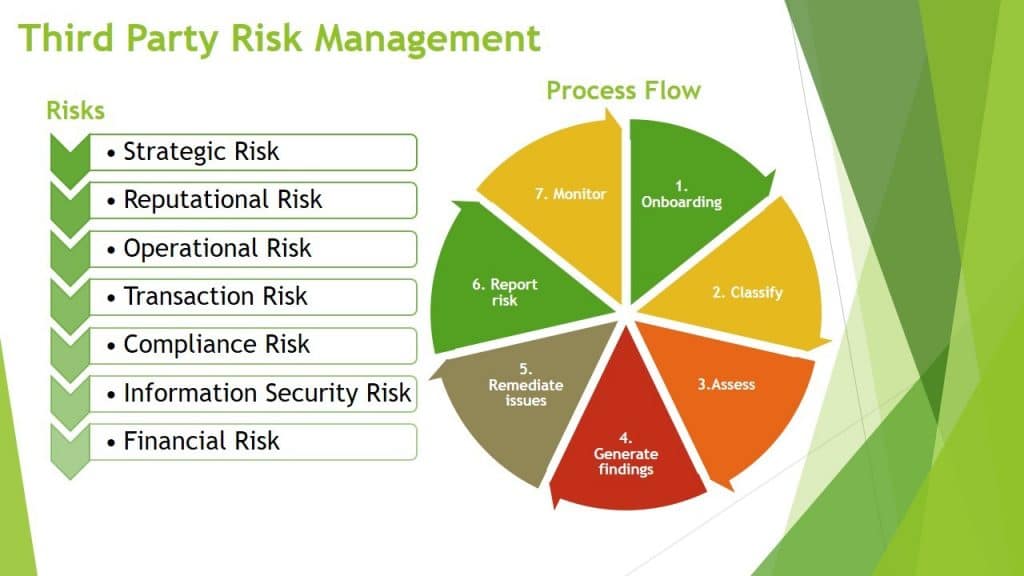
To effectively monitor supplier risk, supply chain risk, or third-party risk, you can utilize Key Risk Indicators (KRIs) and Key Control Indicators (KCIs). These metrics will help you assess potential risks and the effectiveness of controls, while also providing insights into trends over time.
Key Risk and Control Indicators for Supplier, Supply Chain, and Third-Party Risks
KRIs are metrics used to signal potential risks and vulnerabilities within the supply chain or third-party relationships. They are forward-looking and help you anticipate problems before they become critical. Examples of KRIs in this area include:
- Supplier Financial Stability:
- KRI Example: Credit rating changes, late payment history, or declining revenue.
- Scoring: Quantitative (e.g., credit score) or Qualitative (e.g., High, Medium, Low).
- Trend Analysis: Monitor credit score trends over time, showing potential risks of insolvency.
- Delivery Performance:
- KRI Example: On-time delivery rate, missed deadlines, or lead time variability.
- Scoring: Quantitative (% on-time deliveries, days late).
- Trend Analysis: Plot historical delivery data to identify degradation in supplier performance.
- Compliance and Regulatory Risk:
- KRI Example: Frequency of compliance violations, audit findings, or changes in regulatory status.
- Scoring: Quantitative (number of violations) or Qualitative (compliance level: Full, Partial, Non-compliant).
- Trend Analysis: Track compliance issues over time to spot recurring or increasing risks.
- Supplier Concentration Risk:
- KRI Example: Percentage of critical goods supplied by a single supplier.
- Scoring: Quantitative (% of total procurement from one supplier).
- Trend Analysis: Monitor shifts in supplier concentration to identify dependency risks.
- Geopolitical Risk Exposure:
- KRI Example: Number of suppliers in high-risk regions (e.g., war zones, politically unstable areas).
- Scoring: Qualitative (High, Medium, Low based on geographic stability) or Quantitative (number of suppliers).
- Trend Analysis: Track geopolitical risk exposure by region and its potential impact on the supply chain.
Key Control Indicators (KCIs) for Supplier, Supply Chain, and Third-Party Risks
KCIs monitor the effectiveness of controls that are in place to mitigate risks. They help ensure that appropriate actions are being taken to manage identified risks.
- Supplier Audits and Assessments:
- KCI Example: Number and frequency of completed supplier audits.
- Scoring: Quantitative (number of audits) or Qualitative (audit compliance level: High, Medium, Low).
- Trend Analysis: Track the completion of audits and any recurring issues or improvements.
- Contractual Compliance:
- KCI Example: Percentage of suppliers in compliance with contractual terms.
- Scoring: Quantitative (% of compliant contracts).
- Trend Analysis: Measure trends in contract compliance to assess control effectiveness over time.
- Supply Chain Visibility:
- KCI Example: Availability of real-time data across the supply chain (e.g., inventory levels, shipping status).
- Scoring: Quantitative (real-time data integration rate) or Qualitative (High, Medium, Low visibility).
- Trend Analysis: Monitor the improvement or decline in supply chain transparency and control effectiveness.
- Incident Response Time:
- KCI Example: Average time to resolve supply chain disruptions (e.g., cyberattacks, natural disasters).
- Scoring: Quantitative (time to resolve incidents in hours or days).
- Trend Analysis: Track the response time to incidents to measure the efficiency of controls.
- Training and Certification:
- KCI Example: Percentage of supplier personnel trained in cybersecurity or compliance.
- Scoring: Quantitative (% of trained personnel).
- Trend Analysis: Track training completion rates over time to ensure ongoing compliance and control enhancement.
Scoring KRIs and KCIs:
Both quantitative and qualitative scoring methods can be used to measure KRIs and KCIs, depending on the specific risk or control being monitored:
- Quantitative Scoring: Often numeric, providing hard data (e.g., % on-time deliveries, number of incidents). This is useful for trend analysis and visualizing data over time.
- Qualitative Scoring: Typically categorical (e.g., High, Medium, Low). Useful when the data is more subjective or when precise numbers are not available but can still indicate trends.
Trend Analysis for KRIs and KCIs:
- Use dashboards and reporting tools (e.g., Power BI, Tableau) to visualize trends in both KRIs and KCIs.
- Track the progression of indicators over time to detect improvements, deteriorations, or sudden changes.
- Plot both KRIs and KCIs together to show how risk exposure relates to the effectiveness of controls.
By using this combination of KRIs and KCIs, and applying either quantitative or qualitative scoring methods, you can develop a robust framework for assessing supplier and third-party risks while also tracking control effectiveness. This allows for ongoing monitoring and the ability to display trends over time, providing a clear picture of risk management performance.
Tools for KRIs and KCIs for supplier risk, supply chain, and third-party risk management:
Here are several tools that provide Key Risk Indicators (KRIs) and Key Control Indicators (KCIs) for supplier risk, supply chain, and third-party risk management, along with built-in capabilities for scoring and trend analysis with minimal tuning:
A. Prevalent Third-Party Risk Management Platform
- Capabilities: Prevalent offers automated risk assessments, scoring, and monitoring of third-party risks, including Key Risk Indicators. It includes features like dynamic risk scoring, risk reports, and dashboards that allow you to track trends over time.
- Out-of-the-box features: Prebuilt templates and vendor risk profiles for faster deployment. Minimal tuning is needed to customize risk indicators.
- Scoring: Quantitative and qualitative scoring based on risk factors like financial health, regulatory compliance, and operational risk.
- Trend analysis: Visualize risk trends across multiple suppliers over time through dashboards.
- Website: Prevalent
B. RiskWatch
- Capabilities: RiskWatch provides automated risk assessments, scoring, and monitoring for supply chain and third-party risks. It includes out-of-the-box templates for creating KRIs and KCIs across different domains like cybersecurity, operational risk, and vendor compliance.
- Out-of-the-box features: Prebuilt assessments for vendor risk management and supply chain risk with customizable KPIs.
- Scoring: Quantitative scoring (e.g., risk scores) and qualitative ratings (e.g., high, medium, low) to reflect overall risk.
- Trend analysis: Automatically generate risk trend reports to view changes over time.
- Website: RiskWatch
C. MetricStream Third-Party Risk Management
- Capabilities: MetricStream offers a comprehensive platform for managing third-party and supply chain risk. It supports KRIs and KCIs through built-in risk scoring, assessments, and monitoring.
- Out-of-the-box features: Pre-configured templates and risk indicators for third-party risk assessments with options to customize.
- Scoring: Quantitative and qualitative scoring based on factors like vendor performance, compliance, and cybersecurity.
- Trend analysis: Visual dashboards for monitoring key risk/control trends and risk assessments over time.
- Website: MetricStream
D. Aravo Third-Party Risk Management
- Capabilities: Aravo provides a platform for third-party risk management with built-in KRIs and KCIs to assess and monitor suppliers and vendors. The platform comes with automated workflows for risk assessments and tracking.
- Out-of-the-box features: Pre-configured templates for third-party risk with minimal need for customization.
- Scoring: Both quantitative and qualitative risk scoring, based on compliance and operational risks.
- Trend analysis: Real-time dashboards and reports that track and display risk trends and the effectiveness of control measures.
- Website: Aravo
E. RSA Archer Third-Party Governance
- Capabilities: RSA Archer offers robust tools for managing third-party and supply chain risks, with pre-configured KRIs, KCIs, and workflows. It also has reporting capabilities that visualize risks and control trends over time.
- Out-of-the-box features: Configurable dashboards, risk templates, and automated workflows for supplier risk management.
- Scoring: Quantitative risk scoring through risk indicators, combined with qualitative evaluations of vendor performance and compliance.
- Trend analysis: Visual dashboards for monitoring trends, and built-in analytics for historical comparisons of risk and control performance.
- Website: RSA Archer
F. LogicManager
- Capabilities: LogicManager includes features for managing third-party risk, with configurable risk indicators and automated reporting for tracking trends in both risk exposure and control effectiveness.
- Out-of-the-box features: Prebuilt templates and automated workflows to quickly deploy risk assessments and KRIs.
- Scoring: Risk scores based on vendor financial health, regulatory compliance, and operational risk. Both qualitative and quantitative metrics can be incorporated.
- Trend analysis: Trend analysis via automated reporting and dashboards that track risk factors over time.
- Website: LogicManager
G. Coupa Risk Assess
- Capabilities: Coupa’s risk management module provides an integrated platform for assessing supply chain and third-party risks. It uses KRIs and KCIs to monitor supplier performance and compliance with minimal setup.
- Out-of-the-box features: Preconfigured risk indicators and reporting templates for quick implementation.
- Scoring: Quantitative scoring using real-time risk data from multiple sources, as well as qualitative assessments.
- Trend analysis: Built-in analytics and visualizations that show trends in supplier risk over time.
- Website: Coupa
H. ProcessUnity Vendor Risk Management
- Capabilities: ProcessUnity provides a vendor risk management solution that tracks key risks and controls for third-party suppliers. It includes KRIs and KCIs, real-time reporting, and analytics to display trends in vendor risk.
- Out-of-the-box features: Ready-to-use templates for vendor risk scoring and assessments.
- Scoring: Quantitative and qualitative risk assessments based on supplier financial health, regulatory compliance, and cybersecurity posture.
- Trend analysis: Customizable dashboards to visualize risk and control trends over time.
- Website: ProcessUnity
Conclusion:
These tools are designed to automate the tracking of Key Risk Indicators (KRIs) and Key Control Indicators (KCIs), providing both quantitative and qualitative scoring, as well as trend analysis. Many of them come with out-of-the-box templates and minimal tuning requirements, making them suitable for quickly implementing a risk management framework for supplier and third-party risk.
Other References:
https://www.prevalent.net/blog/use-nist-sp-800-53-for-third-party-supply-chain-risk-management
https://www.upguard.com/blog/kpis-to-measure-tprm
https://www.venminder.com/blog/examples-key-risk-indicators-third-party-management