
Privacy Enhancing Cryptography (PEC): Zero Knowledge Proofs – A Revolutionary Leap
In the digital age, privacy and security are paramount. With every byte of data transmitted across the internet, there’s a risk of exposure and misuse.
However, a groundbreaking concept within Privacy Enhancing Cryptography (PEC), known as Zero Knowledge Proofs (ZKP), is setting new standards for secure and private online interactions.
Let’s delve into the fascinating world of ZKP and its role in bolstering digital privacy.
i. Understanding Zero Knowledge Proofs (ZKPs)

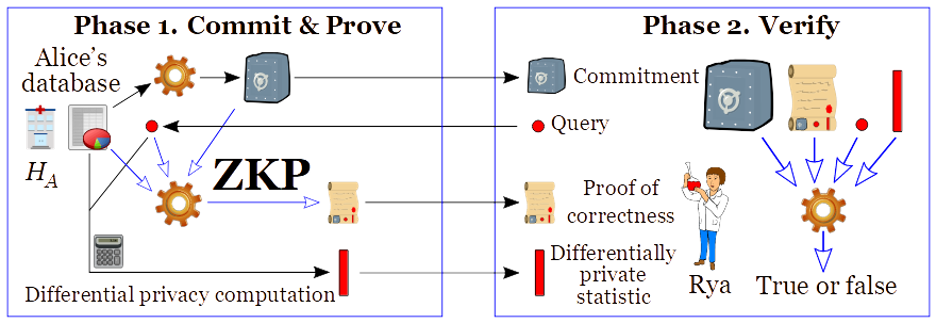
Zero Knowledge Proofs are cryptographic protocols that allow one party, the prover, to demonstrate the validity of a statement to another party, the verifier, without revealing any information beyond the validity of the statement itself.
In simpler terms, ZKPs enable one party to prove knowledge of a secret without revealing the secret itself.
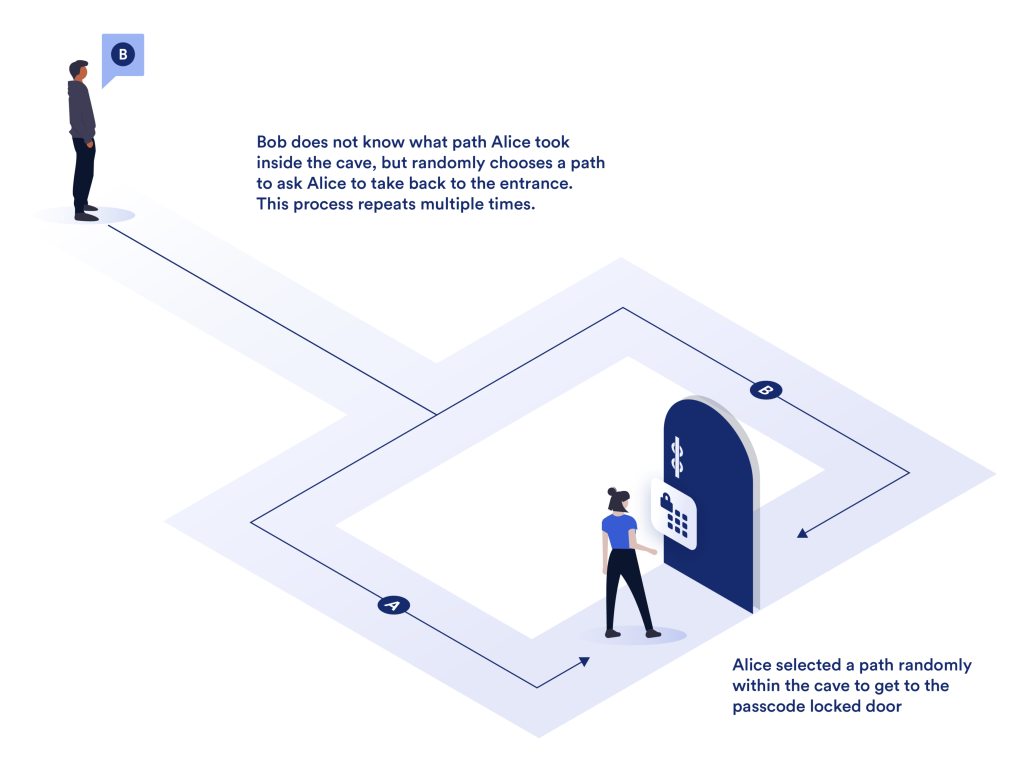
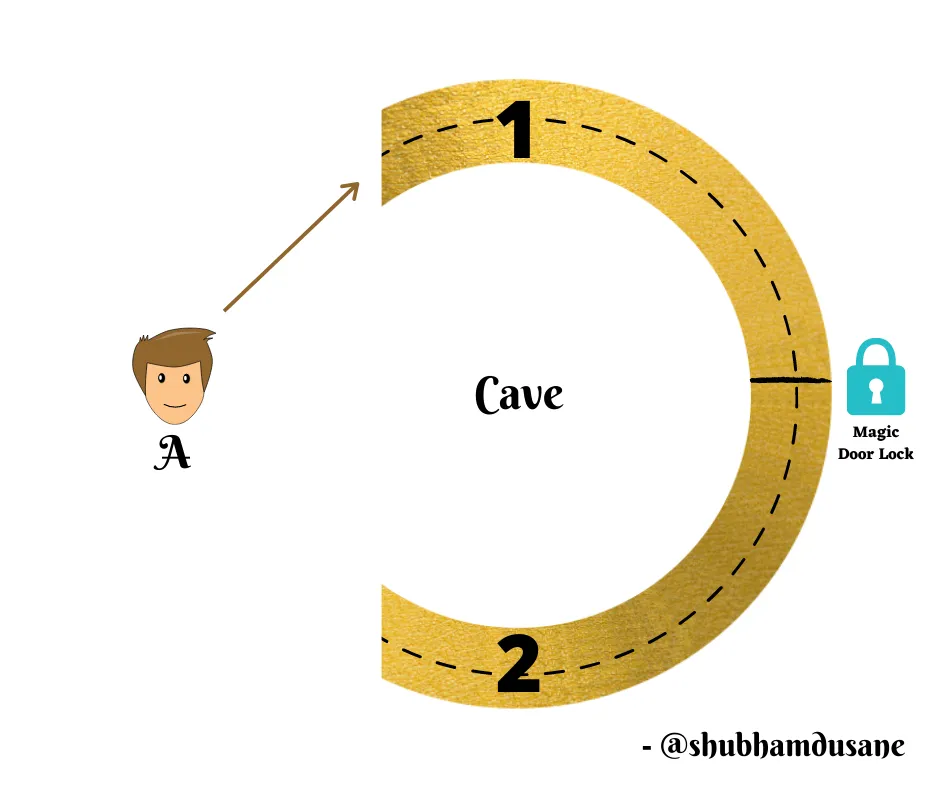
Imagine Alice wants to prove to Bob that she knows the solution to a complex mathematical problem without actually revealing the solution. With Zero Knowledge Proofs, Alice can convince Bob of her knowledge without disclosing any information about the solution other than its correctness.
ii. Origins and Evolution

The roots of Zero Knowledge Proofs trace back to the 1980s, stemming from the research of MIT professors Shafi Goldwasser, Silvio Micali, and Charles Rackoff. Their pioneering work laid the foundation for this privacy-centric approach to proving statements without divulging the information contained in those statements.
iii. Here are some key points about ZKPs:

o Privacy-Preserving: ZKPs ensure that only the validity of the statement is conveyed, keeping all other details confidential.
o Diverse Applications: ZKPs have a wide range of applications, from age verification and digital signatures to secure electronic voting and anonymous credentials.
o Continuously Evolving: The field of ZKPs is constantly advancing, with new and more efficient protocols being developed all the time.
iv. How Zero Knowledge Proofs Work
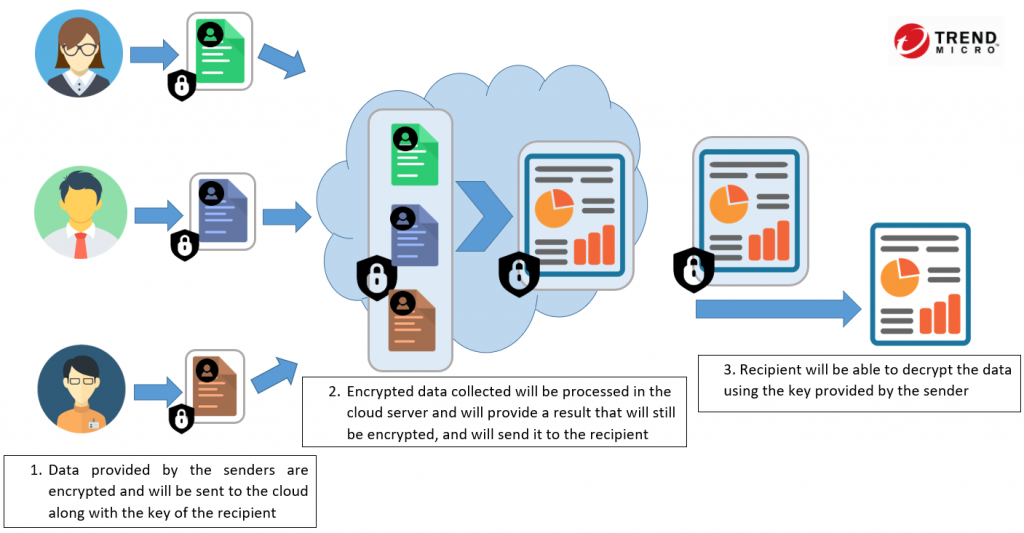
Zero Knowledge Proofs rely on three fundamental properties:
A. Completeness: If the statement is true, an honest verifier will be convinced of its truth by an honest prover.
B. Soundness: If the statement is false, no dishonest prover can convince an honest verifier that it is true, except with negligible probability.
C. Zero-Knowledge: The verifier learns nothing about the secret other than its validity.
To achieve these properties, ZKPs employ sophisticated cryptographic techniques such as commitment schemes, hash functions, and mathematical constructs like elliptic curves and lattice-based cryptography.
v. How ZKP Empowers Privacy

Zero Knowledge Proofs serve as a crucial tool in the expansion of privacy enhancing technologies for several reasons:
o Data Minimization: By proving knowledge of a fact without revealing the fact itself, ZKP adheres to the principle of data minimization, a key aspect of privacy regulations like GDPR.
o Enhanced Security: ZKP mechanisms reduce the amount of data exchanged during cryptographic operations, minimizing the attack surface for malicious entities.
o Versatility: The applications of ZKP range from secure authentication systems without passwords to confidential transactions on blockchain networks, showcasing its versatility.
vi. Applications of Zero Knowledge Proofs
The potential applications for Zero Knowledge Proofs are wide-ranging and transformative across various sectors.
A. Secure Authentication
ZKP enables the creation of authentication systems where users can prove their identity without revealing passwords or other sensitive information, significantly reducing the risk of data breaches.
B. Blockchain and Cryptocurrencies
In the realm of blockchain and cryptocurrencies, ZKP offers a means to conduct transactions with complete privacy, ensuring that details such as the transaction amount and participants’ identities remain confidential.
C. Voting Systems
Zero Knowledge Proofs can facilitate secure and anonymous voting systems, assuring the integrity of the vote while protecting voters’ privacy. This application holds promise for enhancing democratic processes around the world.
D. Digital Identity

Zero Knowledge Proofs offer a promising solution to the challenge of digital identity verification. Individuals can prove their identity without revealing unnecessary personal information, thus minimizing the risk of identity theft and privacy breaches.
vii. Challenges and Future Directions
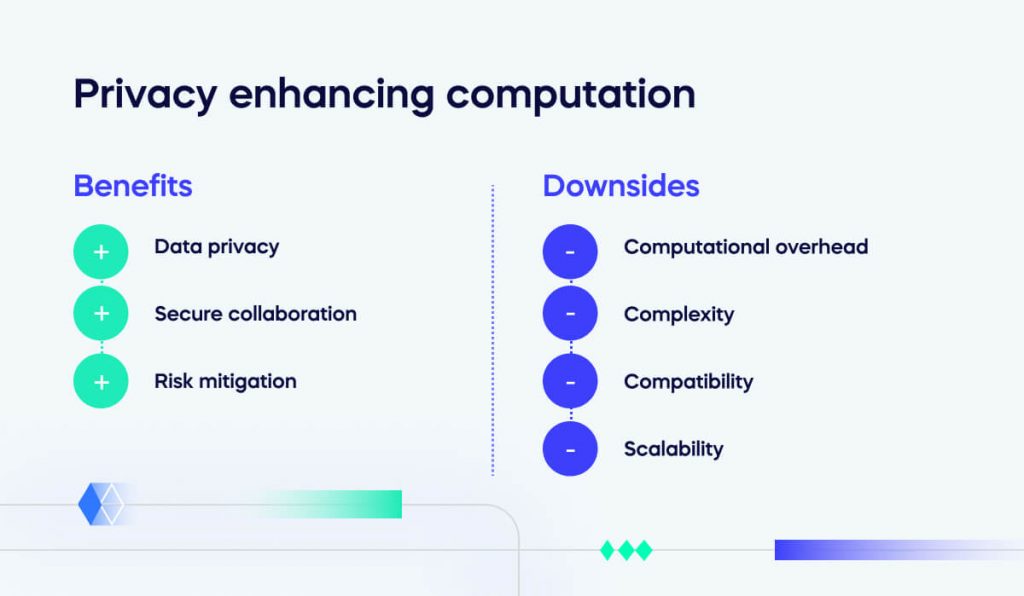
Despite its numerous advantages, the widespread adoption of Zero Knowledge Proofs faces several challenges, including computational complexity and the need for further research into scalable and efficient implementations.
However, the ongoing advancements in cryptographic research and the increasing importance of privacy in the digital domain signify a promising future for ZKP.
Innovations in succinct non-interactive zero-knowledge proofs (zk-SNARKs) and zero-knowledge rollups (zk-Rollups) are addressing scalability and computation challenges, paving the way for wider adoption.
viii. Conclusion

Zero Knowledge Proofs stand at the forefront of privacy enhancing cryptography, offering a powerful tool for secure and private digital interactions.
As our world becomes increasingly digitized, the importance of technologies like ZKP in protecting individual privacy and security cannot be overstated.
The journey of Zero Knowledge Proofs is still unfolding, and its full potential is yet to be realized, marking an exciting chapter in the evolution of cryptography.
ix. Further references
csrc.nist.riphttps://csrc.nist.rip › Projects › Pri…Privacy-Enhancing Cryptography PEC – CSRC
Archive ouverte HALhttps://hal.science › documentPDFArtificial Intelligence and Quantum Cryptography
ResearchGatehttps://www.researchgate.net › 376…(PDF) Recent Developments in Cyber security
