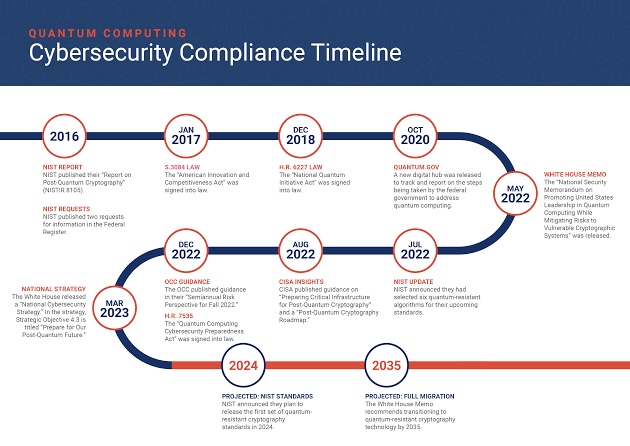
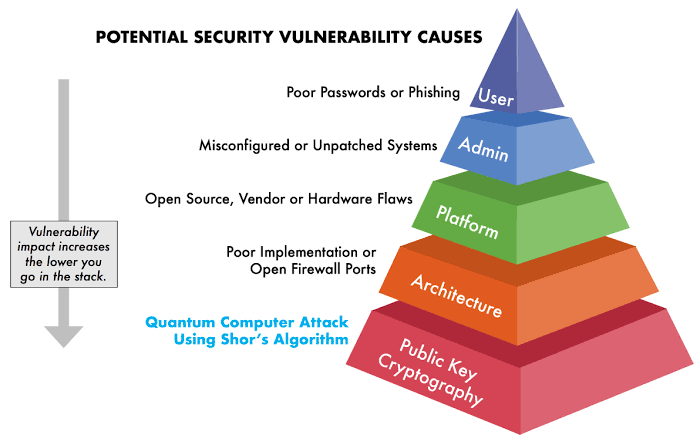
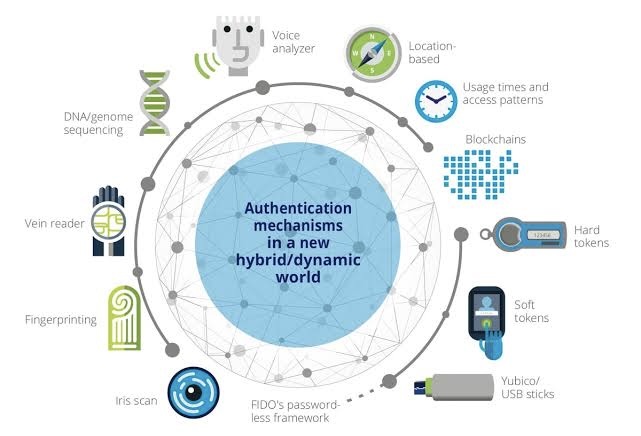
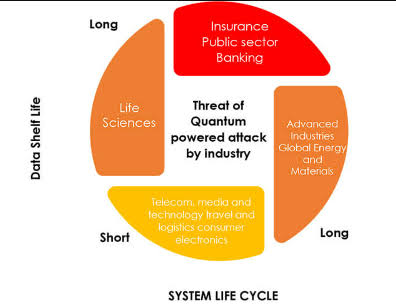
Building a Fortress Around Your Data: How Data Governance Bolsters Cybersecurity
Data governance plays a crucial role in bolstering cybersecurity measures within an organization. It encompasses the practices, policies, and processes that ensure the formal management of data assets, thereby significantly impacting an organization’s ability to protect against cyber threats.
Here’s how data governance influences cybersecurity:
i. Establishing Clear Data Ownership and Responsibility
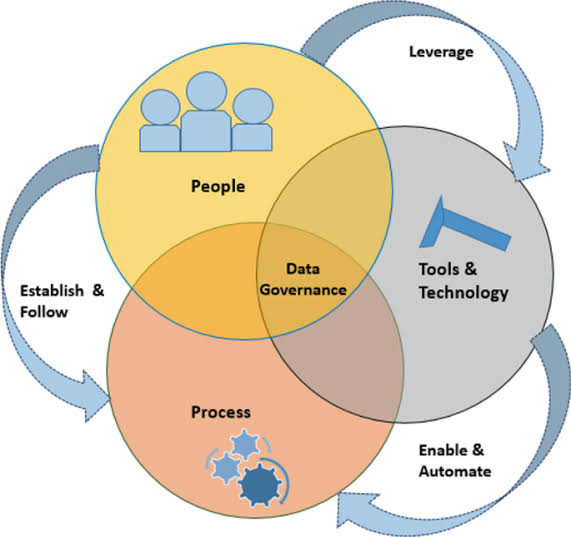
Data governance frameworks define clear responsibilities and roles for data management, ensuring that specific individuals or teams are accountable for the security of different types of data. This clarity helps in maintaining high standards of security as there is a direct responsibility for protecting the data from breaches and unauthorized access.
ii. Shining a Light: Enhanced Data Visibility
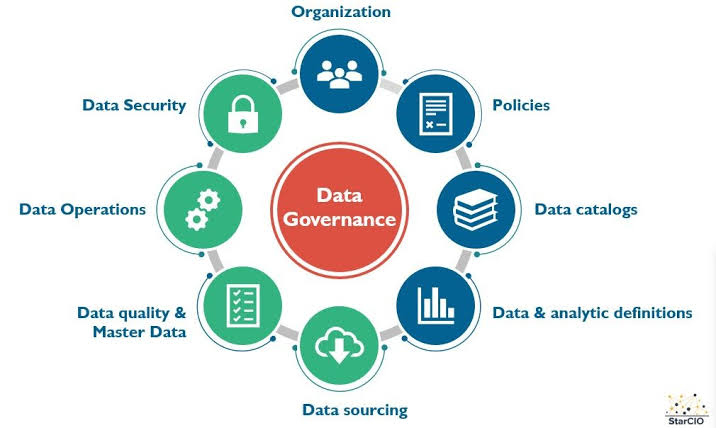
Imagine trying to defend a vast, sprawling city without knowing where the streets, buildings, and critical infrastructure lie. That’s the challenge many organizations face with cybersecurity when they lack data governance. Data governance sheds light on this landscape by providing a comprehensive understanding of what data you have, where it resides, and who has access to it. This newfound visibility empowers you to prioritize security efforts, focusing on the data that truly matters.
iii. Enhancing Data Quality and Integrity
Poor data quality can have direct security implications, including vulnerabilities that attackers can exploit. Data governance ensures that data is accurate, consistent, and reliable. By maintaining high-quality data, organizations can better detect fraudulent activity and anomalies that may indicate a cyber threat.
iv. Tailored Armor: Data Classification and Targeted Controls
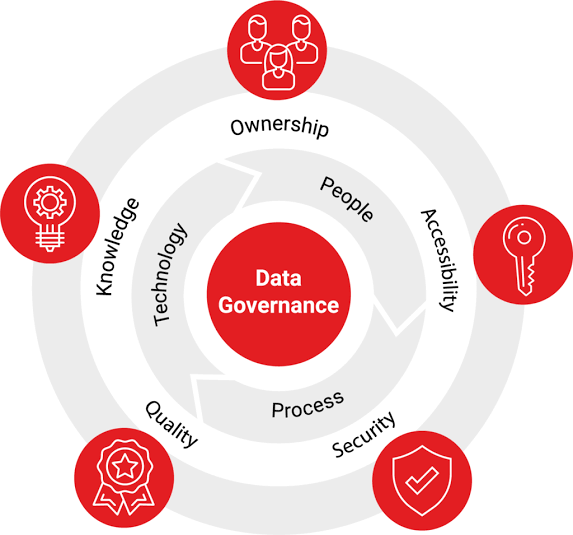
Not all data is created equal. Some, like financial records or customer health information, demand the strongest possible protection. Data governance enables data classification, where information is categorized based on its sensitivity. This, in turn, allows for the implementation of targeted security controls. Highly sensitive data might warrant encryption, restricted access, and rigorous monitoring, while less critical data can have more relaxed measures. This strategic approach optimizes security investments and ensures the right safeguards are in place for the right data.
v. Implementing Comprehensive Data Policies
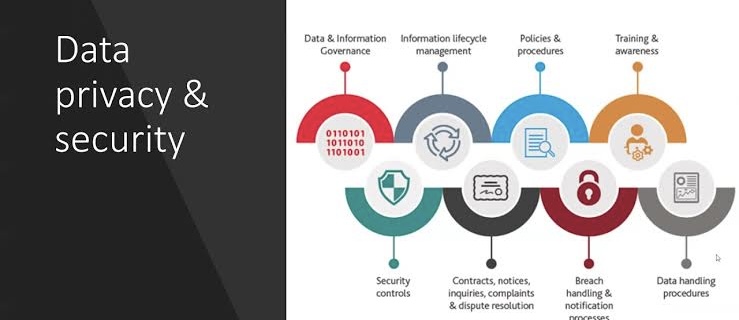
Data governance frameworks include the development and implementation of comprehensive data policies, which cover aspects like data storage, transfer, and access control. These policies are essential for cybersecurity as they help in protecting data throughout its lifecycle, preventing unauthorized access, and ensuring data is used in compliance with legal and regulatory requirements.
vi. Moats and Gatekeepers: Streamlined Access Controls
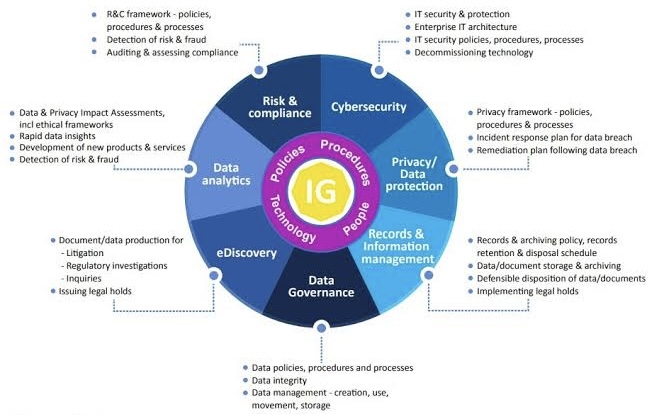
Imagine a castle with wide-open gates, accessible to anyone. That’s essentially what inadequate access controls do to your data. Data governance establishes clear rules dictating who can access what data and under what circumstances. This includes defining user roles, setting permission levels, and implementing robust authentication mechanisms. By creating well-defined perimeters around your data, you significantly reduce the risk of unauthorized access, a major gateway for cyberattacks.
vii. Strengthening Compliance with Privacy Regulations

Regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) have significant cybersecurity implications. Data governance supports compliance with these regulations by ensuring that data is handled securely and in accordance with legal obligations. This not only helps in avoiding legal penalties but also in protecting the organization from data breaches that could exploit non-compliance as a vulnerability.
viii. Facilitating Risk Management
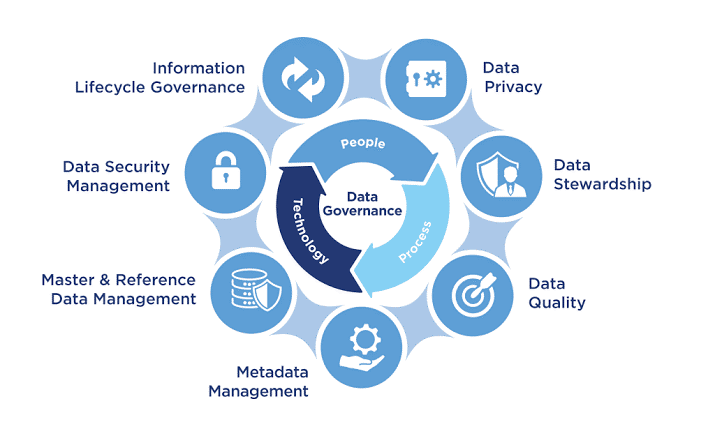
Data governance includes processes for identifying, evaluating, and managing risks associated with data. By understanding where sensitive data resides, who has access to it, and how it is being used, organizations can tailor their cybersecurity strategies to address the most significant risks, thereby enhancing overall security posture.
ix. Rapid Response: Efficient Incident Response

Even the most fortified defenses can be breached. When a security incident occurs, time is of the essence. Data governance empowers a swift and effective response by helping you quickly identify the affected data. By understanding its sensitivity and location, you can prioritize containment, minimize damage, and initiate appropriate remediation steps. This swift action can significantly reduce the impact of a data breach.
x. Beyond the Walls: Compliance as a Shield
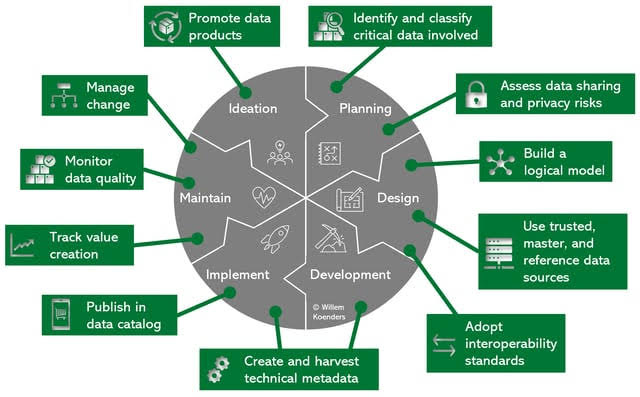
Data privacy regulations like GDPR and CCPA are not just legal hurdles; they’re important tools for bolstering cybersecurity. Many of these regulations mandate data governance practices like data classification, access controls, and incident response procedures. By adhering to these regulations, organizations not only avoid hefty fines but also create a framework for robust data security, strengthening their overall cybersecurity posture.
xi. Building a Culture of Vigilance

Data governance goes beyond technical controls; it fosters a culture of security within your organization. By raising awareness about data privacy and security best practices through data governance initiatives, employees become active participants in safeguarding information. This empowers them to make informed decisions about handling data, further reducing the risk of human error, a significant factor in many cyberattacks.
xii. Conclusion
In conclusion, data governance is not just about managing data; it’s about building a robust security ecosystem around your most valuable asset.
By providing data visibility, enabling targeted controls, streamlining access, facilitating efficient incident response, ensuring compliance, and fostering a culture of security, data governance acts as a powerful ally in today’s ever-evolving cybersecurity landscape.
By embracing data governance, organizations can build a digital fortress, effectively safeguarding their data and mitigating the ever-present threat of cyberattacks.
xiii. Further references
The Role of Data Governance in Security and Risk Management – WWT
LinkedIn · Fintech Association Of Kenya6 reactionsBeefing up cybersecurity through data governance.