
Next-Generation Third-Party Risk Management (NextGen TPRM) is a vital approach to managing cyber risk linked to business partnerships and collaborations.
As organizations broaden their digital footprints, they increasingly rely on third-party providers for various services. However, this can lead to heightened cyber risk because organizations cannot control their partners’ security measures directly.
Traditional Third-Party Risk Management (TPRM) approaches often fall short in addressing the evolving threat landscape. This necessitates a transition to NextGen TPRM, a more dynamic and comprehensive approach to managing third-party cyber risk.
i. Challenges of Traditional TPRM
A. Static and infrequent assessments: Traditional TPRM methods rely on periodic assessments, failing to capture real-time changes in risk posture.
B. Limited visibility: Lack of comprehensive insights into third-party security posture and vulnerabilities.
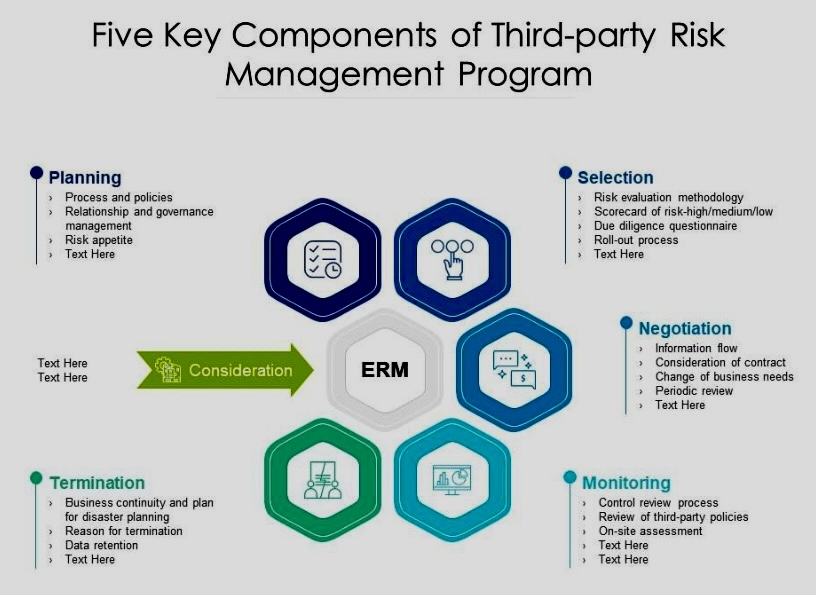
C. Reliance on self-assessments: Over-dependence on self-reported information from third parties, potentially masking actual risks.
D. Manual and inefficient processes: Time-consuming manual processes hinder the scalability and effectiveness of TPRM.
ii. Benefits of NextGen TPRM
A. Continuous monitoring: Real-time monitoring of third-party security posture and threats to proactively identify and mitigate risks.
B. Enhanced visibility: Deeper insights into third-party security controls, vulnerabilities, and potential attack vectors.
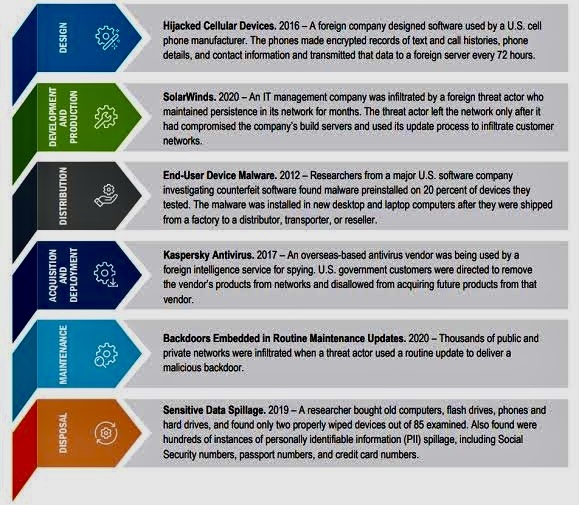
C. Automated assessments: Utilizes automation to streamline assessments, reduce manual effort, and improve efficiency.
D. Integrated risk management: Integrates seamlessly with existing risk management frameworks for holistic risk management.
E. Data-driven decisions: Leverages data analytics to inform risk-based decisions and prioritize mitigation efforts.
iii. Key Features of NextGen TPRM Solutions
A. Automated risk assessments: Employ AI and machine learning to analyze a wider range of data points and identify potential risks.
B. Continuous monitoring: Leverage threat intelligence and security automation tools to provide real-time visibility into third-party security posture.

C. Collaboration tools: Facilitate secure communication and collaboration between organizations and their third parties.
D. Standardized reporting: Provide consistent and transparent reporting on third-party risks and mitigation actions.
E. Risk-based prioritization: Identify and prioritize critical third-party risks based on their potential impact and likelihood of occurrence.
Elevated cyber risk in the context of Third-Party Risk Management (TPRM) arises when the security measures of these third parties are lacking.
If the third-party suffers a data breach, the organization’s security and reputation can be severely impacted. Therefore, NextGen TPRM strategies are essential for mitigating these elevated cyber risks.
iv. Implementing NextGen TPRM
A. Scalable TPRM Framework:
– Strategy: Develop a scalable TPRM framework that adapts to the organization’s growth and evolving cyber risks.
– Rationale: Ensures the sustainability and effectiveness of TPRM practices over time.
B. Develop and implement policies and procedures:
– Strategy: NextGen TPRM (Third-Party Risk Management) represents a significant shift from traditional approaches, emphasizing continuous monitoring, enhanced visibility, and automation. – Rationale: Implementing NextGen TPRM requires robust policies and procedures that guide the entire lifecycle of third-party relationships.
C. Continuous Monitoring:
– Strategy: Implement continuous monitoring tools to assess third-party cyber risks in real-time.
– Rationale: Enables proactive identification of potential threats and vulnerabilities.

D. Automated Risk Assessment:
– Strategy: Utilize automated tools to assess and score the cybersecurity posture of third parties.
– Rationale: Enhances efficiency and provides a more accurate and timely risk assessment.
E. Dynamic Risk Scoring:
– Strategy: Implement dynamic risk scoring that adapts to changing cyber threat landscapes.
– Rationale: Ensures a more responsive risk management approach to evolving cyber risks.
F. Threat Intelligence Integration:
– Strategy: Integrate threat intelligence feeds to stay informed about emerging cyber threats.
– Rationale: Enhances the ability to anticipate and mitigate risks based on current threat landscapes.
G. Contractual Cybersecurity Requirements:
– Strategy: Include robust cybersecurity requirements in third-party contracts.
– Rationale: Sets clear expectations for cybersecurity practices and standards.
H. Joint-Testing and Audits:
– Strategy: Conduct regular joint-testing and audits of third-party security measures and compliance.
– Rationale: Include provisions for this in contractual agreements.
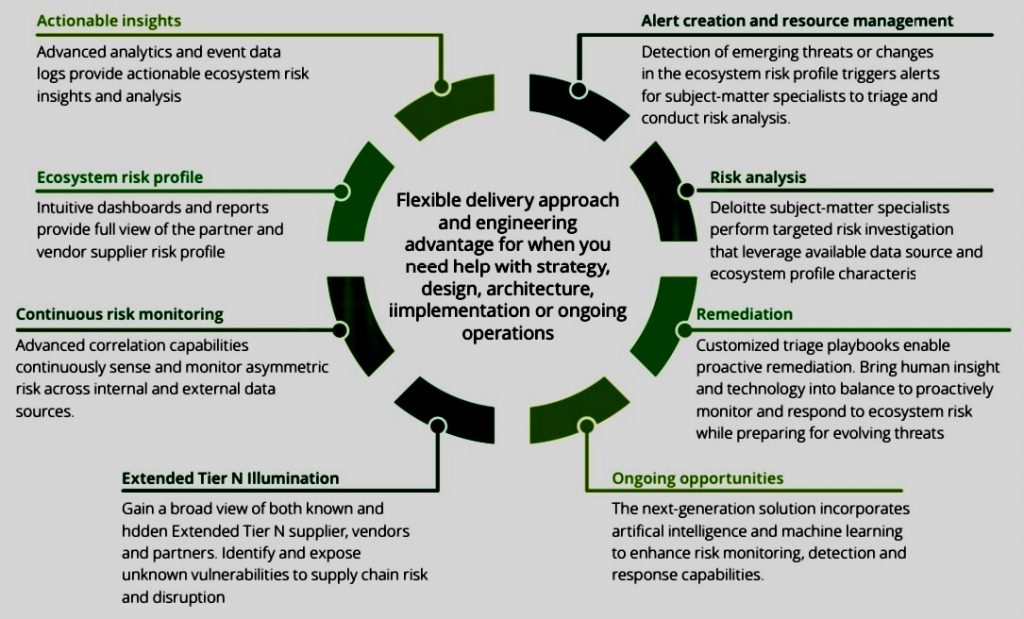
I. Incident Response Planning:
– Strategy: Collaborate with third parties on incident response planning and coordination.
– Rationale: Ensures a swift and coordinated response in case of a cybersecurity incident.
J. Supply Chain Security:
– Strategy: Extend security measures to the entire supply chain ecosystem.
– Rationale: Addresses risks that may originate from interconnected suppliers and partners.
K. Regulatory Compliance Adherence:
– Strategy: Ensure third parties comply with relevant cybersecurity regulations.
– Rationale: Mitigates legal and compliance risks associated with cybersecurity breaches.
L. Vulnerability Management:
– Strategy: Collaborate with third parties on effective vulnerability management practices.
– Rationale: Reduces the likelihood of cyber incidents resulting from known vulnerabilities.
M. Cybersecurity Training for Third Parties:
– Strategy: Provide cybersecurity training and awareness programs to third-party personnel.
– Rationale: Strengthens the overall cybersecurity posture by extending knowledge and best practices.
N. Blockchain for Supply Chain Transparency:
– Strategy: Explore blockchain technology to enhance transparency in the supply chain.
– Rationale: Increases visibility and traceability, reducing the risk of malicious activities.
In today’s interconnected world, organizations rely heavily on third-party vendors for various services and functions. While this provides agility and efficiency, it also introduces significant cyber risks.
By embracing NextGen TPRM, organizations can gain greater visibility and control over their third-party risks, ultimately leading to a more secure and resilient IT ecosystem. This is crucial in today’s environment, where cyberattacks are increasingly sophisticated and targeted towards vulnerabilities within the supply chain.
