Three Strategies to Cease Unproductive Tasks
In today’s fast-paced business environment, efficiency and effectiveness are key to maintaining competitiveness and achieving long-term success.
However, not all tasks, projects, or strategies yield the desired outcomes.
Some work, despite the best intentions and efforts, simply isn’t working. Identifying and halting non-productive work can conserve resources, focus efforts on more fruitful endeavors, and increase overall organizational health.
Three steps to help you stop work that isn’t working:
o Evaluate ruthlessly. Honestly assess the value of your work. Ask yourself if it aligns with your overall goals and if it contributes to the success of your business.
o Identify time sinks. Track your activities for a day or two to pinpoint tasks that drain your time and energy but yield minimal results.
o Strategize for elimination. Once you’ve identified unproductive work, brainstorm ways to eliminate or delegate it. Can you automate it? Outsource it? Or simply remove it from your to-do list altogether?
i. Evaluate and Assess
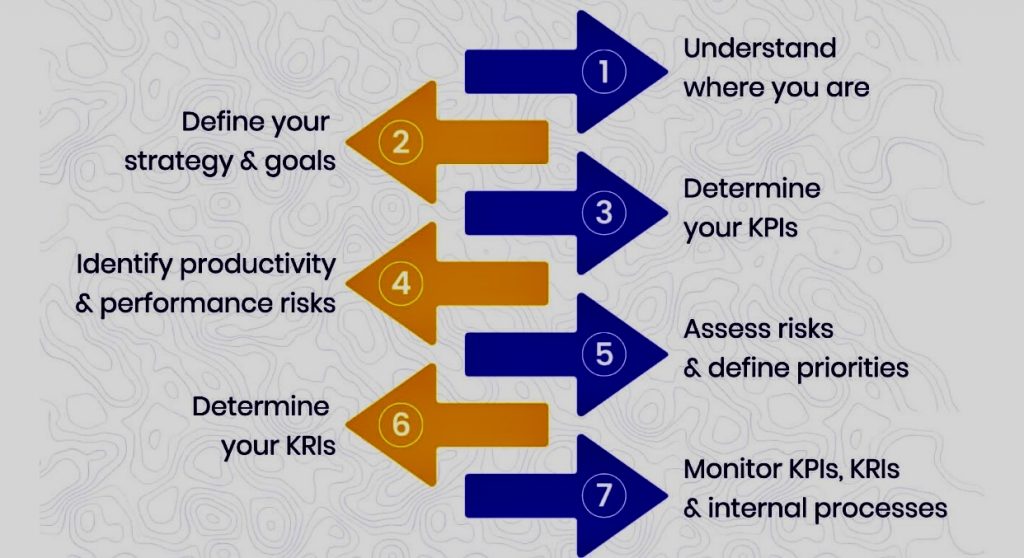
A. Establish Clear Metrics for Success
The first step in identifying work that isn’t working is to have clear, measurable goals and metrics for success. Without these metrics, it’s challenging to objectively determine whether a project or task is failing. These metrics could include return on investment (ROI), key performance indicators (KPIs), deadlines, or qualitative feedback. Regularly reviewing these metrics will provide insight into the project’s progress or lack thereof.
B. Conduct Regular Reviews
Periodic evaluations of ongoing projects and tasks are crucial. These reviews should assess the current status against the outlined metrics for success. They can be in the form of weekly check-ins, monthly reviews, or milestone-based assessments, depending on the nature of the work. It’s essential to create an environment where honest and constructive feedback is valued over preserving the status quo.
ii. Decide with Data
A. Analyze the Data
Once you have collected and reviewed data related to performance metrics, analyze it to identify patterns or issues causing the work to fail. This analysis may reveal problems with the process, resource allocation, or external factors such as market changes or new competition.
B. Involve the Right Stakeholders
Decisions on whether to halt a project should not be made in isolation. Involving key stakeholders in this process ensures that different perspectives are considered and that there is buy-in for the decision. Stakeholders might include team members, management, and possibly clients or customers if the work directly affects them.
iii. Act Decisively and Learn
A. Communication Plan
Breaking the news about stopping a project can be challenging. Develop a clear communication plan that explains the reasons for discontinuation to everyone involved, from team members to stakeholders. Highlight the evaluation process and how the decision aligns with broader business goals. Transparency is key to maintaining trust and morale within the team.
B. Execution of Termination
Once the decision is communicated, set up a methodical plan to wind down the project. This includes reallocating resources, archiving project data, and managing timelines. If the project is client-related, ensure contractual obligations are honored and clients are notified respectfully, offering solutions or alternatives as appropriate.

C. Learn from the Experience
Stopping work that isn’t working isn’t solely about cutting losses. It’s also a valuable opportunity for learning and growth. Conduct a post-mortem analysis to understand what went wrong and why. This analysis is not about assigning blame but about uncovering insights that can prevent similar issues in the future.
D. Pivot or Redirect Resources
Finally, consider how to redirect the resources freed by stopping the project. Is there an alternative approach that might yield better results? Can the team pivot to another project that aligns more closely with the organization’s goals and has a higher chance of success?
iv. Conclusion

Stopping work that isn’t producing desired results is a necessary part of business strategy in the pursuit of efficiency and effectiveness.
The process demands careful evaluation, clear decision-making, and meticulous communication.
By evaluating and assessing projects objectively, making informed decisions with the right stakeholders, and acting decisively to learn from the experiences, businesses can better focus their energies on avenues that promise greater productivity and success.
In doing so, organizations foster a culture of efficiency and continual improvement, which are the hallmarks of any thriving enterprise.
v. Further references
LinkedIn · Mattison Grey M.Ed. MMC, CPPC8 reactions · 3 years agoWhen “Don’t Quit” Doesn’t Work
LinkedIn · Mel Robbins330+ reactions · 5 years ago5 Things to Do When Work Isn’t Working
HuffPosthttps://www.huffpost.com › entryWhat to Do When Things Aren’t Working
The HR Directorhttps://www.thehrdirector.com › w…Work isn’t working, so how can we fix it?
NOBL Academyhttps://academy.nobl.io › work-isn…Why Work Isn’t Working