
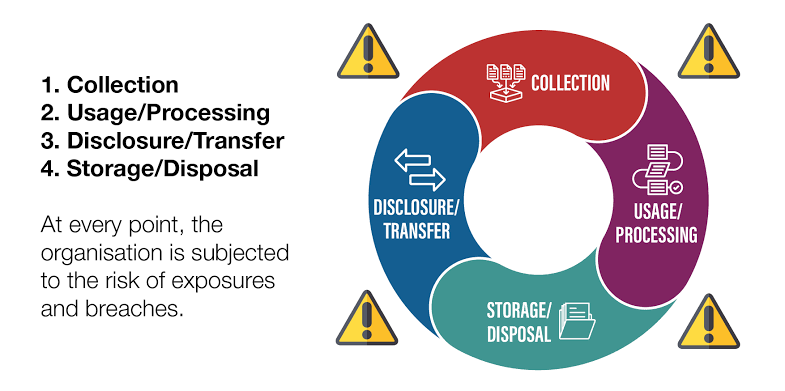
Best Practices for Data Privacy Management from ISO/IEC 27701
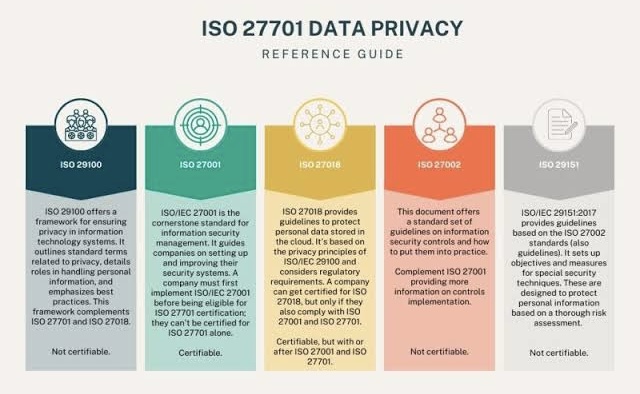
ISO/IEC 27701 (International Organization for Standardization/International Electrotechnical Commission) is a data privacy extension to ISO/IEC 27001, the widely accepted standard for information security management systems (ISMS).
ISO/IEC 27701 is a privacy information management system (PIMS) that provides guidelines on how to manage data privacy, including the necessary approaches to comply with data protection laws and regulations.
i. Here are some key best practices derived from this standard:

A. Governance and Accountability:
o Appoint a Data Privacy Officer (DPO): Establish a dedicated role responsible for privacy compliance and program management.
o Clearly define roles and responsibilities: Assign ownership of data privacy tasks to various teams and individuals.
o Conduct regular privacy impact assessments (PIAs): Evaluate the privacy risks associated with processing personal data.
o Establish a data governance framework: Define policies, procedures, and controls for data collection, storage, use, and disposal.
B. Data Protection and Security:
o Implement data minimization principles: Collect only the necessary personal data and for specific purposes.
o Encrypt sensitive data: Protect personal data at rest and in transit with strong encryption methods.
o Implement access controls: Grant access to personal data only to authorized individuals based on the principle of least privilege.
o Regularly back up and restore data: Ensure data availability and prevent data loss.
C. Transparency and Individual Rights:
o Provide clear and concise privacy notices: Inform individuals about how their data is collected, used, and shared.
o Enable individuals to exercise their data subject rights: Allow individuals to access, rectify, erase, and restrict the processing of their data.
o Respond promptly to data breach incidents: Have a documented incident response plan and inform affected individuals promptly.
D. Continuous Improvement:
o Monitor and audit privacy controls: Regularly evaluate the effectiveness of your PIMS and identify areas for improvement.
o Conduct privacy awareness training: Educate employees on their roles and responsibilities in protecting personal data.
o Stay up-to-date with evolving privacy regulations: Adapt your PIMS to comply with changing legal requirements.
ii. Here are some best practices for data privacy management according to ISO/IEC 27701:
A. Data Protection by Design and by Default:
Embed data privacy into the design of all projects, operations, and business practices. Ensure that personal data is automatically protected in any IT system, service, product, or process.
B. Legal and Regulatory Compliance:
o Stay informed about relevant data protection laws and regulations applicable to your organization.
o Establish processes to ensure ongoing compliance with legal requirements related to privacy.
C. Privacy Impact Assessments:
As per ISO/IEC 27701, organizations should conduct regular privacy impact assessments (also known as data protection impact assessments or DPIAs) to identify potential risks to personal data privacy.
D. Protection of Personal Information:
It is essential that businesses implement the appropriate technical and organizational measures to protect personal information. ISO/IEC 27701 requires that these measures are proportionate to the potential risks.
E. Transparency and Communication:
o Clearly communicate privacy practices to individuals through transparent privacy notices.
o Maintain open communication channels for addressing privacy-related concerns and inquiries.
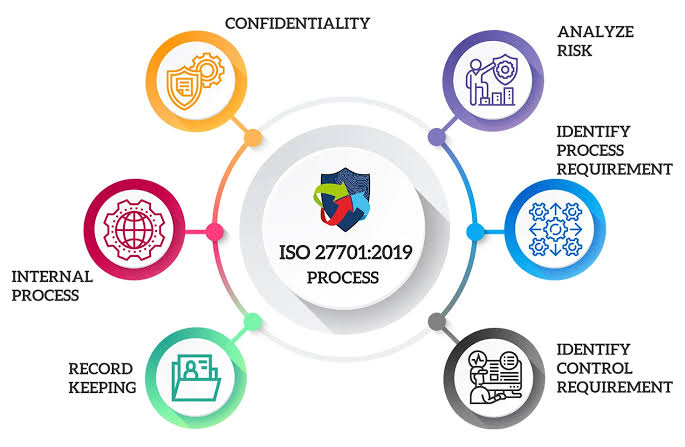
F. Data Minimization:
ISO/IEC 27701 advocates for data minimization, i.e., only collecting and processing what is necessary for the purpose intended and limiting data processing to those areas for which consent has been given.
G. Define Privacy Roles and Responsibilities:
Appoint a responsible person for data privacy, such as a Data Protection Officer (DPO) where necessary, and define privacy roles and responsibilities across the organization.
H. Conduct Risk Assessments:
Carry out Data Protection Impact Assessments (DPIAs) to identify, assess, and mitigate privacy risks associated with processing personal data.
I. Consent Management:
Have mechanisms in place to obtain, manage, and record consent from data subjects, ensuring consent is clear, informed, and specific to the processing activity.
J. Individual Rights:
o Establish processes to facilitate the exercise of individuals’ privacy rights (e.g., access, rectification, erasure).
o Respond promptly and effectively to individuals’ requests related to their personal data.
K. Policy Development:
Establish and maintain privacy policies that articulate the organization’s commitment to data privacy and outline procedures and standards for handling personal information.
L. Implement and Review Technical Controls:
Deploy appropriate technical controls like encryption, access controls, and anonymization techniques, and regularly review these controls for effectiveness.
M. Incident Response and Notification:
o Develop and test an incident response plan specific to privacy incidents.
o Establish procedures for promptly notifying relevant stakeholders and authorities in the event of a privacy breach.
N. Train and Create Awareness:
Inform and train employees about privacy obligations and policies to ensure they understand how to handle personal data appropriately and to recognize potential privacy risks.
O. Third-Party Management:
o Assess and monitor the privacy practices of third-party vendors and service providers.
o Establish contractual agreements that require third parties to adhere to the organization’s privacy policies and standards.
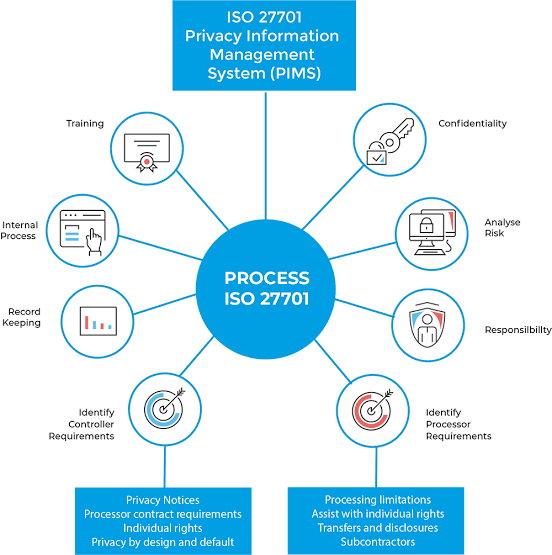
P. Documentation and Record-Keeping:
o Maintain detailed documentation of privacy policies, procedures, and activities.
o Maintain records of processing activities, as required by GDPR and other data protection regulations, that includes categories of processing activities performed on behalf of data controllers.
Q. Incident Response and Breach Notification:
Implement an incident response plan to address data breaches or privacy incidents, and comply with breach notification laws as applicable.
R. Data Transfers:
ISO/IEC 27701 also covers international data transfers and provides guidance on how to manage privacy risks in such situations.
S. Continual Improvement:
Regularly update the PIMS to adapt to changes in privacy legislation, evolving technology, and the organization’s own changing business practices.
iii. Further steps:
o Conduct due diligence on third-party processors: Ensure they have appropriate data security and privacy practices in place.
o Leverage privacy-enhancing technologies (PETs): Explore technologies like anonymization and pseudonymization to reduce privacy risks.
o Promote a culture of privacy within your organization: Make privacy a core value and integrate it into your business practices.
iv. Conclusion
By following these best practices, organizations can establish a robust data privacy management system that protects personal data, builds trust with individuals, and helps them comply with applicable privacy regulations.
ISO/IEC 27701 is especially relevant in light of regulations like the GDPR, aiding organizations in demonstrating their commitment to compliance. Adopting its framework can lead not only to better data privacy practices but also to heightened trust among customers, partners, and regulators.
v. Further references
Five Best Practices for Data Privacy Management from ISO/IEC 27701 – LinkedIn
Mediumhttps://medium.com › iso-27701-20…ISO 27701:2019 and the GDPR
TÜV SÜDhttps://www.tuvsud.com › blogs › o…Overview of ISO 27701 Controls | TÜV SÜD Thailand
