Utilizing the Skills Framework for the Information Age to Strategically Reduce Staff: Protecting the Future of Your Digital Workforce
In an ever-evolving digital landscape, organizations are continuously faced with the challenge of aligning their workforce capabilities with the strategic objectives and technological demands of the market. This occasionally necessitates the difficult decision of downsizing.
However, when approached with a strategic framework such as the Skills Framework for the Information Age (SFIA), downsizing can be managed in a way that not only reduces the workforce but also strategically refines it, ensuring that the remaining team is more aligned with future goals.
i. Understanding SFIA
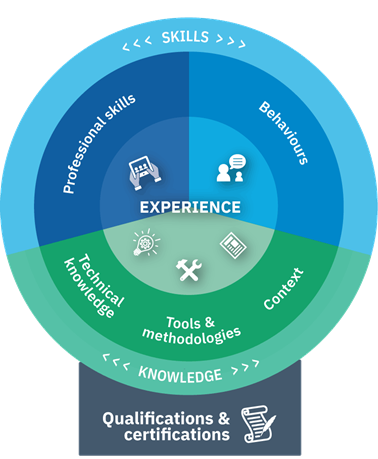
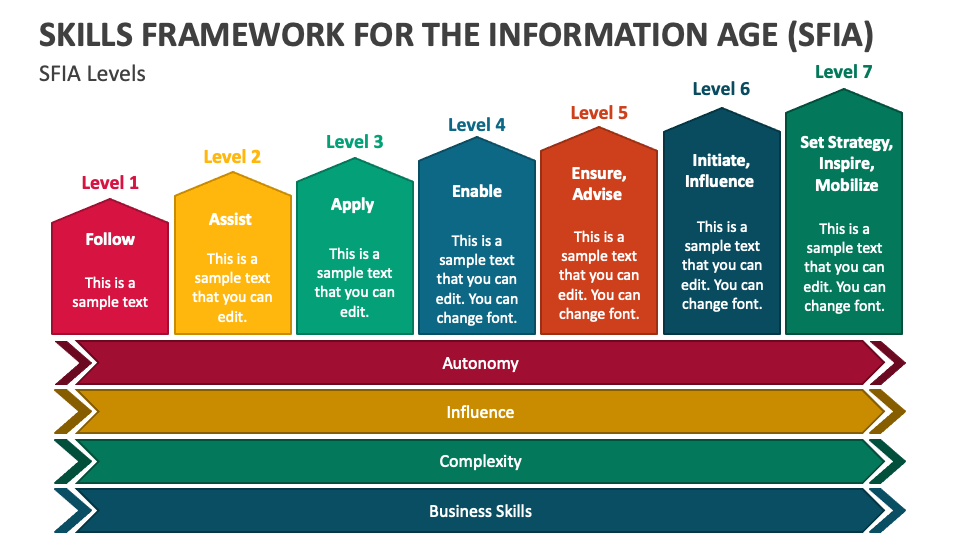
The Skills Framework for the Information Age (SFIA) provides a comprehensive model for the identification of skills and competencies required in the digital era. It categorizes skills across various levels and domains, offering a structured approach to workforce development, assessment, and strategic alignment. By mapping out competencies in detail, SFIA allows organizations to objectively assess the skills available within their teams against those required to achieve their strategic goals.
ii. SFIA: A Framework for Fair and Transparent Downsizing
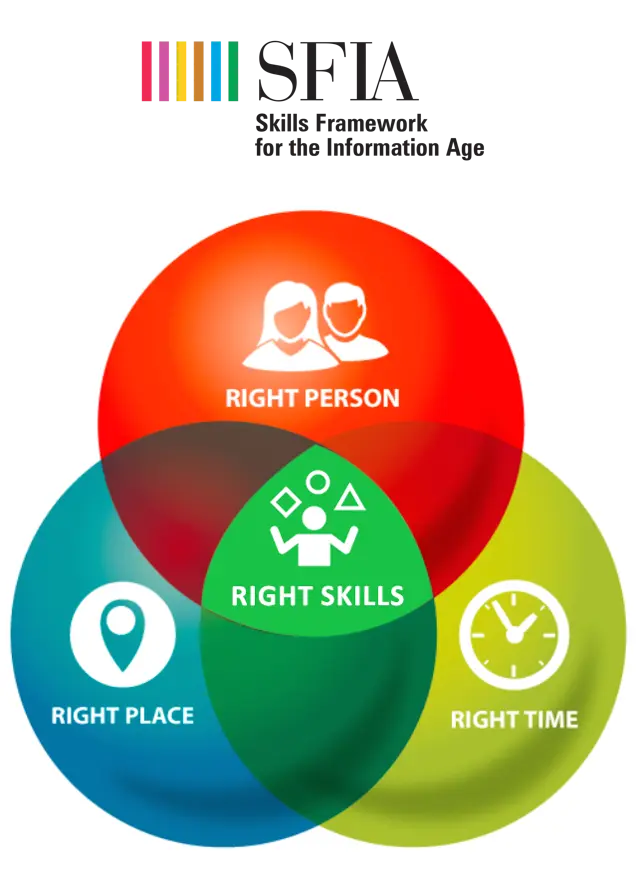
SFIA offers a standardized way to assess and compare employee skill sets. By leveraging SFIA, organizations can:
o Identify critical skills: Pinpoint the skills essential for current and future digital initiatives.
o Evaluate employee capabilities: Assess employees objectively based on their SFIA profiles, ensuring data-driven decisions.
o Maintain a strong digital core: Retain top talent with the most crucial skill sets to safeguard the team’s future.
iii. Strategic Downsizing with SFIA: A Guided Approach
A. Analyzing Current and Future Skill Requirements

The first step in leveraging SFIA for downsizing involves a thorough analysis of the current skill sets within the organization against the backdrop of the future skills required to meet evolving digital strategies. This diagnostic phase is critical in identifying not just surplus roles but also areas where the organization is at risk of skill shortages.
B. Objective Assessment and Decision Making

With SFIA, the assessment of each team member’s skills and competencies becomes data-driven and objective, mitigating biases that can often cloud downsizing decisions. This framework enables managers to make informed decisions about which roles are essential for future growth and which are redundant or can be merged with others for efficiency.
C. Skill Gaps and Redeployment

Identifying skill gaps through SFIA provides insights into potential areas for redeployment within the organization. Employees whose roles have been identified as redundant might possess other skills that are underutilized or looko could be valuable in other departments. This not only minimizes job losses but also strengthens other areas of the business.
D. Future-proofing Through Upskilling

SFIA also helps organizations to future-proof their remaining workforce through targeted upskilling. By understanding the precise skills that will be needed, companies can implement training programs that are highly relevant and beneficial, ensuring that their team is not only lean but also more capable and aligned with future digital challenges.
E. Communication and Support Structures

Effective communication is crucial during downsizing. Using the insights gained from the SFIA framework, leaders can better articulate the reasons behind the restructuring decisions, focusing on the strategic realignment towards future goals. Additionally, offering support structures for both departing and remaining employees, such as career counseling or upskilling opportunities, can help in maintaining morale and trust.
iv. Benefits of Leveraging SFIA for Downsizing
A. Objective Skills Assessment:
o SFIA facilitates an objective assessment of employees’ skills and competencies, enabling organizations to identify redundancies, skill gaps, and areas of expertise within the digital team.
o By basing downsizing decisions on skills rather than job titles or seniority, organizations can ensure alignment with strategic objectives and retain critical capabilities.
B. Strategic Workforce Planning:

o SFIA supports strategic workforce planning by providing insights into the current skill landscape, future skill requirements, and potential areas for development within the digital team.
o Organizations can use this information to align workforce capabilities with evolving business needs, anticipate skill shortages, and proactively address talent gaps.
C. Efficient Resource Allocation:

o By leveraging SFIA to identify redundancies or underutilized skills, organizations can optimize resource allocation and streamline the digital team’s structure.
o This ensures that resources are allocated effectively to high-priority projects and initiatives, maximizing productivity and return on investment.
D. Retaining Critical Capabilities:

o SFIA enables organizations to identify and retain employees with critical skills and expertise essential for the success of digital initiatives.
o By offering redeployment opportunities, upskilling programs, or knowledge transfer initiatives, organizations can retain valuable talent and maintain continuity in project delivery and innovation.
E. Enhancing Employee Engagement:
o Involving employees in the skills assessment process and offering opportunities for redeployment or skills development demonstrates a commitment to employee development and engagement.
o This approach fosters a positive organizational culture, enhances morale, and mitigates the negative impact of downsizing on remaining staff.
v. Beyond Downsizing: Building a Future-Proof Digital Team

While SFIA can aid in objective downsizing, it also promotes long-term digital team development:
o Skills gap analysis: Identify skill deficiencies across the team and implement training programs to bridge those gaps.
o Targeted upskilling: Invest in upskilling initiatives aligned with SFIA to prepare your team for future digital challenges.
o Succession planning: Leverage SFIA data to develop succession plans and cultivate future digital leaders.
vi. Conclusion
Downsizing, especially within digital and tech teams, poses the risk of eroding an organization’s competitive edge if not handled with foresight and precision.
By employing the SFIA framework, businesses can approach this delicate process objectively, ensuring that decisions are made with a clear understanding of the skills and competencies that will drive future success.
This not only helps in retaining a robust digital capability amidst workforce reduction but also aligns employee growth with the evolving needs of the organization.
Ultimately, leveraging SFIA for objective downsizing serves as a strategic maneuver to safeguard your digital team’s future, ensuring the organization emerges stronger and more resilient in the face of challenges.
vii. Further references
SFIAhttps://sfia-online.org › about-sfiaSFIA and skills management — English
De Gruyterhttps://www.degruyter.com › pdfPreparing for New Roles in Libraries: A Voyage of Discovery