The Evolving Role of IS Auditors in the Age of AI: Emerging Skills and Competencies
As the AI revolution continues to reshape industries, the role of Information Systems (IS) Auditors is undergoing significant transformation. New competencies are emerging as essential, driven by the increasing integration of AI technologies into business processes. The demands of the IS auditing profession are shifting, requiring auditors to develop expertise in several critical areas.
Key Competencies at the Forefront of the Shift
A. Advanced Data Analytics with AI Techniques
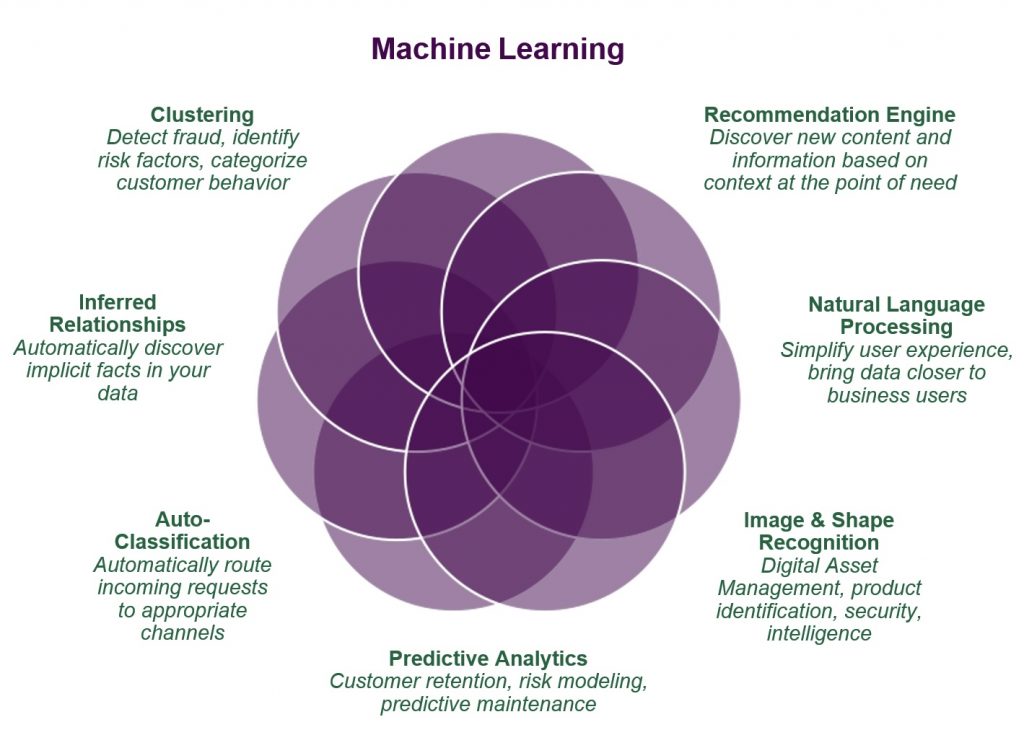
- IS Auditors must now be proficient in advanced data analytics, focusing on AI-specific techniques and big data handling. This expertise is crucial for assessing AI-driven systems, ensuring that data integrity, accuracy, and reliability are maintained.
B. AI Governance and Risk Management Frameworks
- Understanding and applying AI governance frameworks are becoming central to the auditor’s role. IS Auditors must be capable of evaluating AI governance structures, ensuring that AI implementations adhere to risk management protocols and align with business objectives.
C. Explainable AI and Algorithmic Auditing
- As AI systems become more complex, the need for explainability grows. IS Auditors must develop the ability to audit AI algorithms, ensuring that they are transparent, fair, and accountable. This competency is vital for maintaining trust in AI systems and for complying with regulatory requirements.
D. Evolving Regulatory Landscape
- The regulatory environment around AI is rapidly evolving, with new laws and frameworks like the EU AI Act and the NIST AI Risk Management Framework. IS Auditors must stay informed about these developments and understand how to integrate AI-specific regulations with existing standards.
E. Ethical AI
- Ensuring that AI systems are developed and deployed ethically is becoming a core responsibility of IS Auditors. This involves assessing AI for potential biases, fairness, and the overall impact on society.
Additional Competencies for the AI-Driven Era
As IS Auditors adapt to this new landscape, several additional competencies will be essential:
A. AI Lifecycle Management
- Auditors need to understand the complete AI lifecycle, from data collection and model training to deployment and ongoing monitoring. This knowledge is crucial for assessing risks at every stage of AI development.
B. AI Security and Cyber Threats
- With AI systems becoming integral to business operations, IS Auditors must be knowledgeable about AI-specific cybersecurity threats, such as adversarial attacks and AI algorithm manipulation.
C. Continuous Learning Systems Auditing
- Traditional auditing frameworks may not fully apply to AI systems that continuously learn and adapt. IS Auditors must develop expertise in auditing these dynamic systems to ensure ongoing compliance and risk management.
D. Human-AI Collaboration Auditing
- Understanding how AI and human decision-makers interact is crucial. Auditors must evaluate the effectiveness of AI-human collaboration, ensuring that AI supports rather than undermines human judgment.
E. Data Privacy and AI
- As AI systems often require vast amounts of data, IS Auditors need in-depth knowledge of data privacy regulations as they apply to AI, ensuring compliance while balancing the need for high-quality data.
F. AI Ethics and Bias Detection
- Proficiency in identifying and mitigating biases within AI systems is essential. IS Auditors must ensure that AI deployments align with ethical standards, promoting fairness and equity.
G. Cross-Disciplinary Knowledge
- The complexity of AI requires auditors to draw on knowledge from disciplines beyond traditional IT, including law, ethics, and behavioral sciences, to fully understand AI’s implications.
H. Stakeholder Communication and AI Literacy
- IS Auditors must effectively communicate complex AI concepts to non-technical stakeholders, ensuring transparency and understanding across the organization.
I. AI Tool Proficiency
- Familiarity with AI tools and platforms used for data analysis, model development, and AI auditing is essential. Practical experience with these tools enables auditors to provide accurate and actionable insights.
J. Scenario Planning and AI Impact Assessment
- Skills in scenario planning and assessing AI’s broader impacts on business processes, compliance, and risk are crucial for providing comprehensive oversight.
Conclusion
The role of IS Auditors is rapidly evolving in response to the growing influence of AI technologies. The competencies highlighted here, along with the additional skills outlined, will form the foundation of IS auditing in the AI-driven era. Engaging in ongoing discussions and staying informed about these emerging requirements will ensure that the profession continues to adapt and thrive in this new landscape.