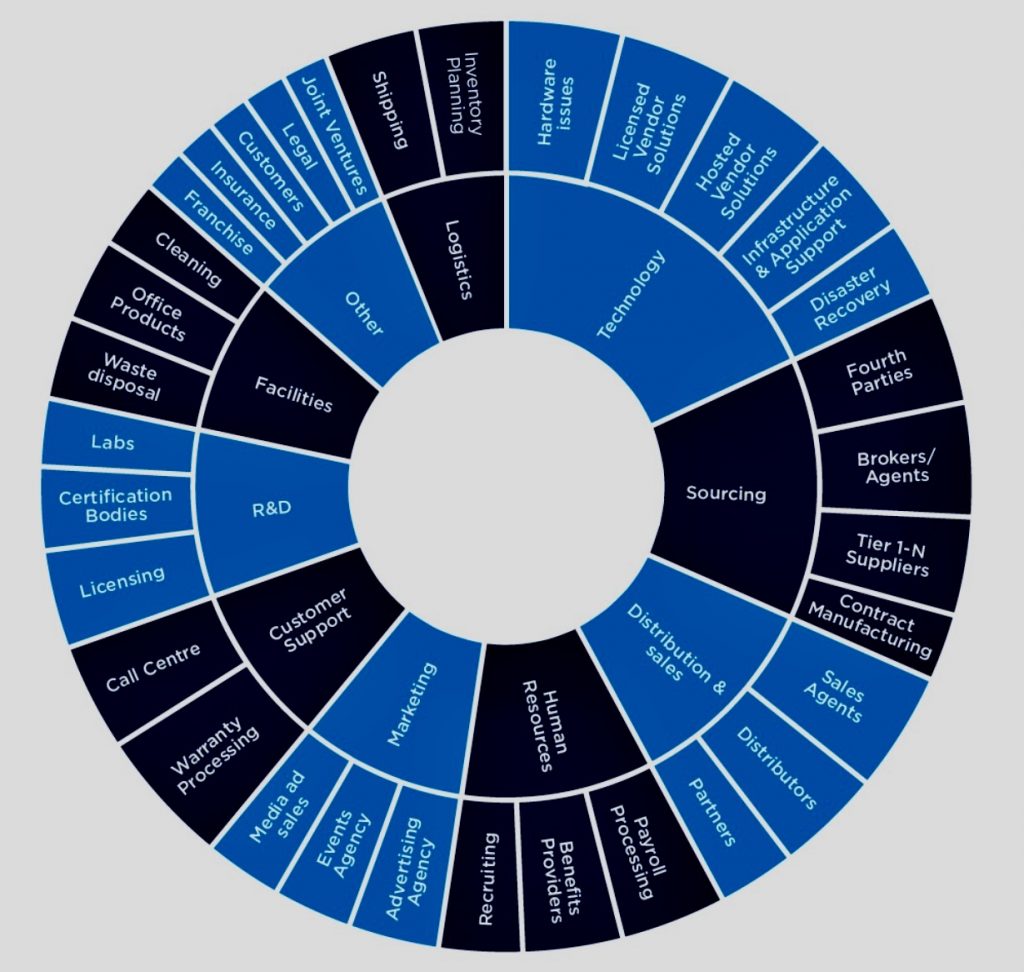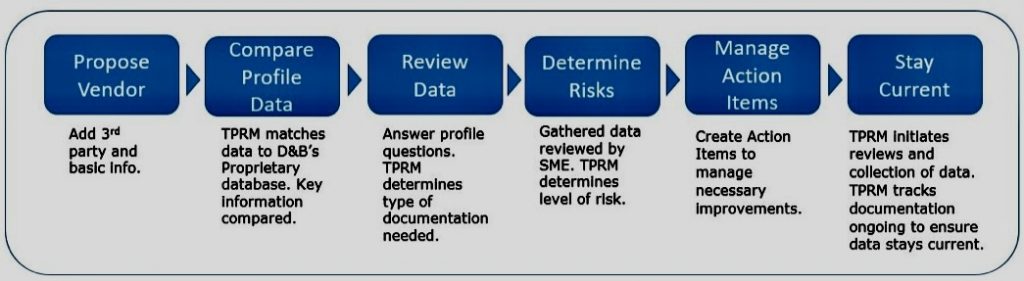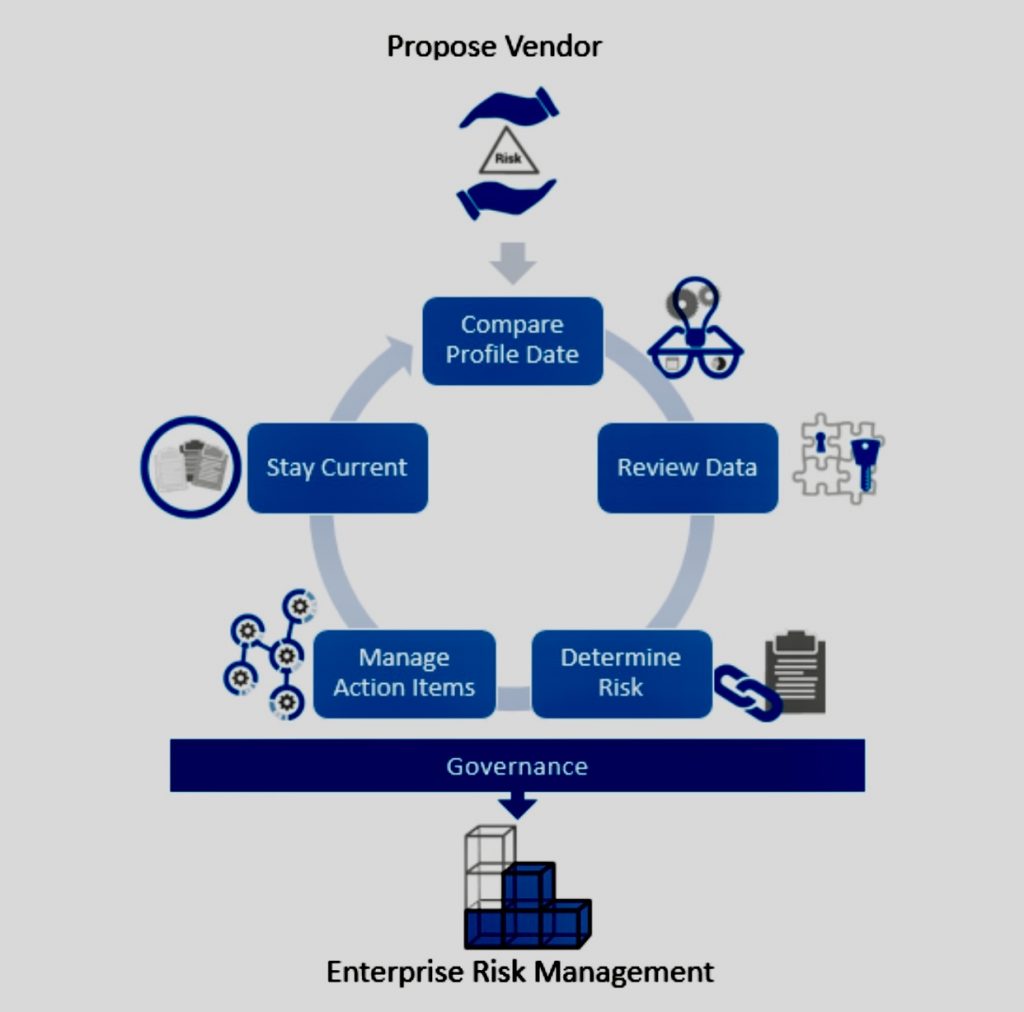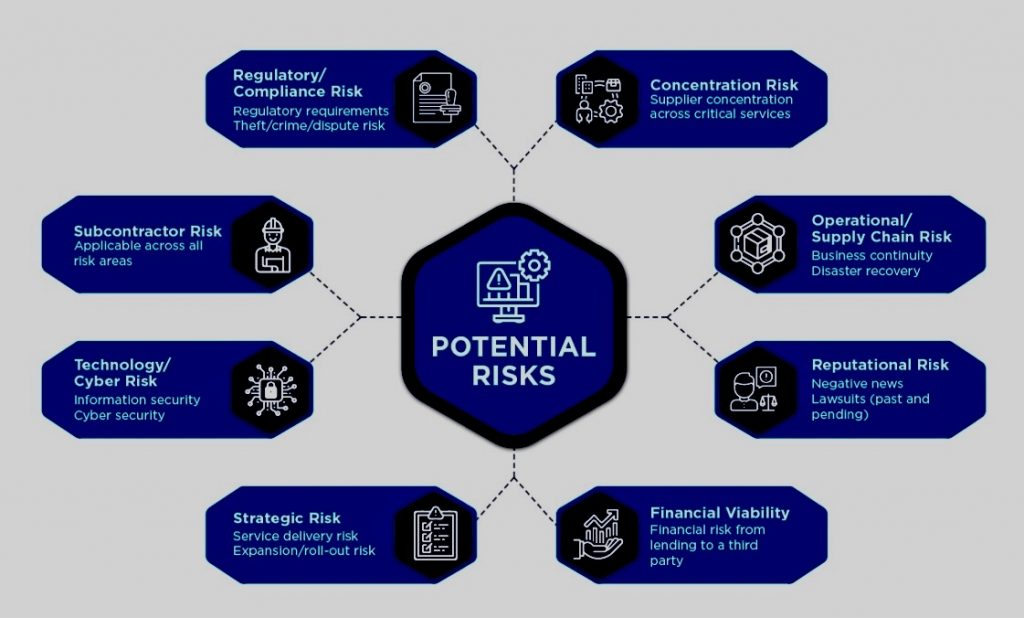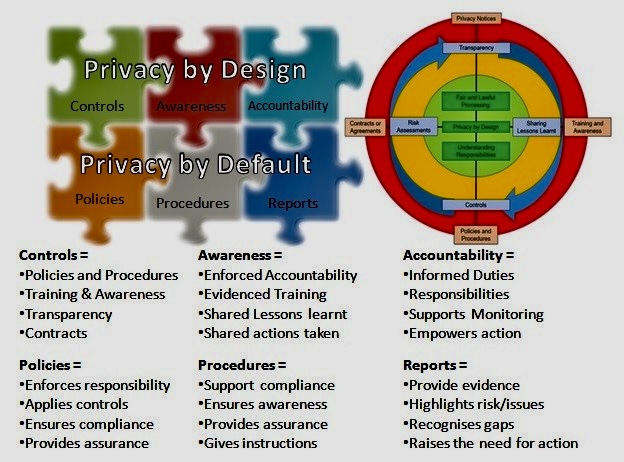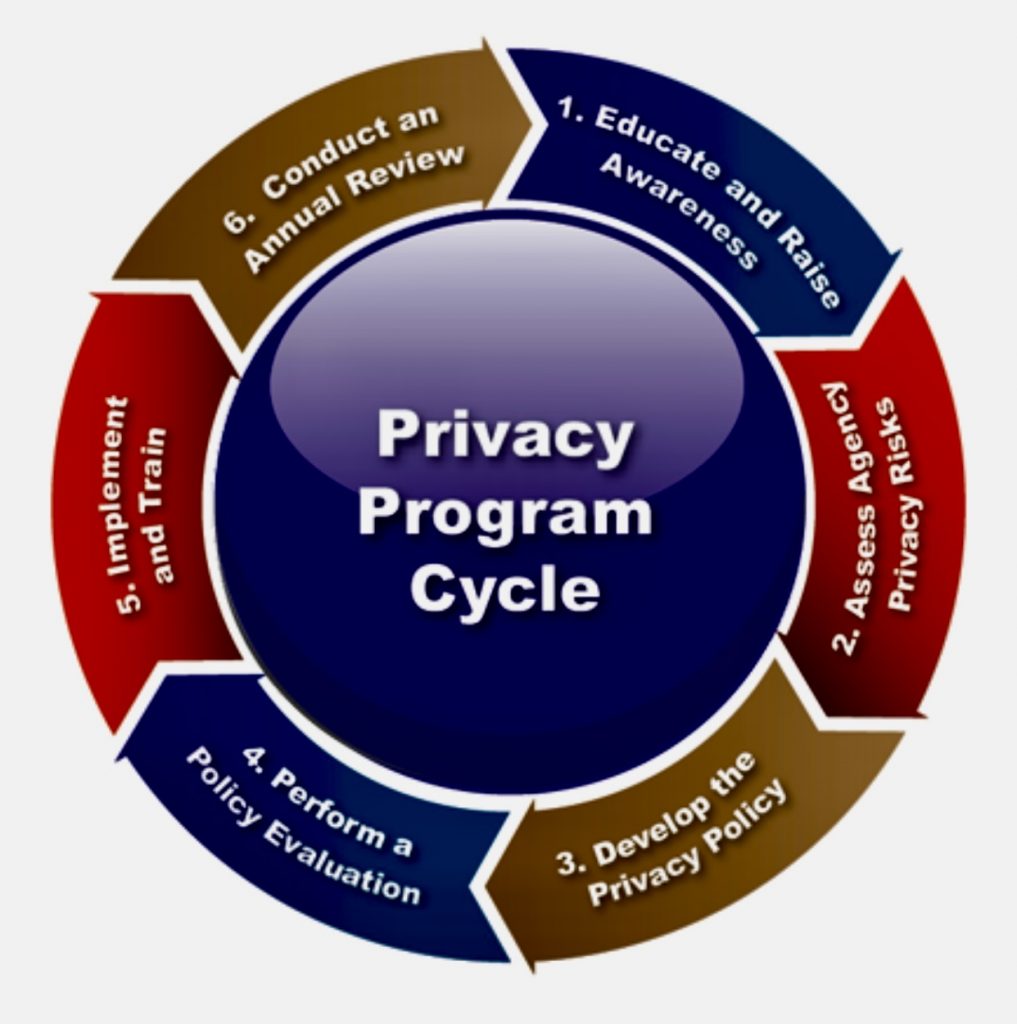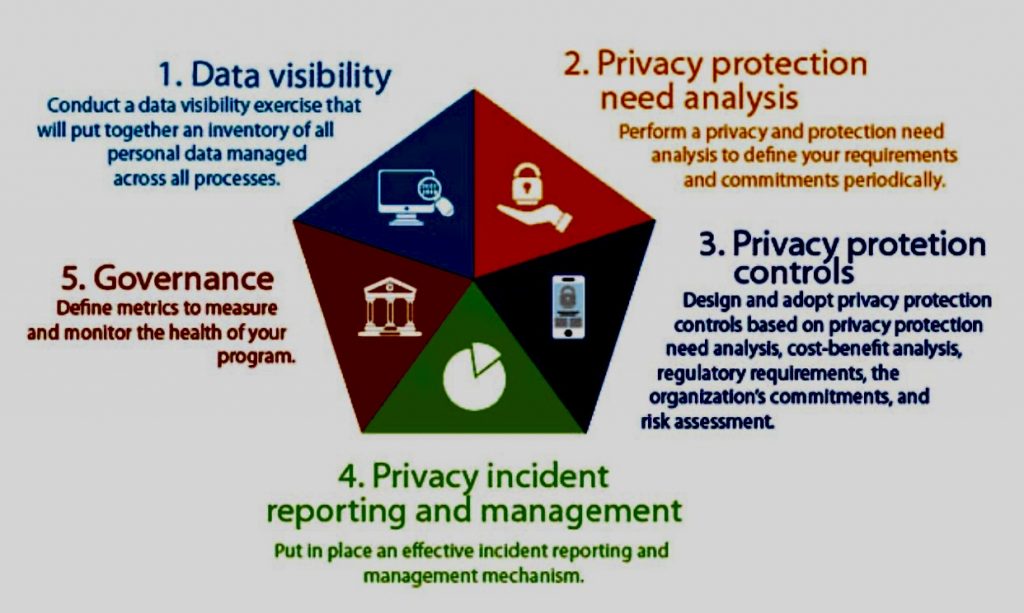
Identifying risk areas in GDPR compliance involves a systematic approach to understanding where personal data may be vulnerable and where an organization might not fully meet the requirements set out by the regulation. Here’s a step-by-step thought process to help identify these risk areas:
1. Understand the Scope of GDPR:
- Identify Personal Data: Determine what constitutes personal data within your organization. This includes any information that can directly or indirectly identify an individual (e.g., names, email addresses, IP addresses, etc.).
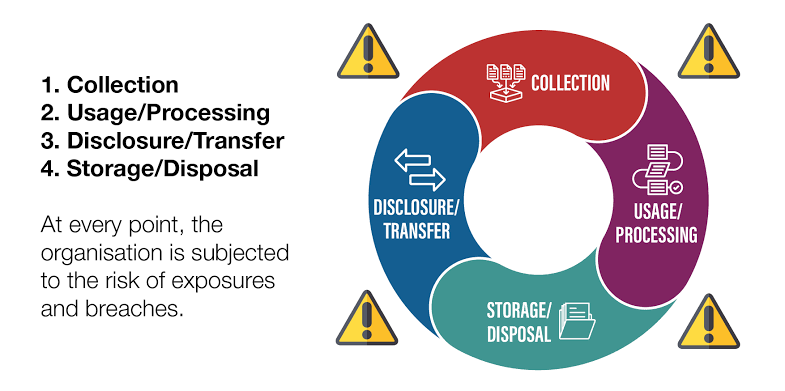
- Mapping Data Flows: Understand how personal data flows through your organization. Identify where data is collected, processed, stored, and transferred, both within and outside the organization.
2. Conduct a Data Inventory:
- Data Collection Points: Identify all points where personal data is collected, whether online (e.g., websites, apps) or offline (e.g., paper forms).
- Data Processing Activities: Document the various processes where personal data is used (e.g., customer relationship management, HR processes, marketing activities).
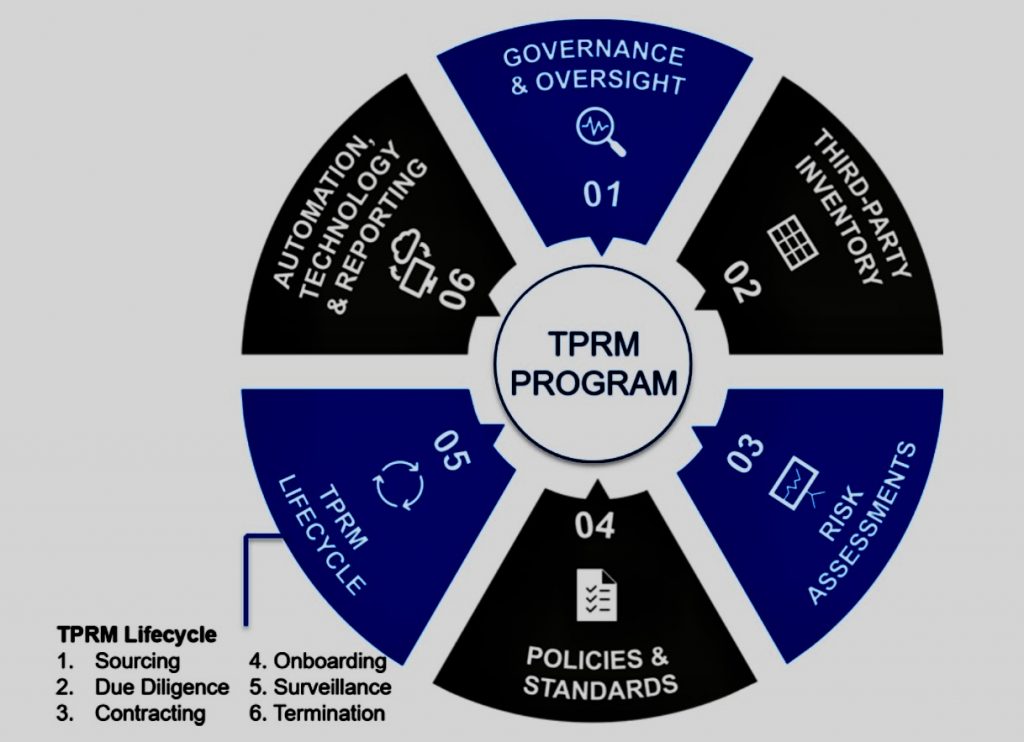
- Third-Party Relationships: Identify third parties (e.g., vendors, service providers) that have access to or process personal data on your behalf.
3. Assess Legal Basis for Data Processing:
- Review Consent Mechanisms: Ensure that consent is obtained in a GDPR-compliant manner, meaning it is freely given, specific, informed, and unambiguous.
- Alternative Legal Bases: For data processing activities not based on consent, ensure there is a valid legal basis (e.g., contract necessity, legitimate interest, legal obligation).
4. Evaluate Data Subject Rights:
- Access to Data: Check if you have mechanisms in place for data subjects to access their personal data.
- Rectification and Erasure: Ensure processes exist for correcting inaccurate data and fulfilling requests for data deletion (“right to be forgotten”).
- Portability and Restriction: Evaluate your ability to provide data portability and to restrict processing when requested by the data subject.
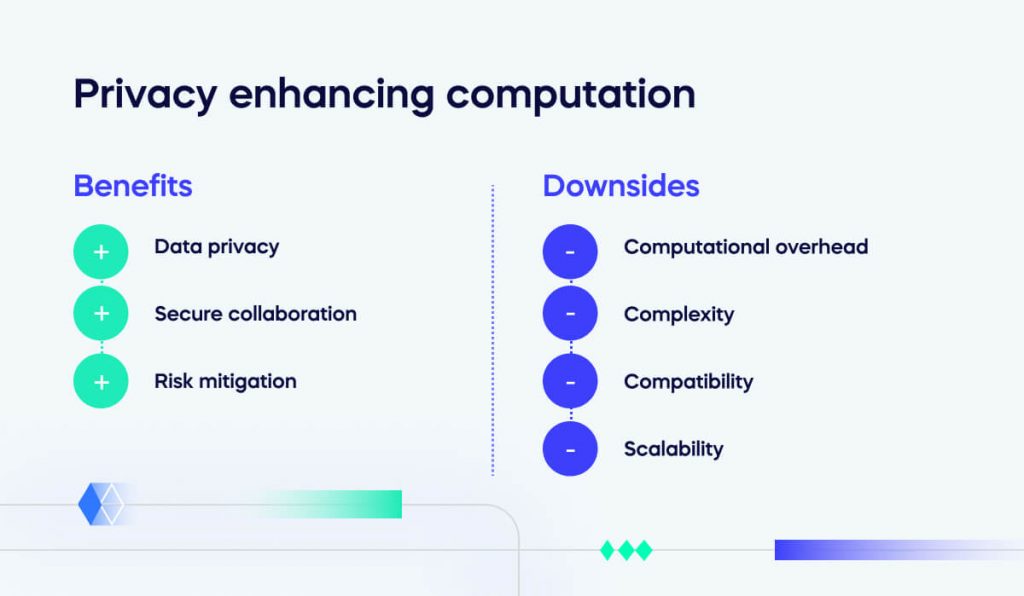
5. Review Data Security Measures:
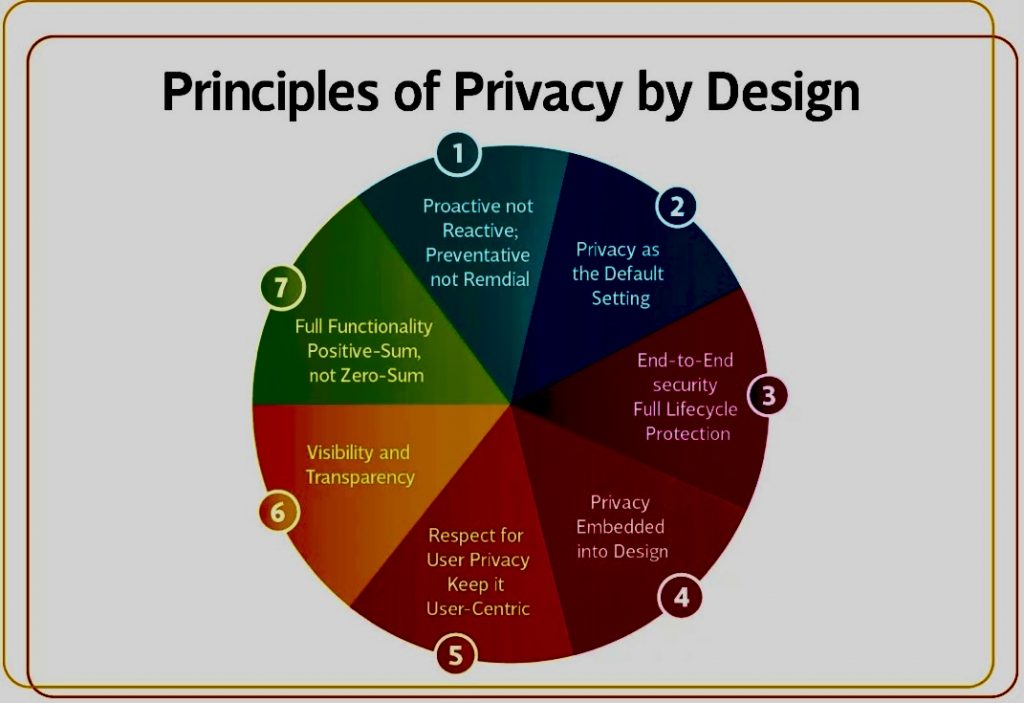
- Technical Safeguards: Assess whether your organization has adequate technical measures (e.g., encryption, access controls) to protect personal data.
- Organizational Measures: Ensure that policies, procedures, and training are in place to mitigate the risk of data breaches.
- Incident Response: Review your procedures for detecting, reporting, and responding to data breaches, ensuring they align with GDPR requirements (e.g., 72-hour notification window).
6. Evaluate Data Transfer Practices:
- International Data Transfers: Identify any transfers of personal data outside the EU/EEA. Ensure that appropriate safeguards are in place (e.g., Standard Contractual Clauses, Binding Corporate Rules).
- Data Localization Laws: Be aware of any local laws that may impact data transfers and ensure compliance with those as well.
7. Assess Data Retention and Minimization:
- Retention Policies: Review your data retention policies to ensure that personal data is kept no longer than necessary for the purposes for which it was collected.
- Data Minimization: Evaluate whether you are collecting and processing only the minimum amount of personal data necessary for your purposes.
8. Governance and Accountability:
- Data Protection Officer (DPO): Determine if your organization requires a DPO and ensure that the role is fulfilled by someone with the necessary expertise and independence.
- Record Keeping: Ensure that records of processing activities are maintained and can be provided upon request.
- GDPR Training: Evaluate whether employees, particularly those handling personal data, have received adequate training on GDPR requirements.
9. Monitor Regulatory Changes and Case Law:
- Stay Updated: Regularly review updates to GDPR guidelines, case law, and enforcement actions to identify new or evolving risk areas.
- Regulatory Engagement: Engage with Data Protection Authorities (DPAs) when necessary to clarify compliance expectations.
10. Conduct Regular Audits and Risk Assessments:
- Internal Audits: Regularly audit your GDPR compliance processes to identify gaps or areas of improvement.
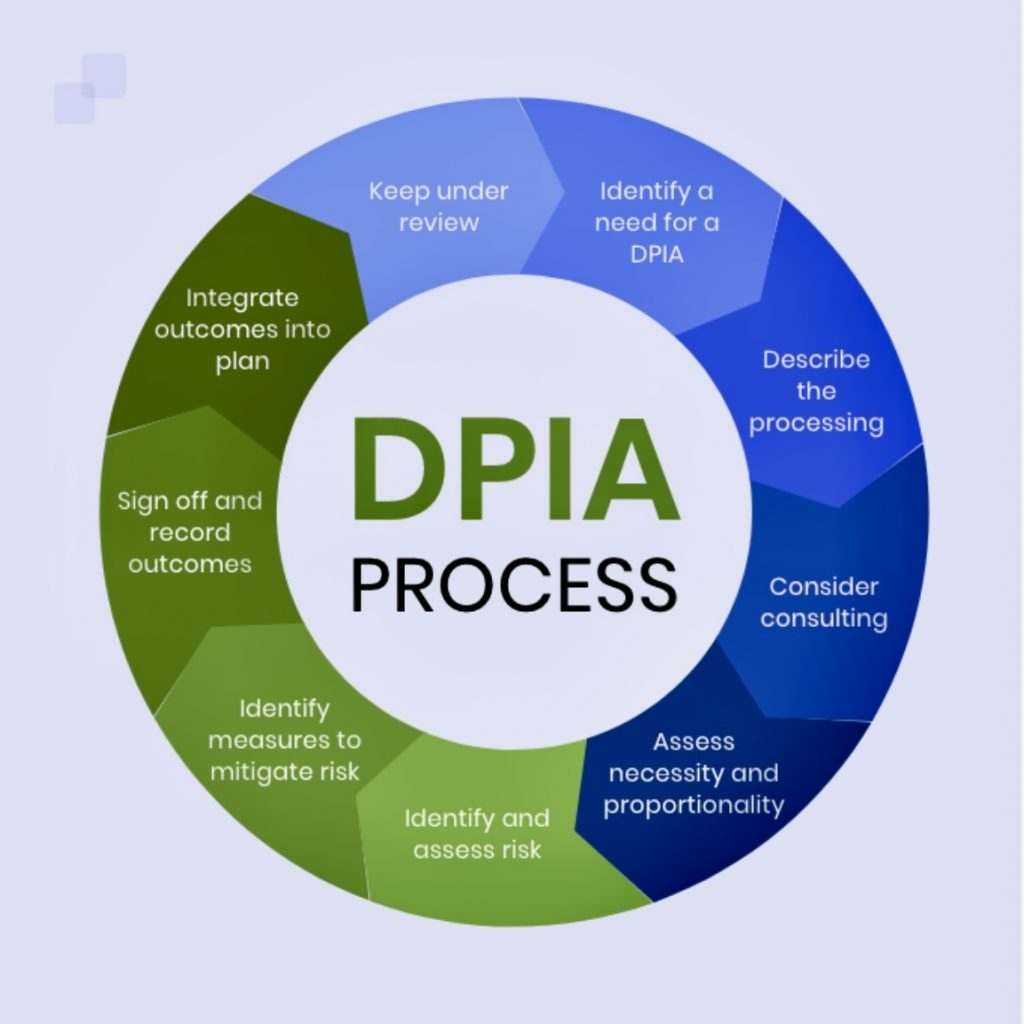
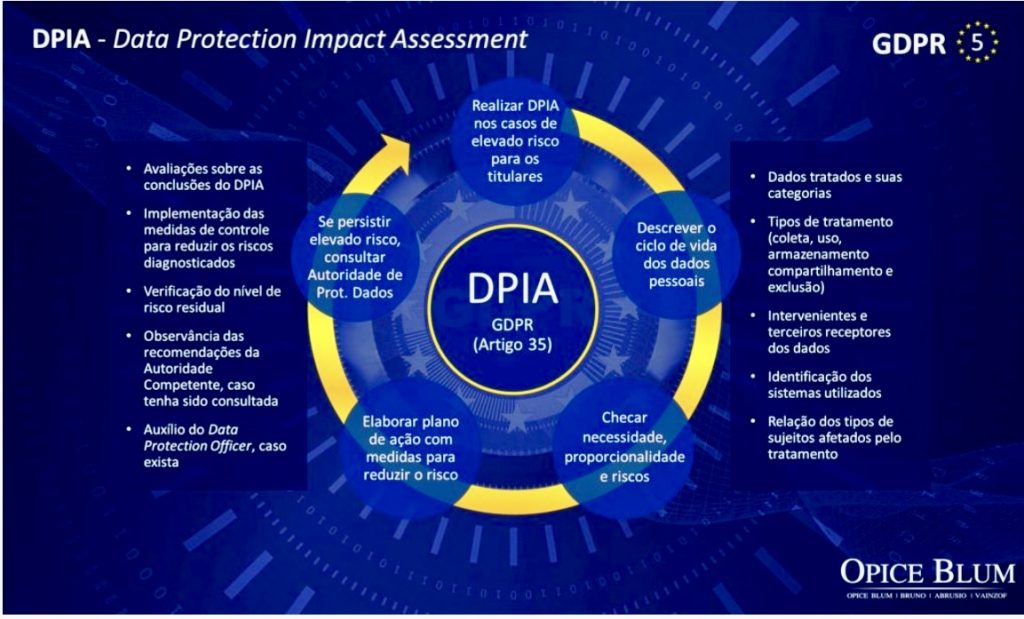
- Risk Assessments: Conduct Data Protection Impact Assessments (DPIAs) for processing activities that are likely to result in high risks to individuals’ rights and freedoms.
11. Engage with Stakeholders:
- Cross-Functional Collaboration: Work with various departments (e.g., IT, Legal, HR, Marketing) to identify risks from their specific perspectives.
- Third-Party Risk: Engage with third parties to ensure their compliance with GDPR, especially if they process data on your behalf.
12. Develop a Mitigation Plan:
- Prioritize Risks: Based on the identified risks, prioritize them based on their potential impact and likelihood.
- Action Plan: Develop and implement an action plan to mitigate these risks, including updating policies, enhancing security measures, and providing additional training.
Conclusion:
Identifying risk areas in GDPR compliance is an ongoing process that requires a thorough understanding of the regulation, continuous monitoring of data practices, and active collaboration across the organization. By systematically addressing each aspect of GDPR, organizations can better manage compliance risks and protect the personal data they handle.