Implementing effective strategies to restrict data access only to authorized individuals is crucial for maintaining data security.

Here are some approaches you can take:
A. Implementing a robust data governance framework:
o Scope: Define data governance goals and objectives.
o Purpose: Improved data quality and consistency, Enhanced data security and privacy, Increased data accessibility and transparency, Reduced data-related risks and costs, Improved regulatory compliance, Enhanced data-driven decision-making, Increased trust and confidence in data
B. Role-Based Access Control (RBAC):
o Scope: Assign permissions based on job roles.
o Purpose: Ensures that individuals only have access to the data necessary for their specific job functions.
C. Least Privilege Principle:
o Scope: Grant the minimum level of access required for users to perform their tasks.
o Purpose: Limits potential damage in case of a security breach or human error.
D. Access Policies and Procedures:
o Scope: Establish clear access policies and procedures.
o Purpose: Provides guidelines for managing access and helps ensure consistency across the organization.
E. User Authentication and Authorization:
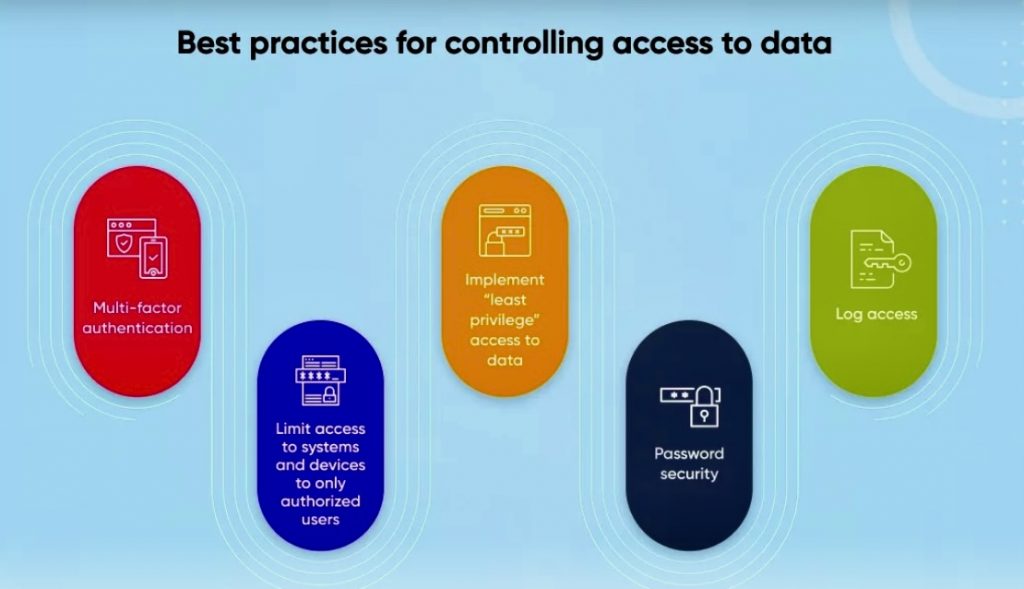
o Scope: Use strong authentication methods (e.g., multi-factor authentication) to verify user identity.
o Purpose: Strengthens access controls by confirming the identity of users before granting access.
F. Utilize IAM Solutions: Identity and Access Management (IAM) solutions can help manage user identities and control access to company resources.
G. Privileged Access Management (PAM):
o Scope: PAM focuses on managing access for privileged users, such as administrators, IT staff, and developers. These users have access to sensitive systems and data, making their accounts prime targets for attackers.
o Purpose: PAM aims to minimize the risk of privilege misuse by implementing additional security controls and restrictions for privileged accounts.
H. Data Classification:
o Best practice: Classify data based on sensitivity.
o Purpose: Allows for more granular control over access, with stricter measures for highly sensitive information.
I. Data Masking and Anonymization:
Data masking replaces sensitive information with fake data, while anonymization removes identifying information from the data. This allows organizations to share data for analysis or testing purposes without compromising user privacy.
J. Encryption:
o Scope: Encrypt sensitive data to protect it from unauthorized access.
o Purpose: Adds an additional layer of security, especially during data transmission and storage.

K. Data Leakage Prevention (DLP):
DLP solutions monitor and control data movement within an organization, preventing sensitive information from being transferred to unauthorized locations or individuals.
L. Regular Access Reviews:
o Scope: Conduct periodic reviews of user access rights.
o Purpose: Identifies and removes unnecessary access, ensuring alignment with current job responsibilities.
M. Audit Trails and Monitoring:
o Best practice: Implement logging and monitoring tools to track user activity.
o Purpose: Enables detection of unauthorized access and provides an audit trail for investigation.
N. Implement a zero-trust architecture (ZTA): To significantly enhance your organization’s security posture by minimizing the attack surface and ensuring access to resources is granted only to authorized users and devices, regardless of their location.
O. Network Segmentation:
o Best practice: Separate the network into segments to restrict access.
o Purpose: Limits lateral movement in case of a security breach, containing potential damage.

P. Access Expiry Policies:
o Best practice: Define access expiration dates for certain roles or data.
o Purpose: Ensures that access is regularly reviewed and aligned with changing business needs.
Q. Utilize Multi-Factor Authentication (MFA):
MFA requires users to provide additional verification factors, such as a code from their phone or a fingerprint scan, in addition to their username and password. This adds an extra layer of security and makes it significantly harder for unauthorized individuals to gain access to data.
R. Biometric Access Control:
o Best practice: Use biometric authentication for additional security.
o Purpose: Adds a highly secure layer of access control based on unique biological characteristics.
S. Employee Training and Awareness:
o Best practice: Educate personnel about security best practices.
o Purpose: Enhances user awareness, reducing the likelihood of unintentional security breaches.
T. Use of Strong Passwords: Encourage the use of complex passwords that are unique to each user. This would minimize the risk of unauthorized access due to compromised credentials.
U. Principle of Least Privilege (PoLP): Apply the principle of least privilege whereby you give users only the access rights they need to do their jobs, nothing more. This minimizes exposure should access credentials be compromised.
V. Session Timeouts: Implement automatic session terminations after a period of inactivity, reducing the risk of unauthorized access.
W. Secure Coding Practices:
Implementing secure coding practices during software development can help prevent vulnerabilities that could be exploited by attackers to access data.
X. Utilize Security Monitoring Tools:
Security monitoring tools can help identify suspicious activity and potential security threats, allowing organizations to take proactive measures to prevent data breaches.
Y. Continuous Communication and Reinforcement:
o Regularly communicate data security updates, policies, and best practices through various channels like newsletters, internal websites, email announcements, and team meetings.
o Encourage open communication and dialogue about data security concerns.
o Utilize various communication channels to cater to different learning styles and preferences.
By implementing a combination of these measures, organizations can establish robust controls to restrict data access to authorized personnel and protect against unauthorized or inappropriate use of sensitive information.