Deciphering Success: The Metrics of a Digital Transformation Strategy
In an era where technology continuously evolves, businesses must adapt to stay competitive.
Digital transformation has become imperative for companies looking to improve efficiency, enhance customer experience, and innovate their processes.
However, effectively measuring the success of a digital transformation strategy is crucial to ascertain the actual value derived from these technological investments.
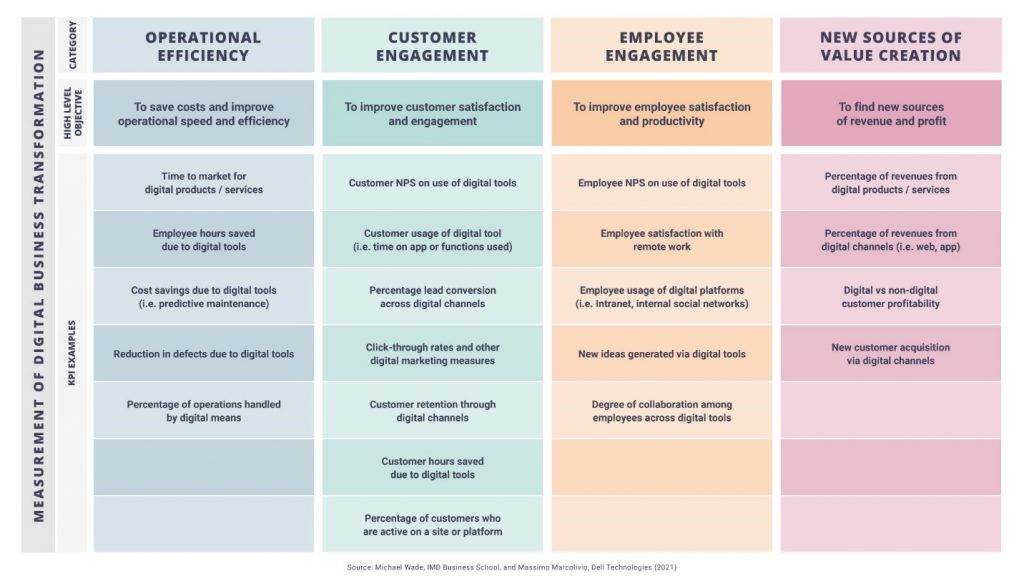
i. Defining Success: Aligning Goals and Metrics

The first step is establishing clear goals for your DX initiative. What specific problems are you trying to solve, or what opportunities are you aiming to capitalize on? Once you have these goals in mind, identify relevant metrics to track progress.
Here are some key areas to consider:
o Customer Experience (CX): Are digital touchpoints improving customer satisfaction, engagement, and loyalty? Track metrics like Net Promoter Score (NPS), customer support resolution times, or website conversion rates.
o Operational Efficiency: Is DX streamlining processes and reducing costs? Monitor metrics like time-to-market for new products, production cycle times, or administrative task completion rates.
o Innovation and Agility: Is your organization better equipped to adapt to changing market dynamics? Measure the success rate of new product launches, the number of innovative ideas generated, or the speed of response to customer feedback.
ii. Alignment with Business Objectives

The primary measure of a successful digital transformation is its alignment with the overarching business goals. Whether it’s increasing revenue, improving customer satisfaction, or reducing operational costs, the outcomes of the transformation should clearly contribute to these objectives. Setting specific, measurable goals at the outset of a digital project helps in defining what success looks like.
iii. Customer Experience Enhancement
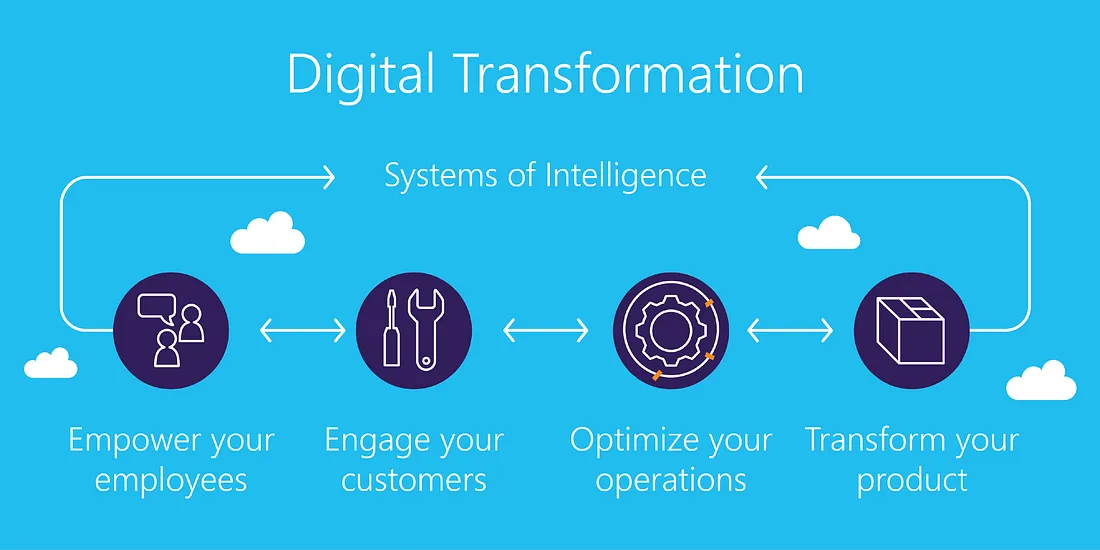
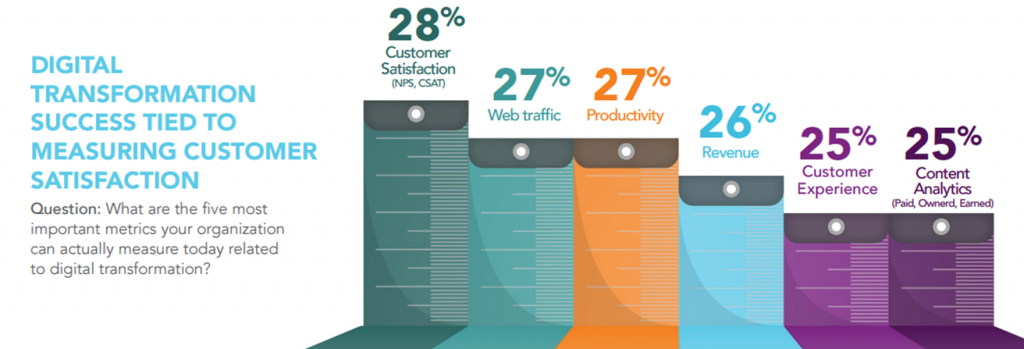
Digital transformation is often aimed at enhancing the customer experience. Metrics such as Net Promoter Score (NPS), customer satisfaction (CSAT) scores, and customer retention rates are indicative of how well the digital initiatives resonate with the target audience and drive customer loyalty.
iv. Customer Satisfaction and Engagement
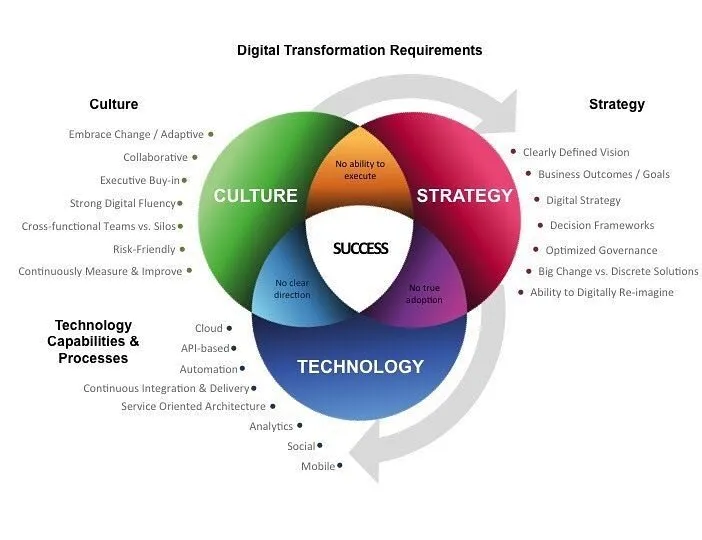
Digital transformation often aims to enhance the user experience. Metrics such as customer satisfaction scores, net promoter scores, customer retention rates, and digital engagement levels provide insights into how effectively the transformation has impacted the end user. Increased engagement or improved satisfaction levels often indicate a successful application of technology.
v. Operational Efficiency
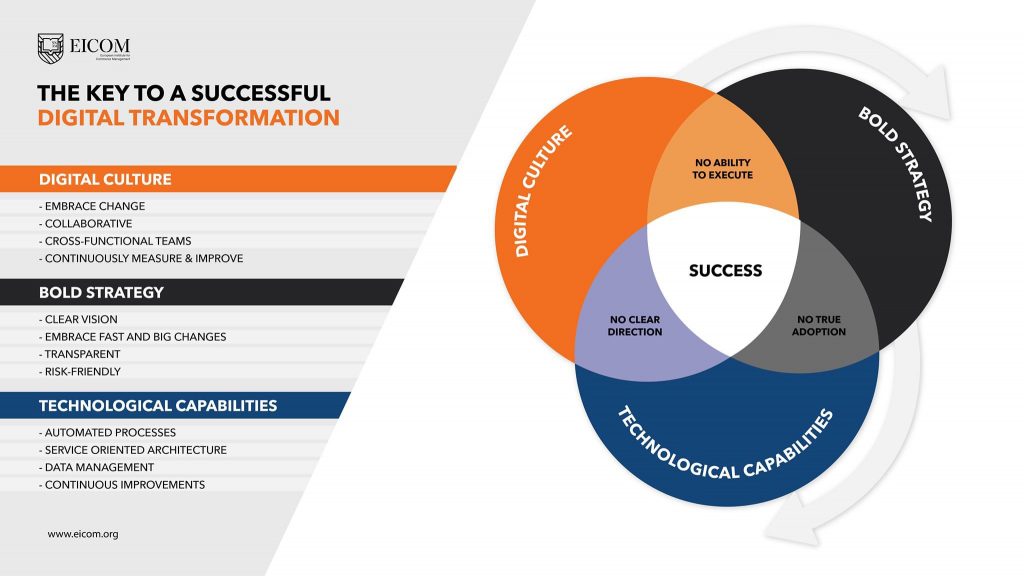
Another critical aspect of digital transformation is its impact on operational efficiency. Metrics such as the time to market for new products, employee productivity, and operational costs should be monitored. Improvements in these areas can demonstrate the effectiveness of digital tools and processes implemented during the transformation.
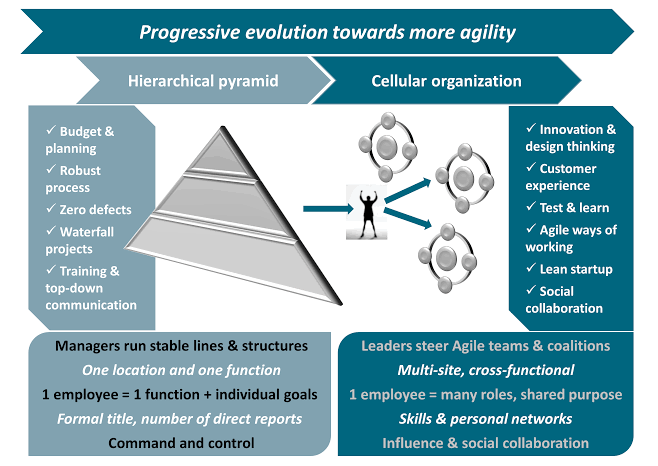
vi. Innovation and Agility
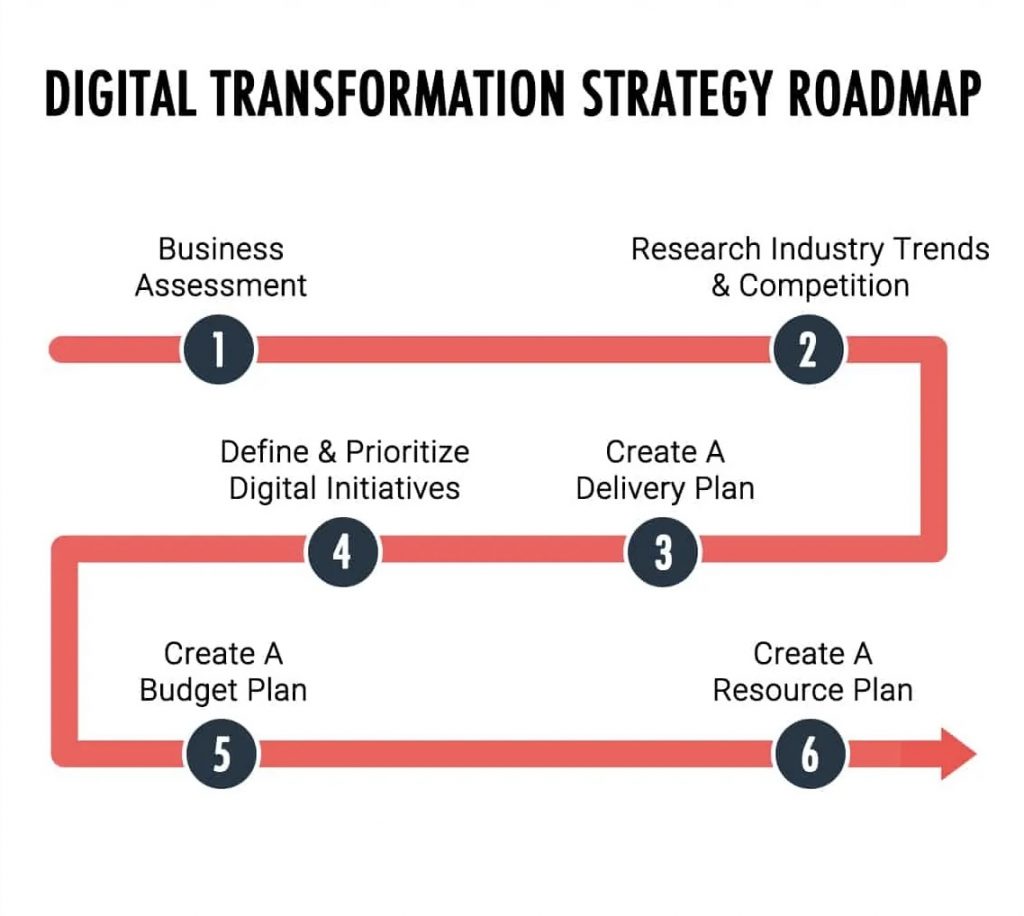
Digital transformation should ideally position a company to be more innovative and agile. This can be measured by the company’s ability to develop new products, enter new markets, or adapt to changes quickly. Tracking the number of new products launched, the time taken from concept to reality, and the response to market changes can help in measuring this aspect.
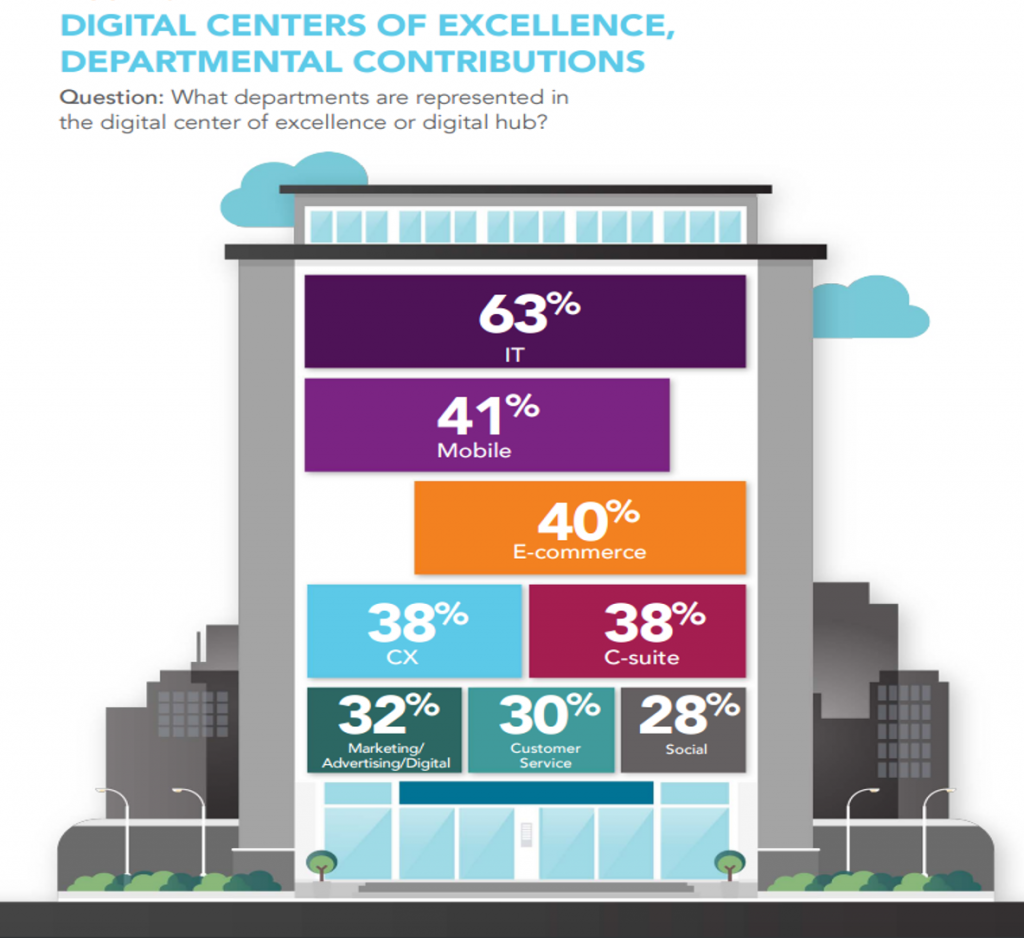
vii. Employee Adoption and Culture Change
The success of digital transformation significantly depends on how well the technology is adopted by the organization’s workforce. Metrics related to technology usage rates, employee satisfaction, and digital skill enhancements are vital. Additionally, a shift in company culture towards more digital-driven decision-making and problem-solving indicates effective internal transformations.
viii. Return on Investment (ROI)
Evaluating the financial impact is essential. This involves calculating the return on investment for digital projects by comparing the costs incurred against the financial benefits obtained. This could include increases in revenue, reductions in costs, or even the avoidance of costs.
ix. Data Utilization and Analytics

The effective use of data is a cornerstone of digital transformation. Organizations need to measure how data analytics have improved decision-making processes, personalized customer experiences, or optimized operations. Metrics on data-driven outcomes can provide clarity on the success of the transformation efforts.
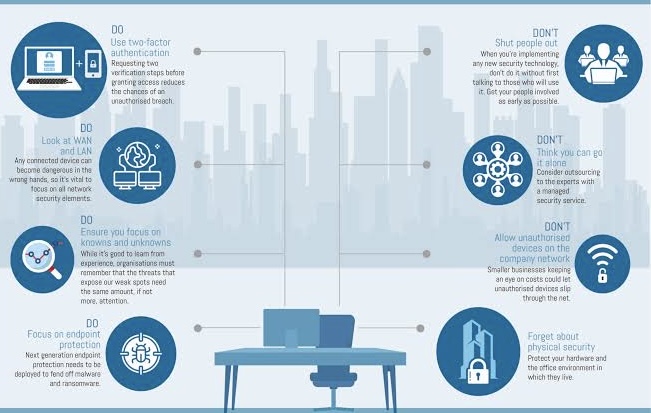
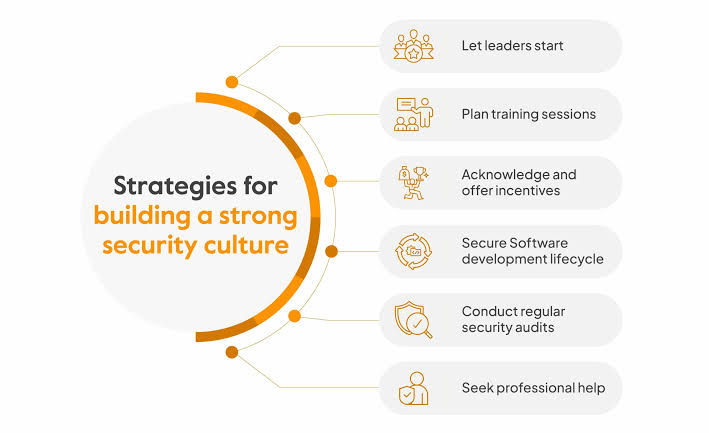
x. Security and Compliance Metrics
As digital solutions are implemented, it’s crucial to ensure that they adhere to relevant security standards and compliance requirements. Metrics related to security incidents, compliance audits, and risk assessments are critical in evaluating the resilient deployment of digital technologies.
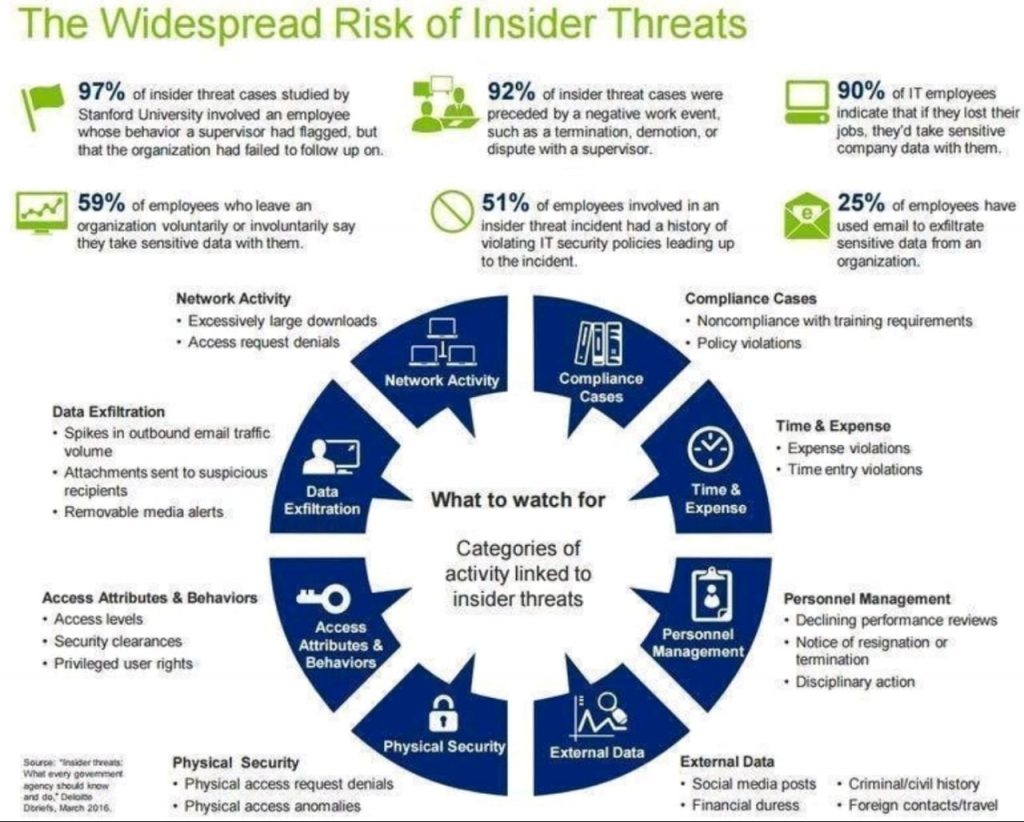
xi. Cybersecurity and Risk Management
With increased digitization comes heightened cybersecurity risks. Success in digital transformation can be measured by the organization’s ability to mitigate cyber threats effectively, adherence to compliance standards, and the resilience of its digital infrastructure against potential security breaches.
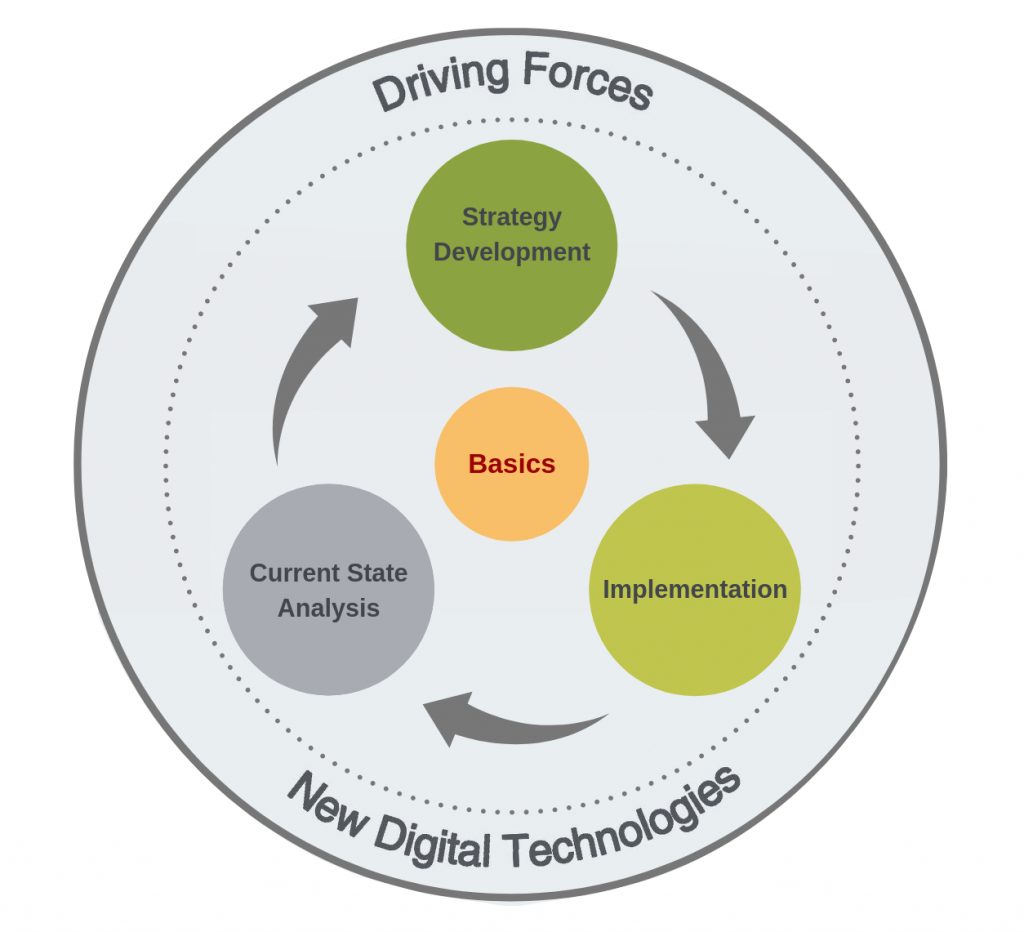
xii. Long-term Sustainability
Finally, measuring the long-term impact of digital transformation efforts on business sustainability is critical. This includes evaluating strategic resilience, market position, and competitive advantage over time. Metrics for analyzing these aspects might be more qualitative but are essential for understanding the enduring value of digital movements.
xiii. Beyond the Numbers: The Human Factor

Remember, DX is not just about technology; it’s about people. Consider metrics that reflect employee engagement with the new tools and processes. Are they more productive and empowered? Track employee training completion rates, user adoption of new platforms, or internal surveys to gauge sentiment towards DX efforts.
xiv. A Holistic View: The Balanced Scorecard Approach

A balanced scorecard approach provides a comprehensive view of DX success. Combine traditional financial metrics with CX, operational efficiency, and employee engagement data to paint a complete picture. This holistic approach ensures DX initiatives contribute to long-term strategic goals.
xv. It’s a Journey, Not a Destination
Digital transformation is an ongoing process, not a one-time event. Regularly monitor your chosen metrics and be prepared to adapt your strategy as needed. Embrace a culture of continuous learning and improvement to ensure your DX initiative delivers lasting value.
xvi. Beyond Measurement: The Power of Storytelling
While metrics are crucial, don’t underestimate the power of storytelling. Showcase real-world examples of how DX has improved customer experiences, streamlined operations, or empowered employees. This narrative can foster buy-in and enthusiasm for the ongoing transformation journey.
xvii. Conclusion
Measuring the success of a digital transformation strategy is multi-dimensional and requires a balanced look at various aspects of the business.
It’s not just about adopting new technologies but transforming processes, culture, and customer interactions for holistic growth and sustainability.
Through establishing clear goals, selecting relevant metrics, and incorporating a holistic view, the success of digital transformation strategy can be effectively measured.
By focusing on these key metrics, organizations can objectively assess the impact and value of their digital transformation efforts, paving the way for informed decisions and continuous improvement.
xviii. Further references
Unosquarehttps://www.unosquare.com › blog6 Key Metrics For A Successful Digital Transformation
McKinsey & Companywww.mckinsey.comHow do you measure success in digital? Five metrics for CEOs
LinkedInhttps://www.linkedin.com › adviceHow to Measure Your Digital Transformation …
Deloittehttps://www.deloitte.com › digitalMeasuring value from digital transformation
Gartnerhttps://www.gartner.com › how-to…How To Measure Digital Transformation Progress
Medium · Michael Martino5 months agoMeasuring the success of a digital transformation strategy