
The Cyber Security Body of Knowledge (CyBOK) is a comprehensive resource that aims to codify the foundational and generally recognized knowledge on Cyber Security.
Within CyBOK, one of the knowledge areas is “Operating Systems & Virtualisation.” This knowledge area focuses on the principles, concepts, and techniques related to operating systems and virtualization in the context of cybersecurity.
It explores various topics related to the design, implementation, and security considerations of operating systems and virtualization technologies.
i. Key Components of the Operating Systems & Virtualization Knowledge Area

A. Operating Systems Fundamentals: This component covers the essential concepts and components of operating systems, including process management, memory management, file systems, and input/output (I/O) subsystems.
o Core functions of operating systems
o Processes and threads management
o Memory management, including virtual memory
o Filesystems and storage management
o I/O management and device drivers
o Security features and mechanisms
B. Operating Systems Security: It explores the security aspects of operating systems, including access control mechanisms, authentication, authorization, secure configuration, and secure communication.
o Access control models and methods
o User authentication and authorization
o Audit logging and monitoring
o Operating system hardening techniques
o Patch management and vulnerability mitigation
C. Virtualization Technologies: This component introduces various virtualization technologies, such as virtual machines (VMs), hypervisors, containers, and cloud infrastructure, along with their benefits, capabilities, and security considerations.
o Concepts and benefits of virtualization
o Types of virtualization (e.g., hardware, software, OS-level virtualization, etc.)
o Hypervisors and Virtual Machine Monitors (VMMs)
o Virtualized environments security challenges
o Containerization technologies like Docker and Kubernetes
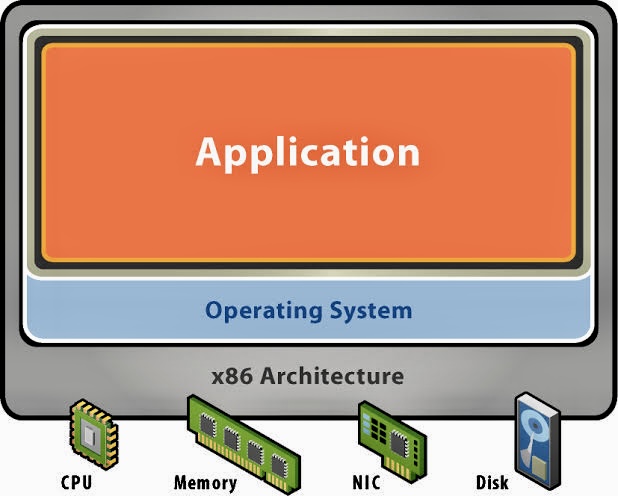
D. Virtualization Security: It addresses the security challenges and countermeasures associated with virtualization technologies, including VM escape, isolation, hypervisor security, and securing cloud-based virtualized environments.
o Secure design and configuration of virtual environments
o Security implications of various virtualization architectures
o Hypervisor security and isolation properties
o Inter-VM attacks and countermeasures
E. Trusted Computing:
o Trusted Platform Modules (TPMs)
o Hardware and firmware security
o Secure booting mechanisms and root of trust
F. OS-Level Security Mechanisms:
o Security through isolation and compartmentalization
o Mandatory Access Control (MAC), Discretionary Access Control (DAC), and Role-Based Access Control (RBAC)
o Sandboxing and application whitelisting
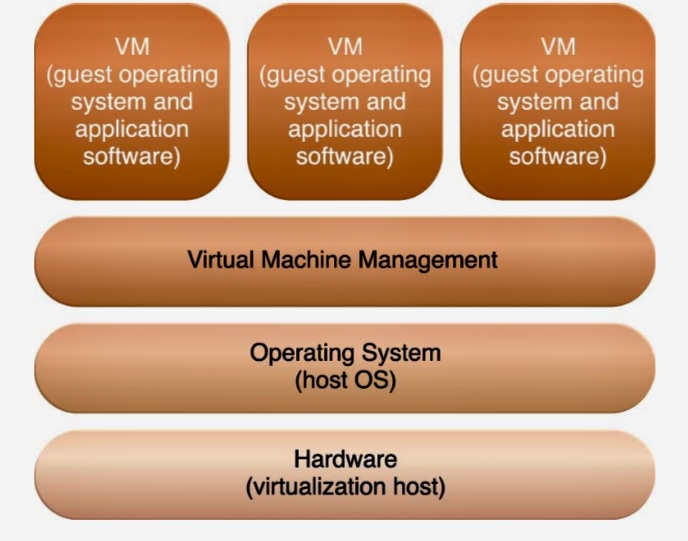
G. Secure System Configuration: This component focuses on the secure configuration of operating systems and virtualized environments. It covers topics such as hardening, patch management, system monitoring, and intrusion detection/prevention.
H. Virtual Machine Security: It specifically delves into the security aspects of virtual machines, covering secure VM deployment, VM escape prevention, VM image security, and secure lifecycle management of VMs.
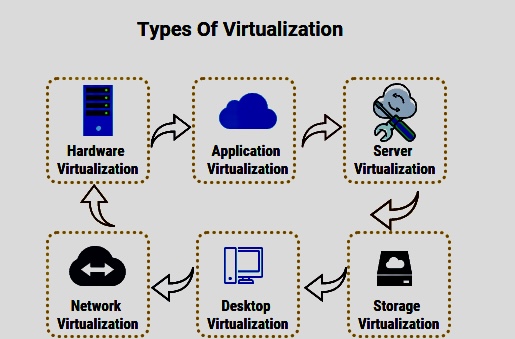
I. Network Security in Virtualized Environments: This component explores network security considerations within virtualized environments, including virtualized network infrastructure, virtual switches, VLANs, and network segmentation for enhanced security.
J. Threats and Attacks in Virtualized Environments: It examines the different types of threats and attacks that target operating systems and virtualized environments, including malware, privilege escalation, VM sprawl, and virtual machine manipulation.
The Operating Systems & Virtualisation Knowledge Area within CyBOK covers key concepts pertaining to the design and operation of operating systems, as well as virtualization technologies, which are critical components for understanding how modern computing environments are secured.
In cybersecurity, understanding the principles of operating systems and virtualisation is essential because many vulnerabilities and threats target these components of IT infrastructure. Security professionals must be versed in these foundational elements to effectively protect systems from malicious actors. CyBOK provides a structured framework that assists in education and informs professionals about these and other critical knowledge areas in cyber security.
https://ivy.fm/podcast/cybok–the-cybersecurity-body-of-knowledge-679647
https://www.researchgate.net/publication/325981474_Scoping_the_Cyber_Security_Body_of_Knowledge
