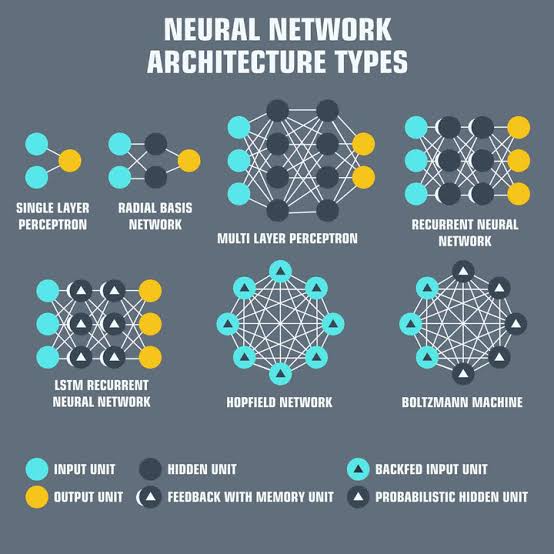
Understanding cybersecurity skills through the SFIA framework: The Missing Piece in Our Cybersecurity Strategy
In today’s ever-evolving cybersecurity landscape, where technological prowess intertwines with everyday business operations, cybersecurity emerges as the bulwark safeguarding digital frontiers. Organizations are constantly struggling to keep pace with the growing sophistication of cyberattacks.
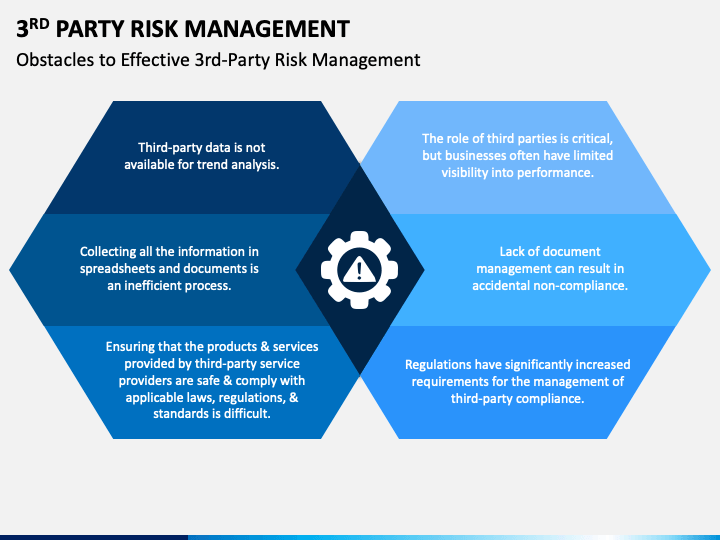
Traditional methods of security awareness training and penetration testing are no longer enough.
This is where SFIA-based skills intelligence comes in.
Central to navigating this labyrinthine domain is a proficient workforce, adept not only in current methodologies but also in anticipating and thwarting emerging threats.
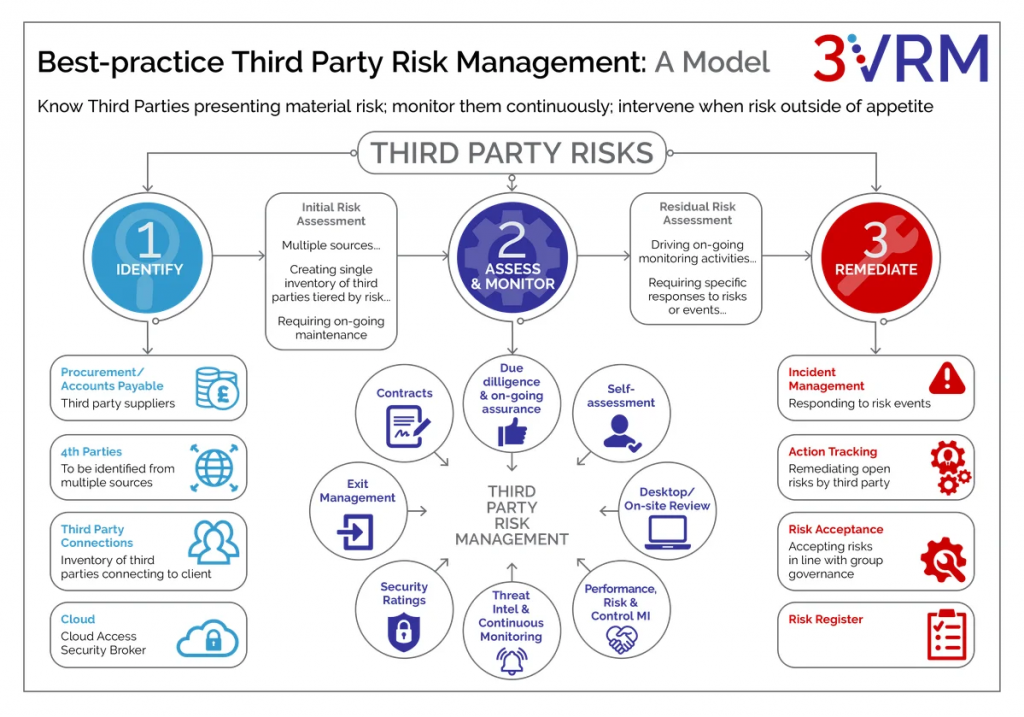
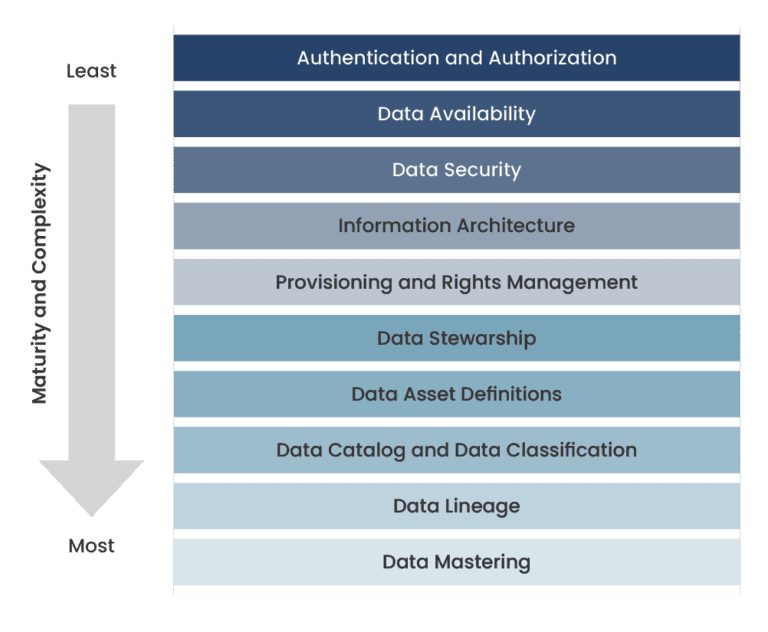
SFIA, or the Skills Framework for the Information Age, is a competency framework that categorizes the skills required in IT and digital occupations. By leveraging SFIA, organizations can gain a deeper understanding of the specific skills their security teams need to effectively combat cyber threats.
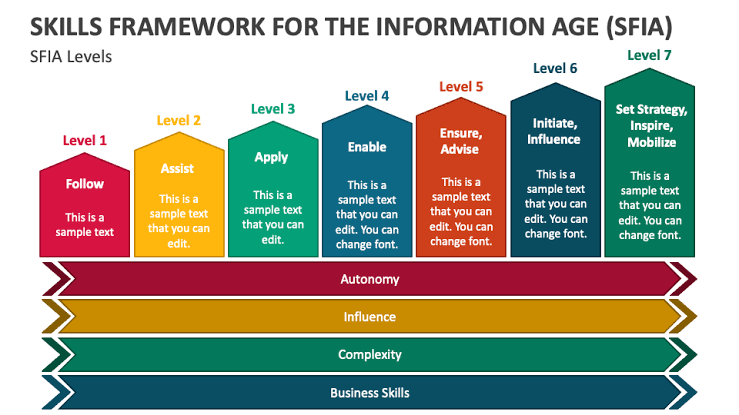
i. Understanding SFIA: A Primer
The Skills Framework for the Information Age (SFIA) is a comprehensive model designed to describe and manage competencies and skills across the IT profession.
SFIA is a global framework designed to describe the skills and competencies required for professionals working in information technology, digital transformation, and related sectors.
Developed by the SFIA Foundation, It provides a universal language for defining skills, abilities, and expertise in a structured and consistent manner.
By delineating skills across various levels of responsibility, SFIA enables organizations to develop clear career pathways and ensure that their workforce is proficient, adaptive, and aligned with the organization’s strategic goals.
ii. Addressing the Cybersecurity Skills Gap

The cybersecurity sector is particularly affected by a significant skills gap, with industry reports consistently highlighting the shortage of skilled professionals capable of defending against increasingly sophisticated cyber threats. Here, SFIA provides a clear outline of competencies expected at various levels of expertise, making it easier for organizations to assess current capabilities and plan for future needs.
iii. The Cybersecurity Conundrum

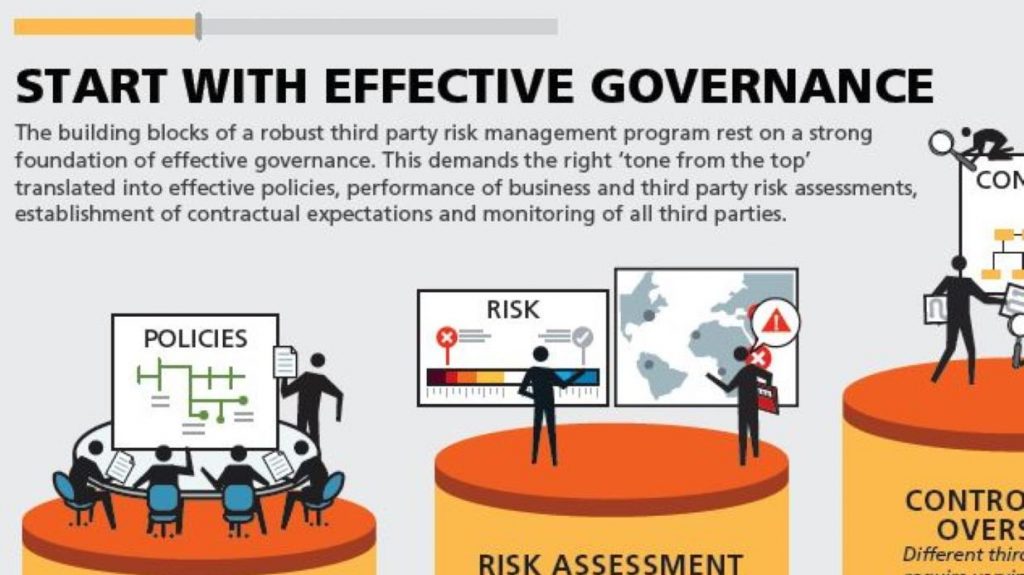
Cybersecurity, with its multifaceted nature, requires a diverse set of skills encompassing not only technical proficiencies but also strategic insight, ethical understanding, and an ability to anticipate the adversary’s next move. The sector’s rapid evolution means that skills which were sufficient yesterday may no longer be adequate tomorrow. This continuous shift poses a significant challenge for organizations in terms of workforce planning, development, and readiness.
iv. Integration of SFIA into Cybersecurity Roles
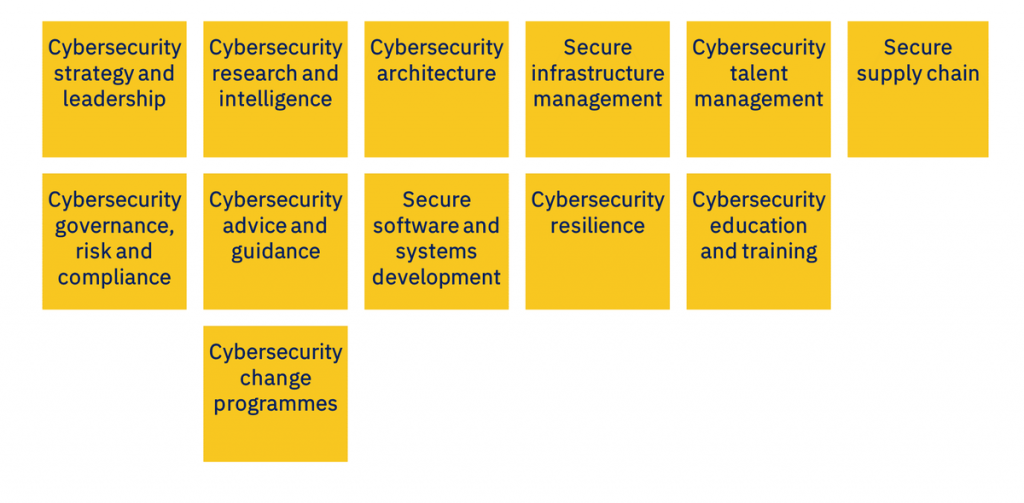
Incorporating SFIA into cybersecurity roles can greatly aid in the recruitment, training, and development of security professionals. For recruitment, SFIA can help create precise job descriptions and required skill sets, enabling more targeted hiring processes. For training, SFIA’s detailed competency levels guide the design of education and professional development programs specific to the needs of the cybersecurity domain.
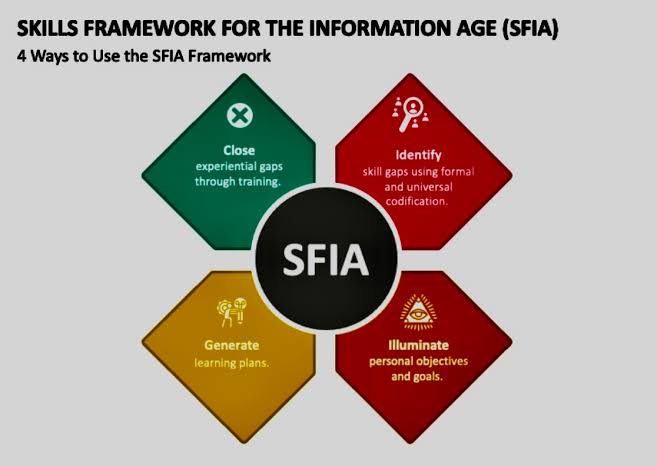
v. SFIA-Based Skills Intelligence: The Game Changer

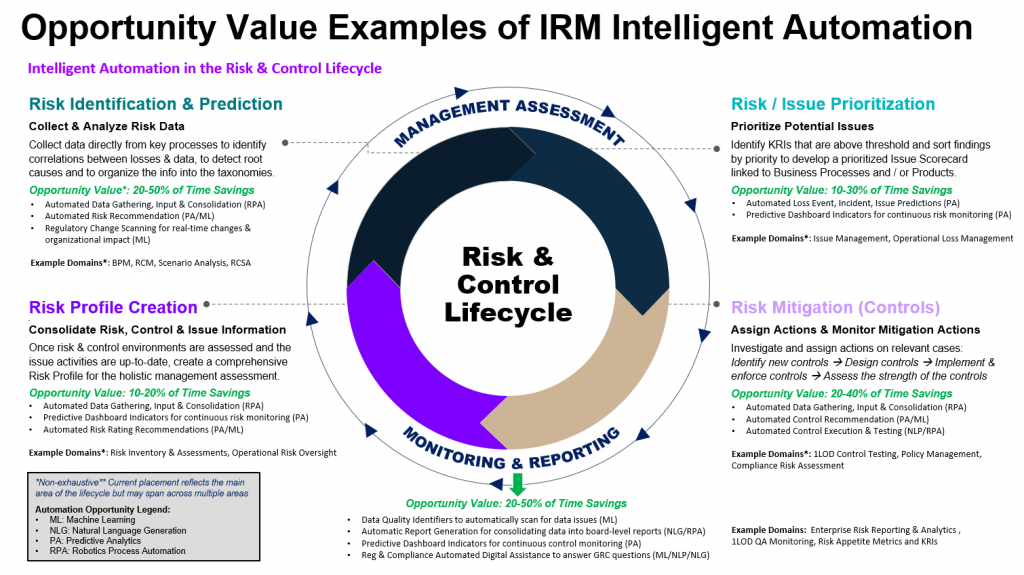
SFIA-based skills intelligence emerges as a pivotal tool in this context, serving as a bridge that connects the present capabilities with future requirements. By leveraging SFIA, organizations can:
o Map Current Skills Landscape: Identify existing competencies, gaps, and areas of over concentration within their cybersecurity workforce.
o Identify Skill Gaps: SFIA can help organizations identify any gaps in their security teams’ skillsets. This allows them to target training and development programs more effectively.
o Forecast Future Skills Needs: Anticipate the skills required to counter new kinds of cyber threats and technologies.
o Develop Targeted Training Programs: Craft training and development programs that are not just reactive but are designed around anticipated future needs.
o Enhance Recruitment Practices: Define clear skill requirements for open positions, thereby attracting candidates who are a better fit for the future challenges the organization is likely to face.
o Improve Hiring Decisions: By aligning job descriptions with the SFIA framework, organizations can ensure they are hiring candidates with the right skills and experience.
o Benchmark Against Industry Standards: SFIA provides a standardized way to compare an organization’s security skills against industry best practices.
o Foster a Culture of Continuous Learning: Encourage ongoing skill development, ensuring that the workforce remains at the cutting edge of cybersecurity defense.
vi. Case Studies: SFIA in Action

Adopting an SFIA-based approach allows organizations to not only address their immediate cybersecurity needs but also to future-proof their cybersecurity workforce. For instance, by understanding the specific SFIA levels and skills associated with cybersecurity roles, companies can identify employees who, with the right training, could transition into these roles, thereby mitigating talent shortages.
Moreover, insights gleaned from SFIA can inform strategic decisions, such as identifying roles that could be effectively outsourced and those that are critical to maintain in-house due to their strategic importance or sensitivity.
Multiple organizations have leveraged SFIA to overhaul their cybersecurity strategy:
o A financial services firm used SFIA to realize a 30% improvement in the time to hire by streamlining the recruitment process based on precise skill requirements.
o A government agency applied SFIA to create a custom training program that reduced cybersecurity incidents by enhancing the competencies of their internal team.
vii. The Benefits of SFIA-Based Skills Intelligence

o Enhanced Security Posture: By ensuring your security team has the necessary skills, you can significantly improve your organization’s overall security posture.
o Reduced Risk of Cyberattacks: A skilled security team is better equipped to identify and mitigate cyber threats.
o Improved ROI on Security Investments: By investing in skills intelligence, organizations can ensure they are getting the most out of their security investments.
viii. challenges in implementing SFIA
The implementation of SFIA-based Skills Intelligence is not without its challenges. Organizations may face hurdles in accurately mapping existing roles to the SFIA framework, as well as in integrating SFIA-based assessments into their talent management processes. Additionally, ongoing updates and refinements to the SFIA framework are necessary to ensure its relevance and effectiveness in an ever-changing digital landscape.
ix. The Path Forward

As cyber threats continue to evolve, so too must the skills of those tasked with defending against them.
SFIA’s framework assists in foresight planning, helping organizations prepare for future technological shifts and the corresponding skill needs.
Implementing SFIA-based skills intelligence in cybersecurity requires a strategic commitment.
Organizations must:
A. Assess: Conduct a thorough assessment of their current skill sets and compare them against SFIA standards.
B. Plan: Develop a clear plan for addressing gaps, enhancing existing skills, and incorporating new competencies that align with future threats and technologies.
C. Implement: Roll out targeted training programs, adjust recruitment criteria, and align workforce planning with the identified skill needs.
D. Review: Regularly review skill requirements and adjust strategies as the cybersecurity landscape evolves.
x. Conclusion
In the escalating battle against cyber threats, SFIA-based skills intelligence offers a structured and foresighted approach to developing a resilient cybersecurity workforce.
The potential benefits of SFIA-based Skills Intelligence for the cybersecurity sector are undeniable. By providing a standardized, dynamic, and granular approach to assessing and developing cybersecurity talent, SFIA-based Skills Intelligence offers a lifeline to organizations grappling with the complex and evolving nature of cyber threats.
By providing a detailed, structured approach to skill and competence management, SFIA enables organizations to build a resilient and agile cybersecurity workforce capable of facing current and future challenges.
As the digital landscape continues to evolve, embracing SFIA-based Skills Intelligence may prove to be the key to building a resilient and capable cybersecurity workforce for the future.
xi. Further references
SkillsTX on LinkedIn: SFIA-Based Skills IntelligenceLinkedIn · SkillsTX1 reaction · 1 month ago
SFIA 8 – illustrative skills profilesSFIAhttps://sfia-online.org › standard-industry-skills-profiles
SFIA Rate CardsSkillsTXhttps://skillstx.com › sfia-rate-cards
T-shaped roles — EnglishSFIAhttps://sfia-online.org › sfia-8 › themes-for-sfia-8 › t-sh…