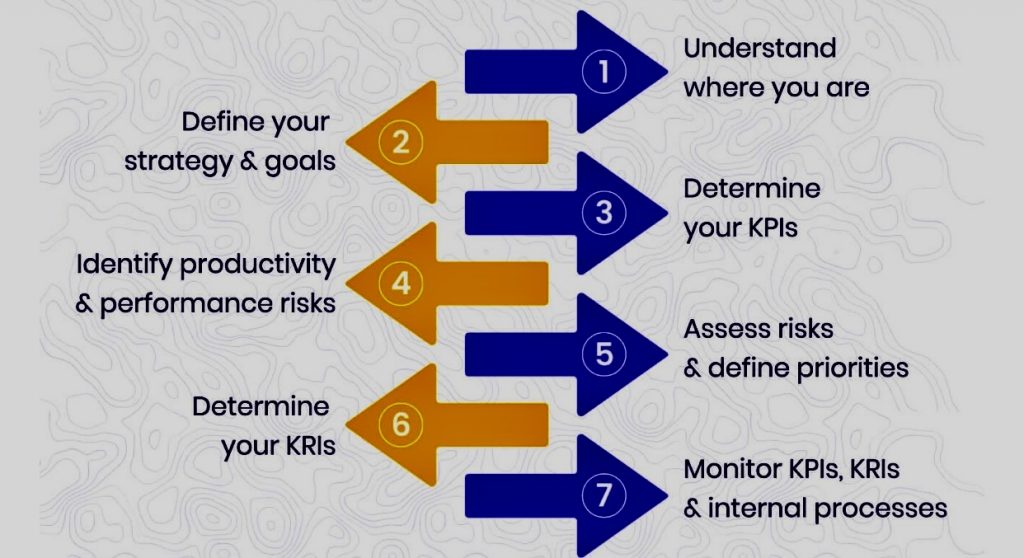
Building a Proactive Cyber Resilience Strategy: Safeguarding Against Evolving Threats
In the digital age, the cyber threat landscape is continuously evolving, posing an ever-present challenge to businesses and organizations worldwide.
With the increasing sophistication of cyber attacks, it’s no longer a question of if an organization will face such threats, but when. This imminent risk underscores the critical need for a proactive cyber resilience strategy.
Cyber resilience refers to an entity’s ability to continuously deliver the intended outcome despite adverse cyber events. It’s a comprehensive approach that encompasses the ability to prevent, respond to, recover from, and adapt to cyber incidents.
i. Understanding Cyber Resilience
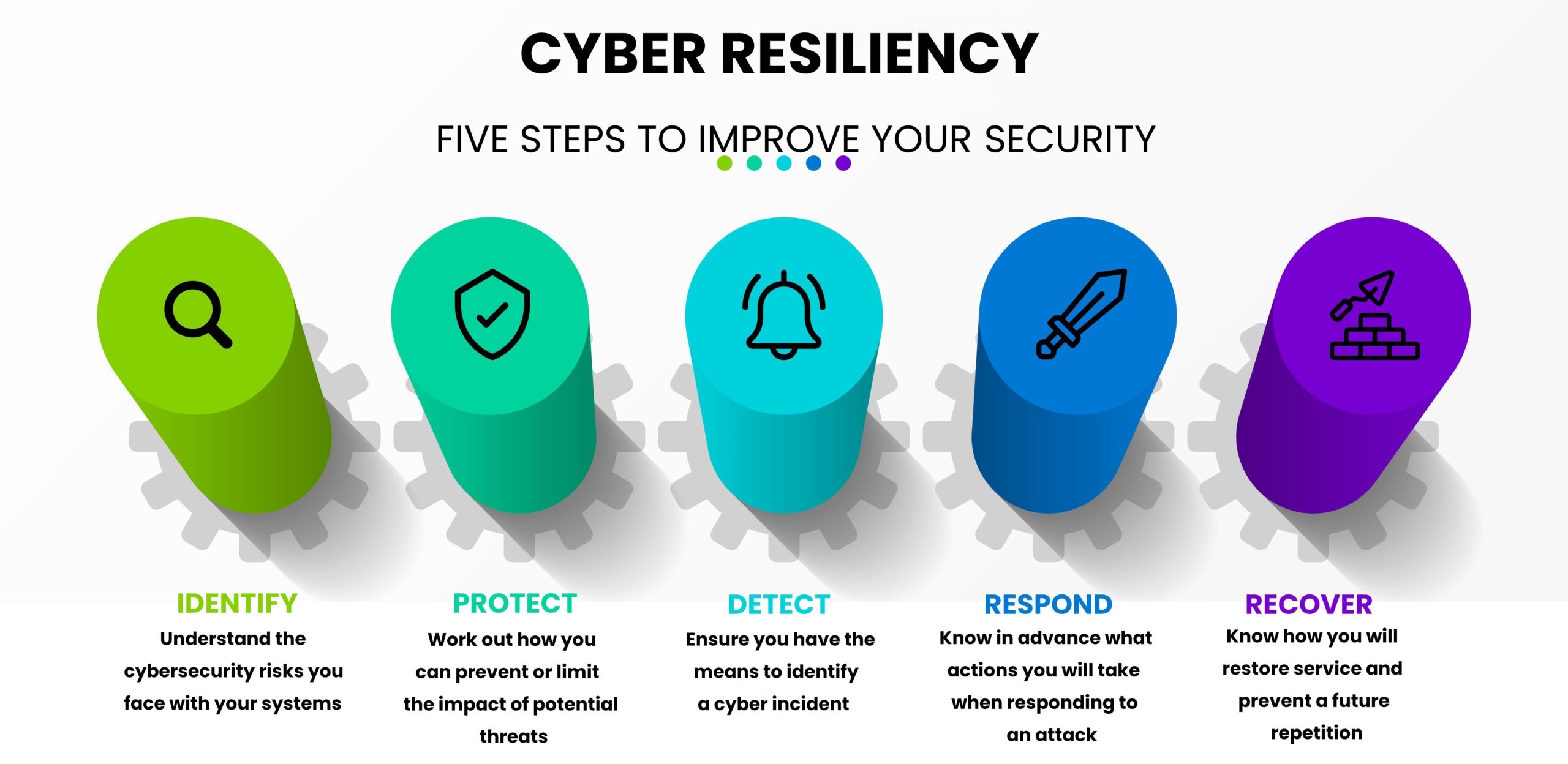
Cyber resilience refers to an organization’s ability to anticipate, withstand, and recover from cyber attacks while maintaining the confidentiality, integrity, and availability of its data and systems. Unlike traditional cybersecurity approaches, which focus primarily on prevention and detection, cyber resilience emphasizes the importance of preparedness, response, and adaptation in the face of inevitable security incidents.
ii. Key Elements of a Proactive Cyber Resilience Strategy
A. Risk Assessment and Management:
o Conduct comprehensive risk assessments to identify potential threats, vulnerabilities, and impacts on critical assets and operations.
o Prioritize risks based on their likelihood and potential impact, taking into account factors such as data sensitivity, regulatory requirements, and business continuity considerations.
o Develop risk management strategies to mitigate identified risks, including implementing security controls, establishing incident response plans, and securing adequate resources for cybersecurity initiatives.
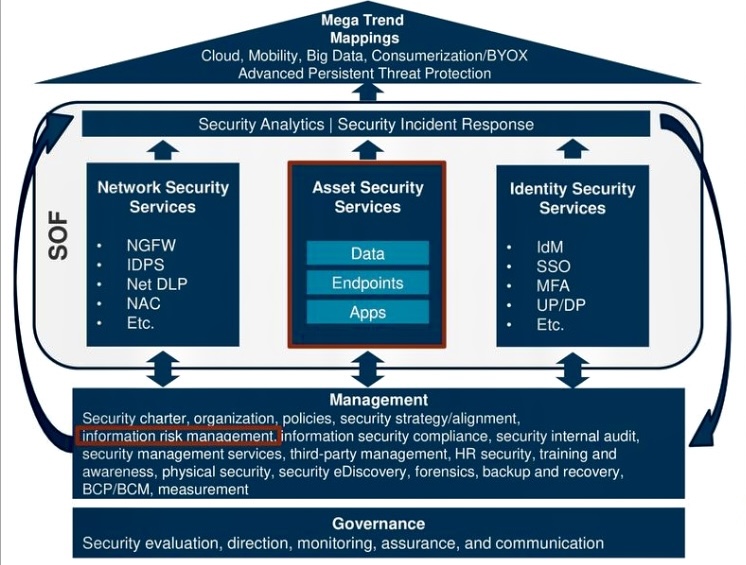
B. Robust Cybersecurity Practices
At the core of cyber resilience is robust cybersecurity. This includes implementing standard security measures such as firewalls, antivirus software, and encryption. However, it goes beyond these basics to encompass regular security audits, the use of advanced threat detection tools, and the adoption of security frameworks like the National Institute of Standards and Technology (NIST) Cybersecurity Framework. Educating employees about their role in cybersecurity and fostering a culture of security awareness are also crucial components.
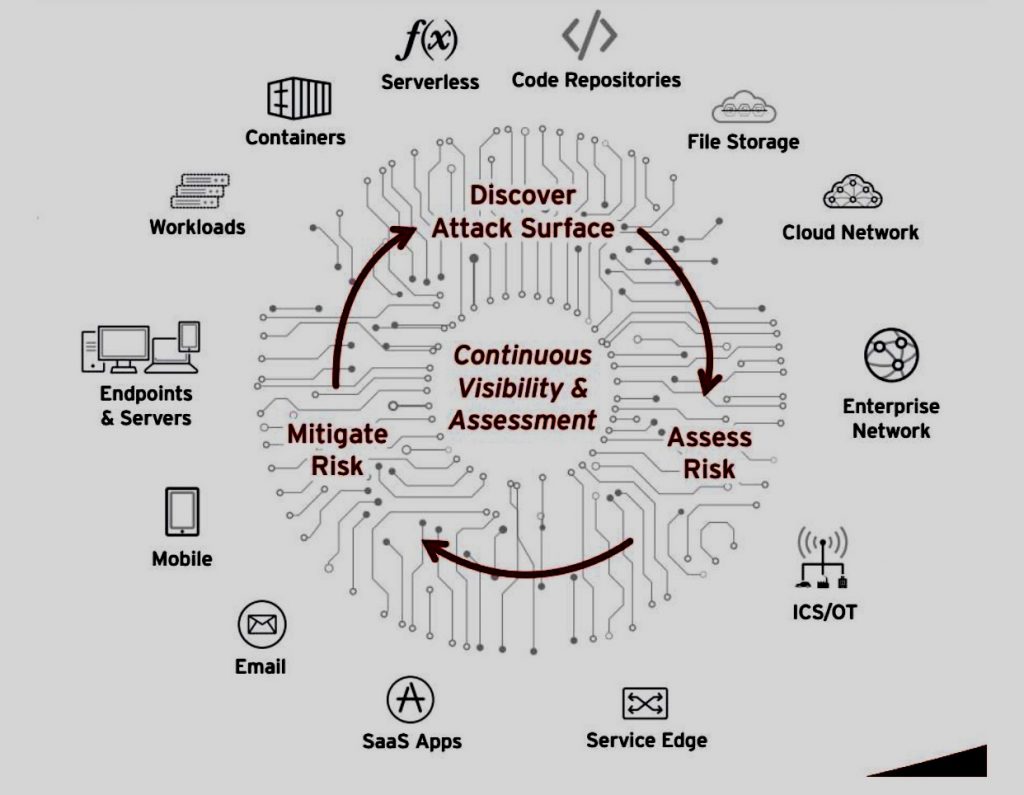
C. Continuous Monitoring and Threat Intelligence:
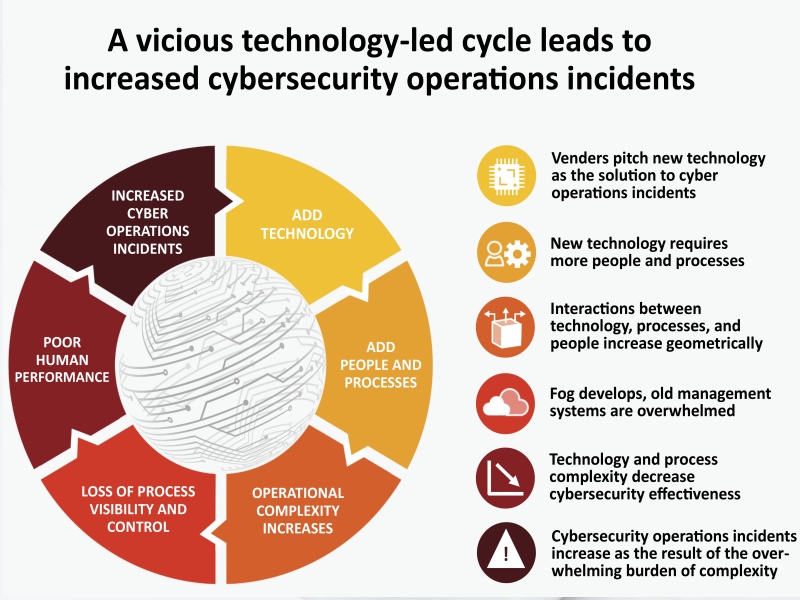
o Implement robust monitoring tools and techniques to detect suspicious activities and anomalies across networks, endpoints, and cloud environments.
o Leverage threat intelligence feeds and information sharing platforms to stay informed about emerging threats, tactics, and vulnerabilities relevant to your organization.
o Establish mechanisms for real-time threat detection and response, enabling rapid containment and mitigation of security incidents before they escalate.
D. Proactive Defense and Incident Response:
o Adopt a defense-in-depth approach to cybersecurity, incorporating multiple layers of security controls, including firewalls, intrusion detection systems, endpoint protection, and encryption.
o Conduct regular security awareness training for employees to educate them about common threats, phishing scams, and best practices for protecting sensitive information.
o Develop incident response plans and playbooks outlining roles, responsibilities, and procedures for responding to cybersecurity incidents promptly and effectively.
E. Business Continuity and Disaster Recovery:
o Develop robust business continuity and disaster recovery plans to ensure the resilience of critical business processes and IT systems in the event of a cyber attack or other disruptive events.
o Test and validate continuity plans regularly through tabletop exercises, simulations, and drills to identify gaps, refine procedures, and improve response capabilities.
o Establish redundant systems, backups, and failover mechanisms to minimize downtime and data loss in the event of a cyber incident or infrastructure failure.
F. Collaboration and Partnerships:
o Foster collaboration and information sharing with industry peers, government agencies, law enforcement, and cybersecurity organizations to exchange threat intelligence, best practices, and lessons learned.
o Engage with third-party vendors, suppliers, and service providers to ensure that cybersecurity requirements are adequately addressed throughout the supply chain.
o Consider partnering with cybersecurity experts, managed security service providers (MSSPs), or incident response teams to augment internal capabilities and expertise.
G. Foster a Culture of Cybersecurity Awareness
Cybersecurity is not just the responsibility of the IT department; it’s a company-wide imperative. Building a culture of cybersecurity awareness involves educating employees on the importance of cybersecurity, encouraging good cybersecurity practices, and ensuring that all staff know how to respond to a cyber incident.
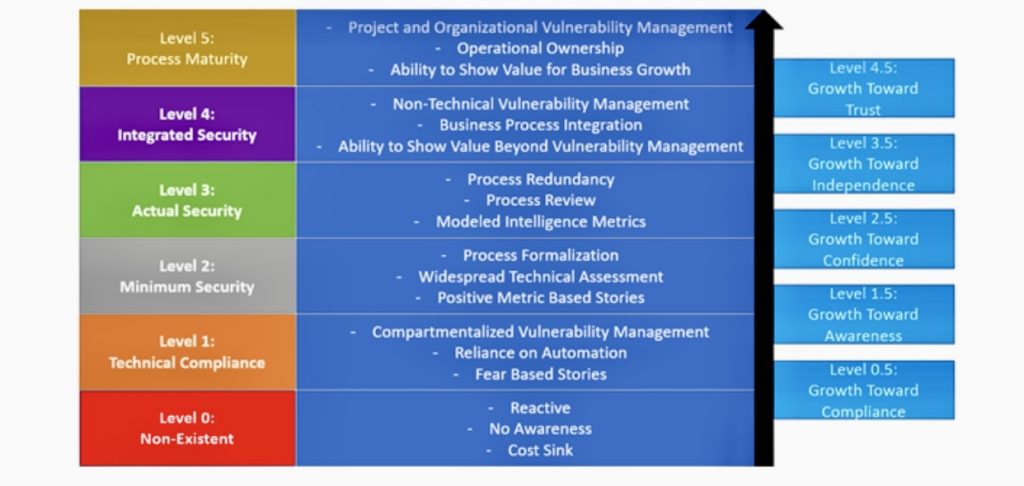
H. Adaptability and Continuous Learning
The cyber threat landscape is dynamic, with new threats emerging continuously. A proactive cyber resilience strategy must, therefore, include mechanisms for monitoring these evolving threats and adapting defenses accordingly. This demands continuous learning and improvement, leveraging insights from past incidents and emerging trends in cybersecurity. Organizations should engage in knowledge sharing with industry peers and participate in cyber threat intelligence networks to stay ahead of potential threats.
I. Regulatory Compliance and Collaboration
Compliance with relevant data protection and privacy regulations, such as the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA), is a crucial aspect of cyber resilience. Furthermore, collaboration with external cybersecurity experts, industry groups, and government agencies can enhance an organization’s preparedness and response capabilities through shared resources and intelligence.
iii. Conclusion
Building a proactive cyber resilience strategy is an ongoing process that requires commitment, investment, and collaboration at all levels of an organization.
By focusing on risk assessment, implementing robust cybersecurity measures, planning for incident response and recovery, fostering adaptability, and ensuring regulatory compliance, organizations can navigate the complexities of the digital landscape with confidence.
Remember, in the realm of cybersecurity, complacency can be the greatest vulnerability. Preparing for, adapting to, and recovering from cyber threats are the hallmarks of a truly resilient organization in today’s interconnected world.
iv. Further references
10 Tips for Creating a Cyber Resilience Strategy | CybeReady
LinkedIn · Blue Team Alpha10+ reactionsPart 3: A Proactive Approach to Building Cyber Resilience
InformationWeekwww.informationweek.comHow to Build True Cyber Resilience
Idenhaus Consultinghttps://www.idenhaus.com › buildin…Building Cyber Resilience: Part II
LinkedIn · Subas Chandra Khanal CISSP®10+ reactionsCyber Resilience Strategy
IT Governancehttps://www.itgovernance.co.uk › c…What is cyber resilience | IT Governance UK
Elev8https://www.elev8me.com › insightsCyber Resilience Strategies for CEOs
Fortinethttps://www.fortinet.com › blogTwelve Steps to Cyber Resiliency | CISO Collective
Bitsightwww.bitsight.comHow to Build a Cyber Resilient Framework