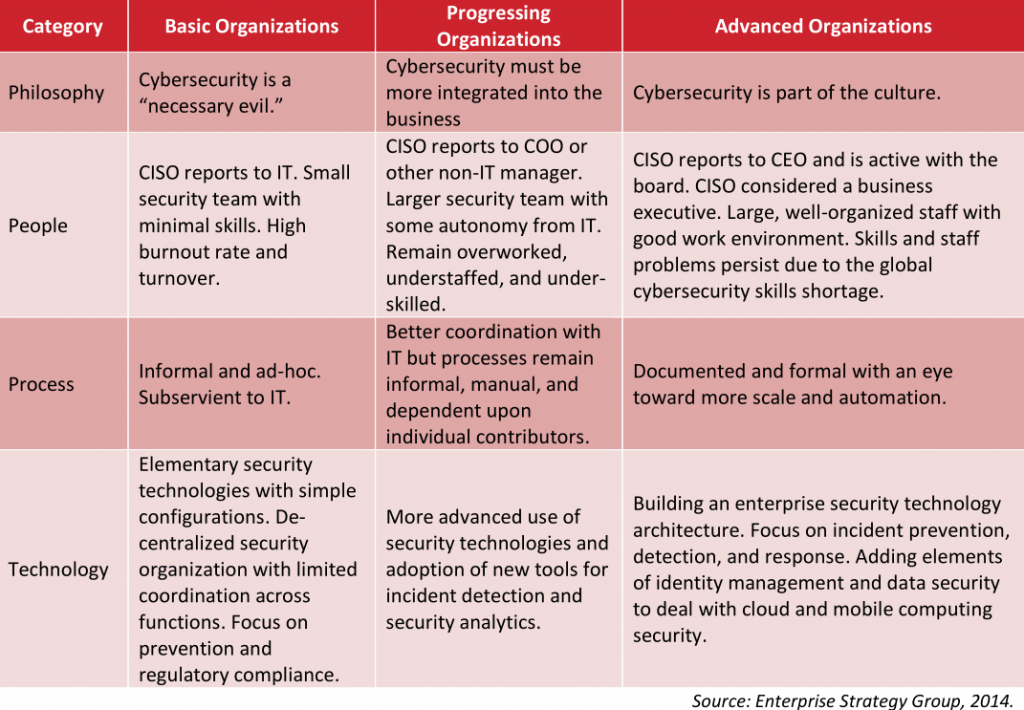
The Payoff of Protection: How Cybersecurity Maturity Impacts Business Outcomes
In today’s digital age, cybersecurity is no longer just an IT issue; it has become a critical business concern that can significantly impact an organization’s success and longevity. As cyber threats continue to evolve in sophistication and frequency, businesses must elevate their cybersecurity posture to protect their assets, reputation, and bottom line. This article explores the impact of cybersecurity maturity on business outcomes and why investing in robust cybersecurity measures is essential for sustainable success.
i. Understanding Cybersecurity Maturity
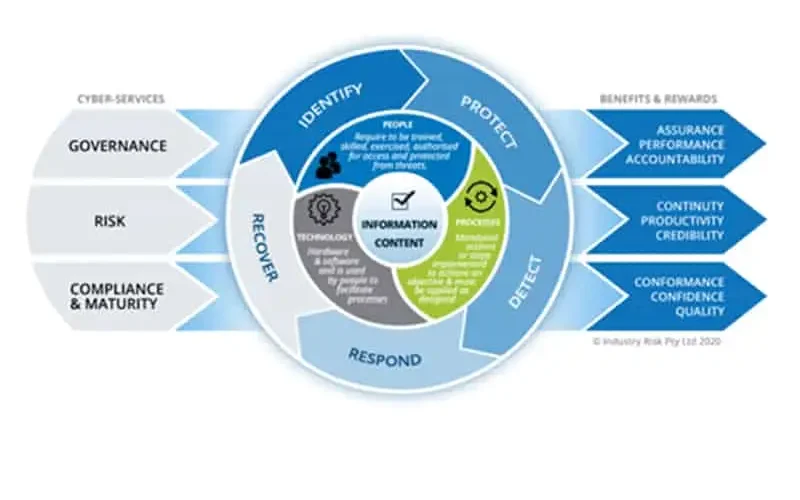
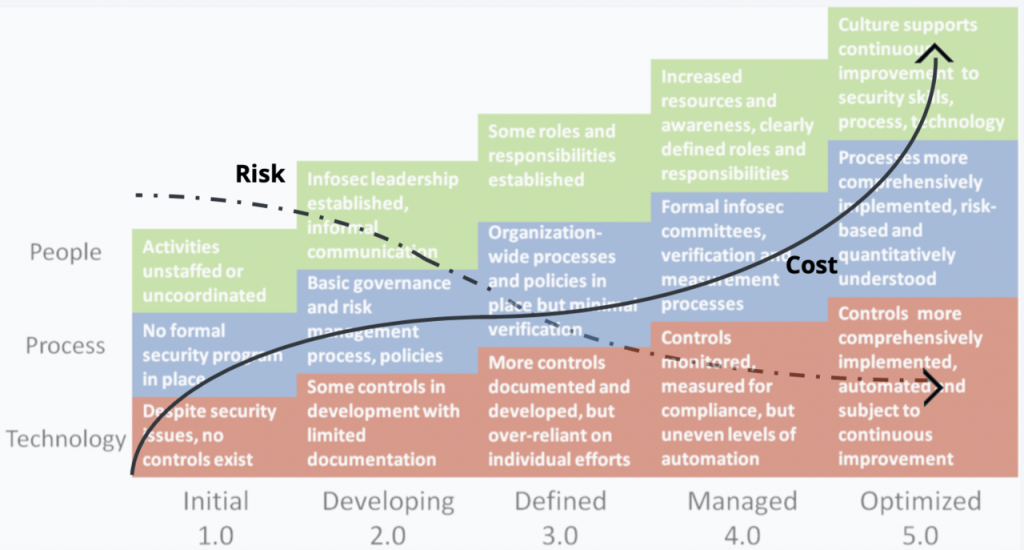
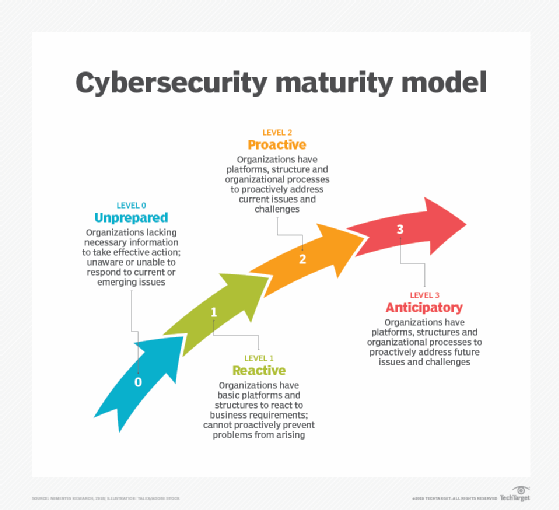
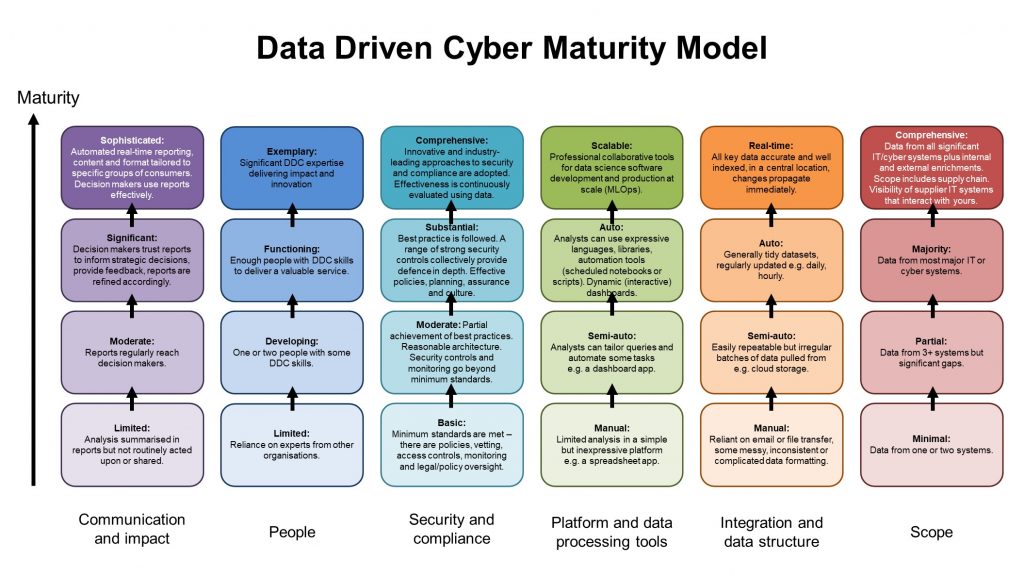
Cybersecurity maturity refers to the extent to which an organization has developed and implemented comprehensive cybersecurity policies, procedures, and controls. It is typically assessed using maturity models that evaluate various aspects of an organization’s cybersecurity practices, including risk management, incident response, compliance, and employee training. These models often classify maturity into different levels, ranging from initial (ad-hoc and reactive) to optimized (proactive and fully integrated).
Cybersecurity maturity can be measured using various frameworks, with the Capability Maturity Model (CMM) and the NIST Cybersecurity Framework being among the most widely recognized. These frameworks assess an organization’s cyber defenses from initial (ad hoc and reactive) to optimized (proactive and predictive) levels.
ii. Levels of Cybersecurity Maturity
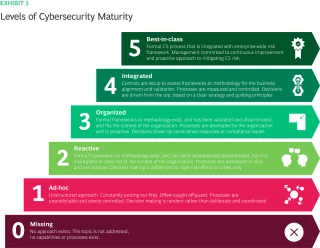
- Initial (Ad Hoc)
- Practices are unstructured and undocumented.
- Security measures are reactive and improvised.
- Repeatable (Managed)
- Basic policies and procedures are in place.
- Security is more consistent but still largely reactive.
- Defined (Established)
- Security practices are standardized and documented.
- There is a formalization of policies and onboarding processes.
- Managed and Measurable
- Security measures are routinely tested and measured.
- There is proactive identification and mitigation of risks.
- Optimized
- Continuous improvement practices are in place.
- Cyber threats are anticipated and mitigated in advance.
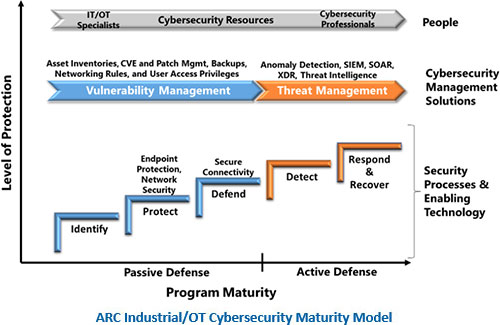
iii. The Impact on Business Outcomes

1. Enhanced Reputation and Customer Trust
A data breach can be a public relations nightmare, eroding customer trust and damaging your brand reputation. A mature cybersecurity posture demonstrates your commitment to protecting customer data, fostering trust and loyalty. This can translate into increased customer satisfaction, positive word-of-mouth marketing, and a competitive edge in attracting new customers.
2. Enhanced Risk Management
Organizations with a high level of cybersecurity maturity can better identify, assess, and mitigate risks. By proactively managing vulnerabilities and threats, they reduce the likelihood of successful cyber attacks. This capability not only protects critical assets but also ensures business continuity and resilience. Effective risk management translates into fewer disruptions, which is crucial for maintaining operational efficiency and achieving strategic objectives.
3. Improved Compliance and Regulatory Adherence
Cybersecurity maturity ensures that an organization complies with relevant laws, regulations, and industry standards. Non-compliance can result in hefty fines, legal penalties, and damage to reputation. By adhering to cybersecurity regulations such as GDPR, HIPAA, and ISO/IEC 27001, businesses can avoid these consequences and build trust with customers, partners, and stakeholders.
4. Increased Customer Trust and Loyalty
Consumers are increasingly concerned about the security of their personal and financial information. Organizations that demonstrate a high level of cybersecurity maturity can assure customers that their data is protected. This assurance builds trust and fosters loyalty, which can lead to increased customer retention and positive word-of-mouth referrals. In contrast, data breaches can erode trust and drive customers away.
5. Improved Investor Confidence and Access to Capital
Investors are increasingly scrutinizing a company’s cybersecurity practices. A mature cybersecurity posture demonstrates your commitment to protecting shareholder value and managing risk. This can position your organization more favorably with investors, potentially leading to easier access to capital for future growth initiatives.
6. Improved Operational Efficiency and Productivity
Cyberattacks can disrupt operations, leading to downtime, lost productivity, and financial setbacks. By implementing robust security measures, you can minimize these disruptions, allowing your team to focus on core business activities.Additionally, automation and streamlined security processes within a mature cybersecurity strategy can further improve operational efficiency.
7. Financial Performance and Cost Savings
Investing in cybersecurity may seem like a significant expense, but it can lead to substantial cost savings in the long run. Mature cybersecurity practices help prevent costly data breaches, ransomware attacks, and other cyber incidents that can result in financial losses, legal fees, and reputational damage. Additionally, insurers may offer lower premiums to organizations with robust cybersecurity measures in place, further reducing costs.
8. Competitive Advantage
Organizations that prioritize cybersecurity can differentiate themselves from competitors. Demonstrating a strong cybersecurity posture can be a unique selling point, especially in industries where data security is paramount. Companies that are perceived as secure and trustworthy are more likely to attract and retain customers, partners, and investors.
9. Innovation and Agility
Cybersecurity maturity enables organizations to adopt new technologies and innovate with confidence. With robust security measures in place, businesses can explore digital transformation initiatives such as cloud computing, IoT, and AI without exposing themselves to undue risk. This agility allows them to stay ahead of the curve and respond quickly to market changes and opportunities.
10. Employee Productivity and Morale
A mature cybersecurity environment also impacts employees. When cybersecurity measures are well-implemented and user-friendly, employees can perform their duties without frequent interruptions or fear of security breaches. Training programs that educate staff on cybersecurity best practices empower them to contribute to the organization’s security efforts. This environment fosters a culture of security awareness and responsibility, boosting overall morale and productivity.
iv. Challenges to Achieving Cybersecurity Maturity
While the benefits of high cybersecurity maturity are clear, achieving it is fraught with challenges. These include:
- Resource Constraints: Investments in sophisticated tools and skilled personnel are often costly.
- Evolving Threat Landscape: Cyber threats are constantly evolving, requiring continuous updates and adaptability.
- Complexity of Integration: Merging cybersecurity practices with existing business processes without disrupting operations can be complex.
- Cultural Barriers: Achieving cybersecurity maturity requires a cultural shift towards prioritizing security across all levels of the organization.
v. The Road to Maturity: Building a Robust Cybersecurity Strategy
To achieve a high level of cybersecurity maturity, organizations should:
- Conduct Regular Assessments: Evaluate current cybersecurity practices and identify gaps using maturity models. Regular assessments help track progress and guide improvements.
- Develop Comprehensive Policies and Procedures: Establish clear, documented cybersecurity policies and procedures that align with industry standards and regulatory requirements.
- Implement a layered security approach: This includes a combination of firewalls, intrusion detection systems, data encryption, and employee training.
- Develop a comprehensive incident response plan: Be prepared to respond quickly and effectively to cyberattacks.
- Invest in employee cybersecurity awareness training: Empower your team to identify and report suspicious activity.
- Implement Advanced Technologies: Leverage advanced cybersecurity technologies such as AI-driven threat detection, multi-factor authentication, and encryption to enhance security.
- Engage with Experts: Partner with cybersecurity experts and consultants to gain insights and support in strengthening your security posture.
- Foster a Culture of Security: Encourage a culture where cybersecurity is everyone’s responsibility. Promote open communication about security issues and celebrate successes.
vi. Conclusion
The impact of cybersecurity maturity on business outcomes is profound and multifaceted. From enhanced risk management and regulatory compliance to improved financial performance and competitive advantage, cybersecurity maturity plays a pivotal role in modern business success. However, achieving and maintaining a high level of cybersecurity maturity requires continuous effort, investment, and a commitment to integrating security into the core ethos of the organization.
By understanding the various dimensions of cybersecurity maturity and striving towards optimization, businesses cannot only protect themselves against cyber threats but also position themselves as leaders in their respective markets. Ultimately, cybersecurity maturity is not merely a technological challenge but a strategic imperative for sustaining business growth and resilience in the digital age.
vii. Further references
Cybersecurity Maturity: Gaps and Solutions | White Paper | ISACAisaca.orghttps://www.isaca.org
Cyber: An Enabler of Business Outcomes – WSJWSJhttps://deloitte.wsj.com › … › CYBERSECURITY
Building a Strong Foundation: Understanding …Kobalt.iohttps://kobalt.io › Blog
