2024 Cybersecurity Guide: Adapting to ISO 27001:2022
In the ever-evolving world of cybersecurity, staying ahead of emerging threats and ensuring compliance with international standards is paramount. With the release of ISO 27001:2022, organizations are now tasked with transitioning to the updated standard to maintain their Information Security Management Systems (ISMS). This transition is not just about updating policies and procedures; it involves a thorough review and alignment of security practices with the new requirements. Below is a comprehensive cybersecurity checklist to guide your organization through the transition to ISO 27001:2022, ensuring you remain compliant and resilient in 2024.
A. Understand the Key Changes in ISO 27001:2022
- Action: Familiarize yourself with the updates in ISO 27001:2022, particularly the changes in Annex A controls, which now align with ISO 27002:2022.
- Key Changes Include:
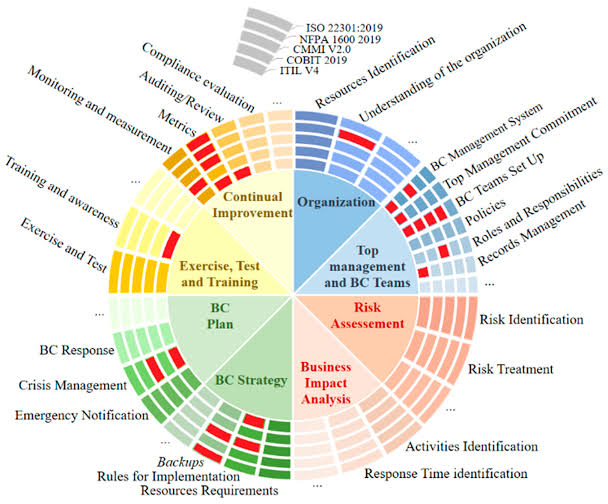
- Reduction of control categories from 14 to 4: Organizational, People, Physical, and Technological controls.
- Introduction of new controls, such as threat intelligence, information security for cloud services, and data masking.
- Enhanced focus on risk management and more granular requirements for control objectives.
B. Update Your Risk Assessment Process
- Action: Revisit your risk assessment process to ensure it aligns with the updated standard’s focus on risk management.
- Steps to Take:
- Identify new threats and vulnerabilities introduced by changes in technology, regulations, and business operations.
- Ensure that risk assessments are performed regularly and that results are documented and communicated to relevant stakeholders.
- Update your risk treatment plan to address newly identified risks and ensure that controls are implemented accordingly.

C. Review and Update Information Security Policies
- Action: Conduct a thorough review of all information security policies to ensure they reflect the new requirements of ISO 27001:2022.
- Focus Areas:
- Incorporate the new controls introduced in ISO 27001:2022 into your policies.
- Ensure that policies address the use of cloud services, remote work, and mobile devices, which have become increasingly prevalent.
- Align policies with the organization’s risk appetite and ensure they are communicated effectively across the organization.
D. Enhance Security Awareness and Training Programs
- Action: Update your security awareness and training programs to reflect the new standard’s emphasis on people controls.
- Training Should Cover:
- The importance of information security and each employee’s role in maintaining it.
- New and emerging threats, including phishing, social engineering, and ransomware.
- Best practices for secure communication, data handling, and remote work.

E. Strengthen Technical Controls and Cybersecurity Measures
- Action: Assess and enhance your technical controls to ensure they meet the requirements of ISO 27001:2022.
- Key Technical Controls:
- Threat Intelligence: Implement systems to gather, analyze, and respond to threat intelligence, enabling proactive defense against cyber threats.
- Data Masking and Encryption: Ensure that sensitive data is masked and encrypted, both in transit and at rest, to protect against unauthorized access.
- Cloud Security: Review and strengthen the security measures for cloud services, ensuring compliance with the new standard’s requirements.
F. Conduct a Gap Analysis and Internal Audit
- Action: Perform a gap analysis to identify areas where your current ISMS falls short of the ISO 27001:2022 requirements.
- Steps to Follow:
- Compare your existing controls and processes against the new standard.
- Document any gaps and create an action plan to address them.
- Conduct an internal audit to verify that the updated ISMS meets the new standard and is ready for external certification.

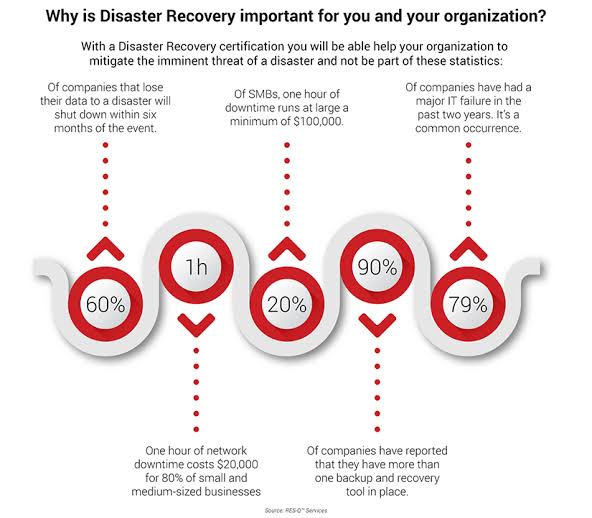
G. Update Incident Response and Business Continuity Plans
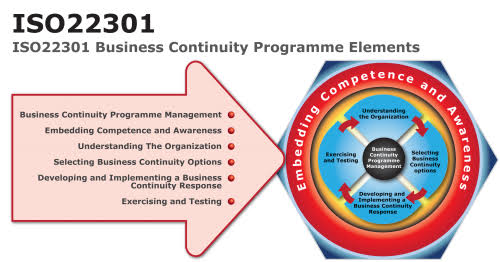
- Action: Review and update your incident response and business continuity plans to ensure they align with the new requirements.
- Key Considerations:
- Ensure that the plans address new and emerging threats, including advanced persistent threats (APTs) and supply chain attacks.
- Test the effectiveness of your incident response plan through regular drills and simulations.
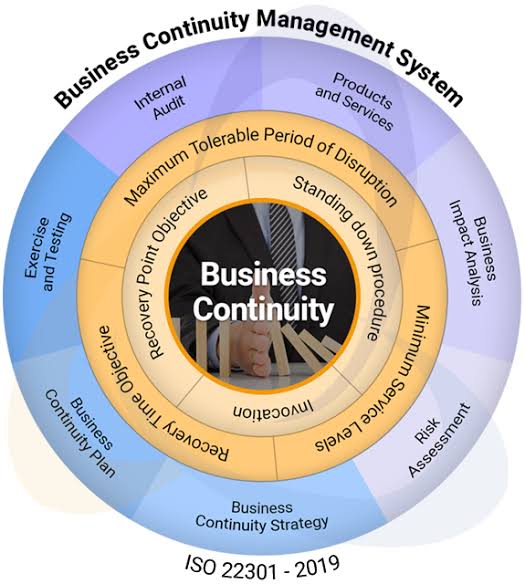
- Update recovery time objectives (RTOs) and recovery point objectives (RPOs) to reflect the organization’s current risk environment.
H. Engage Leadership and Stakeholders
- Action: Ensure that leadership is actively involved in the transition process and understands the implications of the new standard.
- Steps to Take:
- Present the benefits and challenges of transitioning to ISO 27001:2022 to senior management.
- Secure necessary resources and support for the transition, including budget allocation and personnel.
- Regularly update stakeholders on the progress of the transition and address any concerns.

I. Prepare for External Certification
- Action: Engage with a certified external auditor to schedule your ISO 27001:2022 certification audit.
- Preparation Tips:
- Ensure that all documentation is up-to-date and reflects the new standard’s requirements.
- Conduct a pre-audit review to identify any remaining issues or areas for improvement.
- Ensure that all employees are prepared for the audit and understand their roles in maintaining compliance.
J. Monitor, Review, and Improve
- Action: Establish a continuous monitoring and improvement process to maintain compliance with ISO 27001:2022.
- Key Activities:
- Regularly review the effectiveness of your controls and update them as needed.
- Stay informed about new threats, vulnerabilities, and best practices in cybersecurity.
- Foster a culture of continuous improvement, ensuring that the organization remains resilient in the face of evolving risks.
Conclusion

Transitioning to ISO 27001:2022 is a critical step in ensuring that your organization’s cybersecurity posture remains strong and compliant with international standards. By following this comprehensive checklist, you can navigate the complexities of the transition process, address emerging threats, and maintain a robust Information Security Management System that meets the demands of 2024 and beyond. Stay proactive, engage leadership, and commit to continuous improvement to achieve lasting success in your cybersecurity efforts.
Other references
Transition to ISO IEC 27001:2022 – DNVdnv.comhttps://www.dnv.com › Management-Systems › new-iso