CyBOK (Cyber Security Body of Knowledge) is a comprehensive framework that aims to define the core areas of knowledge within the field of cybersecurity.
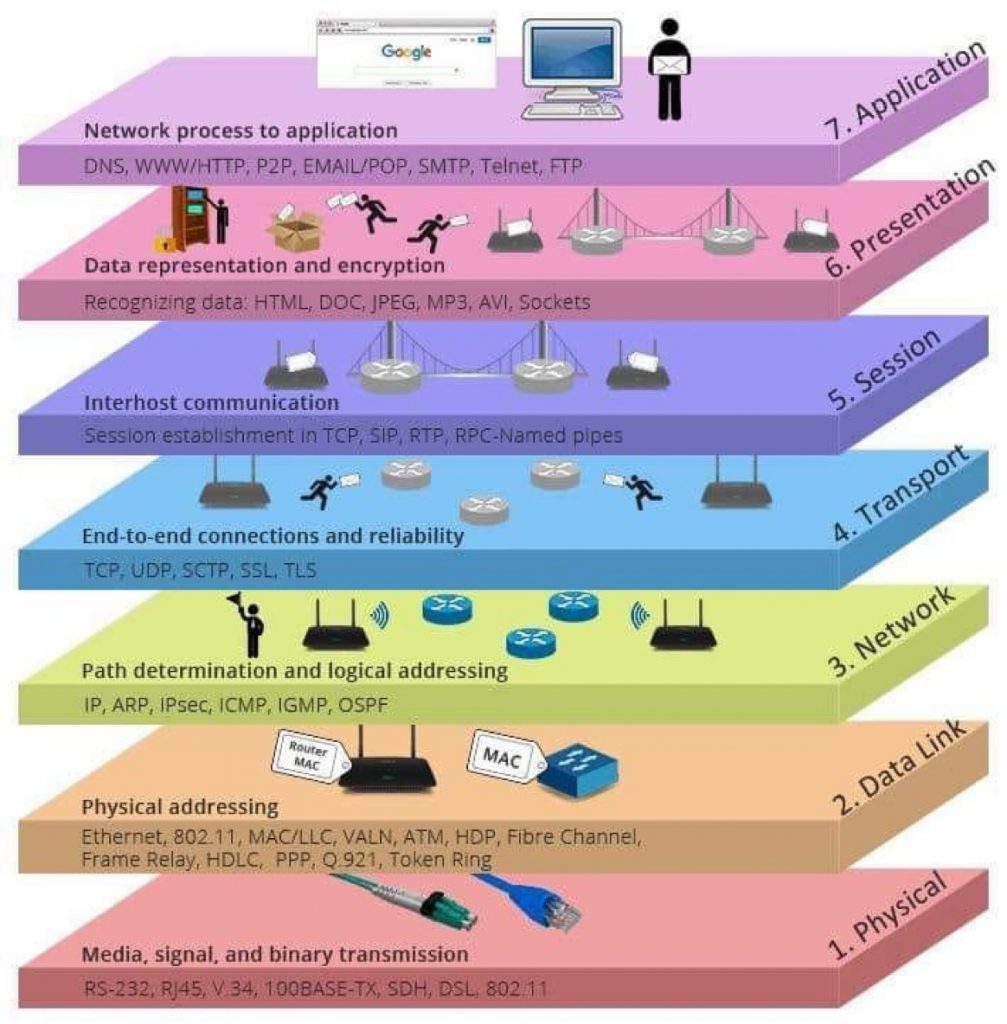
One of the knowledge areas within CyBOK is the “Physical Layer & Telecommunications Security” knowledge area. This area focuses on understanding and protecting the physical infrastructure and communication channels that underpin information systems.
The physical layer relates to the tangible components of information systems, such as physical devices, hardware, and the network infrastructure. Telecommunications security, on the other hand, specifically deals with securing the communication channels used to transmit data between devices, systems, or networks.
i. Here’s a breakdown of the key topics covered in the KA:
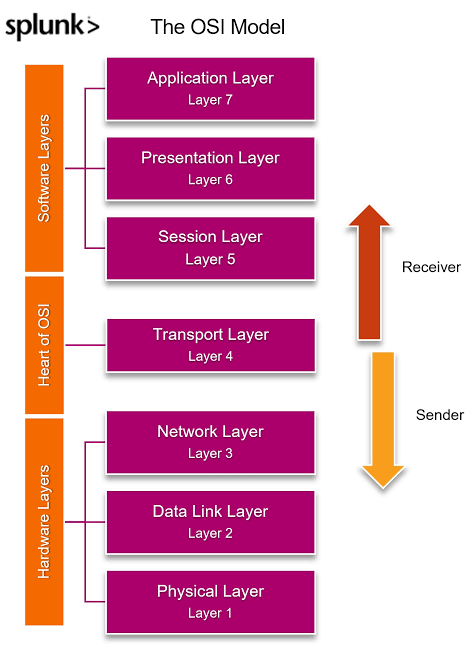
A. Physical Layer Concepts: Understanding the basics of how data is physically transmitted and received, including signal propagation, encoding, and modulation.
B. Physical Infrastructure Security: This includes securing data centers, server rooms, telecommunication facilities, and other physical components of information systems. It encompasses physical access controls, surveillance, perimeter security, and protection against environmental threats like fire, flood, or power interruptions.
C. Network Security: This covers securing the network infrastructure, including routers, switches, cabling, and other network devices. It addresses topics such as network segmentation, intrusion detection and prevention systems, secure configurations, and traffic monitoring.
D. Transmission Media Security: This focuses on securing the transmission media used for communication, such as wired (e.g., fiber optic, Ethernet) and wireless (e.g., Wi-Fi, cellular) channels. It involves measures to protect against eavesdropping, data interception, unauthorized access, electromagnetic interference, and signal jamming.
E. Telecommunications Protocols: This involves understanding and securing the protocols used for transmitting data, such as TCP/IP, Ethernet, Wi-Fi, Bluetooth, and cellular protocols. It includes topics like encryption, authentication, access control, and secure configuration of communication protocols.
F. Wireless Channel Characteristics:
o Understanding the fundamentals of electromagnetic waves and how they propagate through different mediums.
o Analyzing factors like multipath propagation, fading, and interference that impact wireless communication security.
o Exploring modulation techniques used in various wireless communication standards and their implications for security.
G. Wireless Physical Layer Security Mechanisms:
o Reviewing techniques for confidentiality like spread spectrum, frequency hopping, and encryption at the physical layer.
o Examining integrity mechanisms like cyclic redundancy checks (CRCs) and forward error correction (FEC) codes.
o Understanding access control mechanisms like carrier sense multiple access (CSMA) and media access control (MAC) protocols from a security perspective.

H. Physical Layer Vulnerabilities and Threats:
o Identifying common vulnerabilities in wireless communication systems, such as jamming, eavesdropping, and spoofing.
o Analyzing different categories of attacks that exploit physical layer vulnerabilities, including denial-of-service (DoS) attacks, replay attacks, and man-in-the-middle attacks.
o Understanding the risks associated with unintentional radio frequency (RF) emanations.
I. Physical Layer Countermeasures and Detection Techniques:
o Exploring techniques for mitigating threats and vulnerabilities at the physical layer, such as frequency agility, jamming resistance, and directional antennas.
o Discussing methods for detecting and monitoring suspicious activity at the physical layer, including spectrum analysis and intrusion detection systems (IDS).
o Reviewing methodologies for secure physical layer key establishment and authentication.
J. Emanation Security: Techniques like TEMPEST to prevent eavesdropping on electromagnetic emissions from electronic equipment.
K. Applications and Case Studies:
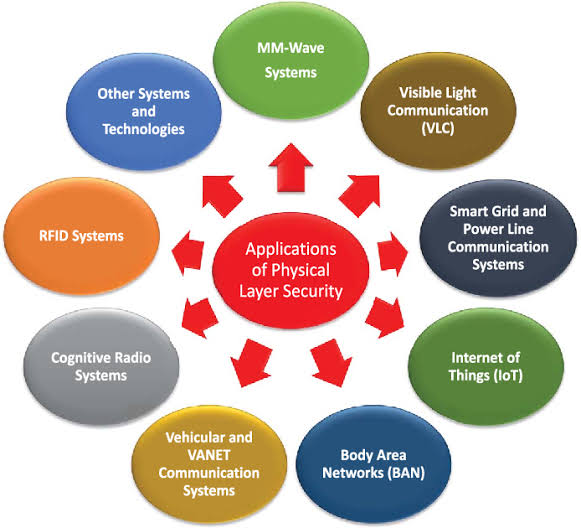
o Examining how physical layer security principles are applied in real-world scenarios, such as mobile networks, wireless sensor networks, and RFID systems.
o Analyzing case studies of successful and unsuccessful physical layer attacks to learn from past experiences.
o Exploring cutting-edge research and development in the field of physical layer security.
L. Cryptography: This area explores methods and techniques for securing data through encryption, decryption, and cryptographic algorithms. It includes studying symmetric and asymmetric encryption, key management, digital signatures, secure hash functions, and cryptographic protocols.
M. Telecommunications Service Providers: This covers the security considerations and requirements for telecommunications service providers. It involves understanding the security controls, service-level agreements, regulatory compliance, and secure interfaces between different service providers.
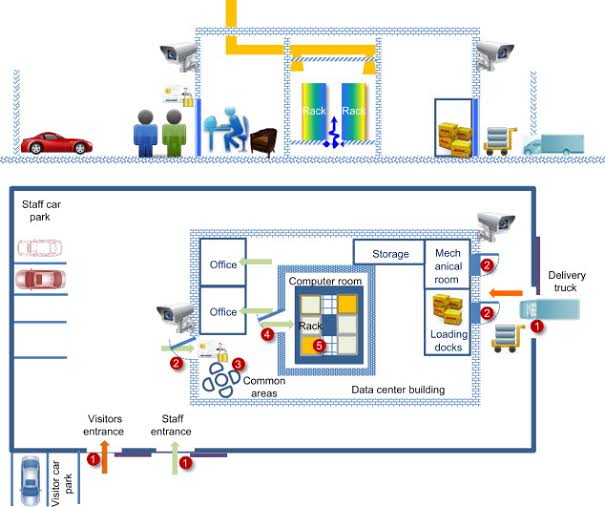
N. Access Control to Physical Resources: Securing access to physical infrastructure, network hubs, servers, and the implementation of measures like locks, biometric systems, and surveillance to safeguard equipment.
O. Telecommunications Infrastructure Security: Addressing the security concerns related to the infrastructure of telecommunications networks, such as cellular networks, satellites, and the Public Switched Telephone Network (PSTN).
P. Regulatory Standards and Best Practices: Understanding the compliance and legal aspects of physical security including industry standards and guidelines.
ii. Benefits of understanding the KA:
o Enhanced security posture: Grasping the vulnerabilities and threats at the physical layer enables organizations to develop stronger defenses against potential attacks.
o Improved wireless network security: Understanding secure physical layer mechanisms can guide the selection and implementation of secure wireless communication technologies.
o Greater awareness of emerging threats: Staying updated on the latest research and developments in physical layer security allows organizations to stay ahead of the curve and proactively mitigate new threats.
iii. Resources:
o The CyBOK website provides a wealth of resources for learning more about the KA, including:
o The FA Knowledge Product: A comprehensive overview of the FA content.
o The CyBOK Glossary: Definitions of key terms used in the FA.
o The CyBOK Training Catalog: Lists training courses that cover the FA content.
o Other valuable resources include academic papers, industry reports, and conferences focused on physical layer security.
For those working in or studying cybersecurity, knowledge of the physical layer is fundamental, as it is where data is most tangibly interfaced with and, hence, can be susceptible to a range of attacks that must be mitigated to ensure the security of an information system as a whole.
https://www.cybok.org/media/downloads/Physical_Layer__Telecommunications_Security_issue_1.0.pdf
https://www.sciencedirect.com/topics/computer-science/physical-layer-security
https://cs.slu.edu/~espositof/teaching/4530/resources/Physical-Layer-Security.pdf
