
Enhance Data Protection with ISO/IEC 27001 and Identity Management: A Powerful Combination
In an era marked by escalating cyber threats, organizations face an imperative to fortify their data protection strategies. The convergence of ISO/IEC 27001, an international standard for information security, and Identity Management presents a formidable alliance to safeguard sensitive information. This article explores how the integration of these frameworks enhances data protection, offering a robust defense against evolving cybersecurity challenges.
i. Understanding the Synergy:

A. ISO/IEC 27001: A Pillar of Information Security:
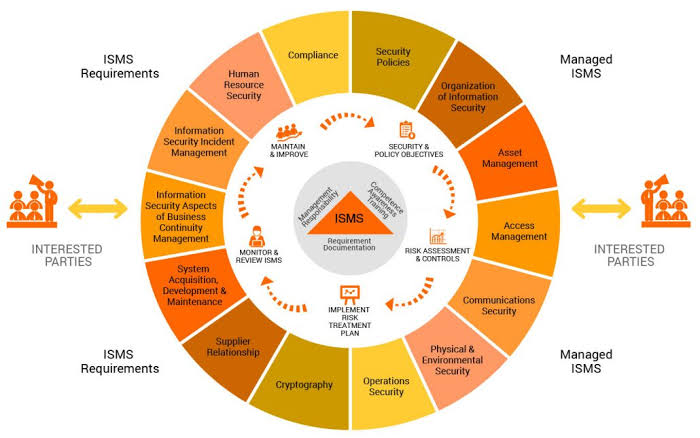
ISO/IEC 27001 serves as a comprehensive framework for information security management systems (ISMS). It establishes a systematic approach to identify, assess, and manage information security risks. By adopting ISO/IEC 27001, organizations demonstrate a commitment to ensuring the confidentiality, integrity, and availability of their information assets.
B. Identity Management: A Crucial Component:
Identity Management (IDM) revolves around managing user identities and their access to systems and data. Effective IDM ensures that the right individuals have appropriate access privileges, reducing the risk of unauthorized access and data breaches. The synergy between IDM and ISO/IEC 27001 is particularly potent in creating a holistic defense mechanism.
ii. When used together, they create a multi-layered defense:
A. ISO/IEC 27001 establishes essential security controls: These controls lay the foundation for secure data handling, including data classification, encryption, and secure disposal.
B. Identity Management strengthens access control: By verifying identities and managing access privileges, it ensures only authorized individuals can access sensitive data.
C. Enhanced accountability and auditability: Both standards emphasize logging and monitoring activities, allowing for tracing access attempts and identifying potential breaches.
iii. Benefits of this Combined Approach:
o Improved Data Security: Mitigates risks of unauthorized access, data breaches, and insider threats.
o Enhanced Compliance: Aligns with various data privacy regulations like GDPR and HIPAA.
o Streamlined Security Management: Provides a unified framework for managing and monitoring security controls.
o Increased Efficiency: Automates access provisioning and reduces administrative overhead.
o Improved User Experience: Enables single sign-on and simplifies access to authorized resources.
iv. Integrating ISO/IEC 27001 with Identity Management:

Here’s how they can be integrated for enhanced data protection:
A. Risk Assessment and Treatment:
o Conduct a thorough risk assessment as per ISO/IEC 27001 to identify potential risks related to identity management.
o Implement risk treatment plans that specifically address identity-related vulnerabilities.
B. Access Control Policies:
o Develop and document access control policies, a core requirement of ISO/IEC 27001, defining roles, and responsibilities within the identity management framework.
o Ensure logical access controls align with the principles of least privilege and need-to-know as stipulated by ISO/IEC 27001.
C. Policy Alignment:
o The integration ensures that IDM policies align with the information security policies defined by ISO/IEC 27001. This coherence strengthens the overall governance structure, minimizing inconsistencies and gaps in security measures.
D. Asset Management:
o As per ISO/IEC 27001 guidelines, maintain an inventory of information assets and associate each with a specific owner.
o Use identity management solutions to assign and enforce access rights for these assets based on roles within the organization.
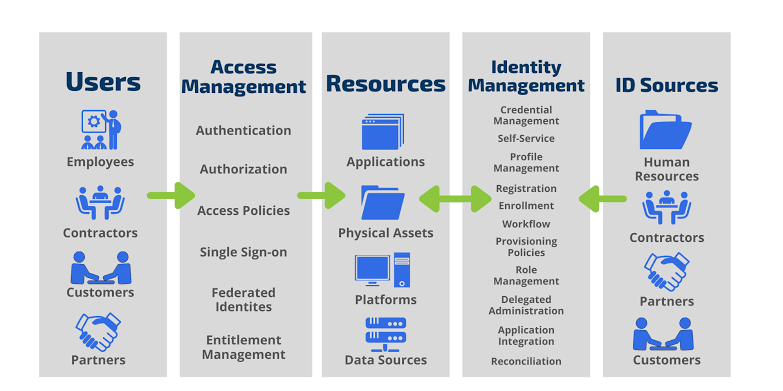
E. User Access Management:
o Establish a formal user registration and de-registration process to enable the assignment of access rights, ensuring this aligns with the access control policies of ISO/IEC 27001.
o Implement identity management systems for provisioning and de-provisioning of access rights in an automated and auditable manner.
F. Regular Reviews and Adjustments:
o Regularly review user access rights as required by ISO/IEC 27001 and adjust these as necessary in the identity management system, reflecting changes in employment roles.

G. Authentication Management:
o Use multifactor authentication mechanisms to strengthen access control, which is recommended practice under ISO/IEC 27001.
o Manage passwords strictly according to the complexity and change frequencies recommended in the standard.
H. Audit Trails and Monitoring:
o Monitor access to network and information assets using the identity management solutions, ensuring this supports the audit requirements of ISO/IEC 27001.
o Keep records of access and activities as part of an audit trail that can be reviewed periodically or in response to security incidents.
I. Awareness and Training:
o Train employees on the importance of identity management as part of the organization’s ISO/IEC 27001 awareness and training programs.
o Include training on topics such as password management and recognition of social engineering attacks.
J. Incident Management:
o Have a response plan in place for incidents related to compromised credentials or unauthorized access.
o The response plan should incorporate the principles of ISO/IEC 27001’s incident management protocols.
K. Compliance Assurance:
o Both ISO/IEC 27001 and IDM contribute to regulatory compliance. The integration ensures that organizations adhere to information security standards while maintaining a robust user identity and access management system.
L. Continuous Improvement:
o Continuously improve identity management practices through internal audits, conforming to the ISO/IEC 27001 standard’s emphasis on improvement.
o Apply the Plan-Do-Check-Act (PDCA) cycle to refine the identity management processes.
v. Challenges and Considerations:
o Complexity of integrating different systems: Requires careful planning and configuration to ensure seamless interaction between ISO/IEC 27001 controls and identity management systems.
o Continuous improvement: Both standards require ongoing monitoring, review, and adaptation to remain effective against evolving threats.
o Resource requirements: Implementing and maintaining these systems requires dedicated personnel with expertise in information security and identity management.
vi. Conclusion
Leveraging ISO/IEC 27001 and identity management in tandem offers a powerful approach to data protection. By implementing a layered security strategy with a focus on both technical controls and identity governance, you can significantly enhance data security, mitigate risks, and build trust with stakeholders.
This convergence reinforces both preventative and detective controls, setting a strong foundation for ensuring the confidentiality, integrity, and availability of sensitive information.
vii. Further references
Enhance Data Protection by Leveraging ISO/IEC 27001 and Identity Management
ISMS.onlinehttps://www.isms.online › knowledgeISO 27001 and a Zero Trust Security Model
