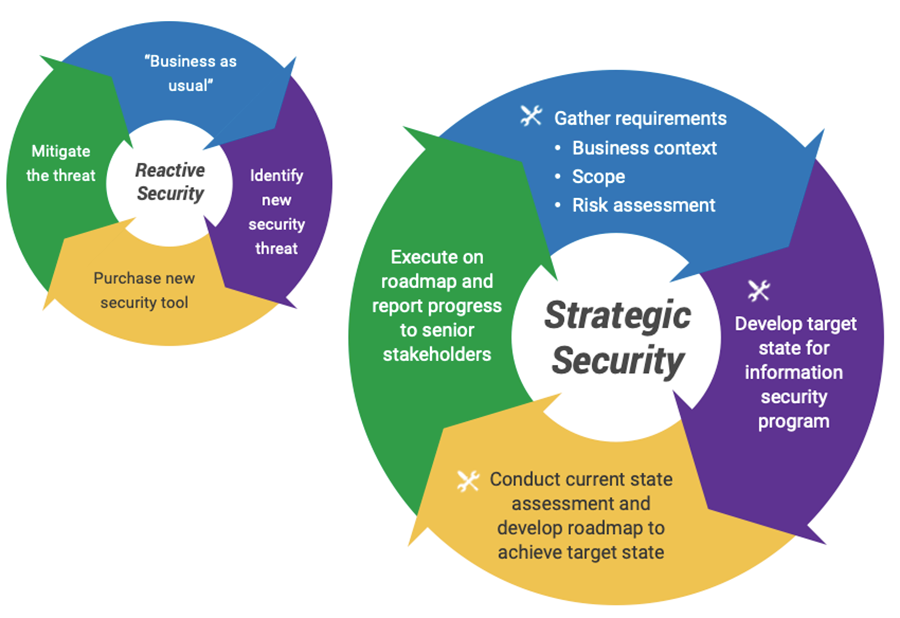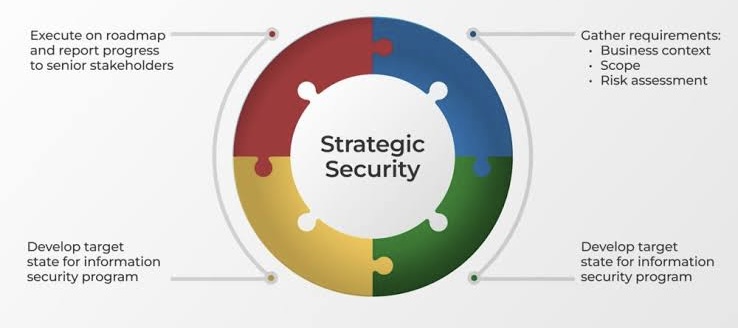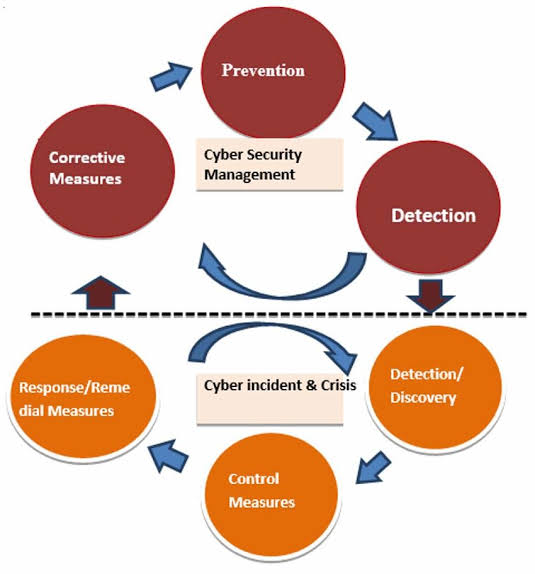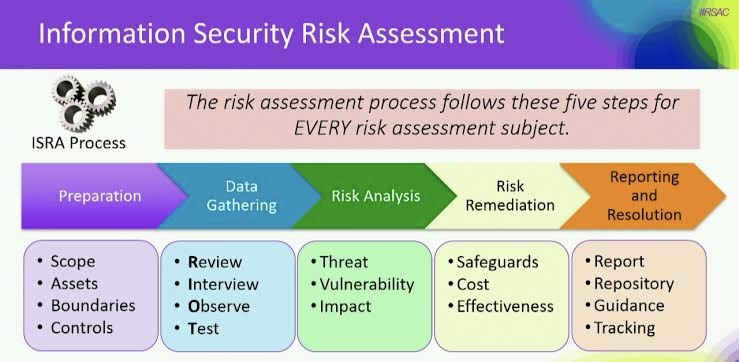
Emerging technologies have begun to play a crucial role in enhancing cybersecurity and securing data against digital threats.
These innovations not only help identify vulnerabilities but also improve defense mechanisms and data security measures.
Here are some of the most promising emerging technologies in cybersecurity:
A. Artificial Intelligence (AI) and Machine Learning (ML):
o Threat Detection and Prediction: AI and ML can analyze large datasets to identify patterns and anomalies, helping in the early detection of potential cyber threats.
o Behavioral Analysis: These technologies can learn and understand normal user behavior, making it easier to detect unusual activities that may indicate a security breach.
B. Blockchain: Originally developed for cryptocurrency transactions, Blockchain technology can be leveraged for data security due to its decentralization and transparency. Each block in the blockchain contains records, and any changes to these records must be approved by all nodes in the network. This way, it’s nearly impossible for hackers to alter or delete information without being noticed.

C. Quantum Computing: While quantum computers might pose a threat by breaking the cryptographic algorithms that underpin today’s cybersecurity, they may also lead to the development of new and more robust security techniques such as quantum encryption o a method that leverages properties of quantum mechanics to encrypt data and transmit it in a way that can not be intercepted undetected.
D. Biometrics: The use of biometric data (such as fingerprints, retinal scans, and facial recognition) as a form of identification and access control is growing. These techniques make it extremely difficult for unauthorized users to gain access to restricted areas or data.
E. Behavioral Biometrics: Behavioral biometrics goes beyond traditional methods like fingerprints and facial recognition to analyze user behavior, such as typing patterns or mouse movements. This can be used to detect unauthorized access, even if the attacker is using stolen credentials.
F. Homomorphic Encryption:
o Secure Data Processing: Homomorphic encryption allows computations to be performed on encrypted data without decrypting it. This ensures that sensitive information remains protected during processing.

G. Post-Quantum Cryptography:
o Preparing for Quantum Threats: As quantum computers advance, the need for cryptographic algorithms resistant to quantum attacks becomes crucial. Post-quantum cryptography is aimed at developing such algorithms.
H. User and Entity Behavior Analytics (UEBA):
o Insider Threat Detection: UEBA utilizes machine learning to analyze user behavior and identify unusual patterns that may indicate insider threats or compromised accounts.
I. IoT Security:
o Network Segmentation: With the increasing number of connected devices in the Internet of Things (IoT), implementing network segmentation helps isolate and secure different parts of a network, preventing lateral movement by attackers.
o Device Authentication: Emerging technologies provide robust methods for ensuring that only authorized devices can access IoT networks.
J. Cloud Security:
o Zero Trust Architecture: Instead of trusting entities based on their location within the network, a zero-trust model assumes that no one is trustworthy and requires continuous verification of identity and security posture.
o Cloud Access Security Brokers (CASB): CASBs provide an additional layer of security by monitoring and controlling data transferred between on-premises infrastructure and cloud services.

K. Cyber Threat Intelligence:
o Automated Threat Intelligence Platforms: These platforms use AI and machine learning to analyze vast amounts of threat data, providing real-time insights and helping organizations stay ahead of potential threats.
L. Edge Computing: As more devices connect to the internet under the Internet of Things (IoT), it has grown increasingly important to secure these endpoints. Edge computing helps to solve this problem by processing data on the device itself (or on a local server), rather than sending it to a remote data center. This decreases the chance of data interception during transit.
M. Zero Trust Architecture (ZTA):
o Strict Access Control: Implements the principle of “never trust, always verify,” limiting access to resources only to authenticated and authorized users and devices.
o Microsegmentation: Breaking up security perimeters into small zones to maintain separate access for separate parts of the network.
N. Cyber Physical Systems (CPS):
o Integrated Security: These systems integrate computation with physical processes and need robust security protocols to prevent dangerous, real-world consequences of cyberattacks.
O. Secure Access Service Edge (SASE):
o Converged Security: Combines networking and security functions into a single cloud-based service, improving security posture and simplifying administration.
P. 5G Technology:
o Network Slicing: Allows for the segregation of networks, providing an isolated environment for sensitive applications.
o Enhanced Encryption: Provides stronger encryption for user data and supports more secure authentication mechanisms.
Q. Automation and Orchestration: Cybersecurity automation and orchestration tools can automatically detect and respond to security incidents, patch systems, and generate reports. These tools reduce the response time to threats and allow security teams to focus on proactive tasks.
Implementing a combination of these technologies, along with robust cybersecurity policies and practices, can significantly enhance the security posture of organizations and safeguard their valuable data against evolving cyber threats. Regular updates, patches, and employee training also remain critical components of a comprehensive cybersecurity strategy.
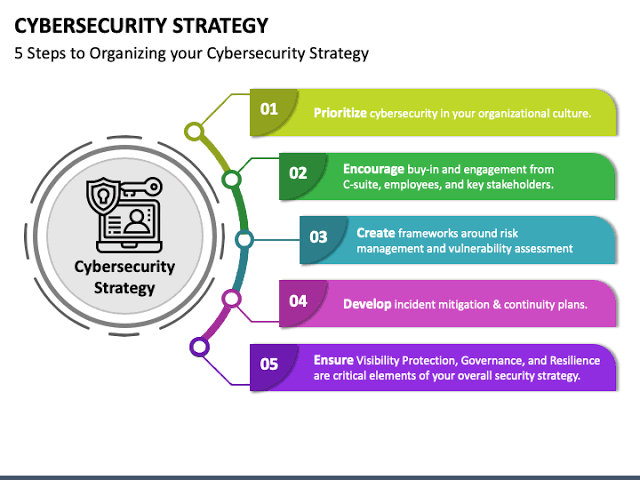
It’s also important for organizations to ensure that cybersecurity measures keep pace with the rapid development of technology, as adversaries often use sophisticated tech for malicious purposes. Regularly updating security practices, engaging in continuous monitoring, and adopting a proactive and layered security stance can help secure data effectively in the evolving digital landscape.
https://www.metacompliance.com/blog/cyber-security-awareness/emerging-technologies-and-their-impact
https://www.linkedin.com/pulse/emerging-technologies-cybersecurity-how-can-secure-your-data-polyd
https://www.ey.com/en_us/emerging-technologies/four-ways-to-embrace-emerging-tech-with-cyber
https://www.researchgate.net/publication/371339686_Cybersecurity_in_the_Era_of_Emerging_Technology