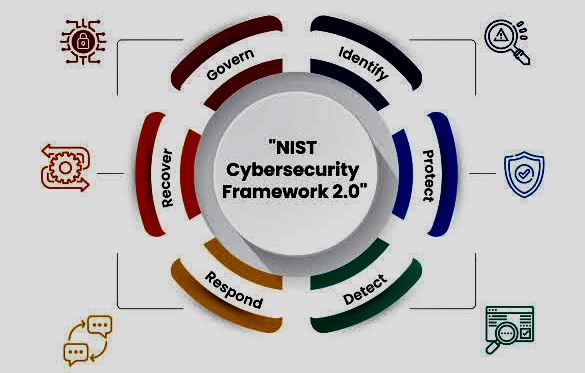
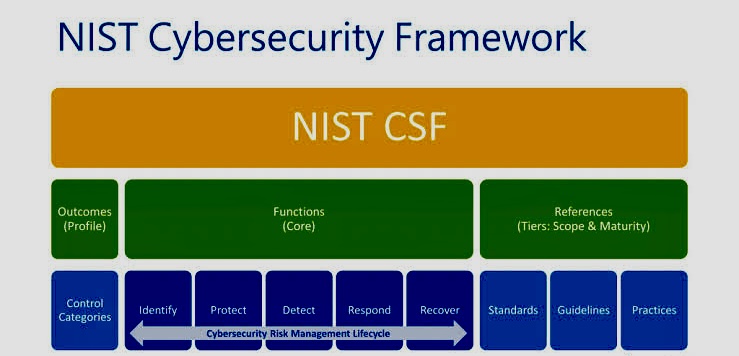
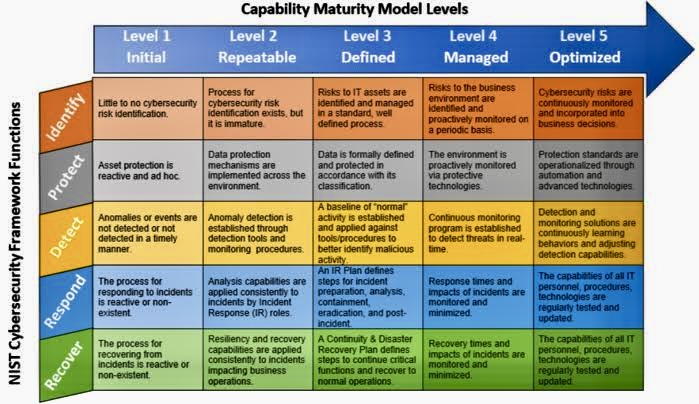
Compliance with the NIST Cybersecurity Framework (CSF) involves adopting a set of policies, procedures, and technologies that align with the five core functions outlined by the framework: Identify, Protect, Detect, Respond, and Recover.
Organizations apply these functions to manage cybersecurity risk in a holistic, comprehensive manner.
i. Here’s what each function typically involves:
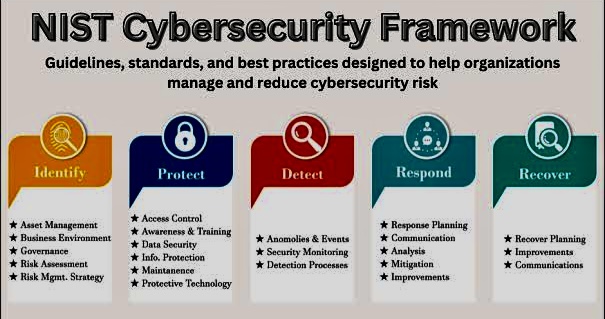
A. Identify:
o Develop an organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities. This involves asset management, business environment comprehension, governance, risk assessment, and risk management strategy.
B. Protect:
o Outline safeguards to ensure delivery of critical infrastructure services. Protect encompasses access control, data security, information protection processes and procedures, maintenance, and protective technology.
C. Detect:
o Implement appropriate activities to identify the occurrence of a cybersecurity event. Detect involves continuous security monitoring, anomaly and event detection, and assessment of the severity of incidents.
D. Respond:
o Take action regarding a detected cybersecurity event. Respond includes response planning, communications, analysis, mitigation, and improvements following an incident.
E. Recover:
o Develop plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident. Recovery encompasses recovery planning, improvements, and communications.
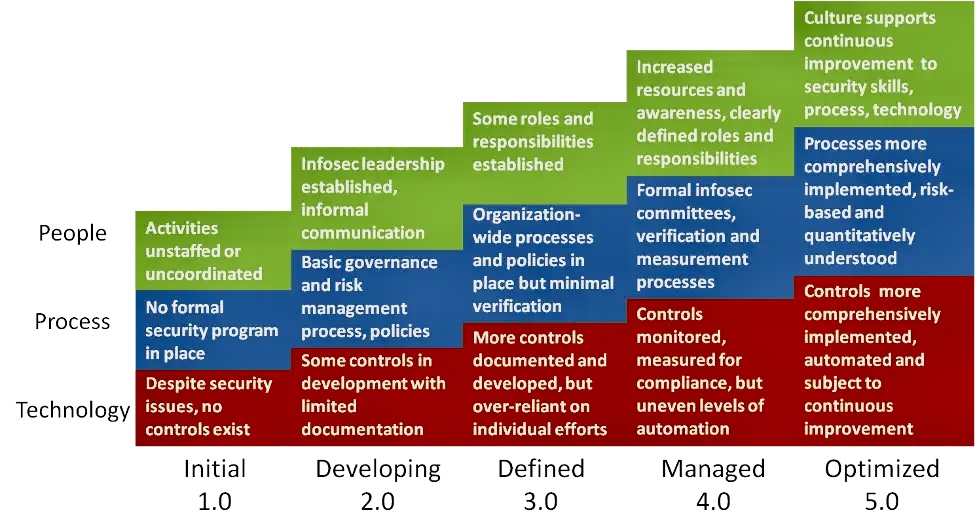
Adherence to the NIST CSF also means establishing a continuous improvement plan to adapt to the evolving cyber landscape.
ii. Here’s how organizations might approach this process:
A. Risk Assessment: Organizations should regularly perform risk assessments to identify and prioritize threats.
B. Policies and Procedures: Formulating clear cybersecurity policies and procedures helps in both the alignment with the framework and in providing a clear path for the workforce to follow.
C. Training and Awareness: Continuous training programs for employees ensure that everyone is aware of the threats and knows how to avoid them or respond if necessary.
D. Incident Response: Having a robust incident response plan is essential for quickly containing and mitigating breaches.
E. Recovery Plan: Just as with incident response, organizations need a strong recovery plan to minimize downtime and restore services after a breach.
F. Audit and Monitoring: Routine audits and continuous monitoring are necessary to ensure that cybersecurity measures are effective and to identify areas needing improvement.
G. Vendor Management: Vendors must also comply with the NIST standards, especially if they handle an organization’s data or systems. As such, their compliance should be regularly assessed.
iii. Here’s a guide on how to ensure compliance with the NIST CSF:
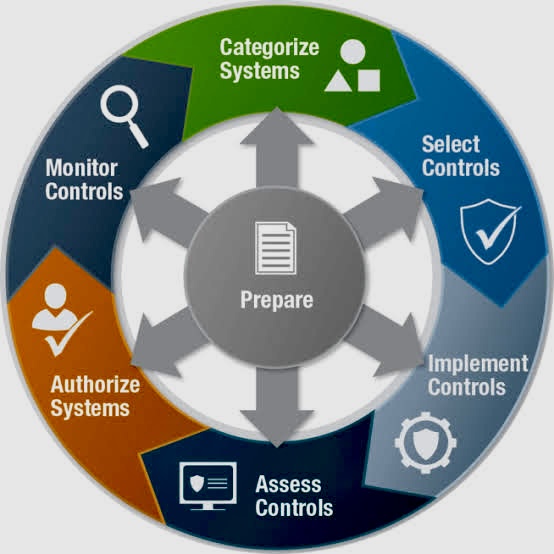
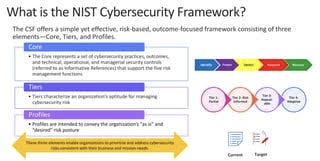
A. Understand the Framework: Familiarize yourself with the NIST CSF documentation, including the Core, Implementation Tiers, and Framework Profile. Understand the five functions: Identify, Protect, Detect, Respond, and Recover.
B. Assessment of Current State (Identify): Conduct a comprehensive assessment of your organization’s current cybersecurity practices. Identify and document assets, risks, and vulnerabilities. This is the foundation of the NIST CSF.
C. Establish a Governance Structure: Develop a governance structure that supports the implementation of the NIST CSF. Clearly define roles, responsibilities, and accountability for cybersecurity at all organizational levels.
D. Create a Risk Management Program: Develop and implement a risk management program aligned with the NIST CSF. This includes assessing risks, prioritizing them, and establishing risk mitigation strategies.
E. Set Objectives: Define specific objectives based on the CSF’s core functions. Tailor these objectives to align with your organization’s unique needs, risk tolerance, and business objectives.
F. Develop a Roadmap: Create a detailed plan outlining the steps required to achieve compliance. This roadmap should prioritize actions based on risk and resource availability. Consider factors like technology, personnel, budget, and timelines.
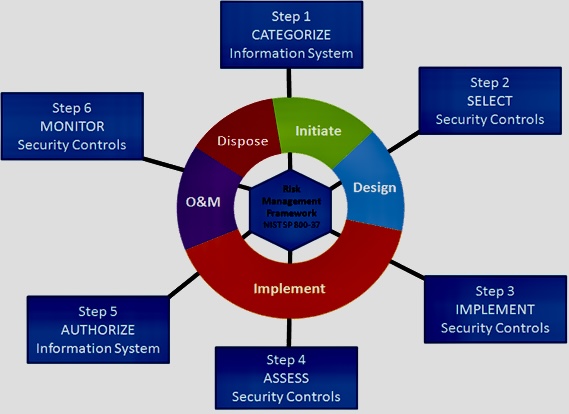
G. Implement Controls: Implement appropriate safeguards and controls to address identified gaps and mitigate cybersecurity risks. This may include adopting security policies, deploying security technologies, conducting training and awareness programs, and establishing incident response and recovery processes.
H. Develop a Framework Profile: Create a Framework Profile based on the organization’s business needs, risk tolerance, and available resources. Tailor the NIST CSF functions and categories to align with your specific objectives.
I. Implement Core Functions (Protect, Detect, Respond, Recover): Develop and implement policies, procedures, and controls to address each of the Core Functions. This includes protecting assets, detecting cybersecurity events, responding to incidents, and recovering from them.
J. Establish an Incident Response Plan (Respond): Develop an incident response plan that aligns with the NIST CSF. Clearly define roles and responsibilities for responding to and mitigating cybersecurity incidents.
K. Training and Awareness Programs: Implement cybersecurity training and awareness programs for employees. Ensure that staff is informed about cybersecurity risks, policies, and best practices.
L. Continuous Monitoring (Detect): Establish continuous monitoring capabilities to detect and respond to cybersecurity events in real-time. Leverage technologies and processes to identify anomalies and potential threats.
M. Collaboration with Third Parties: If applicable, extend the NIST CSF principles to third-party vendors. Ensure that vendors adhere to cybersecurity standards and practices to mitigate risks associated with external partnerships.
N. Regular Assessments and Audits: Conduct regular assessments and audits to evaluate the effectiveness of your cybersecurity controls and adherence to the NIST CSF. Use the results to make improvements and adjustments as needed.
O. Document and Communicate: Document your implementation of the NIST CSF and communicate it to relevant stakeholders. This documentation serves as evidence of compliance and helps in maintaining transparency.
P. Incident Analysis and Lessons Learned (Recover): After incidents, conduct thorough analyses to understand what happened and why. Use the lessons learned to improve your organization’s ability to recover effectively.
Q. Continuous Improvement: Embrace a culture of continuous improvement. Regularly review and update your cybersecurity practices to align with changes in the threat landscape and updates to the NIST CSF.
Using the NIST CSF as a guide, organizations can strengthen their cybersecurity posture and minimize the risks associated with cyber threats.
The framework is voluntary, but it has gained recognition as a gold standard for cybersecurity practices across various industries. Compliance can also support adherence to other regulations and standards, such as GDPR for privacy or ISO/IEC 27001 for information security management.
Achieving compliance with the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) is essential for organizations aiming to establish a robust and adaptive cybersecurity posture.
https://www.cisco.com/c/en/us/products/security/what-is-nist-csf.html#~the-basics-of-csf
https://www.auditboard.com/blog/fundamentals-of-nist-cybersecurity-framework-controls/
