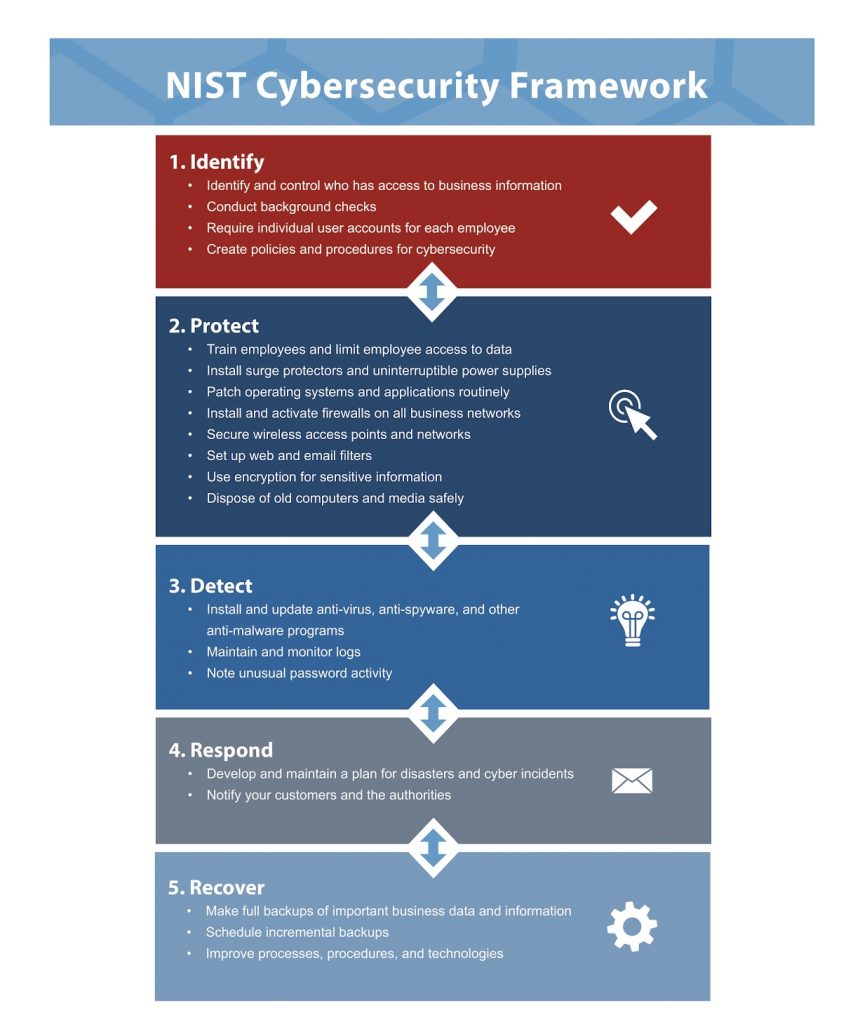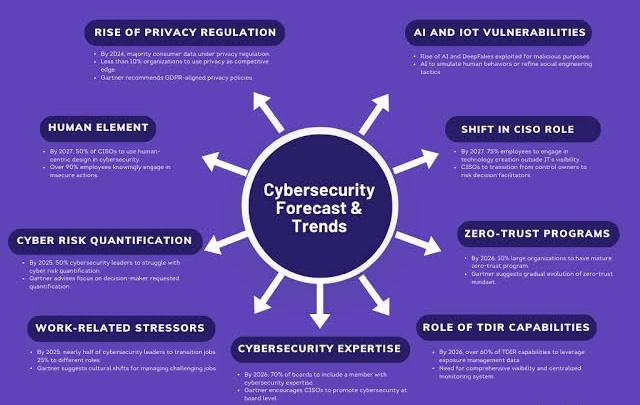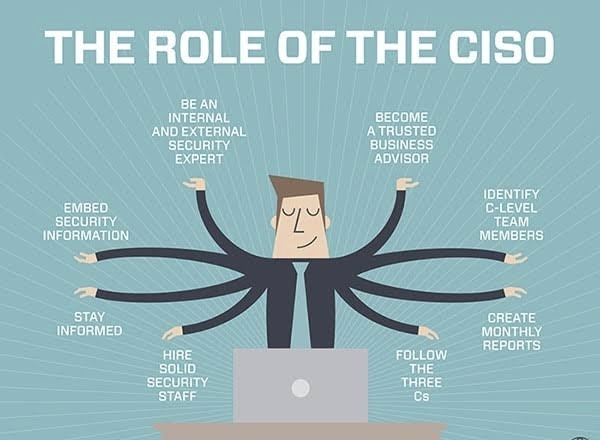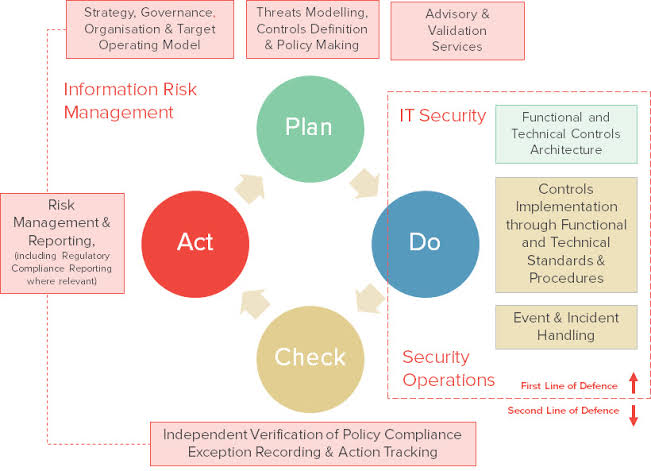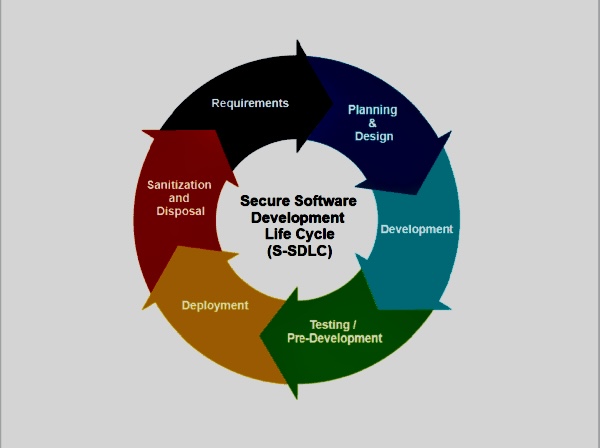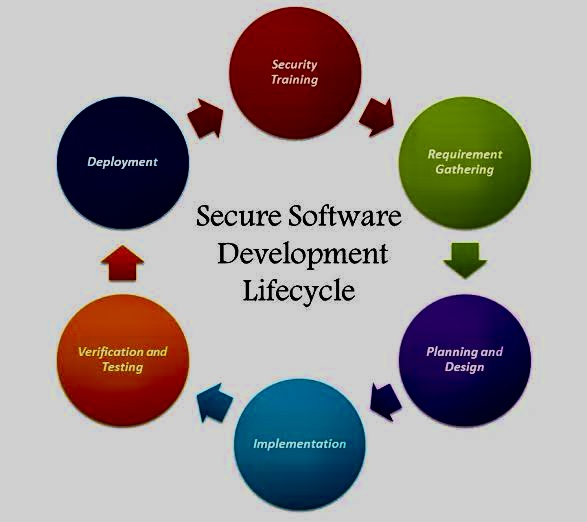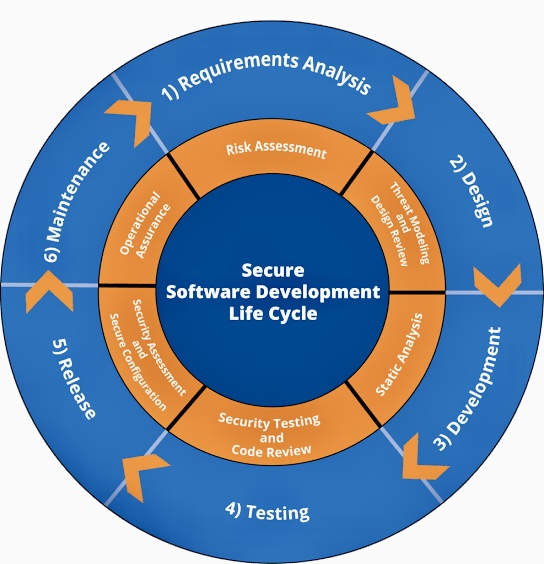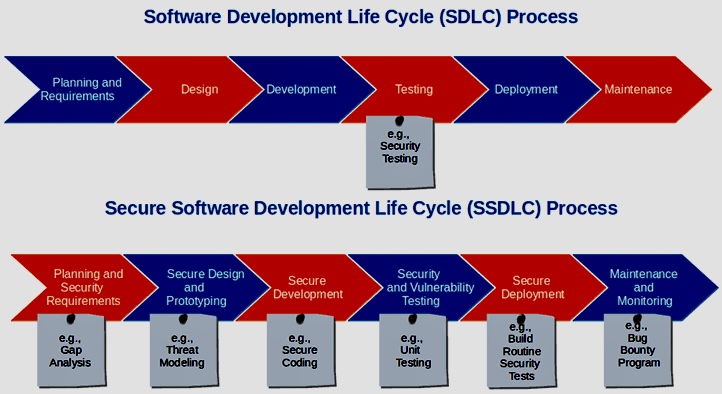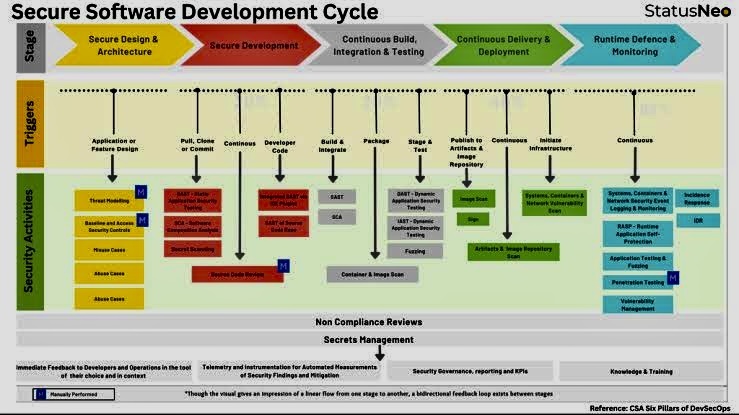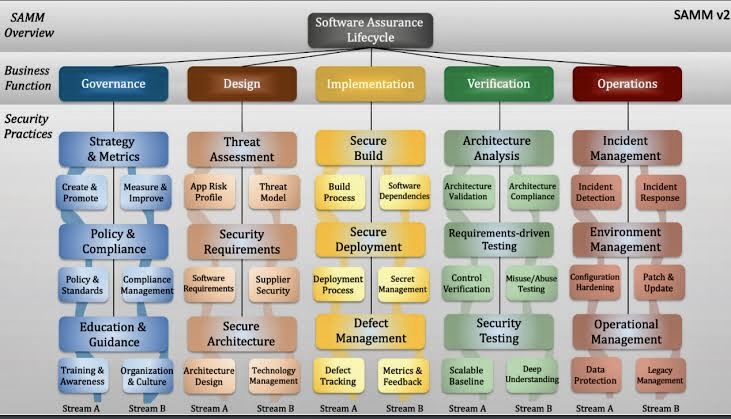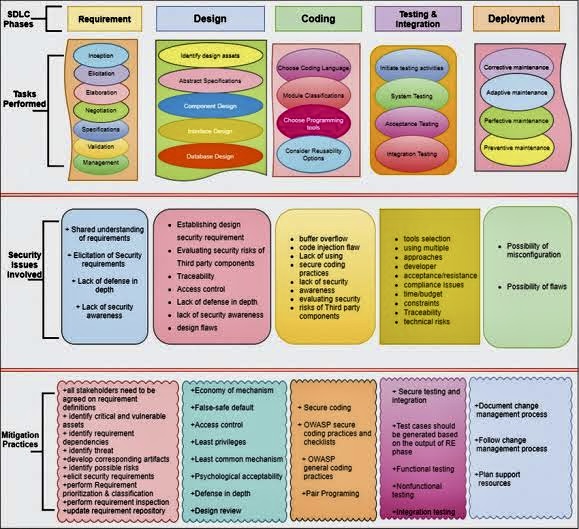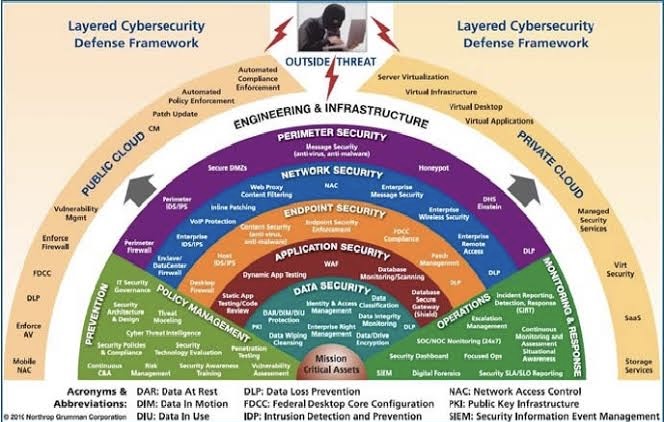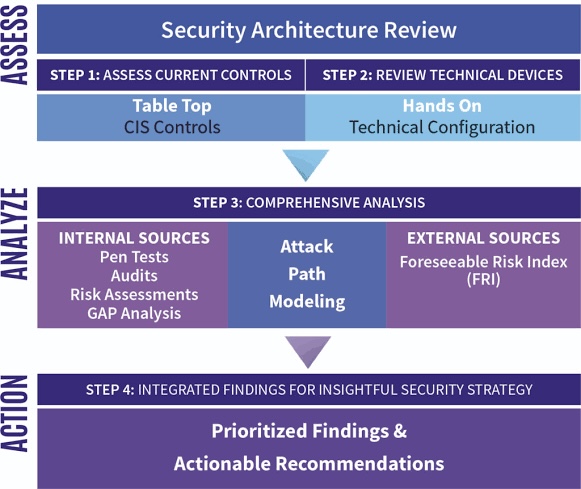
Interconnection Among Security Management Frameworks, Control Inventories, and Security Activities
In the evolving landscape of cybersecurity, the interplay between security management frameworks, control catalogs, and security processes is pivotal in establishing robust, resilient defenses against threats and vulnerabilities that organizations face.
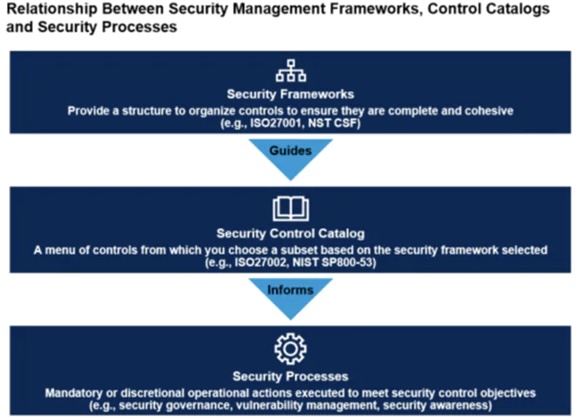
i. Security Management Frameworks
Security Management Frameworks offer a structured approach for managing and mitigating risk within an organization. These frameworks provide an overarching methodology for crafting, implementing, and maintaining security practices.
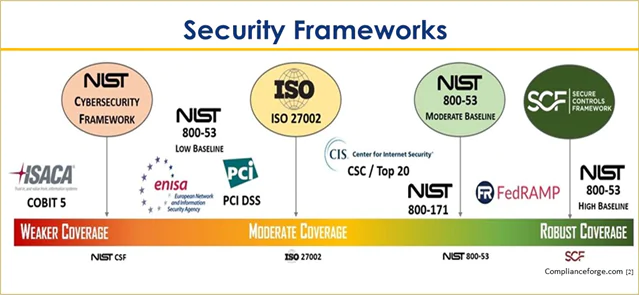
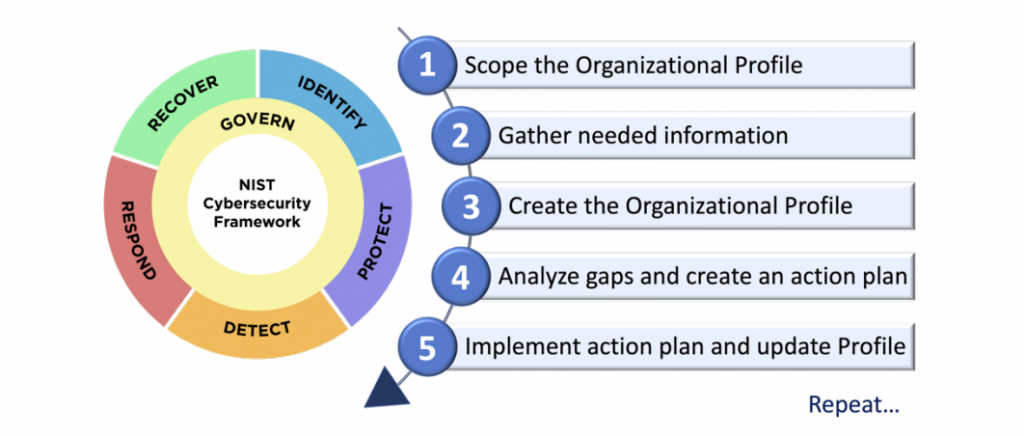
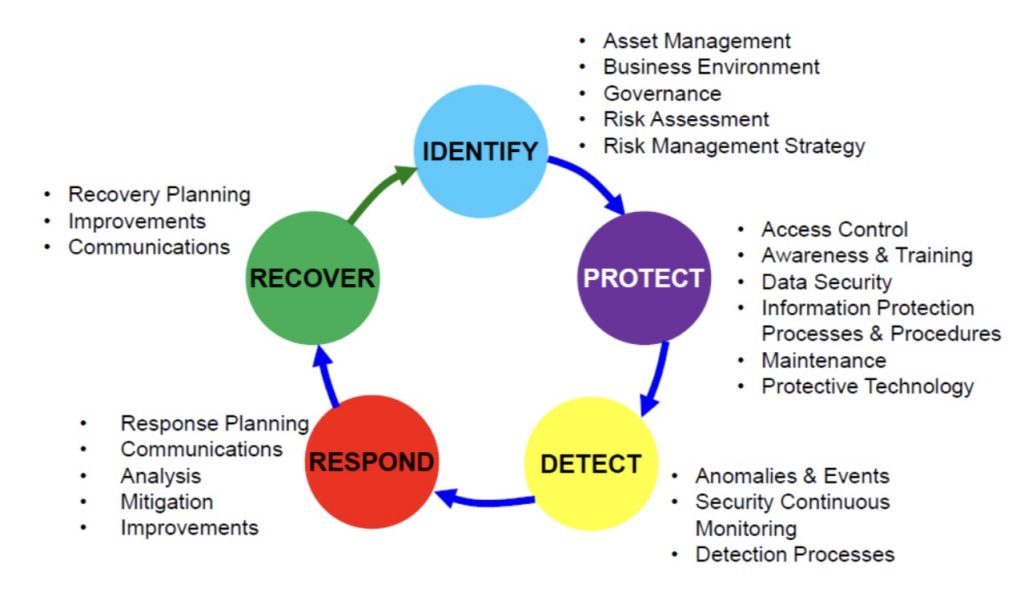
Popular frameworks such as ISO/IEC 27001, NIST Cybersecurity Framework, and COBIT serve as comprehensive guides for organizations to develop their customized security programs. These frameworks are not prescriptive but rather suggest a modular, adaptable strategy for cybersecurity, accounting for the organization’s size, nature, and specific risks.
ii. Control Catalogs
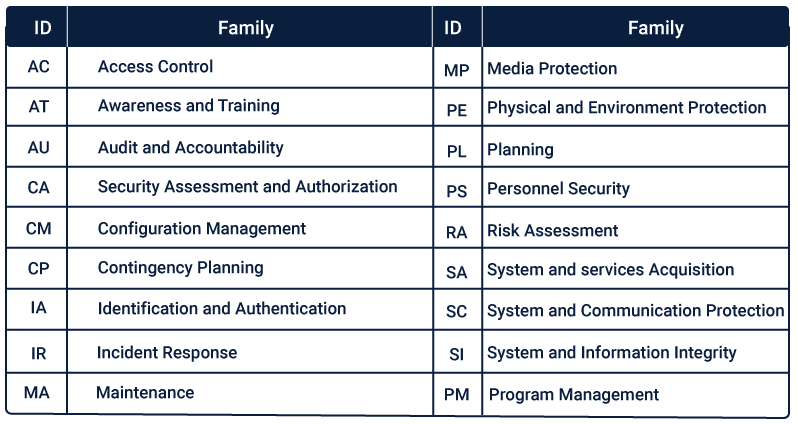
While security frameworks lay down the strategy, Control Catalogs are the tactical elements that comprise specific security controls and measures an organization can implement.
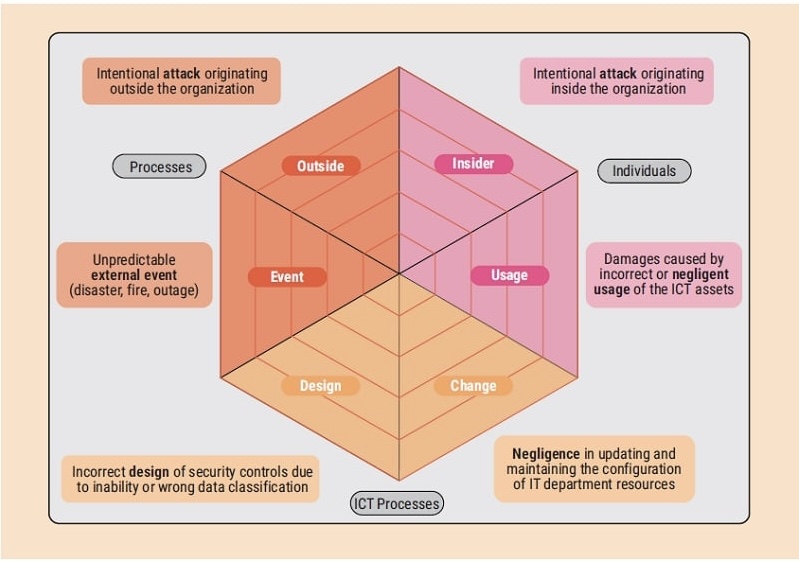
They are essentially a detailed list of security best practices and technical directives designed to protect information and assets. NIST SP 800-53 and the CIS Controls are examples of widely recognized control catalogs.
These catalogs offer categorized security controls such as access control, incident response, and disaster recovery, providing organizations with a detailed roadmap for implementing practical security measures.
iii. Security Processes
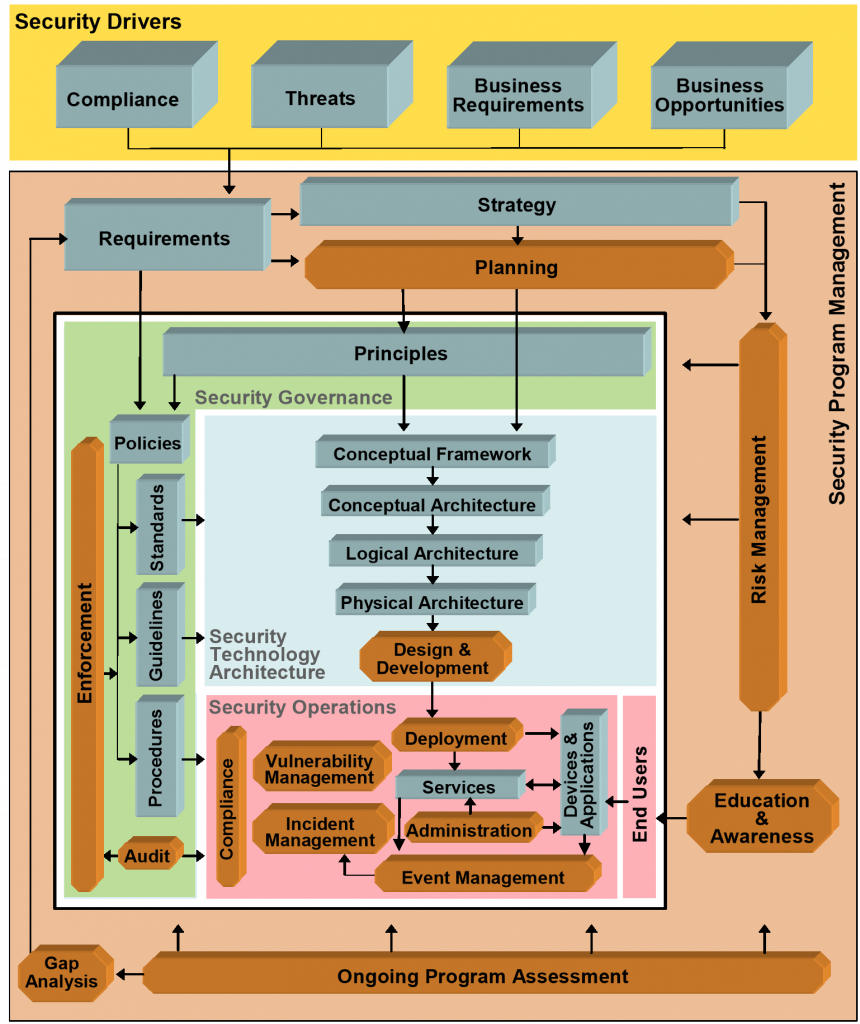
Security Processes refer to the procedural and operational aspects of implementing and managing the security controls and policies outlined by the framework and control catalogs.
These processes encompass the day-to-day activities, procedures, roles, and responsibilities designed to enforce and maintain security controls. Security processes are dynamic, requiring regular updates and assessments to ensure effectiveness.
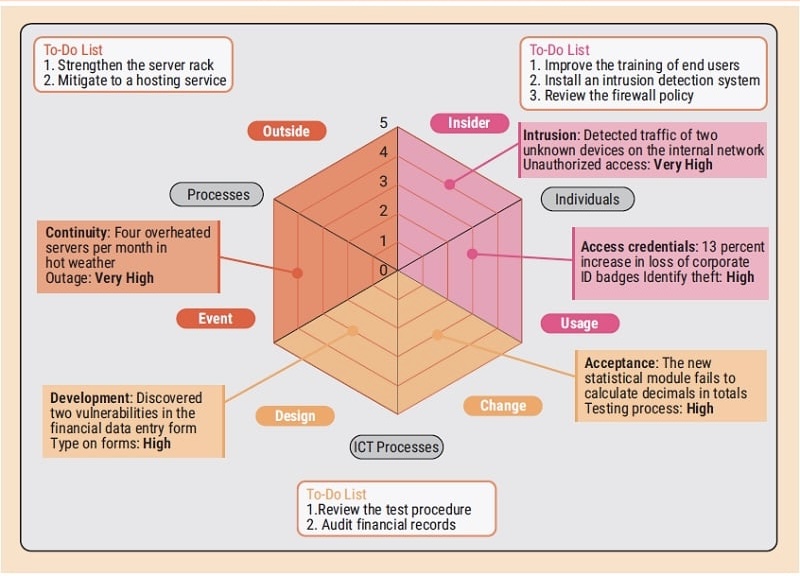
They involve routine tasks such as patch management, vulnerability scanning, risk assessments, and security training and awareness programs.
iv. The Synergistic Relationship
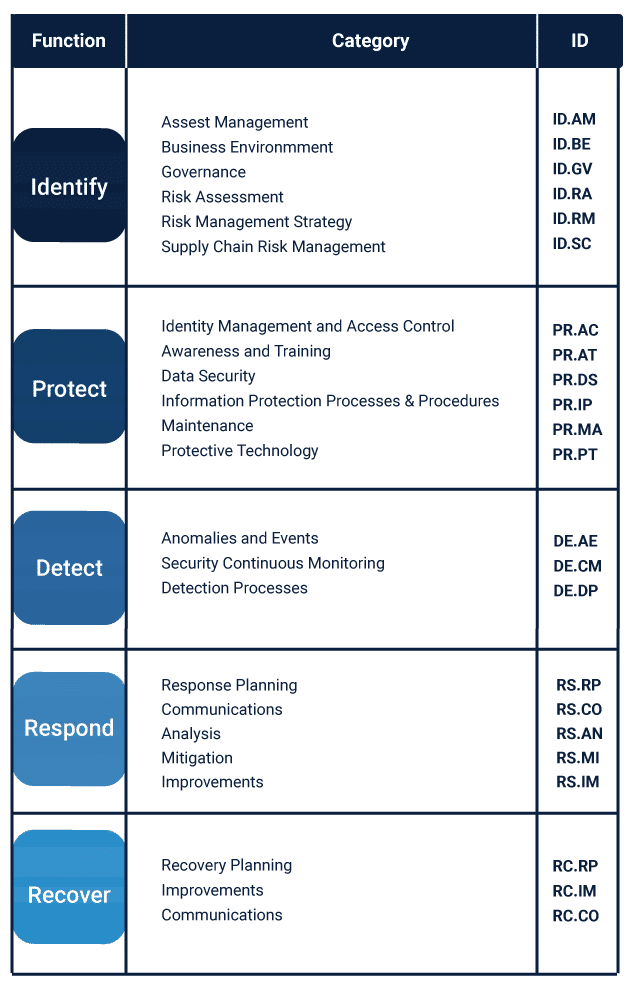
The relationship between Security Management Frameworks, Control Catalogs, and Security Processes is inherently synergistic and cyclical.
Foundational Frameworks: Frameworks serve as the cornerstone, offering a strategic outline.
They help organizations identify their core assets, assess risks, and determine their overall cybersecurity posture. By doing so, frameworks provide a structured method for selecting appropriate control catalogs that align with the organization’s specific needs and threats.
Tactical Control Catalogs: Subsequently, control catalogs bridge the strategic guidance provided by frameworks with tactical, actionable controls. They furnish the specifics – what needs to be implemented to safeguard against identified risks. By adopting relevant controls from these catalogs, organizations can tailor their cybersecurity measures to fit their unique environment.
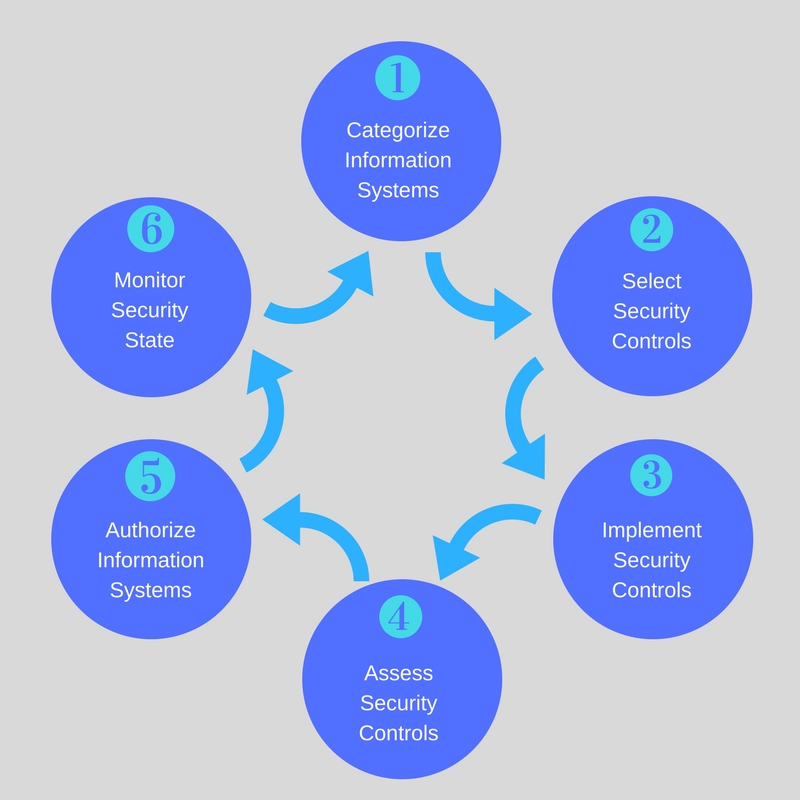
Operational Processes: The implementation and ongoing management of these controls are realized through security processes. These processes translate strategic and tactical guidance into actionable steps, ensuring that the controls are effectively integrated into the organizational environment and that they operate as intended.
Continuous Improvement Cycle: Moreover, this relationship fosters a continuous improvement cycle. Security processes generate data and feedback on the effectiveness of controls, which informs risk assessments and strategy adjustments within the framework. This cycle of assessment, implementation, monitoring, and improvement is crucial for adapting to the ever-changing cybersecurity landscape.
v. Interconnection and Interdependence
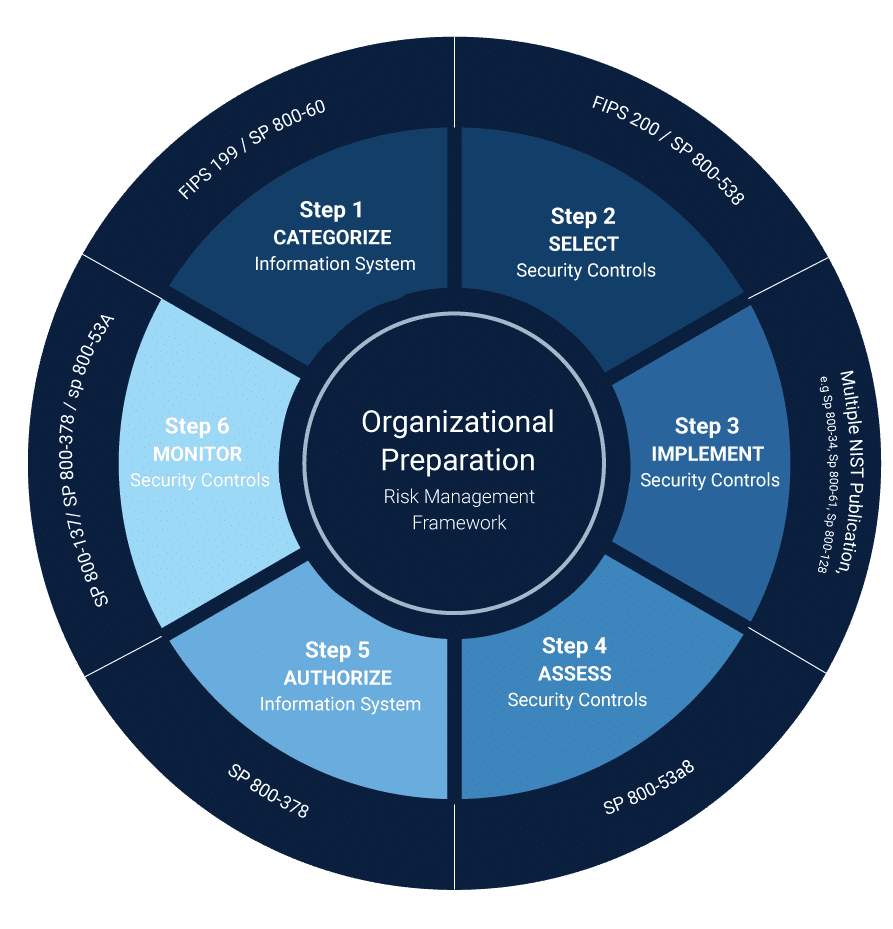
The relationship between security management frameworks, control catalogs, and security processes is both interconnected and interdependent. Security management frameworks offer the overarching structure and strategy for cybersecurity, within which control catalogs provide the specific actions and mechanisms to be deployed. Security processes, in turn, operationalize these controls, bringing the strategy to life through practical application.
This triad operates in a cycle of continuous improvement. Security processes generate insights and data through monitoring and evaluation, which inform adjustments in controls and potentially lead to updates in the strategic framework. For example, an incident response process might reveal vulnerabilities not previously accounted for, prompting a reassessment of the control catalog and adjustments to the broader framework to incorporate new forms of defense.
Moreover, the effectiveness of this integrated approach hinges on customization and context. Organizations differ in terms of size, complexity, industry, and risk profile. Therefore, the adoption of security management frameworks, control catalogs, and security processes must be tailored to fit the specific needs and circumstances of each organization. What remains constant, however, is the necessity of aligning these elements to create a coherent and robust information security strategy.
vi. Conclusion
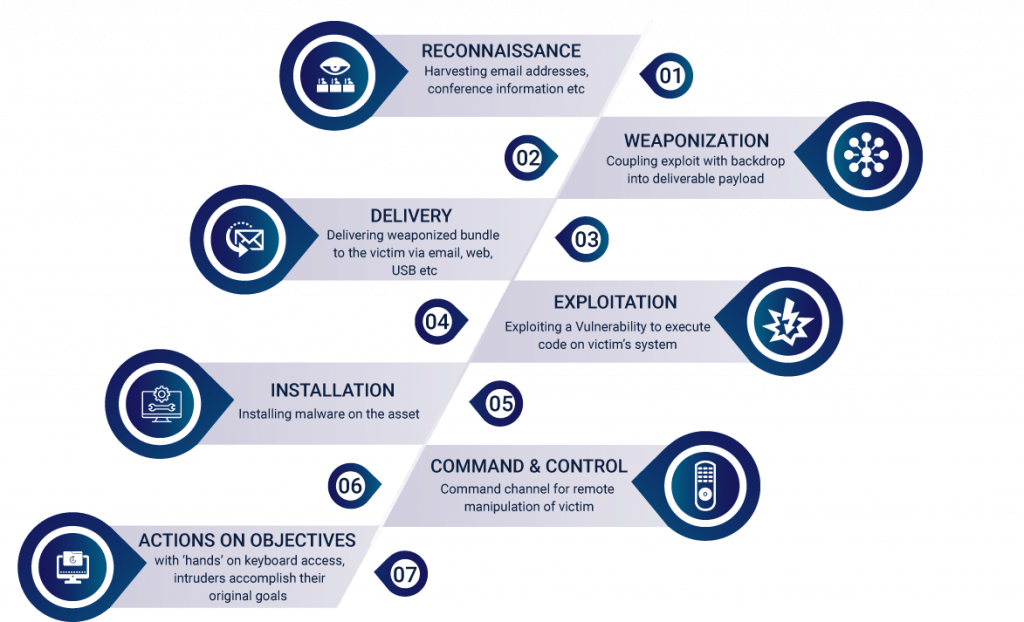
The interdependence of Security Management Frameworks, Control Catalogs, and Security Processes forms the backbone of effective cybersecurity management.
This relationship ensures that strategic planning is effectively translated into practical, operational actions that protect an organization’s information assets against threats.
By understanding and leveraging this relationship, organizations can enhance their security posture, ensuring resilience against current and future cybersecurity challenges.
vii. Further references
UW Homepagehttps://ntiergrc.ssw.washington.edu › …Security Control Frameworks
MDPIhttps://www.mdpi.com › …Risk-Management Framework and Information-Security Systems for Small …
ScienceDirect.comhttps://www.sciencedirect.com › sys…System Security Plan – an overview
CyberSainthttps://www.cybersaint.io › blogNIST SP 800-53 Control Families Explained