Powering Your Digital Transformation through Talent Strategies Focused on Skills
In the rapidly evolving digital landscape, organizations across industries are embarking on digital transformation journeys.
These transformations, aimed at improving efficiency, enhancing customer experience, and innovating product offerings, require not just advanced technologies but also a highly skilled workforce.
Accordingly, the success of digital transformation hinges not just on technology but significantly on the talent that drives it. Here, skills-based talent strategies emerge as a critical enabler, providing organizations with the agility, creativity, and expertise needed to navigate the complexities of the digital age.
Traditional hiring practices, often focused on credentials and formal education, are increasingly unable to meet the dynamic needs of digital initiatives.
As a response, forward-thinking companies are adopting skills-based talent strategies. This approach emphasizes the practical skills and competencies candidates bring to the table, rather than their educational background or job titles. Let’s delve into how organizations can fuel their digital transformation by leveraging skills-based talent strategies.
i. The Shift to Skills-Based Talent Strategies
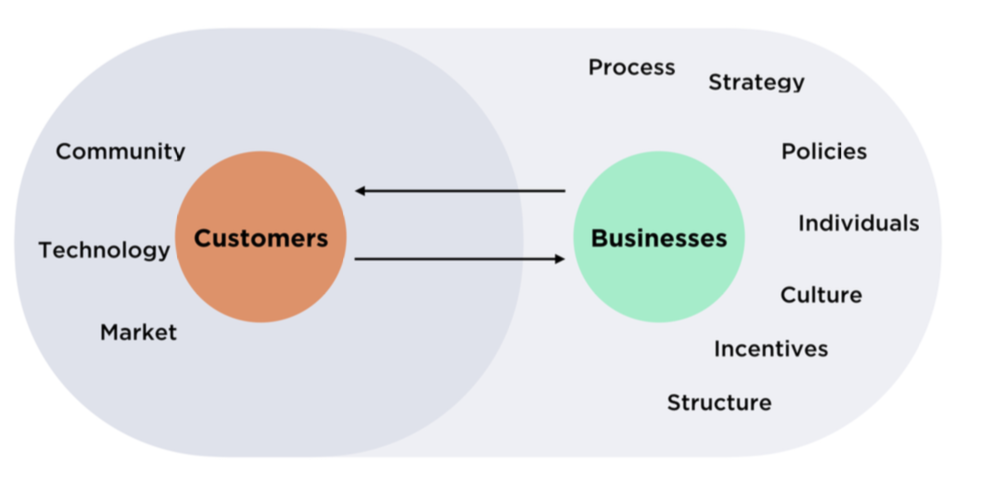
Skills-based talent strategies pivot on identifying, attracting, and nurturing the specific competencies that align with an organization’s digital objectives. This shift represents a more flexible, inclusive, and efficient way to close the talent gap in critical areas such as cybersecurity, data analytics, AI, and cloud computing.
ii. Advantages of Skills-Based Strategies

A. Enhanced Adaptability: By focusing on skills, organizations can more easily adapt to technological changes, as they can quickly identify and fill gaps in their workforce’s capabilities.
B. Increased Diversity: This approach often leads to more diverse hiring, as it removes barriers to entry that might have excluded talented individuals without traditional qualifications but with relevant skills.
C. Optimized Talent Utilization: Skills-based strategies enable companies to better leverage their existing workforce by identifying and deploying hidden or underutilized talents within their teams.
iii. Define Skills-Based Talent Strategies

o Identify Skill Gaps: Assess your current workforce skills and compare them to the skills required for your digital initiatives. This will help you identify any gaps that need to be addressed.
o Build a Skills-Based Talent Pool: Look beyond traditional job titles and focus on the specific skills needed for your projects. This opens your talent pool to a wider range of qualified individuals.
o Invest in Upskilling and Reskilling: Provide training opportunities for your employees to develop the skills needed for digital transformation. This can include internal training programs, online courses, or tuition reimbursement.
o Promote Internal Mobility: Create opportunities for employees to move within the organization to roles that better utilize their skill sets. This not only motivates employees but also helps fill talent gaps.
o Embrace Flexible Work Arrangements: A skills-based approach allows for more flexible work arrangements, as talent can be identified based on skills rather than location. This can attract a wider range of talent and improve employee satisfaction.
iv. The Role of Skills-Based Strategies in Digital Transformation
A. Enhanced Agility and Innovation
Digital transformation demands a workforce that can quickly adapt to new technologies and methodologies. Skills-based strategies ensure that employees can transition between roles and projects as needed, fostering a culture of agility and innovation. For example, a software developer with expertise in artificial intelligence (AI) can be reallocated to projects involving AI integration without the constraints of rigid job descriptions.
B. Bridging the Skill Gap
As technology evolves, so does the demand for new skills. Traditional hiring processes often struggle to keep up with these changes, leading to skill gaps that can hinder transformation efforts. By focusing on the specific skills required for current and future projects, organizations can bridge these gaps more effectively. Upskilling and reskilling existing employees become central to this approach, allowing organizations to build a versatile and future-ready workforce.

C. Optimizing Talent Utilization
A skills-based approach enables organizations to maximize the potential of their existing talent. By understanding the skills available within the organization, leaders can deploy resources more strategically, ensuring that the right people are working on the right projects. This optimization not only enhances productivity but also boosts employee engagement and satisfaction by aligning work with individuals’ strengths and interests.
D. Data-Driven Decision Making
Implementing a skills-based strategy requires robust data analytics to track and predict skill requirements. By leveraging data, organizations can gain insights into workforce capabilities, identify trends, and make proactive decisions about talent development and acquisition. This data-driven approach allows for more precise alignment between business goals and workforce capabilities, ensuring that digital transformation efforts are well-supported.
v. Implementing Skills-Based Talent Strategies

A. Redefine Job Descriptions and Hiring Criteria
Begin by revising job descriptions and hiring criteria to focus on specific skills and competencies needed to perform job functions effectively, rather than on degrees or years of experience. This involves a detailed analysis of the tasks and objectives associated with each role and determining the necessary skills for success.
B. Utilize Skills Assessments and Competency-Based Interviews
Incorporate tools and techniques designed to objectively assess a candidate’s skills and competencies. This may include practical assessments, project-based tasks, or scenario-based questions during the interview process that allow candidates to demonstrate their abilities in real-world contexts.

C. Invest in Training and Upskilling Programs
Digital transformation is an ongoing journey, and so is the development of your workforce. Investing in continuous learning opportunities allows employees to acquire and refine the skills needed to support new technologies and methodologies. This not only helps close the skills gap but also increases employee engagement and retention.
D. Embrace a Culture of Lifelong Learning
Foster an organizational culture that values and encourages continuous improvement and knowledge acquisition. This can be facilitated by providing access to online courses, workshops, and conventions. In addition, create a supportive environment where learning from failure is seen as a stepping stone to innovation.

E. Leverage Analytics to Track Skills Development
Implementing a skills inventory or utilizing HR analytics tools can help organizations track the development of skills across their workforce. This data can inform strategic decisions about talent deployment, identify areas for further training, and measure the effectiveness of skills-based strategies.
vi. Conclusion

The agility and efficiency demanded by digital transformation initiatives cannot be supported by traditional hiring practices alone.
By adopting skills-based talent strategies, organizations can more effectively meet the challenges of the digital age. This approach not only helps companies tap into a wider talent pool but also fosters a more dynamic, innovative, and inclusive workforce.
Ultimately, by prioritizing skills and competencies, organizations can ensure they have the human capital necessary to support their digital ambitions and drive sustainable growth in an increasingly competitive business environment.
vii. Further references
Fueling Your Digital Transformation with Skills-Based Talent Strategies – LinkedIn
Deloittehttps://www2.deloitte.com › blogSkills-based Talent Strategies
Fuel50https://fuel50.com › learn › transf…How to transform into a skills-based organization
Forbeshttps://www.forbes.com › sites › al…Aligning Talent With Digital Transformation
Gloathttps://gloat.com › blog › hr-digita…How Digital Transformation Is Reshaping HR
SponsoredAVEVAhttps://www.aveva.comThe Digital Future of Industry
Courserahttps://www.coursera.org › articlesDigital Talent: A Guide to Workforce Transformation
Coevolvehttps://www.coevolve.com › insig…Bridging Digital Transformation IT Skills Gap
Boston Consulting Grouphttps://www.bcg.com › capabilitiesTalent & Skills Strategy Consulting | BCG