CyBOK’s Web & Mobile Security Knowledge Area (WMSKA)
The CyBOK Web & Mobile Security Knowledge Area (WMSKA) dives into the intricate world of safeguarding applications and systems in the modern web and mobile ecosystem.
i. It serves as a valuable resource for both academic and professional audiences, aiming to:
A. For Academics:
o Guide course development: The WMSKA provides a structured framework for designing academic programs focused on web and mobile security.
o Assess student knowledge: It establishes a baseline for evaluating learner expertise in key areas of web and mobile security threats and defenses.
B. For Industry Professionals:
o Enhance security practices: The WMSKA offers practical guidance on implementing effective security measures for web and mobile applications.
o Identify vulnerabilities and mitigations: It helps professionals understand common threats and implement appropriate countermeasures to protect their systems.
ii. Core Focus of WMSKA:
A. Intersection of Web & Mobile Security: The WMSKA emphasizes the interconnectedness of security mechanisms, vulnerabilities, and mitigation strategies in both web and mobile domains.
B. Evolution of the Ecosystem: It acknowledges the rapid advancements in web and mobile technologies and adapts its focus to emerging threats and security challenges.
C. Client-Server Interaction: The WMSKA highlights the critical role of secure communication between client-side applications (web browsers, mobile apps) and server-side infrastructure.
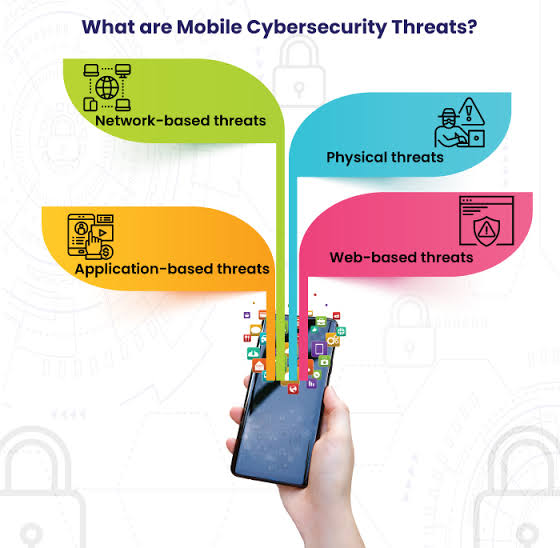
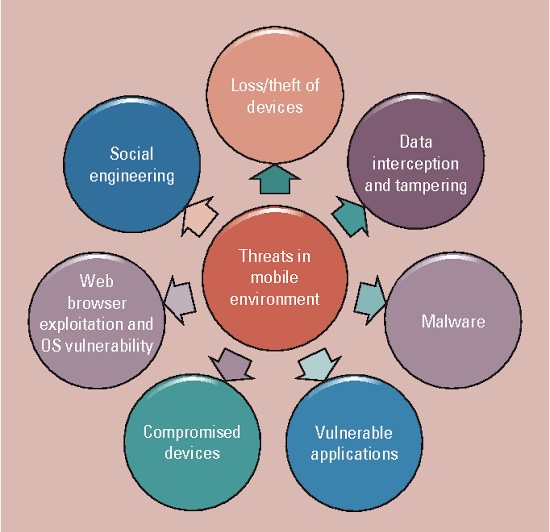
iii. The knowledge area would typically cover issues such as:

A. Web Security:
a. Web Application Vulnerabilities: Issues like SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and more.
b. Browser Security: The safety features within web browsers, such as same-origin policies, content security policies, and sandboxing.
c. Web Protocols Security: Secure communication over the internet using HTTPS and TLS, and the security of other web-based protocols.
d. Server Security: Protecting web servers and the infrastructure that supports web applications from attacks such as DDoS.

B. Mobile Security:
a. Mobile Platform Vulnerabilities: Security weaknesses inherent within mobile operating systems like Android and iOS.
b. App Security: Security issues within mobile applications, including both design flaws and implementation bugs.
c. Mobile Device Management (MDM): Techniques and policies for managing the security of mobile devices in an organizational context.
d. Security Architecture for Mobile Applications: Best practices and patterns for developing secure mobile applications.
e. Emerging Technologies: Addressing security in relation to new mobile technologies such as 5G and the use of mobile tech in Internet of Things (IoT) devices.
iv. Benefits of Utilizing WMSKA:

A. Proactive Approach to Security: By understanding vulnerabilities and mitigation techniques, professionals can proactively build secure web and mobile applications.
B. Reduced Risk of Attacks: Implementing the knowledge contained in the WMSKA can significantly reduce the risk of successful cyberattacks on your systems.
C. Improved Overall Security Posture: The WMSKA promotes a holistic approach to web and mobile security, leading to a stronger overall security posture for your organization.
v. Here are some additional resources:

A. Books:
o “The Tangled Web: A Guide to Securing Modern Web Applications” by Michal Zalewski
o “Web Application Security: Exploitation and Countermeasures for Modern Web Applications” by Andrew Hoffman
o “Mobile Application Security” by Himanshu Dwivedi, Chris Clark, David Thiel
B. Research Papers & Reports:
o Google’s yearly Android Security reports
o Whitepapers published by OWASP on both web and mobile security.
C. Websites & Online Resources:
o The Open Web Application Security Project (OWASP): Their resources on web application and mobile security are industry standards.
o SANS InfoSec Reading Room: Contains numerous papers and articles on web and mobile security.
D. Courses & Tutorials:
o Coursera: “Web and Mobile Security” by University of Maryland
o Pluralsight: “Web Security and the OWASP Top 10: The Big Picture”
o Udemy: Courses on Android and iOS app security
E. Webinars, Podcasts, & Videos:
o RSA Conference webcasts relating to web and mobile security
o OWASP’s YouTube channel has many talks focused on web and mobile security issues.
vi. Conclusion
The Cyber Security Body of Knowledge (CyBOK) aims to codify the foundational and generally recognized knowledge on Cyber Security. Each knowledge area within CyBOK provides a high-level description of its topic, explaining core concepts, key issues, and technologies.
The Web & Mobile Security Knowledge Area within CyBOK deals specifically with security aspects of web and mobile computing systems. Given the pervasiveness of web and mobile technologies in modern life, this area reflects key issues that concern the security of applications and services that run on these platforms.
Studying these areas provides valuable insights into the current threats and security practices necessary to protect web and mobile systems. Professionals working in Cyber Security, or anyone interested in the field, are likely to find this information critical, as web and mobile technologies underpin much of the global digital ecosystem.
https://www.cybok.org/media/downloads/Web__Mobile_Security_issue_1.0_XFpbYNz.pdf