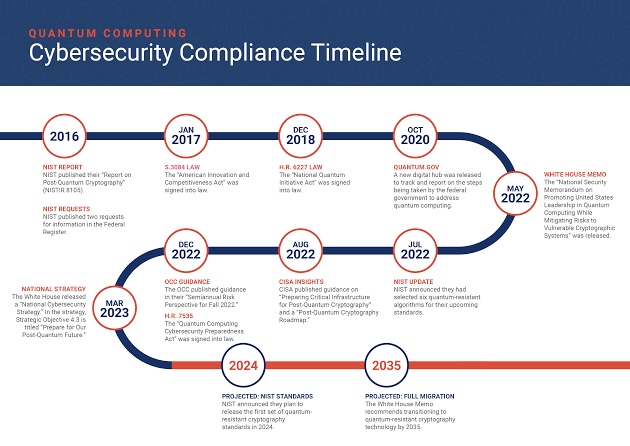
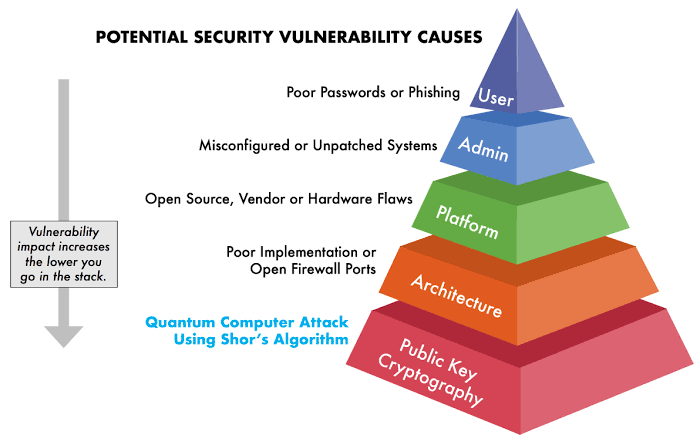
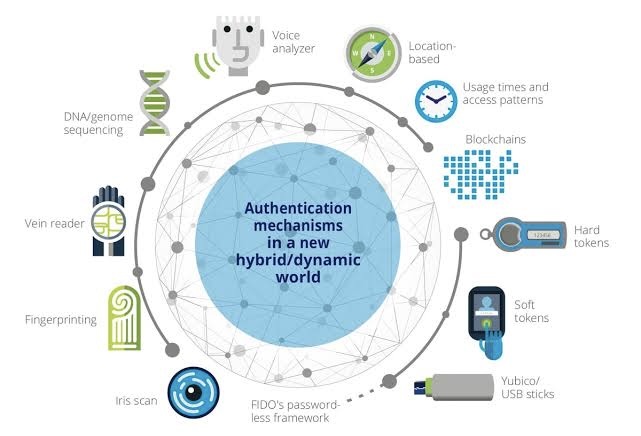
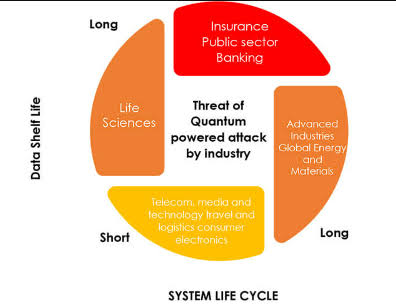
Decoding Cyber-Attacks: Understanding the Intricacies
In our increasingly digitized world, the prevalence of cyber-attacks has become a significant concern. From individuals to large corporations, everyone is a potential target.
These malicious activities are perpetrated by individuals or groups with the intent of disrupting, damaging, or gaining unauthorized access to computer systems, networks, or devices.
Understanding what cyber-attacks entail is crucial for fortifying our defenses against these ever-evolving threats.
i. Understanding Cyber-Attacks
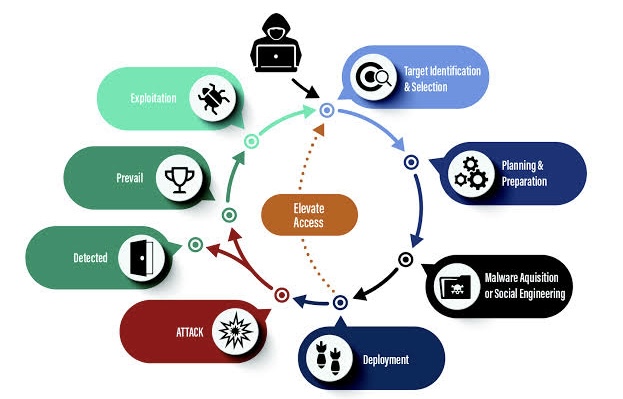
o A Malicious Intent: At their core, cyberattacks are deliberate attempts by individuals or groups to gain unauthorized access to devices, computer systems or network infrastructures for various malicious purposes.
o These purposes can range from data theft and financial gain to sabotage, espionage, or simply causing disruption.
o The mechanisms and techniques used in such attacks are diverse and continually evolving, making cybersecurity a relentless battle between attackers and defenders.
o These unauthorized attempts can lead to data breaches, financial loss, damage to reputation, and even compromise national security.
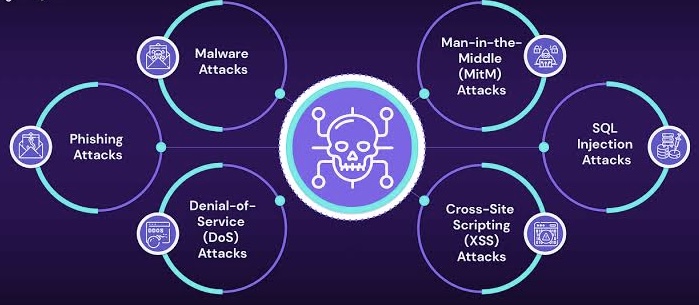
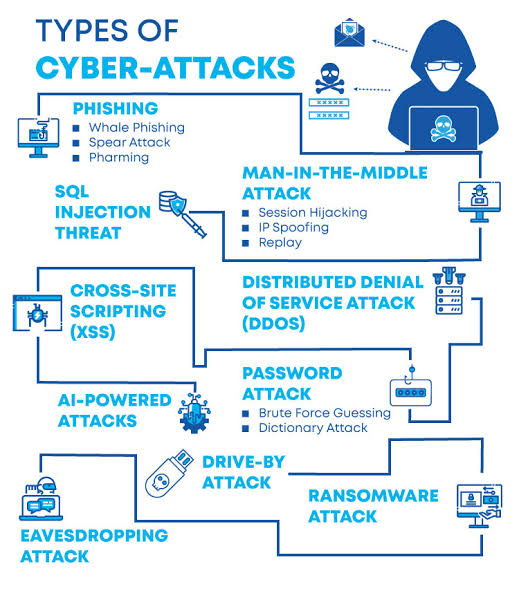
ii. Types of Cyber-Attacks
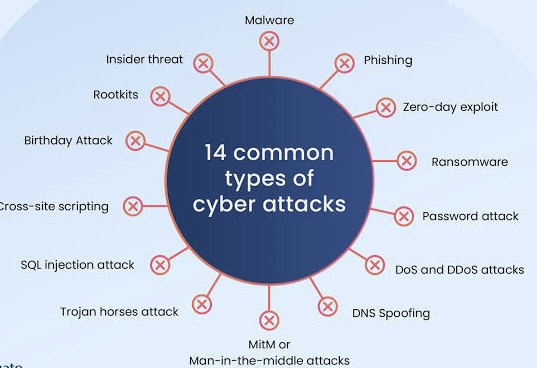
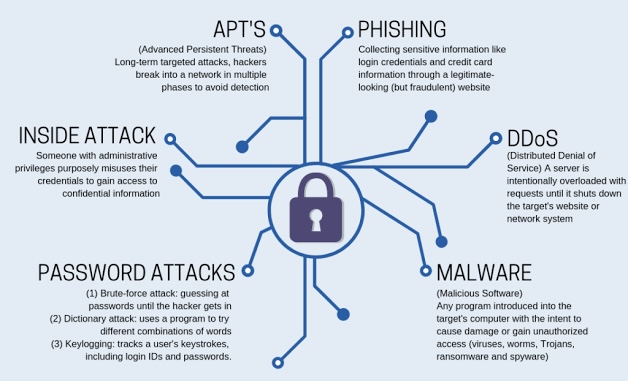
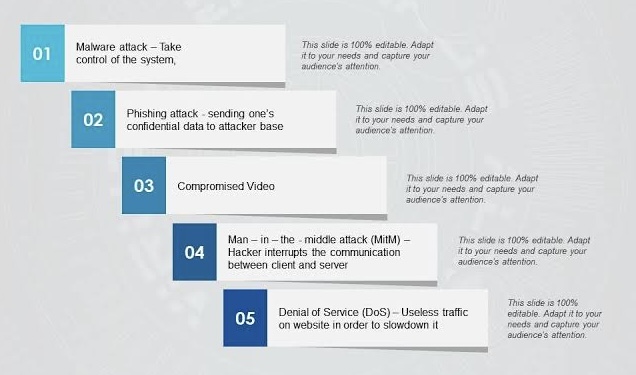
o Malware Attacks: These involve malicious software such as viruses, worms, trojans, and ransomware that disrupt or damage systems, steal data, or hold data hostage for ransom.
o Phishing Attacks: Cybercriminals use fraudulent communications, often via email, to trick individuals into revealing sensitive information or downloading malware.
o Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks: These attacks aim to overload systems, networks, or servers with excessive traffic, rendering them inaccessible to legitimate users.
o Man-in-the-Middle (MitM) Attacks: Attackers intercept and possibly alter communications between two parties without their knowledge.
o SQL Injection: Through insertion of malicious code into SQL queries, attackers can manipulate databases to access or modify data they should not have access to.
o Zero-Day Exploits: These involve attacking software vulnerabilities before the vendor has identified and fixed the issue, hence the term “zero-day” to indicate the exploit occurs before any protection is available.
iii. A Multi-Pronged Approach
Cybercriminals employ various methods to achieve their goals, and these methods are constantly evolving. Here are some common attack vectors:
o Malware: Malicious software like viruses, worms, and ransomware can infect devices, steal data, or disrupt operations.
o Phishing: Deceptive emails or messages lure users into clicking malicious links or attachments, compromising their systems.
o Social engineering: Attackers exploit human psychology to manipulate individuals into revealing sensitive information or granting unauthorized access.
o Exploiting vulnerabilities: Unpatched software or weak security configurations create openings that attackers can exploit to gain access to systems.
iv. The Motives Behind Cyber-Attacks

Cyber-attacks are driven by a multitude of motives, including but not limited to:
o Financial Gain: Many cyber-attacks are financially motivated, with hackers seeking to steal sensitive data or extort money through ransomware. Cryptocurrency has become a preferred mode of payment for ransom demands.
o Espionage and State-Sponsored Attacks: Nation-states may conduct cyber-espionage to gather intelligence or disrupt critical infrastructure. State-sponsored attacks can have far-reaching consequences, impacting global geopolitics.
o Hacktivism: Activists or groups with specific agendas may engage in cyber-attacks to promote their causes. This can involve defacing websites, leaking sensitive information, or disrupting online services.
o Cyber Warfare: As technology intertwines with national security, cyber warfare includes attacks on military systems, critical infrastructure, and government networks. It has the potential to escalate geopolitical tensions.
o Espionage: Both corporate and state-sponsored actors engage in cyber-attacks to steal sensitive information, intellectual property, or state secrets.
o Sabotage: In some cases, the goal is to disrupt operations, damage reputations, or exact revenge.
o Stealing data: This encompasses sensitive information like financial records, personal details, or intellectual property.
o Disrupting operations: Cyberattacks can cripple computer systems or networks, causing operational disruptions and financial losses.
o Deploying malware: Malicious software can be installed on compromised systems to steal data, damage files, or launch further attacks.
o Extortion: Attackers may threaten to leak stolen data or disrupt operations unless a ransom is paid.
v. The Impact of Cyber-Attacks
The implications of cyber-attacks can be widespread and devastating.
o Financial losses: Businesses can suffer from lost revenue, operational costs, and potential fines due to data breaches.
o Reputational damage: Cyberattacks can erode trust and damage an organization’s reputation.
o Privacy violations: Data breaches can expose personal information, leading to identity theft and other serious consequences.
o Disruptions: Cyberattacks can disrupt critical infrastructure, impacting essential services like healthcare, transportation, and utilities.
o For individuals, the consequences include identity theft, loss of privacy, and financial loss. o Businesses and organizations might suffer from operational disruptions, loss of sensitive data, financial damages, legal implications, and reputational harm.
o At the state level, cyber-attacks can threaten national security, undermine public trust in institutions, and disrupt essential services.
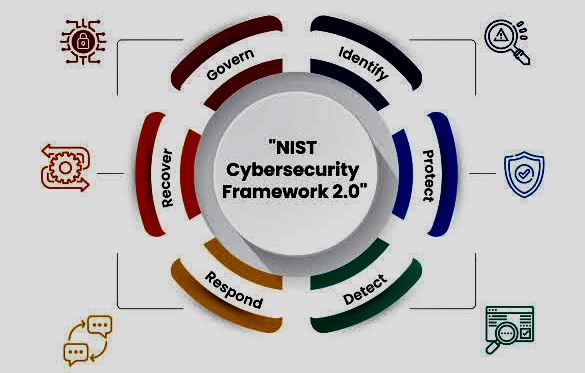
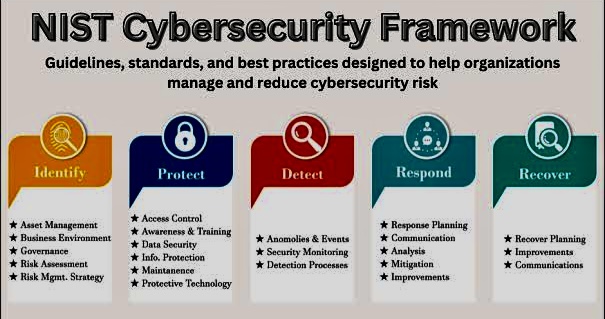
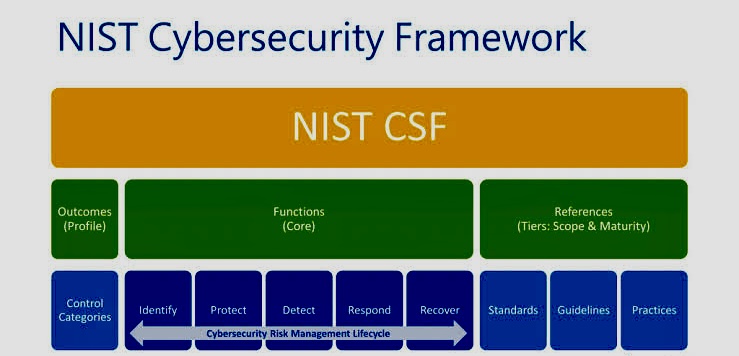
vi. Prevention and Mitigation Strategies
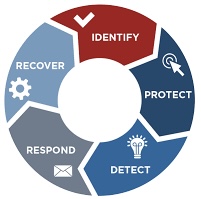
Protecting against cyber-attacks requires a multi-faceted approach:
o Preventive Measures: Implementing robust security protocols, regularly updating software, and using encryption can help prevent attacks.
o Cybersecurity Awareness: Education is a powerful defense. Individuals and organizations must stay informed about the latest threats, practice safe online behaviors, and undergo regular cybersecurity training.
o Strong Authentication and Access Controls: Implementing robust authentication methods and strict access controls helps prevent unauthorized access to systems and data.
o Regular Software Updates: Keeping software, operating systems, and security applications up-to-date is crucial to patch vulnerabilities that could be exploited by attackers.
o Incident Response Plans: Having a well-defined incident response plan enables organizations to react promptly and effectively when a cyber-attack occurs. This minimizes potential damage and recovery time.
o Detection and Response: Organizations need advanced threat detection and response strategies to identify and mitigate attacks swiftly.
o Collaboration: Sharing information about threats and defenses among businesses, governments, and security professionals is crucial for enhancing collective security.
vii. Conclusion

Despite the growing sophistication of cybersecurity measures, the dynamic nature of cyber-attacks means that the threat landscape is constantly changing.
In conclusion, understanding the intricacies of cyber-attacks empowers individuals and organizations to bolster their defenses. As technology advances, so do the tactics of cybercriminals, making ongoing education and proactive cybersecurity measures essential in the ever-evolving landscape of digital threats.
The cybersecurity arena is a battlefield of innovation, where defenses are continuously adapted in response to new threats, ensuring the digital world remains a step ahead of malicious actors.
viii. Further references
Forbeshttps://www.forbes.com › businessWhat Is A Cyber Attack? Definition, Types & Prevention
CrowdStrike.comwww.crowdstrike.com10 Most Common Types of Cyber Attacks Today
UpGuardwww.upguard.comWhat is a Cyber Attack? Common Attack Techniques and Targets
Aurahttps://www.aura.com › learn › type…17 Most Common Types of Cyber Attacks & Examples (2024)
Prey Projectpreyproject.comMastering Modern Cybersecurity Threats: Your Essential Guide | Prey Blog
Sophoshttps://www.sophos.com › en-us › t…Threat Actors Explained: Motivations and Capabilities
ResearchGatehttps://www.researchgate.net › 3490…(PDF) What are Cyber-Threats, Cyber-Attacks …