Quantum Computing: Fueling the Future of Digital Transformation
In an era where digital transformation dictates the pace of business evolution, quantum computing emerges as a revolutionary force, poised to redefine the landscape of technology and innovation.
This cutting-edge computing paradigm offers the potential to solve complex problems that are beyond the reach of classical computers, promising to supercharge digital transformation across industries.
By harnessing the principles of quantum mechanics, quantum computing stands to accelerate the processing power available to organizations, enabling breakthroughs in various fields including material science, cryptography, and artificial intelligence.
i. Understanding Quantum Computing

Quantum computing harnesses the principles of quantum mechanics, the branch of physics that deals with the behavior of particles at the atomic and subatomic levels. Unlike classical computers, which use bits (0s and 1s) for processing information, quantum computers use quantum bits or qubits.
Qubits can exist in multiple states simultaneously, thanks to superposition, and can be correlated with each other through entanglement. This allows quantum computers to process vast amounts of information at speeds unattainable by traditional computing systems, opening new horizons for solving complex problems.
ii. Applications of Quantum Computing in Digital Transformation

A. Optimization: Quantum computing excels in solving optimization problems that involve finding the best solution among a vast number of possibilities. From supply chain management and logistics to financial portfolio optimization, quantum algorithms can significantly enhance efficiency and reduce operational costs.
B. Machine Learning and AI: Quantum computing holds promise for revolutionizing machine learning and artificial intelligence by enabling faster training of complex models and more accurate predictions. Quantum algorithms can uncover hidden patterns in large datasets and optimize algorithms for various applications, from drug discovery to personalized recommendations.
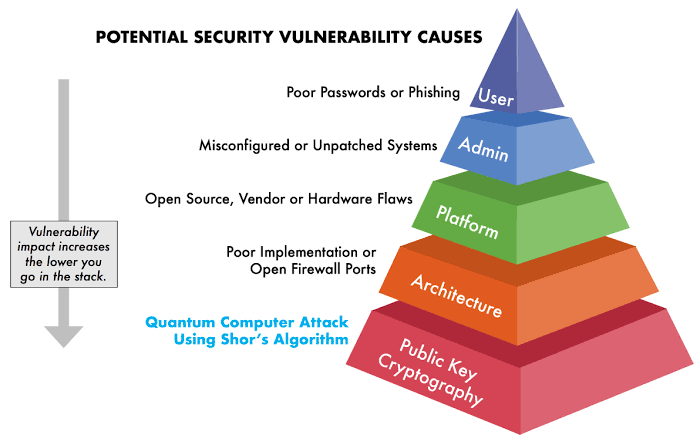
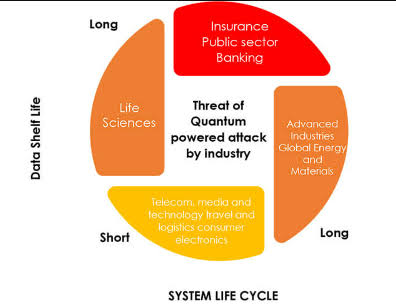
C. Cryptography and Security: The advent of quantum computing also poses challenges for traditional cryptographic methods, as quantum algorithms could potentially break current encryption schemes. However, quantum cryptography offers solutions for secure communication and data protection, leveraging the principles of quantum mechanics to ensure unbreakable encryption.
iii. Unleashing the Potential of Quantum Computing
So, how can quantum computing accelerate digital transformation? Here are a few ways:
o Revolutionizing Drug Discovery and Materials Science: By simulating complex molecules and materials with unparalleled accuracy, quantum computing can expedite drug discovery, optimize material design, and lead to breakthroughs in fields like clean energy.
o Boosting Financial Modeling and Risk Management: Quantum algorithms can analyze massive datasets and identify intricate financial patterns, enabling superior risk management, fraud detection, and investment strategies.
o Optimizing Logistics and Supply Chains: Quantum computing can revolutionize logistics by optimizing delivery routes, managing inventory in real-time, and ensuring efficient resource allocation across complex supply chains.
iv. Quantum Computing in Digital Transformation

A. Accelerated Data Analysis: In the age of big data, the ability to quickly analyze and derive insights from vast datasets is invaluable. Quantum computing offers the potential to process and analyze data at unprecedented speeds, enabling businesses to make more informed decisions faster, identify trends and patterns not immediately apparent, and innovate based on these insights.
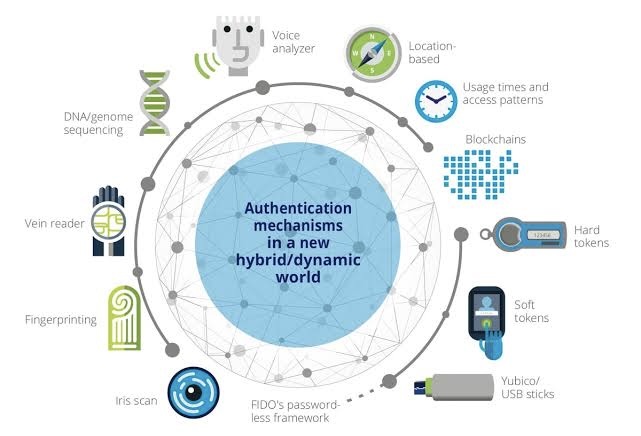
B. Enhanced Security: Digital transformation brings with it increased risks of cyber threats. Quantum computing introduces new paradigms in encryption and cybersecurity. Quantum key distribution (QKD) promises secure communication channels that are theoretically invulnerable to eavesdropping. Additionally, the advent of quantum computing necessitates the development of quantum-resistant encryption methods, ensuring a proactive approach to future cybersecurity challenges.
C. Breakthroughs in Artificial Intelligence (AI) and Machine Learning (ML): AI and ML are at the heart of digital transformation, driving automation and intelligent decision-making. Quantum computing could exponentially increase the capabilities of AI and ML models by enabling the processing of complex, multidimensional datasets far beyond the reach of classical computers. This could enhance predictive analytics, natural language processing, and personalization, among other AI applications.
D. Optimization of Operations: Many businesses face optimization challenges, from logistics and supply chain management to resource allocation. Quantum computing can solve optimization problems more efficiently than classical computing, providing solutions that minimize costs, reduce waste, and improve overall operational efficiency.
E. Experimentation and Research: Organizations can integrate quantum computing into their digital transformation strategies by investing in research and experimentation. Collaborating with quantum computing companies, universities, and research institutions can provide access to cutting-edge technologies and expertise.
F. Talent Development: Developing in-house expertise in quantum computing is essential for organizations looking to leverage this technology effectively. Investing in training programs, workshops, and partnerships with academic institutions can help cultivate a skilled workforce capable of harnessing the power of quantum computing.

G. Strategic Partnerships: Forming strategic partnerships with quantum computing providers and startups allows organizations to access quantum computing resources and expertise without significant upfront investment. Joint ventures and collaborations can accelerate innovation and drive digital transformation initiatives forward.
v. Preparing for the Quantum Future

To harness the potential of quantum computing in digital transformation, businesses need to prepare strategically:
A. Invest in Quantum Skills and Knowledge: Building or acquiring expertise in quantum computing will be essential. This includes understanding quantum principles, staying informed about technological advancements, and considering partnerships with quantum computing firms or academic institutions.
B. Explore Quantum Computing as a Service (QCaaS): As quantum computing hardware is complex and costly, QCaaS offers a more accessible entry point. Many cloud providers are beginning to offer quantum computing services, allowing businesses to experiment with quantum algorithms and applications without significant upfront investment.
C. Identify High-Impact Use Cases: Organizations should start by identifying specific problems or areas within their operations where quantum computing could have the most significant impact. Early focus on feasible, high-value applications can help build momentum for broader quantum initiatives.
D. Stay Agile and Open to Innovation: The field of quantum computing is advancing rapidly. Businesses should remain agile, ready to adapt their strategies as new quantum capabilities emerge, and open to reimagining processes and services in light of quantum’s potential.
vi. Challenges and Considerations
While the potential of quantum computing is vast, several challenges must be addressed for widespread adoption. These include technical hurdles such as qubit stability and error correction, as well as ethical and regulatory considerations surrounding data privacy and security.
vii. Embracing the Quantum Future

While quantum computing is still in its early stages, major tech players like IBM, Google, and Microsoft are actively developing quantum technologies.
Businesses can prepare for the quantum revolution by:
o Understanding the Potential: Familiarizing yourself with how quantum computing can impact your industry is crucial.
o Exploring Cloud-Based Solutions: Cloud platforms offering access to quantum computing resources can help businesses experiment and develop quantum-ready applications.
o Building Expertise: Encouraging ongoing learning and collaboration with quantum computing experts will position your business for future advancements.
viii. Conclusion

Quantum computing represents a paradigm shift in computational power, with the potential to supercharge digital transformation across industries. By embracing quantum computing technologies and integrating them into their digital strategies, organizations can unlock new opportunities, drive innovation, and stay ahead in today’s rapidly evolving digital landscape.
As we stand on the brink of the quantum era, businesses that strategically embrace and prepare for quantum computing will be best positioned to lead in the digitally transformed world, turning challenges into opportunities for sustainable growth and competitive advantage.
ix. Further references
techUKhttps://www.techuk.org › resourceHow does quantum computing in the cloud work?
Qurecahttps://qureca.com › quantum-strat…Quantum Strategy for Business
UK Research and Innovationhttps://www.ukri.org › news › strat…Strategic partnership to supercharge AI in healthcare
Splunkhttps://www.splunk.com › learnThe Digital Transformation Beginner’s Guide