The Future of CISO: Transitioning from Technical Expert to Business Leader
In the ever-evolving landscape of cybersecurity, the role of Chief Information Security Officer (CISO) is undergoing a transformative shift.
Historically, the CISO’s primary responsibility was to ensure the organization’s digital assets were protected from cyber threats.
However, as cyber threats become more sophisticated and pervasive, the CISO’s role has expanded beyond technical expertise.
Modern CISOs are now expected to possess a comprehensive understanding of the organization’s business operations and objectives.
i. The Evolution of the CISO Role; Business Aspects
A. Aligning Cybersecurity with Business Strategy
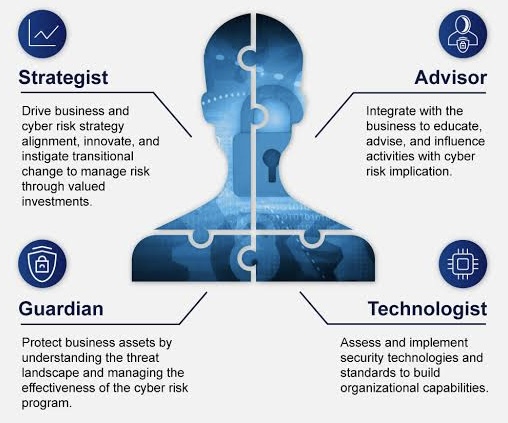
The future CISO is a strategic thinker, capable of aligning cybersecurity initiatives with overall business goals. This alignment ensures that cybersecurity efforts are not just reactive measures but integral components of the organization’s strategic planning. By integrating security into the fabric of business processes, CISOs contribute to the resilience and sustainability of the entire enterprise.
B. Managing Risk Effectively
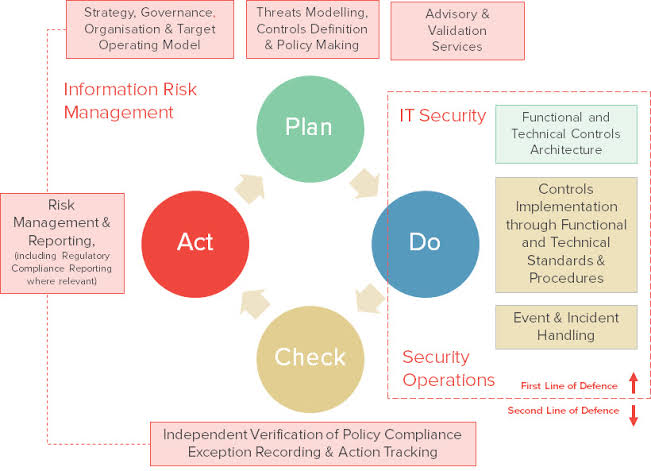
Risk management has become a core competency for CISOs in their journey from technical experts to business leaders. Beyond implementing security measures, CISOs must assess and prioritize risks based on their potential impact on business operations. This involves making informed decisions that balance security requirements with the organization’s appetite for risk, ultimately contributing to the overall resilience of the enterprise.
C. Communication and Collaboration
Effective communication has become a cornerstone of the modern CISO’s skill set. The ability to convey complex technical concepts in a language understandable to non-technical stakeholders is crucial. CISOs must foster collaboration across departments, working closely with executives, legal, compliance, and IT teams to create a unified front against cyber threats. This collaboration ensures that cybersecurity is not seen as a siloed function but an integral aspect of the entire organizational ecosystem.
D. Adapting to Regulatory Changes
In an era of constantly evolving regulatory landscapes, CISOs must stay informed about industry-specific compliance requirements. Navigating these complex regulatory environments demands a nuanced understanding of both technical aspects and legal implications. By doing so, CISOs can ensure that the organization not only meets regulatory standards but also stays ahead of emerging compliance challenges.
E. Continuous Learning and Adaptation
The future CISO is committed to continuous learning and adaptation. With technology evolving rapidly, staying ahead of emerging threats requires a proactive approach to skill development and staying informed about industry trends. This commitment to professional growth enables CISOs to lead their organizations with a forward-thinking and adaptive mindset.
ii. The Driving Forces
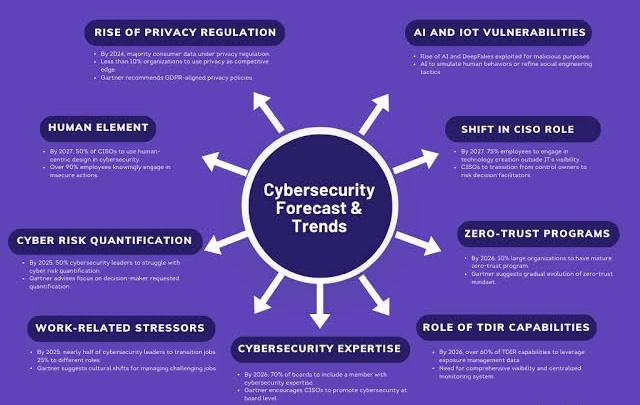
A. Escalating Cyber Threats: The ever-increasing sophistication and frequency of cyberattacks necessitate a proactive approach that aligns cybersecurity with business objectives.
B. Business Integration: Cybersecurity is no longer just an IT concern; it impacts every aspect of an organization. CISOs need to understand business processes and risks to integrate security effectively.
C. Regulatory Landscape: Complex and evolving regulations require CISOs to be aware of legal implications and translate them into actionable plans.
D. Stakeholder Communication: CISOs need to effectively communicate complex security issues to diverse audiences, from technical teams to board members.
iii. Skills for the Future CISO
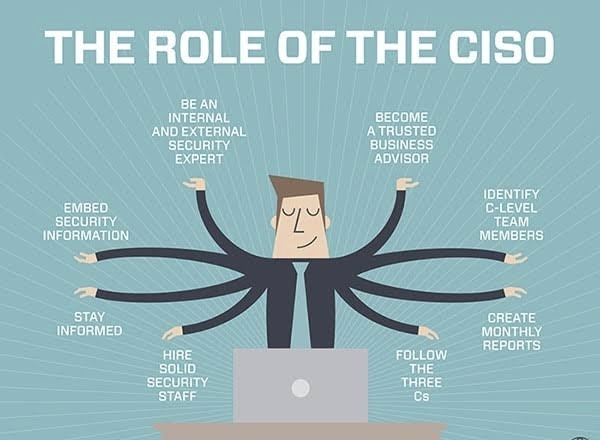
A. Business Acumen: Understanding financial metrics, risk management frameworks, and competitive landscape.
B. Communication & Storytelling: Translating technical jargon into business-understandable terms, effectively communicating risks and mitigation strategies.
C. Leadership & Collaboration: Building relationships across departments, fostering a culture of security awareness, and leading diverse teams.
D. Strategic Thinking: Aligning cybersecurity initiatives with business goals, prioritizing resources, and anticipating future threats.
E. Continuous Learning: Staying abreast of emerging technologies, evolving threats, and best practices.
iv. The Evolving Role
A. From Gatekeeper to Enabler: Moving beyond “saying no” to enabling innovation while managing risks.
B. From Reactive to Proactive: Anticipating threats, building resilience, and fostering a proactive security culture.
C. From Siloed to Integrated: Collaborating with business units, legal teams, and other stakeholders.
D. From Cost Center to Value Creator: Demonstrating the positive impact of cybersecurity on business objectives.
v. Here’s how the CISO role is expected to evolve
A. Strategic Business Alignment:
o CISOs are expected to align security strategies with business goals.
o They need to understand the market, industry, and even global trends that affect their organization.
B. Risk Management Expertise:
o The role of the CISO will further integrate into enterprise risk management.
o They’ll need to identify, quantify, and prioritize risks in business terms, such as potential lost revenue or legal implications.
C. Communications Skills:
o CISOs must be able to communicate risk and security postures to non-technical stakeholders, such as board members and executives.
o They will play a critical role in educating and advising on cybersecurity as a business issue, not just a technical one.
D. Influencing Organizational Culture:
o Future CISOs will be key in embedding a culture of security awareness throughout the organization.
o They’ll need to advocate for security to be seen as a shared responsibility.
E. Navigating Digital Transformation:
o As companies undergo digital transformations, CISOs will need to oversee the security of new technologies, whether it’s cloud computing, IoT, or artificial intelligence.
o They should be prepared to understand and mitigate the risks associated with these changes.
F. Privacy and Compliance:
o With new regulations like GDPR and CCPA, the CISO will play a leading role in ensuring compliance.
o This includes managing data governance frameworks and handling the intricacies of data privacy.
G. Incident Management and Response:
o CISOs must be able to develop and execute effective incident response plans.
o They need the ability to coordinate cross-functional teams during a security incident.
H. Budgeting and Resource Allocation:
o CISOs will be tasked with making strategic decisions about where to invest in security infrastructure.
o They need to justify the ROI of security investments to other leaders and manage a budget that balances risk and cost.
I. Broader Technological Understanding:
o Even as they transition into more strategic roles, CISOs must keep up with technological advances to understand the security implications.
o This doesn’t mean they need to know every detail but should have a team that can provide depth in technical issues.
J. Leadership and Development of Teams:
o They must lead and develop their teams, attracting and retaining top talent in the cybersecurity field.
o A contemporary CISO will often act as a mentor and coach, ensuring that their team has a progression plan and the opportunity for ongoing learning.
vi. Looking Ahead
o Some propose the BISO (Business Information Security Officer) role, where CISOs report directly to the CEO, highlighting the strategic importance of cybersecurity.
o Continuous skills development and adaptation will be crucial for CISOs to navigate the ever-changing threat landscape.
o Effective communication and collaboration across all levels of the organization will be essential for building a comprehensive cybersecurity posture.
vii. Conclusion

This change is indicative of a broader trend where roles traditionally considered ‘supporting’ are now pivotal in strategic decision-making.
CISOs are becoming integral to the executive team, with a remit that is as much about contributing to business growth as it is about protecting assets.
By embracing this shift, CISOs can play a pivotal role in fortifying their organizations against cyber threats while contributing strategically to the overall success of the business.
The modern CISO has a seat at the table not only as a defender of the enterprise but as a forward-thinking leader helping to navigate its future.
As we look to the future, the CISO’s ability to balance technical expertise with a keen understanding of business dynamics will be instrumental in safeguarding enterprises from the ever-changing landscape of cybersecurity challenges.
viii. Further references
The Evolution of the CISO Role: Steering Through Challenges and Leading with …
LinkedIn · PECB30+ reactionsThe Future of CISO: From Technical Expert to Business Leaders
CIO Africacioafrica.coThe Growing Role Of CISOs
Mediumhttps://medium.com › geekcultureThe CISO of the future. How the role of the CISO …
CXO Magazinehttps://www.cxomagazine.com › de…Developing a Pipeline of Future Cybersecurity Leaders
Dark Readinghttps://www.darkreading.com › wha…What the Boardroom Is Missing: CISOs
Korn Ferryhttps://www.kornferry.com › insightsWelcome to the Board: Your CISO?
FutureCIOhttps://futurecio.tech › gartner-reve…Gartner reveals five behaviours of effective CISOs
LinkedInhttps://www.linkedin.com › pulseThe Future of CISO: From Technical Expert to …