Embracing the Future: Essential Skills for ITSM Professionals in an AI-Driven Job Market
The rapid advancement and adoption of artificial intelligence (AI) technologies are reshaping industries, and the field of IT Service Management (ITSM) is no exception.
As organizations strive to enhance efficiency, reduce costs, and improve service delivery, AI is increasingly becoming a vital tool.
For ITSM professionals aiming to stay relevant and competitive in this evolving landscape, acquiring a new set of skills is imperative.
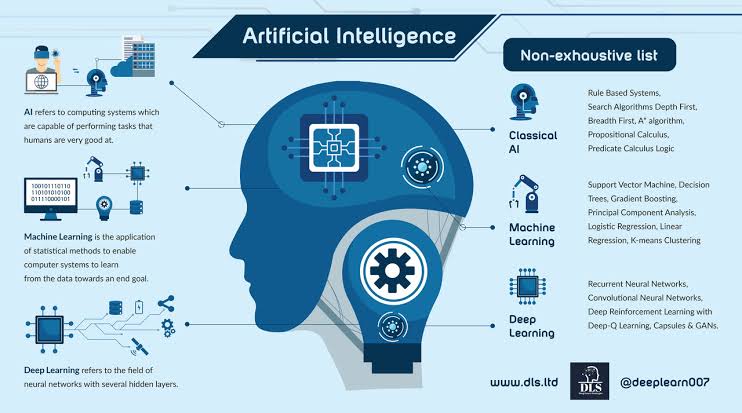
i. Understanding of AI and Machine Learning Fundamentals

o AI and ML Concepts: A foundational knowledge of AI and machine learning (ML) principles is essential. ITSM professionals should understand how AI algorithms work, learn basic ML models, and grasp how these technologies can automate tasks, predict issues, and drive decision-making processes.
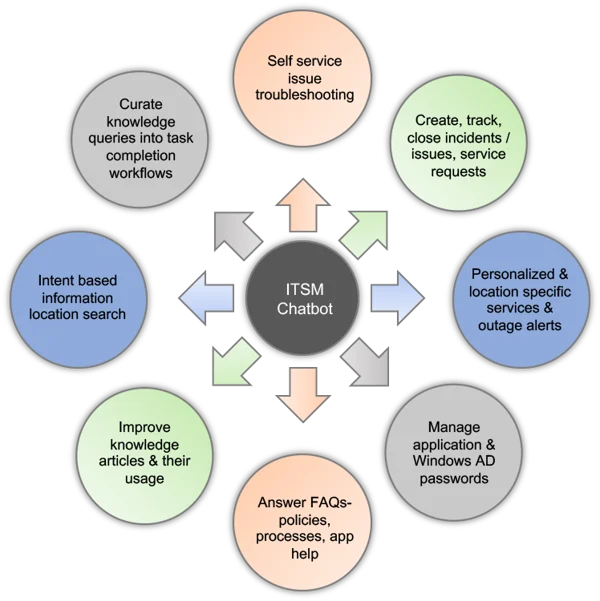
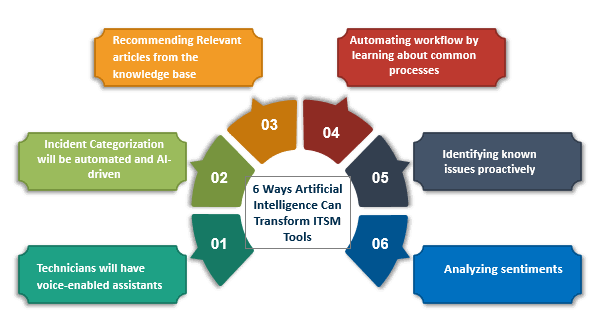
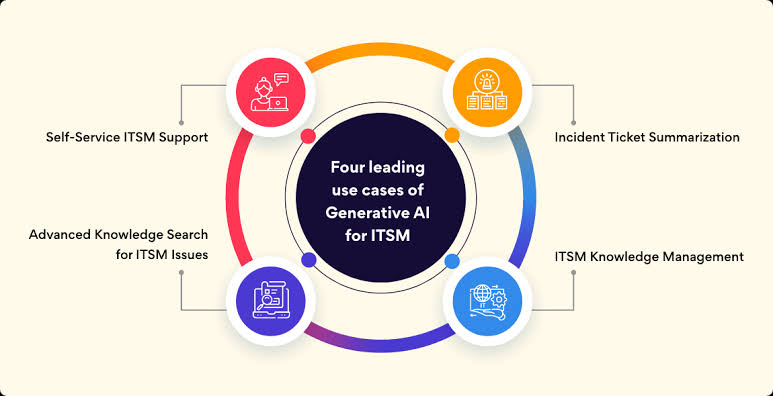
o Application of AI in ITSM: Professionals need to know how AI can be applied in ITSM contexts, such as in predictive analytics for incident management, chatbots for user support, and automation of routine tasks. Understanding specific use cases helps in identifying opportunities to incorporate AI into ITSM strategies.
ii. Data literacy
AI technologies are underpinned by an immense volume of data. Therefore, developing data literacy— the ability to read, understand, create, and communicate data as information—is essential. Proficiency in data analysis tools and methodologies will empower ITSM professionals to derive actionable insights from data, enhancing decision-making and strategic planning processes.
iii. Data Analysis and Management

o Data Analytics Skills: Proficiency in data analysis is crucial because AI systems rely heavily on data for training models and making decisions. ITSM professionals must be able to interpret data, draw insights, and understand data quality requirements for AI applications.
o Data Governance: Managing and safeguarding data is increasingly important. Knowledge of data governance principles ensures that data used in AI systems is accurate, secure, and compliant with regulations.
iv. Programming and Automation Skills
o Coding Knowledge: A basic understanding of programming languages used in AI development, such as Python or R, can be highly beneficial. This doesn’t mean ITSM professionals need to become expert coders, but a familiarity with the basics can aid in collaborating more effectively with AI teams.
o Automation Tools: Familiarity with automation tools and platforms that integrate AI functionalities within ITSM workflows is essential. Knowing how to leverage these tools can lead to significant efficiency gains.
v. Change Management and Strategic Thinking

o Adapting to Change: As AI reshapes ITSM processes, the ability to manage change is more important than ever. ITSM professionals should be skilled in leading and managing transition processes, including technology adoption, and in preparing teams for new ways of working.
o Strategic Planning: Understanding how AI can align with and support the organization’s overall objectives is key. Professionals must be able to develop strategies that leverage AI for competitive advantage and innovation in service management.
vi. Automation expertise

With AI automating routine tasks, ITSM professionals will need to develop expertise in designing, implementing, and managing automated workflows to improve efficiency and free up time for more strategic work.
vii. Critical thinking and problem-solving
As AI takes over routine tasks, ITSM professionals will need to focus on higher-order thinking skills like critical analysis, problem-solving, and decision-making to address complex issues and ensure service continuity.
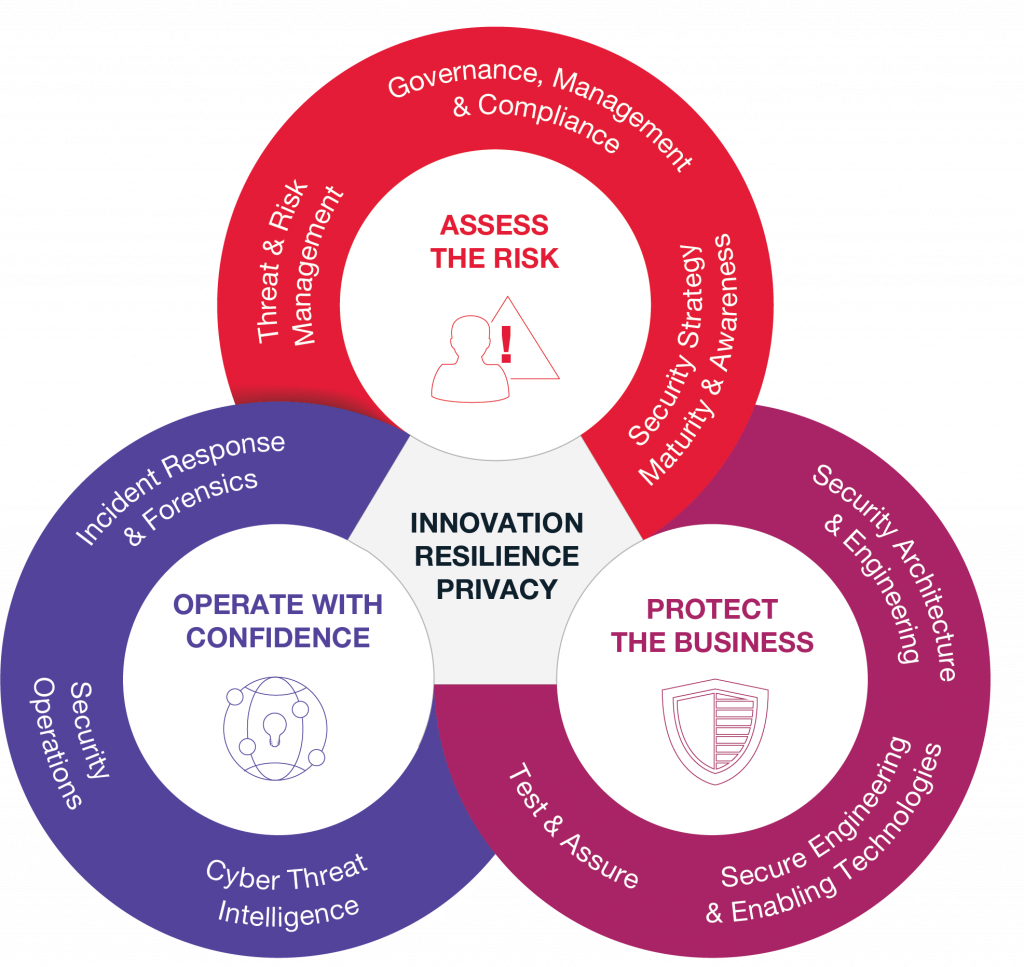
viii. Ethical Considerations and AI Governance

o Ethical AI Use: With the power of AI comes responsibility. ITSM professionals should be aware of ethical considerations, ensuring AI is used in a way that is fair, transparent, and respects privacy.
o AI Governance: Knowledge of frameworks and guidelines for AI governance is important for ensuring responsible AI implementation. This includes monitoring AI systems for biases, errors, and performance issues.
ix. Emotional Intelligence and Ethical Considerations

As AI takes over more technical tasks, the importance of human-centered skills like emotional intelligence (EQ) will surge. ITSM professionals must hone their EQ to manage teams effectively, foster collaboration, and navigate the complex ethical considerations AI introduces. Understanding the ethical implications of AI, including bias, privacy, and job displacement concerns, will be critical for guiding ethical AI integrations in IT services.
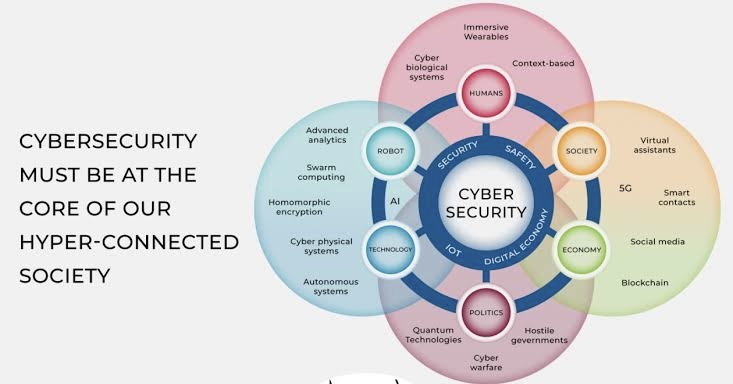
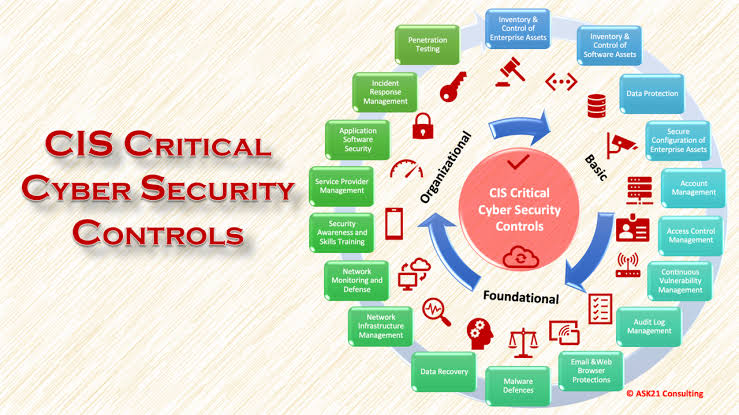
x. Cybersecurity Proficiency

As AI technologies become more prevalent, cybersecurity threats are evolving in sophistication. ITSM professionals need to prioritize cybersecurity proficiency to safeguard organizational data and systems from cyber threats. Understanding AI-based security solutions, threat detection techniques, and risk mitigation strategies will be crucial in ensuring the integrity and resilience of ITSM infrastructures.
xi. Continuous Learning and Adaptability

o Lifelong Learning: The field of AI is dynamic, with new developments constantly emerging. A commitment to continuous learning, through courses, workshops, and staying abreast of industry trends, is crucial.
o Adaptability: The ability to adapt to new technologies and approaches is essential. ITSM professionals should be open to experimenting with new tools, workflows, and methodologies as the field evolves.
xii. Communication and interpersonal skills

The human touch will remain essential in ITSM. Strong communication and interpersonal skills will enable ITSM professionals to effectively explain complex AI concepts to stakeholders, collaborate with AI systems, and provide exceptional customer service.
xiii. Conclusion

In conclusion, as AI continues to sculpt the job market, ITSM professionals must proactively expand their skill sets beyond traditional IT service management paradigms.
Acquiring a mixture of technical competencies, soft skills, and a deep appreciation for the ethical dimensions of AI will equip ITSM professionals to navigate the challenges and opportunities presented by AI adoption.
Investing in these areas will not only secure their relevance in the future job market but also position them as leaders in the AI-transformed ITSM landscape.
xiv. Further references
TechBeaconhttps://techbeacon.com › will-ai-ta…Will AI take your IT operations job?
ServiceNowhttps://www.servicenow.com › blogsAI and the Skills of the Future
DevOps.comhttps://devops.com › the-skills-suc…The Skills Successful DevOps Pros Need in 2023
LinkedIn · win10+ reactionsThe Impact of Artificial Intelligence on the Job Market