often resides in disparate systems, making it difficult to get a holistic view of organizational risk.
o Manual Processes: Reliance on manual workflows for risk identification, assessment, and mitigation slows down responses and increases the risk of human error.
o Limited Visibility: Lack of real-time risk insights hinders proactive decision-making and effective resource allocation.
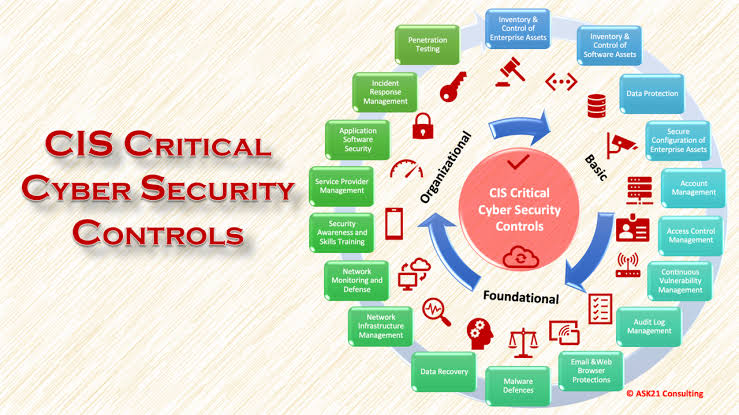
iv. Benefits of Digitizing the Risk Function
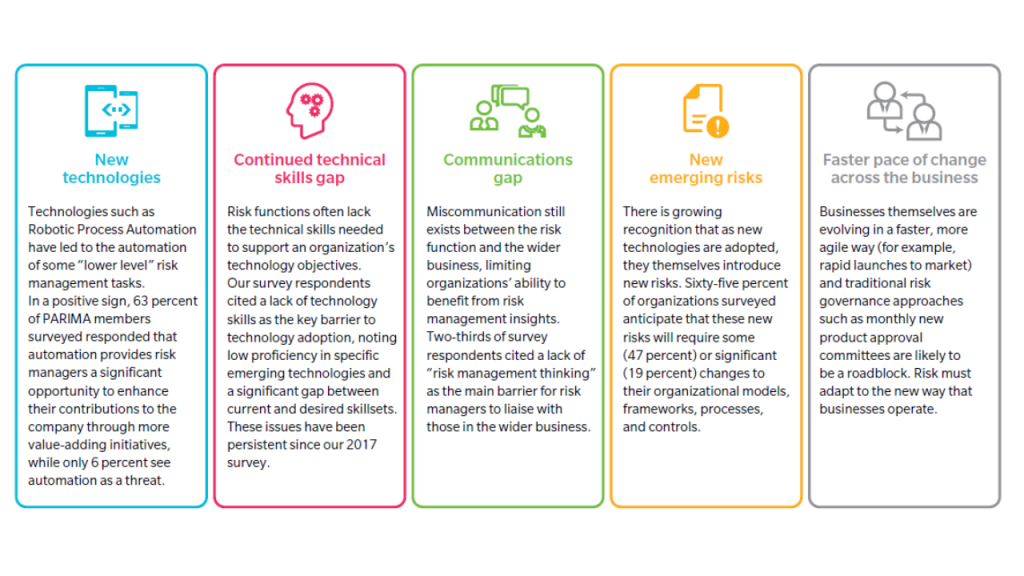
A. Real-time Risk Detection and Response: Digital tools powered by artificial intelligence (AI) and machine learning (ML) enable real-time monitoring and detection of risks. This immediacy allows organizations to respond swiftly to potential threats, minimizing damage.
B. Enhanced Risk Visibility: A clear and comprehensive view of all organizational risks promotes informed decision-making at all levels.
C. Improved Risk Mitigation: Proactive identification and prioritization of risks enable timely and effective mitigation strategies.
D. Data-Driven Decision Making: Data insights from analytics provide a strong foundation for making informed risk management decisions.
E. Enhanced Data Analytics: Digital risk management harnesses the power of big data analytics. By analyzing vast amounts of data from various sources, organizations can uncover hidden risks, identify trends, and predict potential future threats. This data-driven approach ensures a more comprehensive view of the risk landscape.
F. Automation of Routine Tasks: Automation tools can handle repetitive and mundane risk management tasks, reducing the likelihood of human error and freeing up risk professionals to focus on more strategic activities.
G. Improved Compliance Management: With regulatory requirements constantly evolving, digital risk management platforms can help organizations stay compliant. These tools can track regulatory changes, ensure timely updates to risk protocols, and generate necessary compliance reports with ease.
H. Scalability and Flexibility: Digital risk management solutions can scale alongside business growth. Whether a company expands into new markets or introduces new products, digitized risk functions can adapt quickly to new variables.
v. The Power of Digitizing Risk Management
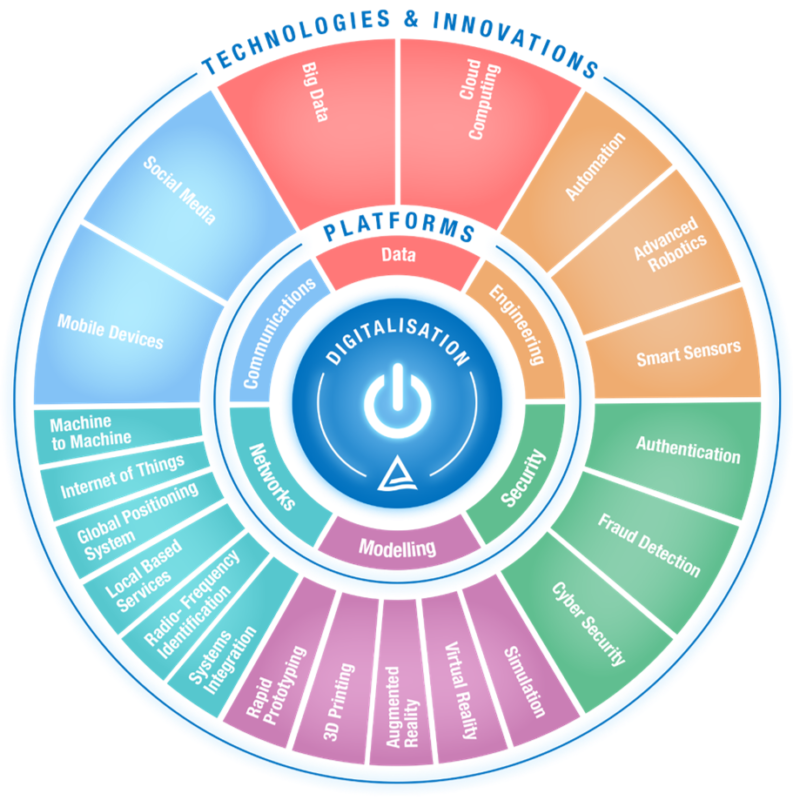
By leveraging technology, organizations can transform their risk function from a reactive to a proactive force. Here’s how:
o Centralized Risk Management Platform: A cloud-based platform can consolidate risk data from various sources, providing a single source of truth. This fosters collaboration and improves risk visibility across the organization.
o Advanced Analytics: Leveraging data analytics tools allows for the identification of emerging threats, trends, and patterns that might be missed by traditional methods. This enables more informed risk assessments and prioritization.
o Automated Workflows: Automating repetitive tasks like data collection, reporting, and scenario modeling streamlines workflows and frees up valuable resources for strategic analysis.
o Real-Time Risk Monitoring: Continuous monitoring of internal and external data sources allows for the identification and mitigation of risks in real-time, minimizing potential damage.
vi. Key Technologies Driving the Shift

Several technologies are pivotal in transforming the risk function:
A. Artificial Intelligence and Machine Learning
AI and machine learning are at the forefront of the digital transformation in risk management. These technologies can automate the analysis of large datasets, providing insights into potential risks that might not be evident through traditional methods. Predictive analytics can forecast future risks, enabling organizations to take preemptive measures.
B. Blockchain
Blockchain technology offers a new level of transparency and security, which is particularly beneficial for managing financial and transactional risks. Its immutable ledger ensures that all transactions are recorded accurately and cannot be tampered with, reducing the risk of fraud and enhancing trust.
C. Big Data Analytics
The ability to process and analyze vast amounts of data enables organizations to identify risks that would otherwise go unnoticed. This analytical power turns data into actionable insights.
D. Cloud Computing
The adoption of cloud computing provides scalability and flexibility, enabling risk managers to access and analyze data from anywhere, at any time. Cloud platforms also offer robust security features and disaster recovery options, ensuring business continuity in the face of unforeseen events.
E. Internet of Things (IoT)
IoT devices generate a wealth of data that can be used to monitor and manage risk in real-time. For example, sensors in a manufacturing plant can detect equipment malfunctions before they lead to costly downtime or safety incidents.
vii. Strategies for Digitizing the Risk Function

A. Assess Current Capabilities: Begin by evaluating existing risk management processes and technologies. Identify gaps and areas where digital tools can add value.
B. Develop a Clear Roadmap: Outline a strategic plan for integrating digital technologies into the risk function. This roadmap should include short-term and long-term goals, as well as key milestones to measure progress.
C. Selecting the Right Tools: It’s crucial to choose technologies that align with the organization’s risk management goals. This might include AI-driven analytics platforms, automated compliance tools, or blockchain solutions for enhanced transparency.
D. Training and Change Management: Introducing new technologies requires a shift in mindset and skills. Training programs and change management strategies are essential to ensure that staff can effectively use new tools and embrace a digital risk management culture.
E. Data Integration: Establish a seamless flow of data between the risk management platform and other relevant systems within the organization.
F. Foster a Culture of Innovation: Encourage innovation within the risk function by promoting a mindset that embraces change and seeks out new solutions. This cultural shift is essential for successfully integrating digital technologies.
G. Collaborate with Technology Partners: Partner with technology providers who specialize in digital risk management solutions. Their expertise can accelerate the adoption of new technologies and ensure seamless integration with existing systems.
H. Continuous Improvement: Digitization is not a one-time project but an ongoing process. Organizations should continuously monitor the effectiveness of their digital risk management tools, seek feedback, and make improvements as needed.
viii. Conclusion

In a world where risks are more complex and multifaceted than ever, digitizing the risk function is not just an option but a necessity. By leveraging advanced technologies, organizations can transform their risk management approach from reactive to proactive, turning potential threats into opportunities for growth and resilience. As the pace of digital transformation accelerates, the ability to manage risks digitally will be a key differentiator for successful organizations in the modern era.
ix. Further references
WORLD CLASS RISK ASSURANCEDeloittehttps://www2.deloitte.com › Documents › audit
Connect. Modernize. Digitize.Deloittehttps://www2.deloitte.com › Documents › Risk